DHL-themed malspam reveals embedded malware in animated gif
Introduction
On Wednesday 2018-08-01, @dvk01uk from myonlinesecurity.co.uk tweeted about a recent example of malicious spam (malspam) pushing malware (link to tweet). In recent weeks, this type of malspam has been pushing malware using the Agent Tesla keystroke logger. It looks like Agent Tesla is still involved with today's malspam, but this time, it's not so straight-forward. An Agent Tesla binary was found hiding in an animated gif.
Today's diary examines the malspam, infection traffic, and associated malware.
The email and my infected lab host
The email seems like a typical example of mass-distribution malspam. It has a spoofed sender's address, but it isn't very convincing as an actual DHL email. Header information follows:
- Received: from server.paperattention.com ([162.241.238.78])
- From: "DHL Express International " <[email protected]>
- Subject: Arrival Notice For BL - 01/08/2018 / Vessel - DHL ATLANTIC
- Date: 01 Aug 2018 18:07 UTC
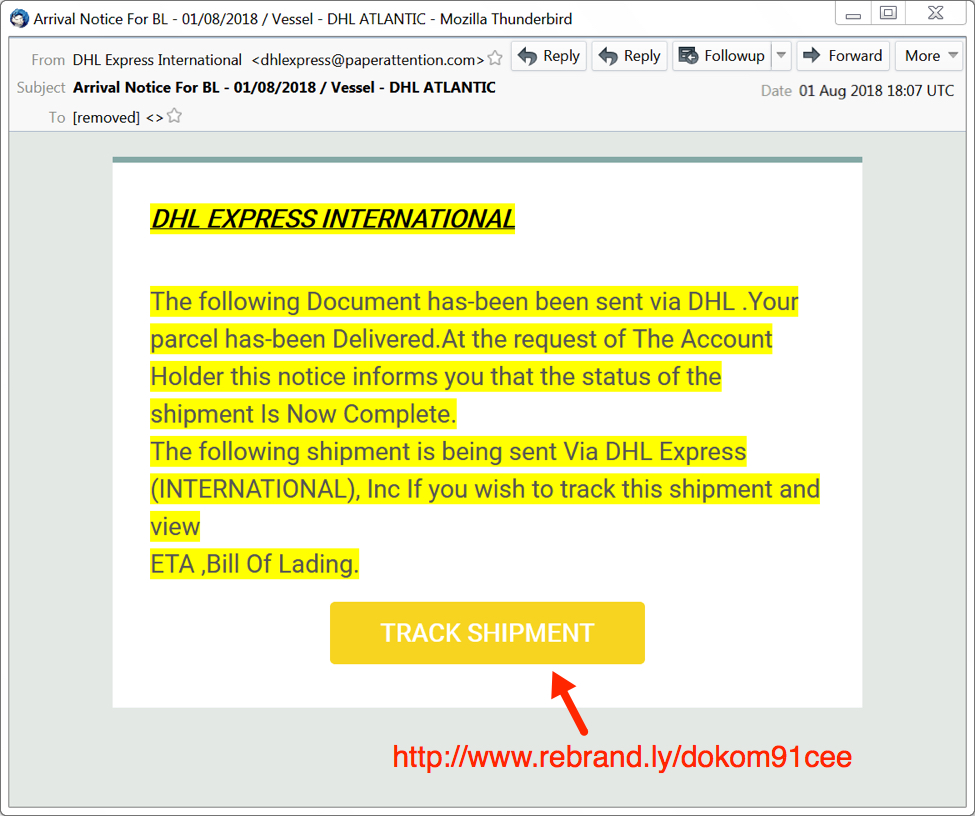
Shown above: Screenshot of the fake DHL email.
The link returned a zip archive that contained a file named "Arrival Notification.exe" which looks like "Arrival Notification" when the file extensions are hidden (a default setting for Microsoft Windows). In my lab host, double-clicking Arrival Notification.exe caused it to copy itself to the user's AppData\Roaming directory. This malware was made persistent through a script file in the Windows Startup folder.
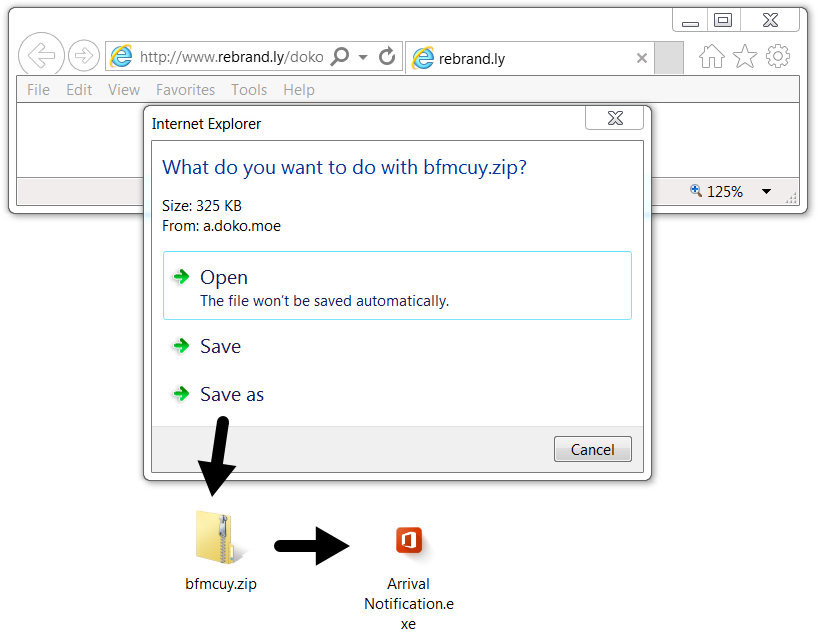
Shown above: Downloading malware from link in the email.
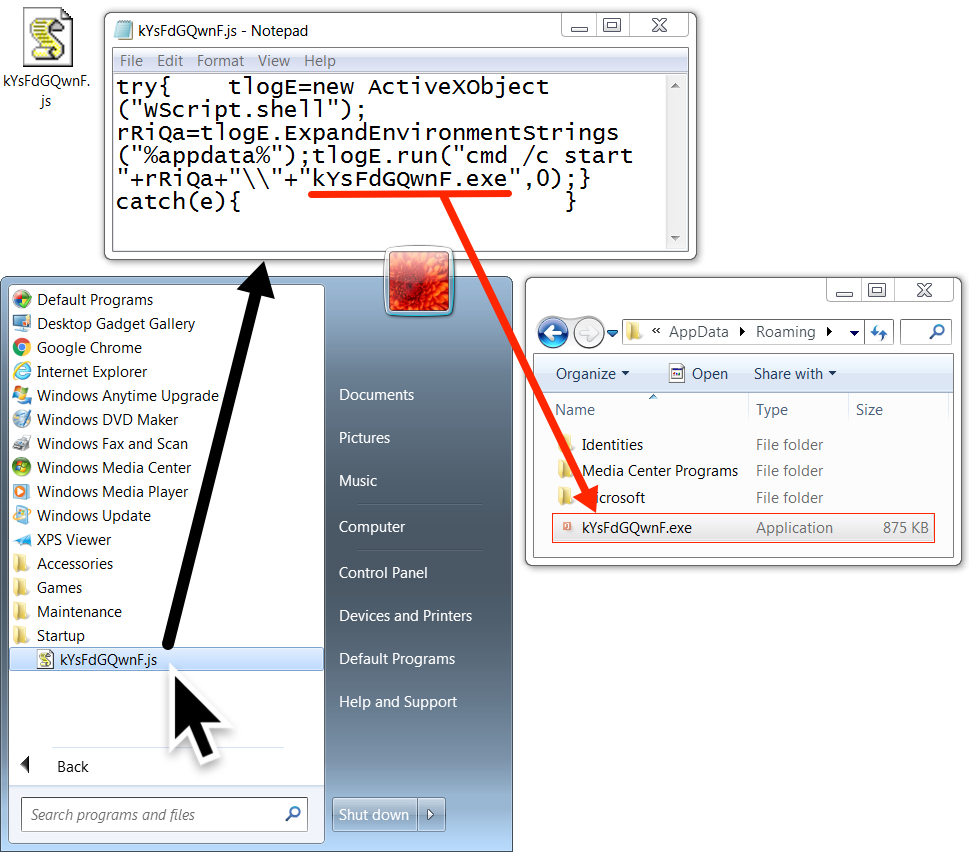
Shown above: Malware made persistent on my infected lab host.
The traffic
Network traffic consisted of the URL from the email, which redirected to a different URL to deliver the zip archive. After that, I saw an HTTP request to mydocuments1.is that returned an animated gif. The final line of infection traffic was an IP address check by my infected lab host to checkip.dyndns.org.
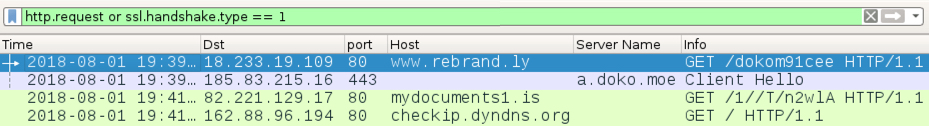
Shown above: Traffic from the infection filtered in Wireshark.
IP address checks may be suspicious, but they are not inherently malicious. My suggested block list based on this infection traffic is:
- hxxp://www.rebrand.ly/dokom91cee
- hxxps://a.doko.moe/bfmcuy.zip
- Any URL to mydocuments1.is
The animated gif
The HTTP request to mydocuments1.is returned an animated gif, which is somewhat strange. This gif was provided to Didier Stevens, who quickly found and extracted two malware binaries from it--a Windows EXE file and a Windows DLL file. According to Didier, the malware binaries were appended to the end of the gif. I reviewed the gif in a hex editor and found the PE headers for both files. It was pretty easy to carve out the binaries based on that.
Shown above: An animated gif of me reviewing the animated gif in a browser (I call it "gifception").
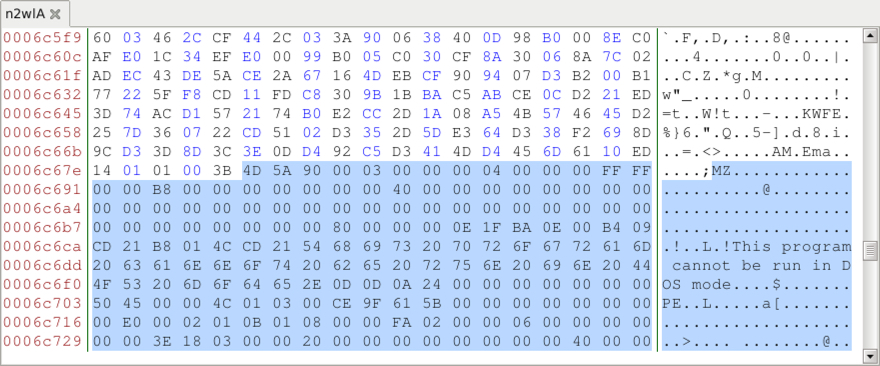
Shown above: Reviewed the gif in a hex editor and found the start of the 1st malware binary.
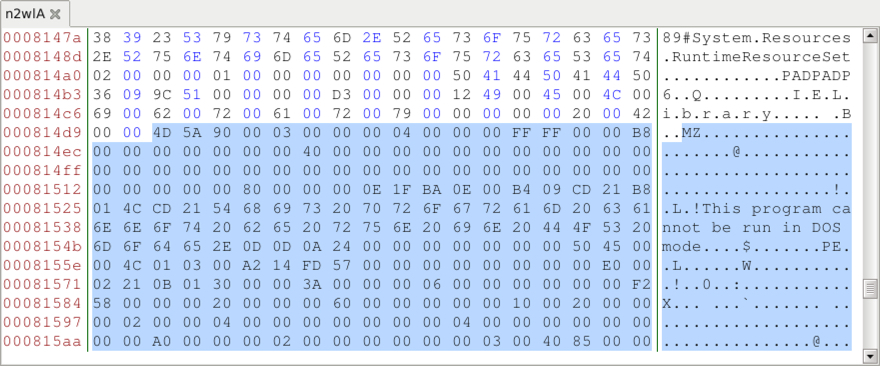
Shown above: Start of the 2nd malware binary when reviewing the gif in a hex editor.
Malware and artifacts
The following files are associated with this infection:
SHA256 hash: 7a8e7f7cd18c0f9e74c36fb792b46ca67a20e0851caa4a21a0f341debc23e7d9
File size: 333,431 bytes
File name: bfmcuy.zip
File location: hxxps://a.doko.moe/bfmcuy.zip
File description: Zip archive downloaded from link in the malspam
SHA256 hash: a486a258a822173a9e621252853b8eea343d20946252042b28d454aa6db98fe4
File size: 895,488 bytes
File name: Arrival Notification.exe
File location after executing: C:\Users\[username]\AppData\Roaming\kYsFdGQwnF.exe
File description: Malware from the downloaded zip archive
SHA256 hash: 96834c98d7c9e58068e78e4f4bf755a87c9c44655b4b2b4097ffc83aa3c61a3d
File size: 176 bytes
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\kYsFdGQwnF.js
File description: Script file in Windows Startup folder to keep malware persistent after reboot
SHA256 hash: 9dea34a4df20f3e2392f92d2f26dad88ba66827269431aa824c9aa8a0b80289b
File size: 641,155 bytes
File location: hxxp://mydocuments1.is/1//T/nw2lA
File description: Animated gif with 2 items of embedded malware
SHA256 hash: 81e882a394af440cea06cb490105efd721ffba30ca88ea92573d2f9ef27d2c86
File size: 197,120 bytes
File description: First file extracted from the animated gif - Windows EXE
SHA256 hash: fda201abced38c6cb1bfb82e0e42f6e48709d5dd8c8a738a4d2d47128464afcc
File size: 109,992 bytes
File description: Second file extracted from the animated gif - Windows DLL
Final words
Outside of the embedded malware in the animated gif, I couldn't find anything unusual in my lab setup. I could not find either items of malware extracted from the gif in my infected lab host, and I didn't see any Agent Tesla-specific traffic during the infection.
Criminals have embedded malware in images before, so this is not a new trick. Still, I don't commonly run into this technique among the mass-distribution malware I frequently see. Embedding malware in an animated gif might provide a way to avoid detection by security solutions. As I write this, the gif shows a detection ratio of 3 / 58 in VirusTotal.

Shown above: Low detection rate in VirusTotal for gif with embedded malware.
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
A pcap of the infection traffic, associated malware, and the email example for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
https://myonlinesecurity.co.uk/fake-dhl-arrival-notice-or-shipment-notice-delivers-malware-via-embedded-exe-files-inside-mp3-music-files/
Anonymous
Aug 6th 2018
7 years ago