First Exploit Attempts For Juniper Backdoor Against Honeypot
Just a quick update: We do continue to see an increasing trend in login attempts to our honeypot using the backdoor password. If anybody has a vulnerable device to "donate", I would like to send some of that traffic to it (need it to be accessible in an isolated network. Do not need it shipped :) ).
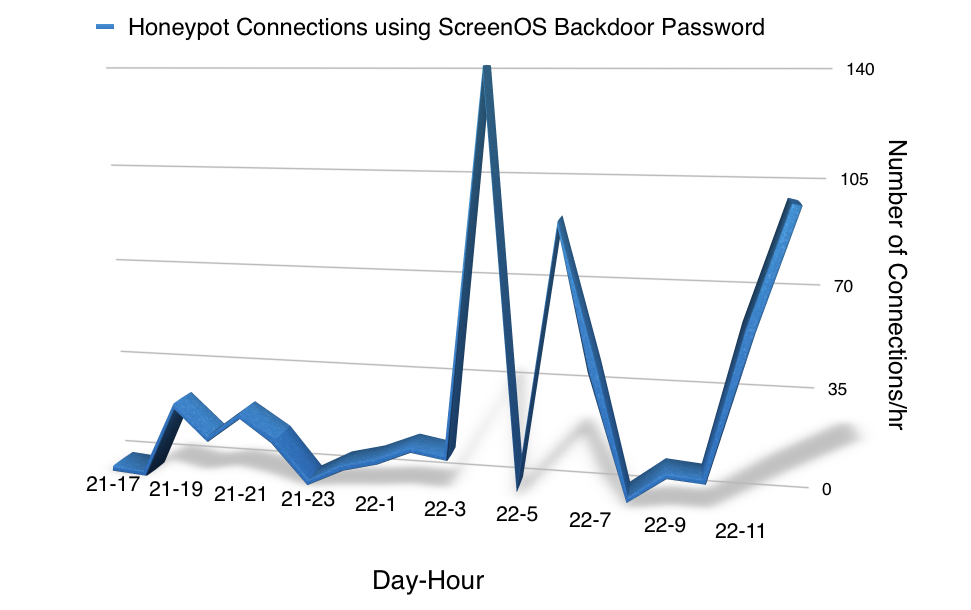
We are detecting numerous login attempts against our ssh honeypots using the ScreenOS backdoor password. Our honeypot doesn't emulate ScreenOS beyond the login banner, so we do not know what the attackers are up to, but some of the attacks appear to be "manual" in that we do see the attacker trying different commands.
We saw the first attempt at 17:43:43 UTC about an hour after I adjusted the kippo honeypot to return the Netscreen banner.
The most popular usernames so far:
+---------------+----------+ | username | count(*) | +---------------+----------+ | root | 29 | | admin | 18 | | netscreen | 8 | | login | 8 | | administrator | 5 | | test | 4 | | system | 2 | | bob | 1 | | sdes | 1 | | sqzeds | 1 | | sqzds | 1 | +---------------+----------+
The most frequent source IPs for this attack so far:
+-----------------+----------+ | ip | count(*) | +-----------------+----------+ | 83.82.244.85 | 24 | | 84.104.21.148 | 8 | | 176.10.99.201 | 7 | | 88.169.13.26 | 7 | | 76.18.66.48 | 5 | | 64.39.109.5 | 4 |<- Qualys (probably "research") | 198.50.145.72 | 4 | | 2.239.22.90 | 4 | | 86.195.19.248 | 4 | | 80.123.56.190 | 3 | | 64.39.108.99 | 2 | | 79.120.10.98 | 2 | | 62.42.12.8 | 1 | | 192.99.168.52 | 1 | | 94.210.22.151 | 1 | | 174.114.144.109 | 1 | +-----------------+----------+
Based on hour of day (UTC, Dec. 20th)
+------+----------+ | hour | count(*) | +------+----------+ | 17 | 1 |<- honeypot was adjusted 16:55 to return Netscreen banner | 19 | 25 | | 20 | 14 | | 21 | 23 | | 22 | 15 | +------+----------+
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Dec 22nd 2015
1 decade ago
t.ourVersionString = 'SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.3'
and change it to
t.ourVersionString = 'SSH-2.0-NetScreen'
then restart kippo.
Anonymous
Dec 22nd 2015
1 decade ago
ssh_version_string = SSH-2.0-NetScreen
Anonymous
Dec 22nd 2015
1 decade ago
I don't see any attempts against those accounts in your post.
Anonymous
Dec 23rd 2015
1 decade ago
Anonymous
Jan 4th 2016
1 decade ago