Binary analysis with Radare2
When I need to do a quick binary analysis, Radare2 is my framework of choice. Radare2 consists of multiple tools that will assist you during analysis:
| r2 | primary tool and used for static analysis and interactive debugging |
| radiff2 | unified binary diffing util, if you need to find out differences between versions of binaries, this tool is much of help. |
| rabin2 | shows all kind of information on imports, sections headers etc and many different file formats |
| rax2 | mathematical expression evaluator for all kind of conversions |
| ragg2 | compile programs written in a simple high-level language into tiny binaries |
| rafind2 | find byte patterns in files |
| rasm2 | command line assembler and disassembler tool for multiple architectures |
| rahash2 | supports a large number of hashing algorithms and functions on strings and files |
| rarun2 | launcher for running programs in different environments with options for scripting and redirecting in- and output, |
| cutter | Qt based Gui for Radare2 |
Radare2 runs on many platforms, supports local native and remote debugging, many architectures, advanced scripting (python, javascript, go, etc), patching, code (block) emulation and analysis. Each of the tools deserves an individual post, but I'll highlight a few features which I use often.
Converting and evaluating expressions using rax2, converting test into its hex value.
$ rax2 -S test
74657374
Generating hashes for 38 algorithms at once, using rahash2.
$ rahash2 -a all ./traur.bin
./traur.bin: 0x00000000-0x000373ff md5: edccfe5ef48de6b0f3bbf53cc1012533
Upload.exe: 0x00000000-0x0007d8cf sha1: 6e24eb2ad12990b617b2287aedd57ba5686a85f6
Upload.exe: 0x00000000-0x0007d8cf sha256: eb9553ddb141d5281b49dac4b50a6f626902c4e14dc3532fafb737f85e667915
Upload.exe: 0x00000000-0x0007d8cf sha384: 911dc5810ecf6e8c5fc77f7b05f25ef74e4e276589675ad8c7b2c90d04af25321a4ef58f33798f976ba87b6194d6dc08
Upload.exe: 0x00000000-0x0007d8cf sha512: cc5d1907c897d46b77dda8fb44da6585147079402ad5d3f36a577f6a6e83aa5a2d02eef7a52e38319a4c56d29abe518f9b7a7ecfd8d2bcd70a376790177d97e6
Upload.exe: 0x00000000-0x0007d8cf md4: 387c58ff2ac57565706e9c1bd0543578
Upload.exe: 0x00000000-0x0007d8cf xor: 74
....
A quick assessment of a binary using rabin2:
$ rabin2 -I ./Upload.exe
arch x86
binsz 514256
bintype pe
bits 32
canary false
class PE32
cmp.csum 0x000894e8
compiled Fri Apr 16 07:47:33 2010
crypto false
endian little
havecode true
hdr.csum 0x00000000
linenum false
lsyms false
machine i386
maxopsz 16
minopsz 1
nx false
os windows
overlay true
pcalign 0
pic false
relocs true
signed false
static false
stripped true
subsys Windows GUI
va true
Extract string section information using rabin2:
$ rabin2 -z ./Upload.exe
000 0x00044c0a 0x004bb20a 5 12 (.rsrc) utf16le SOUND
001 0x00044c16 0x004bb216 6 14 (.rsrc) utf16le FINISH
002 0x00044c68 0x004bb268 4 5 (.rsrc) ascii }}}K
Extract imports using rabin2:
$ rabin2 -i ./Upload.exe
[Imports]
1 0x004c37ac NONE FUNC KERNEL32.DLL_LoadLibraryA
2 0x004c37b0 NONE FUNC KERNEL32.DLL_GetProcAddress
3 0x004c37b4 NONE FUNC KERNEL32.DLL_VirtualProtect
4 0x004c37b8 NONE FUNC KERNEL32.DLL_VirtualAlloc
5 0x004c37bc NONE FUNC KERNEL32.DLL_VirtualFree
...
Disassembly of entry0 using r2:
$ r2 ./Upload.exe
-- Can you stand on your head?
[0x004ba3c0]> aaaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze function calls (aac)
[x] Analyze len bytes of instructions for references (aar)
[x] Emulate code to find computed references (aae)
[x] Analyze consecutive function (aat)
[x] Constructing a function name for fcn.* and sym.func.* functions (aan)
[x] Type matching analysis for all functions (afta)
[0x004ba3c0]> pd
;-- eip:
/ (fcn) entry0 436
| entry0 ();
| 0x004ba3c0 60 pushal
| 0x004ba3c1 be00604700 mov esi, 0x476000 ; section.UPX1
| 0x004ba3c6 8dbe00b0f8ff lea edi, [esi - 0x75000]
| 0x004ba3cc 57 push edi
| ,=< 0x004ba3cd eb0b jmp 0x4ba3da
| 0x004ba3cf 90 nop
| | ; CODE XREF from 0x004ba3e1 (entry0)
Find the differences between two binaries using radiff2.
$ radiff2 -g main /bin/true /bin/false | xdot -
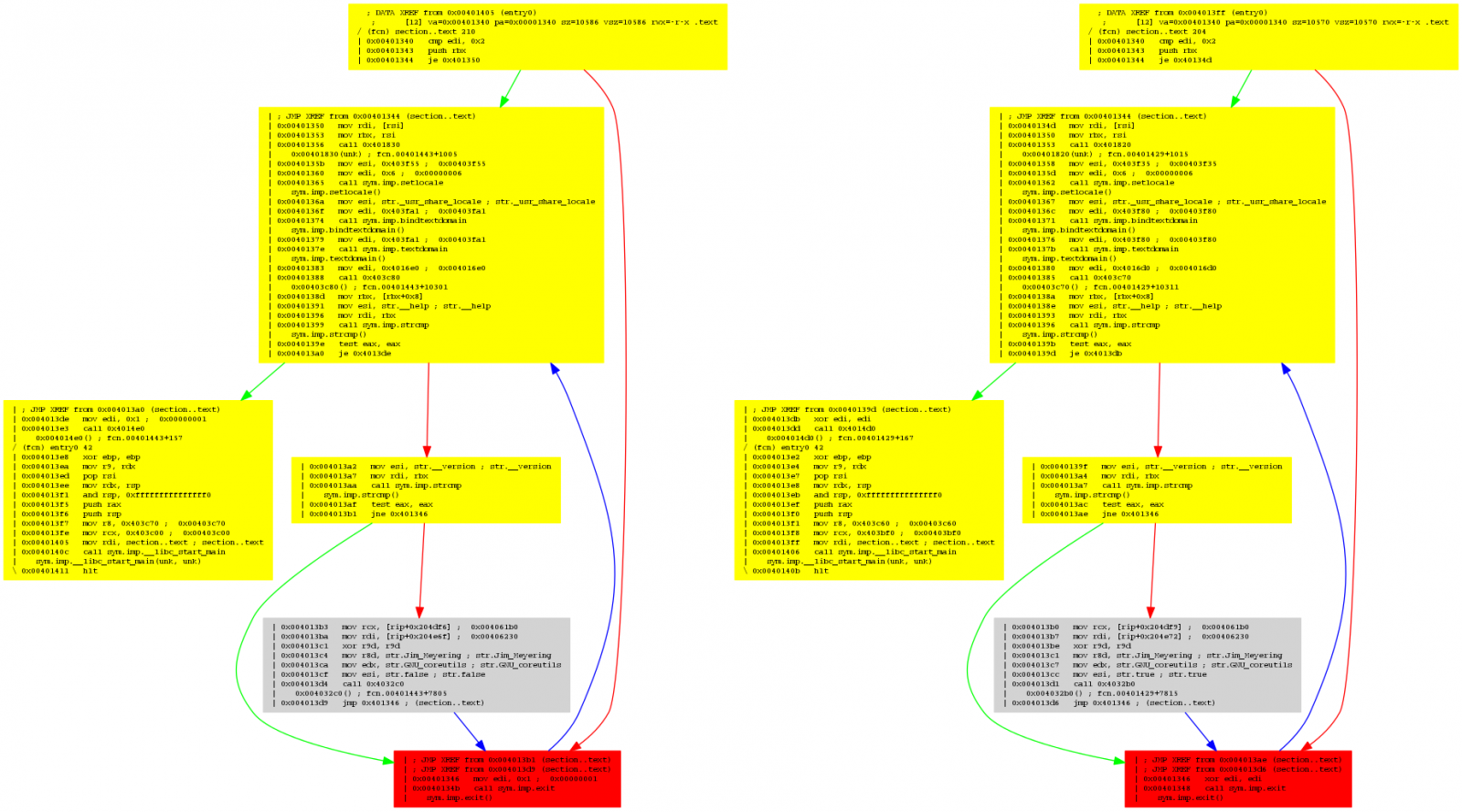
Cutter is the Qt based GUI of Radare2.

When you want to get started, it is being advised to use Radare2 from Docker or source.
References
* http://radare.org/
* http://radare.today/
* https://github.com/radareorg/cutter
* https://radare.gitbooks.io/radare2book/
* https://radare.gitbooks.io/radare2book/content/radiff2/binary_diffing.html
* https://www.megabeets.net/a-journey-into-radare-2-part-1/


Comments