It is a resume - Part 2
In part 2, we are going to take a closed look at the image in object 3.
First we dump the stream and look at the beginning and end:
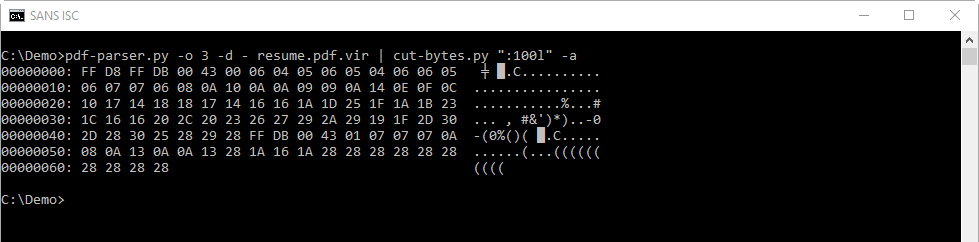
FF D8 is the Start Of Image Marker of a JPEG image.
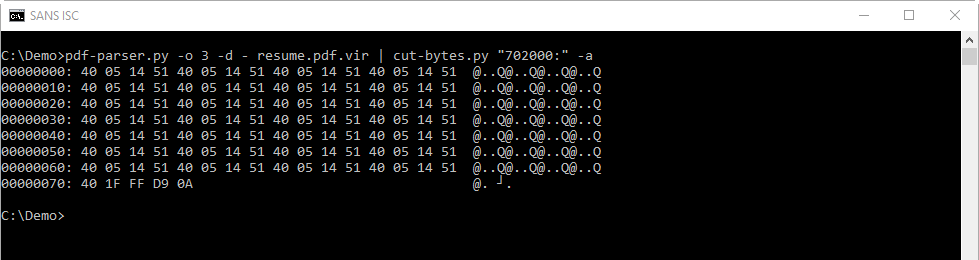
FF D9 is the Eod Of Image Marked of a JPEG image.
It's likely that we are indeed dealing with a JPEG image, and not something else.
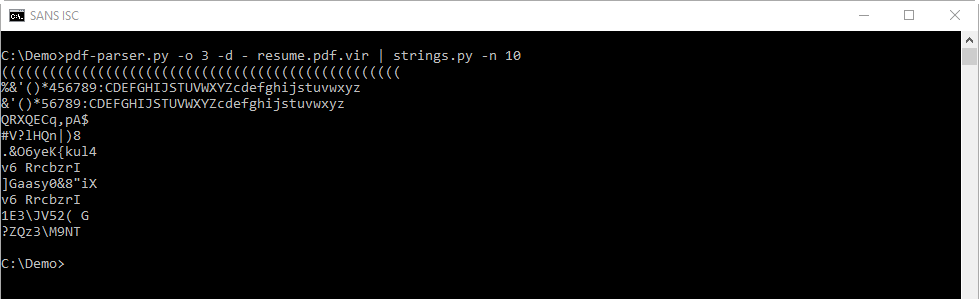
Next I check if I can find strings inside the JPEG image:
With my maldoc YARA rules (maldoc.yara found in the oledump.py ZIP package) I can search for shellcode:
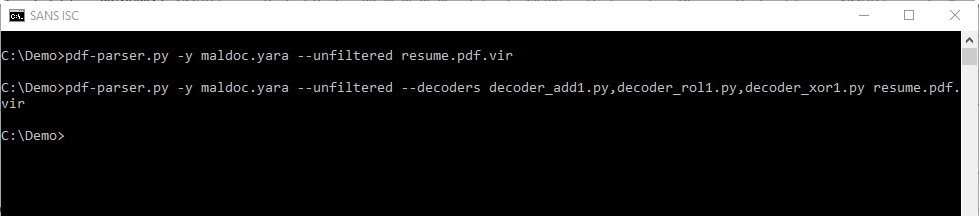
The first line will scan the raw stream (the JPEG image) with YARA and the rules we provided (maldoc.yara).
The second line will perform the same scan, but with decoders to see if the shellcode is encoded with simple encoding techniques (XOR 1 byte, ADD 1 byte and ROL 1 byte).
There is no output from these commands, the YARA rules don't trigger: this means we can't find shellcode inside the image. This does not necessarily mean there is no shellcode, but that we can't find any...
In part 3, we'll take a deeper look...
Didier Stevens
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments