Multipurpose PCAP Analysis Tool
I was looking for a tool to easily graph traffic for a project (there are many out there) and while searching I found this tool written as a project by "[...] Daniel Botterill as part of his MSc Computer Security degree, it has been designed to take in a PCAP capture file and report back any malicious behaviour identified."[1]
This tool is packed with options (tabs) to analyze traffic in many different ways. There is two sample pcap files included in the MalwareAnalysis folder for testing the tool or you can use your own. I update two lists in BlocklistedAddresses\blocklists [3][4] folder before starting the tool for the first time. You can add any list you want which will need to be configured after you start the tool under the Analyzer Settings which I will come back later.
This tool is easy to use and requires Java to be installed in order to work. Download the package from here. It runs on Windows and Linux (I haven't tested it on Linux) and unzip it. There are 4 scripts available to copy (as admin) the correct windows version of jnetpcap.dll to %windir%\system32 or same process for libjnetpcap.so to the correct Linux library. To start the program after the initial installation, you can execute the MalWareAnalysis.jar file.
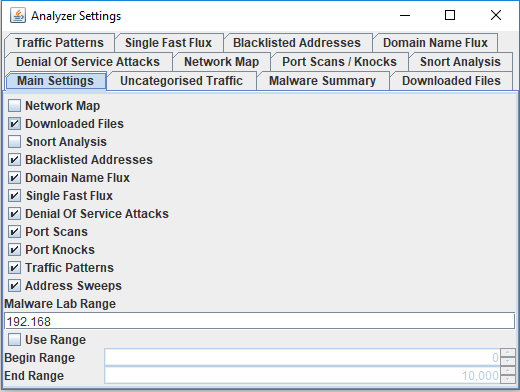
Now it is time to configure the tool before importing any packets. To configure the tool, select Options -> Analyzer Settings:
All the different options are displayed here. For example, I wanted a Network Map to display the traffic relationships and I checked the network map box before moving on to the Blocklisted Addresses tab and added the bt_spyware.txt list to my analyzer as this graph:
Next open and import a pcap file into the PCAP Analyzer:
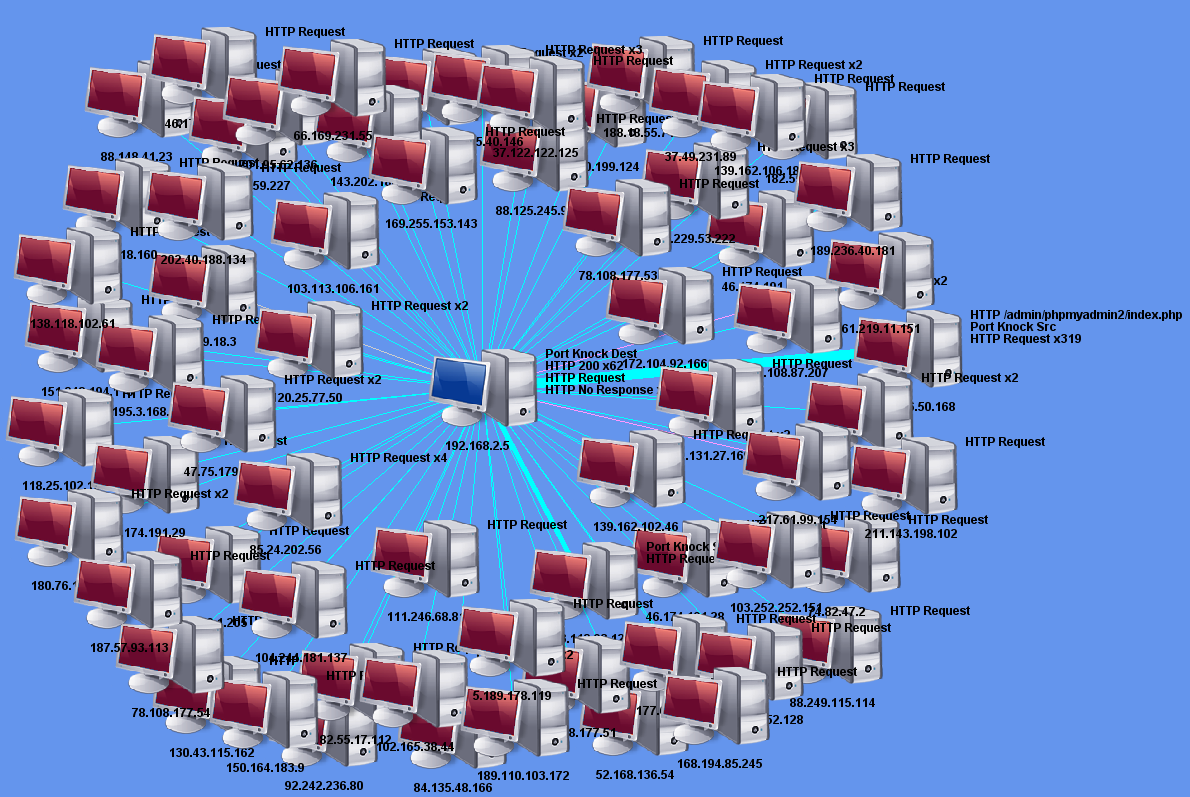
The pcap I picked contained all the web connections to my honeypot for the last 24 hours. I now go to the Network Map tab and check the traffic relationship between my honeypot (center 192.168.25.5) and the inbound connections to the web server. The graph shows how many attempts per IP and sometimes shows the URL. You can adjust the Network Map Layout (drop down from top) to view the IPs or move the icon around. You can see one of the source to the right requested various PHP scripts 319 times(only first one shown) against the honeypot. The thicker is the line, the more traffic between the hosts.
This one of the many features available. The last feature I am going to used is the Stream Viewer -> TCP Streams. Each packet can be selected to view the ASCII data (if readable)
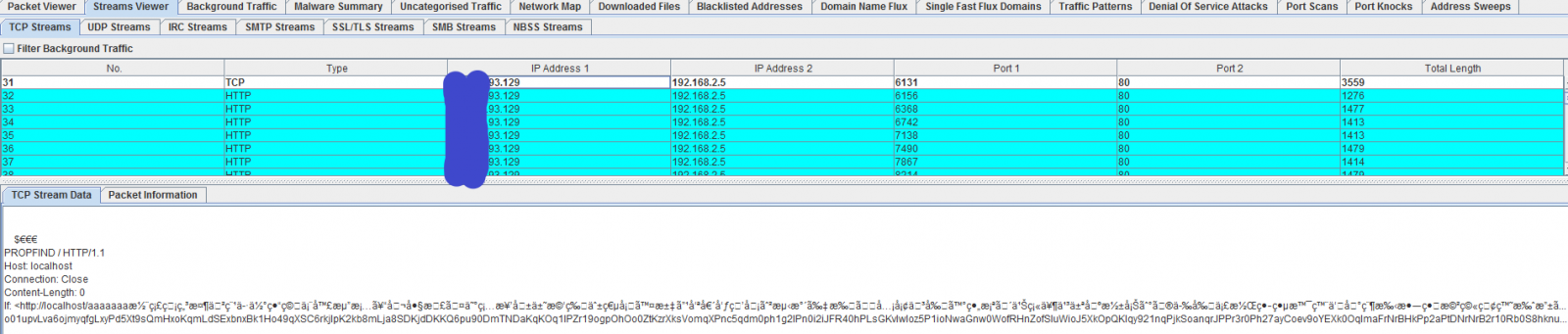
It is not a replacement for Wireshark but has many of its features where some are easier and quicker to use and can be very useful as another tool to analyze traffic and its payload. There are so many more features I could talk about, you just have to test it for yourself if it should become part of your security set.
[1] http://www.cs.bham.ac.uk/~tpc/PCAP/
[2] http://www.cs.bham.ac.uk/~tpc/PCAP/MalwareAnalysis.zip
[3] https://zeustracker.abuse.ch/blocklist.php?download=domainblocklist
[4] https://www.iblocklist.com/lists
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments
So I did a fast check and the results are ... troubling.
URL analysis (2 hits):
https://www.virustotal.com/#/url/be1c4b4dd5c5b2c7109ff7f9f888c0045eea00fd7565f103b87933c655893816/detection
File analysis (3 hits):
https://www.virustotal.com/#/file/f32b9e2a638c9af9f2075e7af0eba37988c8b369dd7069f0b4f007a3c1137ad4/detection
Call me paranoid but I wouldn't just use this outside a very restricted lab.
Anonymous
Nov 19th 2018
7 years ago
It seems that the engines hit on the sample PCAP files provided in the zip archive.
Anonymous
Nov 19th 2018
7 years ago
File Name: trid.exe
File Type: exe
File Size: 60928
File MD5: 562fb3edb3c3ed9b56efd7b869d8f9ae
File SHA1: e2978bc736a0216be5723c7c8027442693db1b7b
File Sha256: bfbfa2634e9197914cbe91d992487fb29d5b7f914c1524a37172c9bdc341e15e
Verdict: Benign
Analyzed On: Check Point Threat Cloud
Resource: http://www.cs.bham.ac.uk/~tpc/PCAP/MalwareAnalysis.zip
File Name: jnetpcap.dll
File Type: dll
File Size: 377974
File MD5: 918e1bd9b2e1df5db4ba80928f07729c
File SHA1: c35137a58850d0f9fcc11a9bc61b0c3fba1f0c52
File Sha256: 9d9385776ae500283fa20902abe98f96051c5d4a6fdf2fd15214626ffb783577
Verdict: Benign
Analyzed On: Check Point Threat Cloud
Resource: http://www.cs.bham.ac.uk/~tpc/PCAP/MalwareAnalysis.zip
File Name: DomainScore.java
File Type: c
File Size: 3657
File MD5: 11a5e96be4495bd3500acf388c7d69d2
File SHA1: a1adcd4f688d13c376f6d4b2e3a97a435795ac9c
File Sha256: 4cc504e584bf541f3ec0ab104dac57ef16b1b193d3a675895d589ce6f155e6a0
Verdict: Benign
Analyzed On: Check Point Threat Cloud
Resource: http://www.cs.bham.ac.uk/~tpc/PCAP/MalwareAnalysis.zip
However the verdict is BENIGN.
But it may mean a lot of people may have a hard time downloading the ZIP file.
Anonymous
Nov 19th 2018
7 years ago
UPDATE 1: I had run it once before, using sample1.pcap. I zipped it up afterwards, and so had the files below.
I took out the files in the following folder, re-zipped, and uploaded to VirusTotal and it came back clean except for Cat-QuickHeak and NANO-Antivirus. Take out the two sample pcaps and its clean.
MalwareAnalysis\DownloadedPCAPFiles\Files\
pcapFile0 - .exe
pcapFile1 - .exe
pcapFile2 - Unknown Long string of alphanumeric characters
pcapFile3 - .exe
pcapFile4 - .exe
pcapFile5 - unknown gibberish - with a SYN or ACK here and there.
pcapFile6 - .exe
pcapFile7 - unknown gibberish - with a SYN or ACK here and there.
pcapFile8 - .exe
pcapFile9 - .exe
pcapFile10 - unknown gibberish - with a SYN or ACK here and there.
pcapFile11 - unknown gibberish - with a SYN or ACK here and there.
pcapFile12 - unknown gibberish - with a SYN or ACK here and there.
pcapFile13 - unknown gibberish - with a SYN or ACK here and there.
pcapFile14 - unknown gibberish - with a SYN or ACK here and there.
The unknown files all look to be the same file, except for pcapFile7.
All files above removed, but the two pcap files at the root of the zip, sample1.pcap and sample2.pcap in the zip:
https://www.virustotal.com/#/file/9a137573c033ba4a8d922b03490224b4d3282798de488b15f91569d68d27d109/detection
All the files above removed, as well as the two sample pcaps removed (that are in there even if you did not run the tool on sample1/2.pcap yet):
https://www.virustotal.com/#/file/7ab6aaca9b185508a9491897a5250681912677de5adf13dcdbb4e1e96d040a0b/detection
I have it up and running on Windows 7 64 bit. I had to install the 64 bit version of Java to get it to work.
Hope this helps.
Update 2: Those files are related to what is under the tab downloaded files. There are 15 files in there too. This was found when I opened sample1.pcap.
Sample2.pcap took longer to run, and there were a lot more files under the download tab. When I went back to the DownloadedPCAPFiles\Files\ folder, there were a ton more files in there. 162 files to be exact (they overwrote my original 15 files). It seems these are extractions the tool has made, from the pcaps once processed.
Anonymous
Nov 19th 2018
7 years ago
The MalwareAnalysis\DownloadedPCAPFiles\Files\ directory should be checked and scrubbed each time after you process a PCAP file to ensure it remains clean.
Anonymous
Nov 29th 2018
7 years ago