Performing network forensics with Dshell. Part 1: Basic usage
by Manuel Humberto Santander Pelaez (Version: 1)
I found out recently there is a very interesting tool that enables some interesting capabilities to perform network forensics from a PCAP capture file. It's named Dshell and it was released in December 2014 by the United States Army Research Labs (ARL). Its purpose is to easy develop plugins to support the dissection of network packet captures and decode possible unknown malicious protocols.
This is the first part of a three-diary-set. I will show the following in each part:
- Part 1: Basic usage
- Part 2: Decoder development process
- Part 3: Practical cases
You can download it from https://github.com/USArmyResearchLab/Dshell and easily follow the installation instructions. You can launch the framework by typing dshell in the command prompt. There is a major keyword that launches the decoding framework and it's called decode. Let's see the available options:
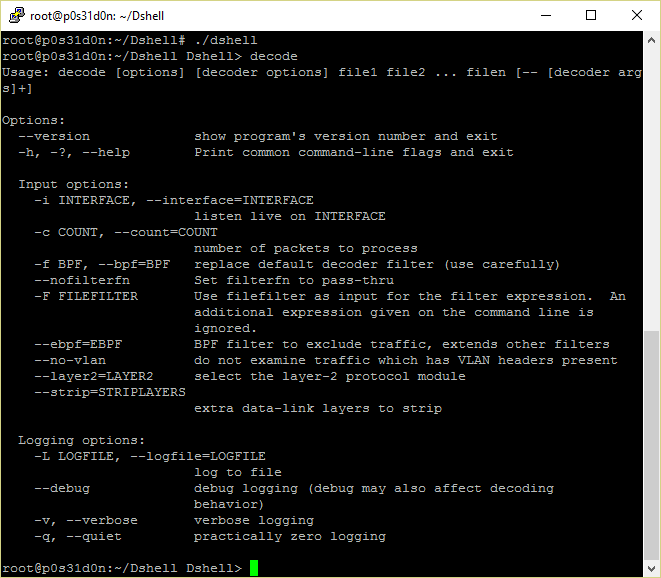
As you can see, usage is pretty simple. The following decoders are available to use in the decoder options command section:
- DNS: Decoder that extracts and summarize DNS queries:
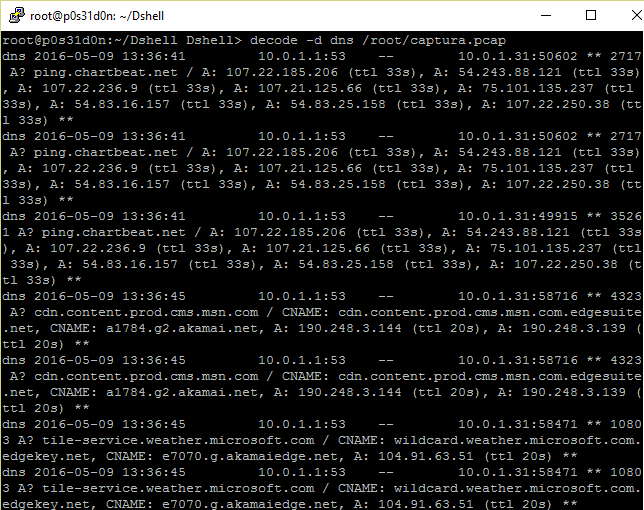
- httpdump: Decoder that shows the direction of the traffic being sent in http protocol, the verb used, industry of the server IP address and additional information where available:
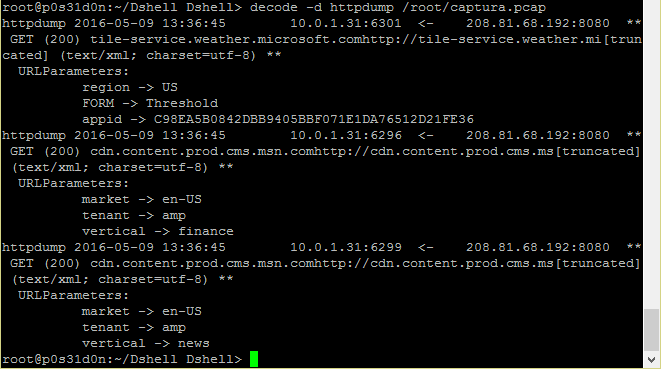
- Netflow: Decoder that is able to tell the direction of the traffic being sent in the network.
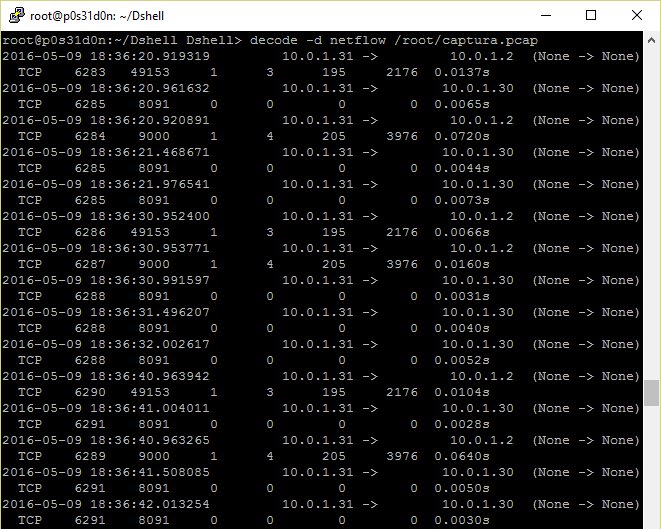
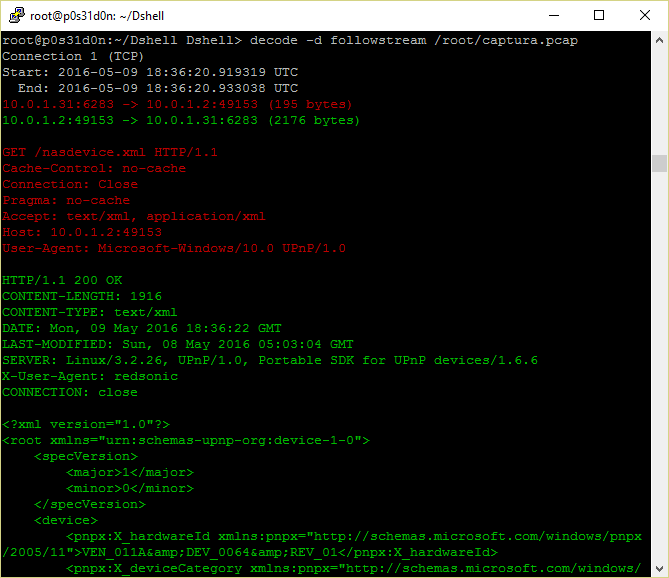
- followstream: Decoder that performs similar function as the follow stream feature in wireshark, showing all the data being transferred in a network connection.
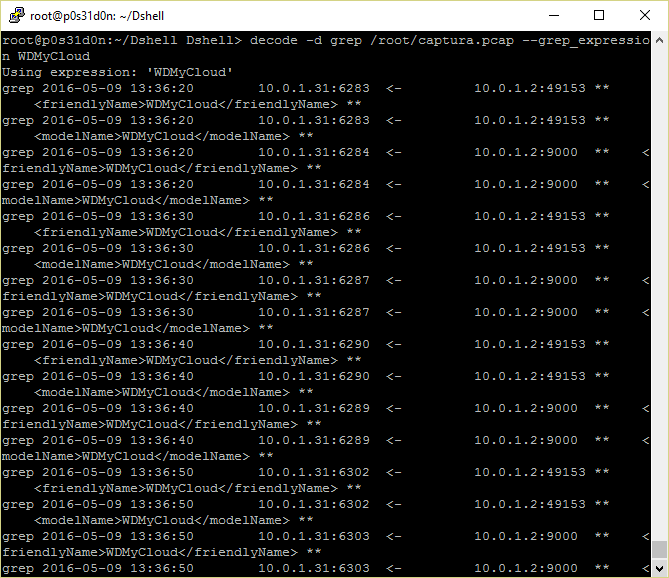
- grep: Decoder that is able to perform expression search inside the packet capture, similar to ngrep:
I'm sure you will find useful the options I just showed. Stay tuned for the next two parts ;)
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments
Anonymous
May 10th 2016
9 years ago