Email roulette, May 2019
Introduction
For today's diary I play a game of email roulette. My version of email roulette is picking a recent item of malicious spam (malspam), running the associated email attachment in a live sandbox, and identifying the malware. I acquired a recent malspam example through VirusTotal (VT) Intelligence. Let's see what the roulette wheel give us today!
Searching for malspam attachments in VT Intelligence
VT Intelligence is a subscription server, and from what I understand, it's fairly expensive. Fortunately I have access through my employer. In the VT Intelligence search window, I used the following parameters:
tag:attachment fs:2019-05-07+ p:3+
This returned anything tagged as an email attachment, first seen on or after 2019-05-07, with at least 3 vendors identifying an item as malicious. After the results appeared, I sorted by the most recent submissions.
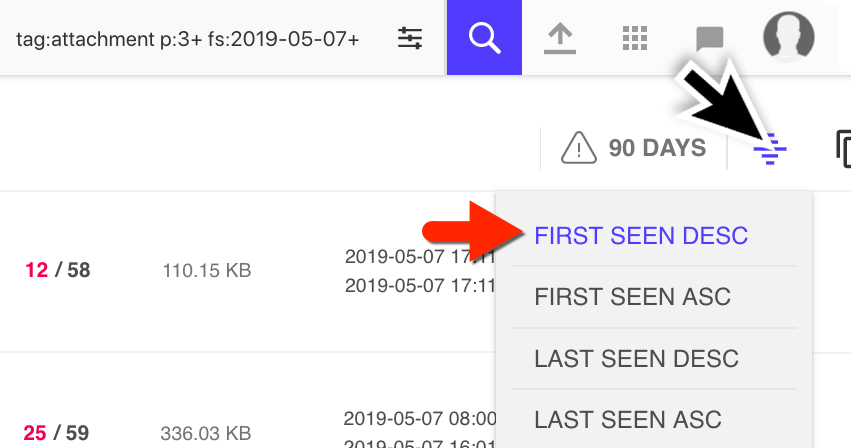
Shown above: Searching and sorting in the VT Intelligence portal.
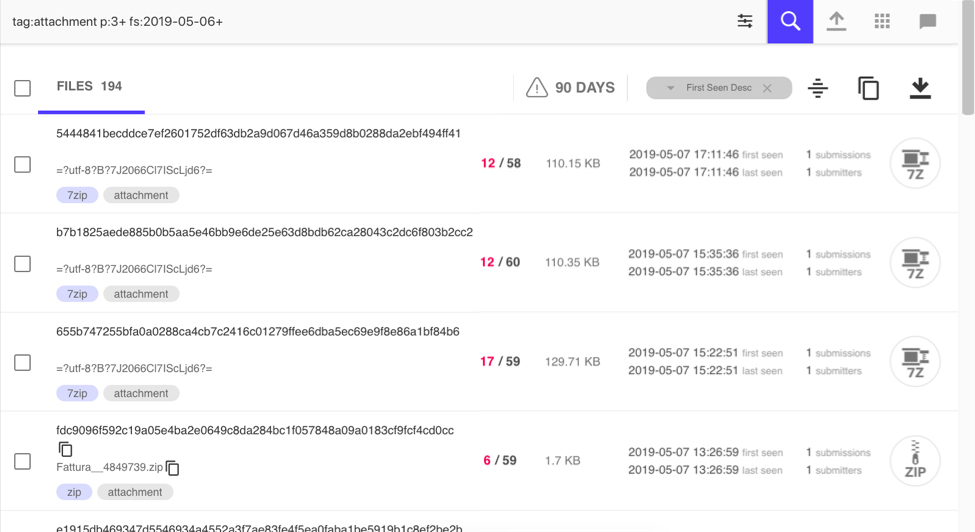
Shown above: Results sorted by most recent at the time of my search.
The three most recent results I saw were 7-zip archives (.7z files). The file names did not use ASCII characters, but were base64 encoded. The base64 string represents UTF-8 characters, where the format is name:"=?utf-8?B?[base64 string]?="
I picked the most recent result and selected the relations tab, which revealed the associated malspam. Then I retrieved that email from VT Intelligence.
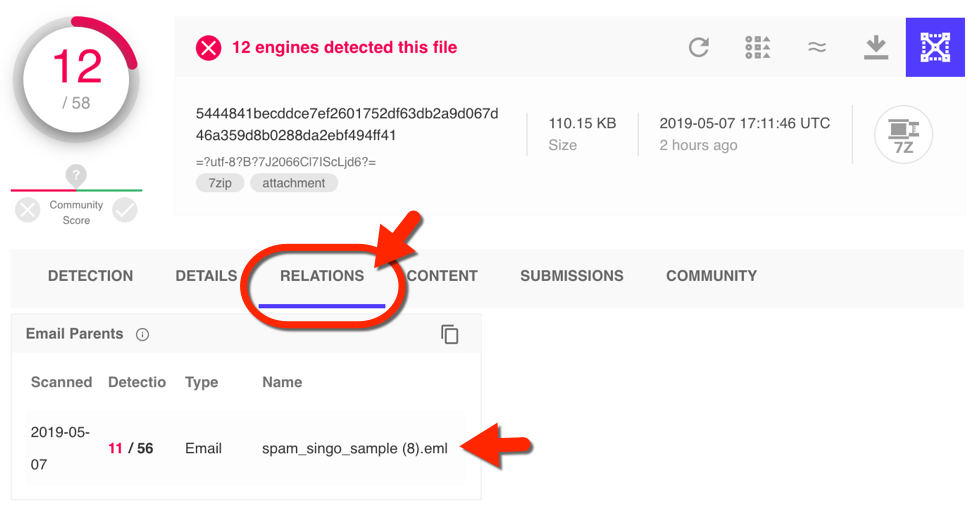
Shown above: Pivoting on the attachment to find its parent email.
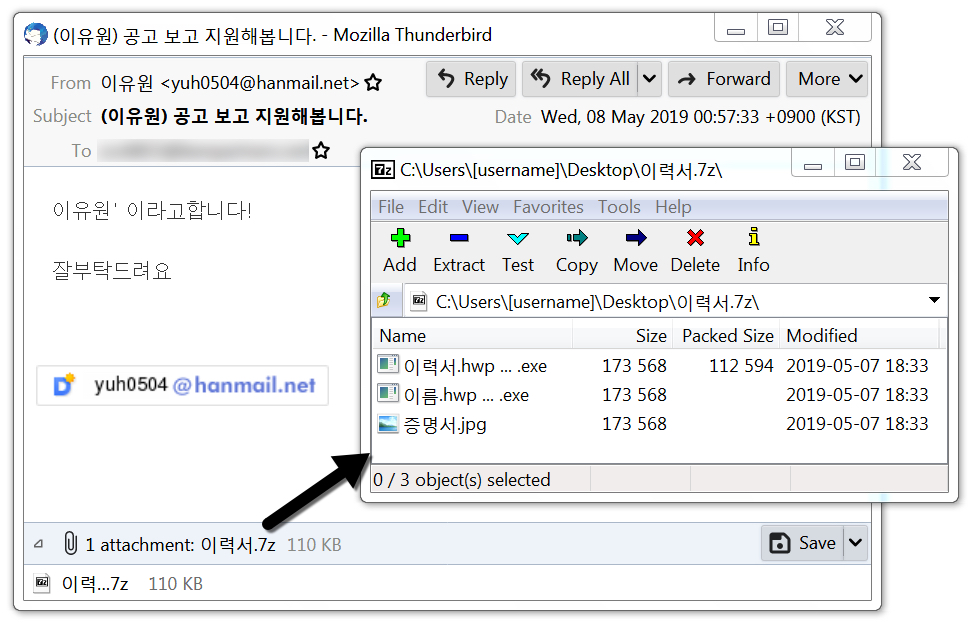
Shown above: The email opened in Thunderbird on a Windows 7 host.
The attached 7-zip archive contained 3 files with different names, but they were all the same file hash, so they were the same malware. I extracted them and ran one on a vulnerable Windows host. The result was a Gandcrab ransomware infection.
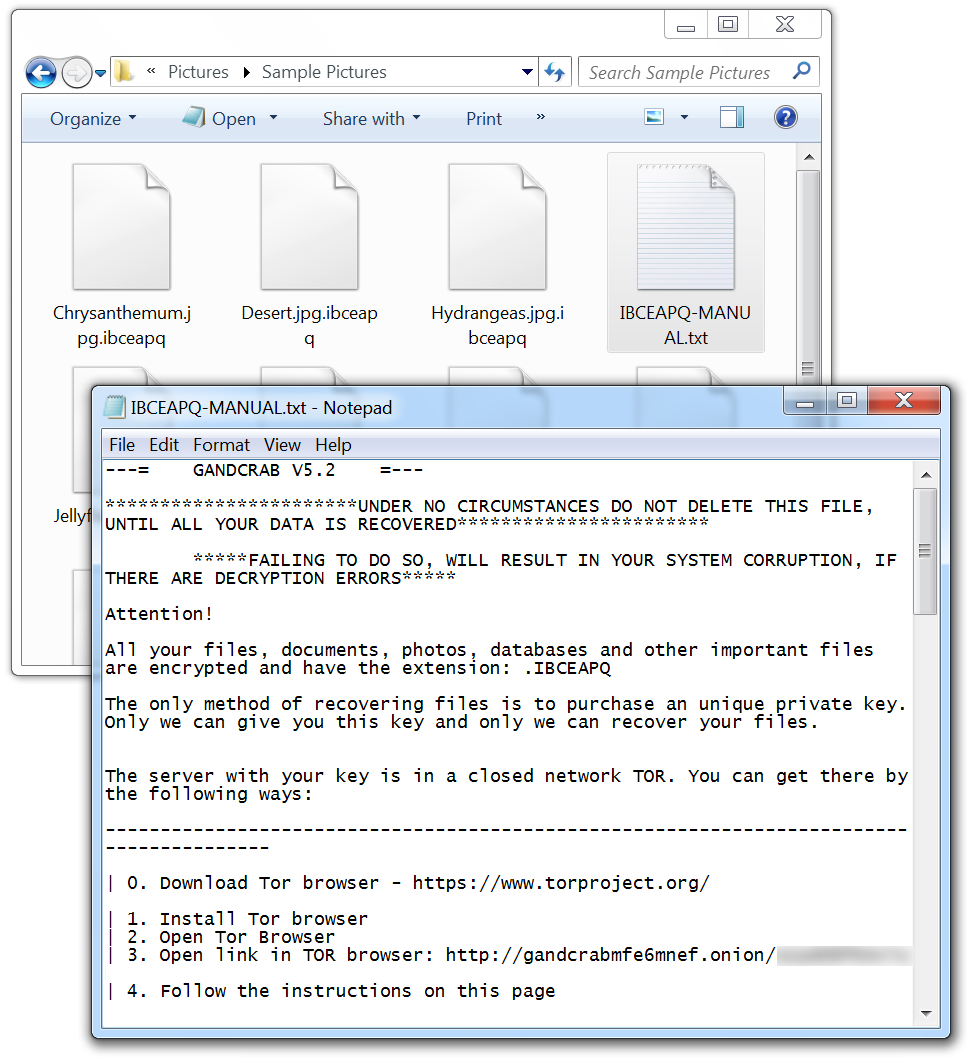
Shown above: Encrypted files and the ransom note on my infected Windows host.
Indicators
The following are indicators associated with this infection:
SHA256 hash: 39f97e750a8ebcc68a5392584c9fd8edc934e978d6495d3ae430cb7ee3275ffe
- File size: 157,810 bytes
- File description: Example of Korean malspam (.eml file) pushing Gandcrab
SHA256 hash: 5444841becddce7ef2601752df63db2a9d067d46a359d8b0288da2ebf494ff41
- File size: 112,792 bytes
- File description: 7-zip archive (.7z file) attached to Korean malspam
SHA256 hash: df53498804b4e7dbfb884a91df7f8b371de90d6908640886f929528f1d6bd0cc
- File size: 173,568 bytes
- File description: Gandcrab executables (.exe files) extracted from the above .7z archive
- Any.Run sandbox analysis
Final words
This round of email roulette gave us a Gandcrab ransomware infection. What type of malware might I find next? Perhaps we'll know when I try this again next month for another diary.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments