Massive wave of ransomware ongoing
For an updated summary, see: WannaCry/WannaCrypt Ransomware Summary
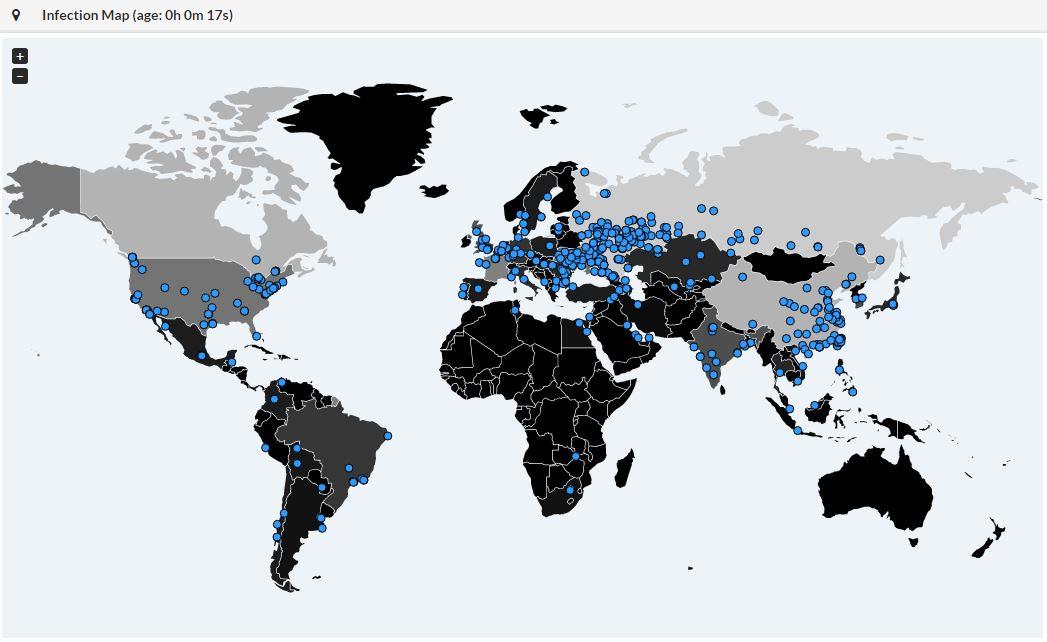
For a few hours, bad news are spreading quickly about a massive wave of infections by a new ransomware called "WannaCry". We are still trying to collect more information about it. It seems that 45K attacks were detected from 74 differents countries:
Big targets have been telecom operators (ex: Telefonica in Spain) and hospitals in UK. Once the malware has infected a computer, it spreads across the network looking for new victims using the SMB protocol.
The ransomware uses the Microsoft vulnerability MS17-10[1]. (This vulnerability was used by ETERNALBLUE[2])
Here are some IOC's that we already collected:
SHA256:
- 09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
- 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
- 2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41dd
- 2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d
- 4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
SHA1:
- 45356a9dd616ed7161a3b9192e2f318d0ab5ad10
- 51e4307093f8ca8854359c0ac882ddca427a813c
MD5:
- 509c41ec97bb81b0567b059aa2f50fe8
- 7bf2b57f2a205768755c07f238fb32cc
- 7f7ccaa16fb15eb1c7399d422f8363e8
File extension: .wncry
Ransomware notification: @[email protected]
Emerging threats has an IDS rule that catches the ransomware activity: (ID: 2024218)
alert tcp $HOME_NET 445 -> any any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response"; flow:from_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:2;)
Until now, the best protection is of course to patch your systems as soon as possible and keep your users aware of the new ransomware campaign to preven them to open suspicious emails/files.
[1] https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
[2] https://isc.sans.edu/forums/diary/ETERNALBLUE+Windows+SMBv1+Exploit+Patched/22304/
We will update this diary with more information if available.
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
flowbits:isset,ETPRO.ETERNALBLUE;
Do you have the other rule that sets the ETERNALBLUE flowbit?
Anonymous
May 12th 2017
8 years ago
Anonymous
May 12th 2017
8 years ago
alert smb any any -> $HOME_NET any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Request (set)"; flow:to_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 18 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:set,ETPRO.ETERNALBLUE; flowbits:noalert; classtype:trojan-activity; sid:2024220; rev:1;)
alert smb $HOME_NET any -> any any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response"; flow:from_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:1;)
Anonymous
May 12th 2017
8 years ago
https://www.hybrid-analysis.com/sample/ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa?environmentId=100
Anonymous
May 13th 2017
8 years ago
Open this domain, www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
It is a killswitch for the worm. If the malware finds it, is shuts down. Malwarebytes figured it out and bought the name and setup the site.
Expect a new variant yet this weekend, that bypasses this flaw.
Anonymous
May 13th 2017
8 years ago
Anonymous
May 13th 2017
8 years ago
https://www.theguardian.com/technology/2017/may/13/accidental-hero-finds-kill-switch-to-stop-spread-of-ransomware-cyber-attack?CMP=fb_gu
Anonymous
May 13th 2017
8 years ago
intitle:"Index of" "WNCRY"
returns a couple of dozen systems, some that are displaying things like:
404.html.bak.WNCRY, 2017-03-18 23:19, 616. [TXT], @[email protected], 2017-05-12 22:52, 933. [ ], @[email protected], 2017-05-12 02:22, 240K.
I haven't been brave enough to actually click any of the links, though...
Anonymous
May 13th 2017
8 years ago
In addition to this: use Software Restriction Policies to stop the PRIMARY attack vector, i.e. deny execution of anything your users can write/create (unless installed into a safe directory where only an administrator can write).
Anonymous
May 13th 2017
8 years ago
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
(Microsoft) Customer Guidance for WannaCrypt attacks
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
We are working with customers to provide additional assistance as this situation evolves, and will update this blog with details as appropriate.
Phillip Misner, Principal Security Group Manager Microsoft Security Response Center
Further resources:
Download English language security updates: Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86, Windows XP SP2 x64,Windows XP SP3 x86, Windows XP Embedded SP3 x86, Windows 8 x86, Windows 8 x64
Download localized language security updates: Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86, Windows XP SP2 x64,Windows XP SP3 x86, Windows XP Embedded SP3 x86, Windows 8 x86, Windows 8 x64
General information on ransomware: https://www.microsoft.com/en-us/security/portal/mmpc/shared/ransomware.aspx
MS17-010 Security Update: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
MS17-010: Security update for Windows SMB Server: March 14, 2017
Including Windows 10
https://support.microsoft.com/en-us/help/4013389/title
http://www.trymytools.com/how-to-remove-wannacryptor-ransomware-and-decrypt-files/
Anonymous
Jun 8th 2017
8 years ago