Another example of Angler exploit kit pushing CryptoWall 3.0
Introduction
Angler exploit kit (EK) has been evolving quite a bit lately. Recently, this EK has been altering its URL patterns on a near-daily basis. The changes accumulate, and you might not recognize current traffic generated by Angler. After two weeks of vacation, I almost didn't recognize it. This diary provides two traffic examples of Angler EK as we enter July 2015.
Angler EK still pushing a lot of CryptoWall 3.0
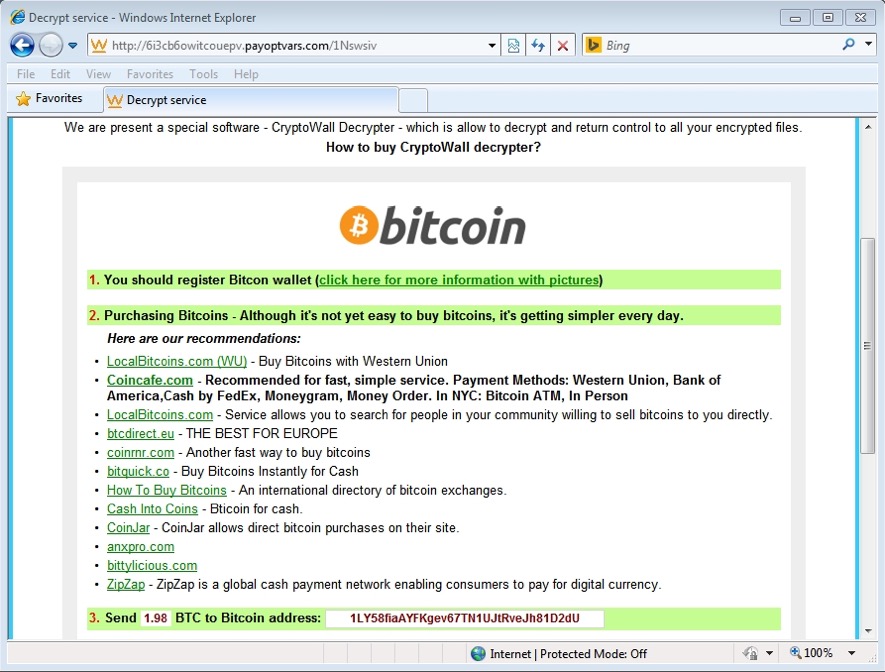
Angler pushes different payloads, but we're still seeing a lot of CryptoWall 3.0 from this EK. We first noticed CryptoWall 3.0 from Angler near the end of May 2015 [1], and we've seen a great deal of it since then [2]. The CryptoWall 3.0 sample for today's diary used 1LY58fiaAYFKgev67TN1UJtRveJh81D2dU as a bitcoin address for the ransom payment.
Traffic examples
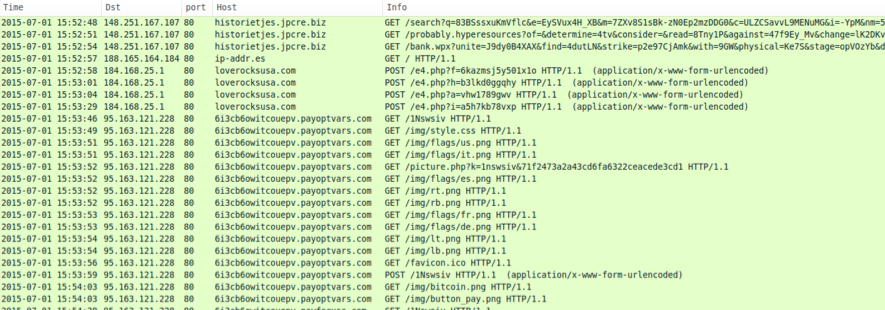
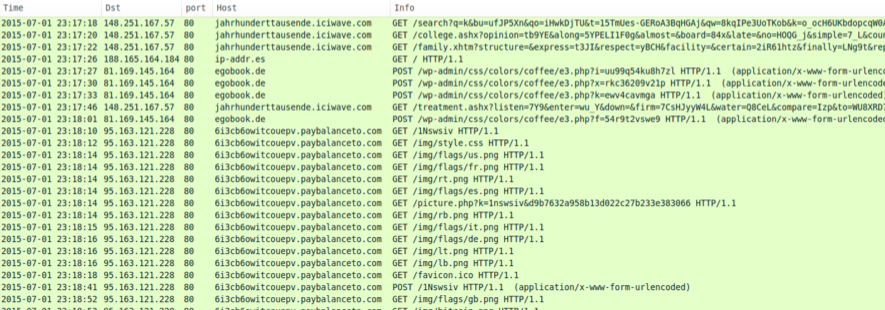
Traffic from Tuesday, 2015-07-01 shows Angler EK from 148.251.167.57 and 148.251.167.107 at different times during the day. Click on the images below for a full-size view of the associated HTTP traffic from the infected Windows hosts.
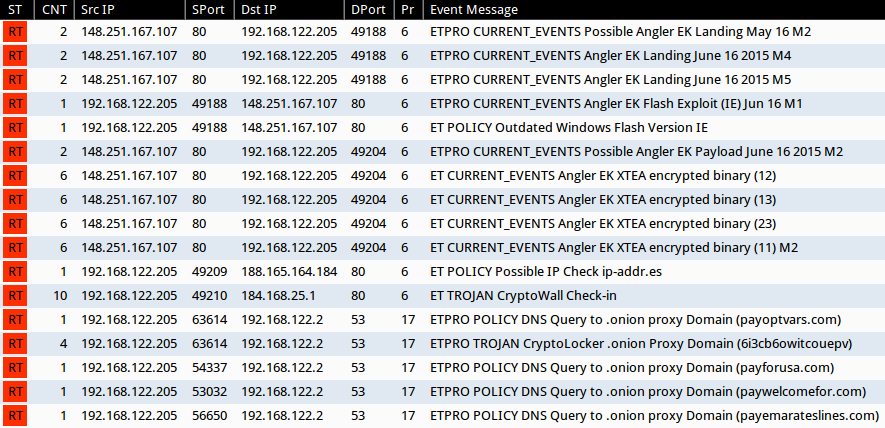
The people at Emerging Threats do a good job of keeping their Snort-based signatures up-to-date through their ETOpen and Proofpoint ET Pro rulesets. Below is an image of events from the infection traffic I saw using Suricata on Security Onion.
Preliminary malware analysis
Sample of a CryptoWall 3.0 malware payload delivered by Angler EK on 2015-07-01:
- File size: 240.0 KB ( 245760 bytes )
- MD5 hash: f52679c115377e42943b0427d968f891
- Detection ratio: 4 / 55
- First submitted: 2015-07-01 23:01:15 UTC
- https://www.virustotal.com/en/file/2dfd43d6776b5712e5fd9d82d3a6b5d0097d2b9371915539ed0b88f4097224a8/analysis/
- https://malwr.com/analysis/ZGYzOTljNGZjY2M1NDliY2FkY2YzNzcxYTQ4OWI4NGQ/
- https://www.hybrid-analysis.com/sample/2dfd43d6776b5712e5fd9d82d3a6b5d0097d2b9371915539ed0b88f4097224a8?environmentId=1
Final words
Pcap files of the 2015-07-01 infection traffic are available at:
- http://www.malware-traffic-analysis.net/2015/07/01/2015-07-01-Angler-EK-sends-CryptoWall-3.0-traffic-example-1.pcap
- http://www.malware-traffic-analysis.net/2015/07/01/2015-07-01-Angler-EK-sends-CryptoWall-3.0-traffic-example-2.pcap
A zip file of the associated malware is available at:
The zip file is password-protected with the standard password. If you don't know it, email [email protected] and ask.
---
Brad Duncan
ISC Handler and Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/diary/Angler+exploit+kit+pushing+CryptoWall+30/19737
[2] https://isc.sans.edu/diary/Increase+in+CryptoWall+30+from+malicious+spam+and+Angler+exploit+kit/19785


Comments
Anonymous
Jul 3rd 2015
1 decade ago
Anonymous
Jul 3rd 2015
1 decade ago