Checking for BACNet devices inside corporate networks
by Manuel Humberto Santander Pelaez (Version: 1)
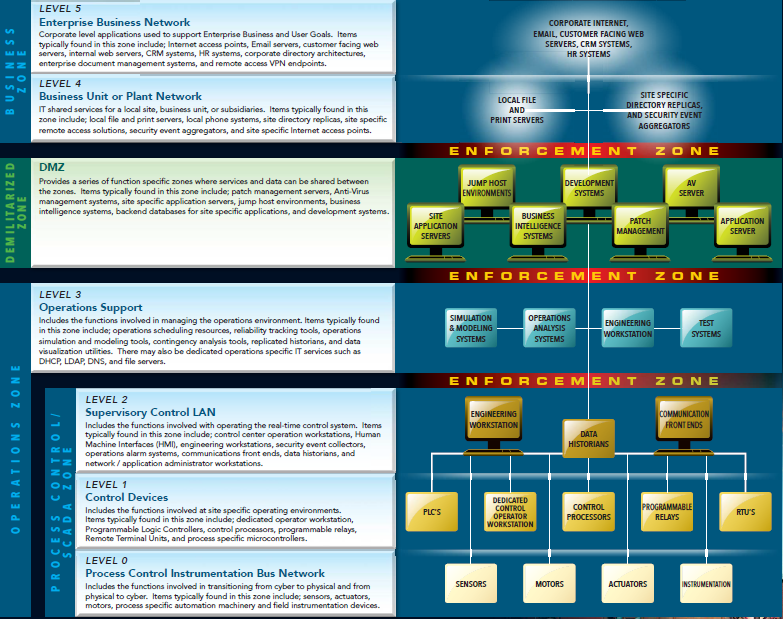
Building automation Networks are very common today for intelligent buildings. They interconnect several type of devices like escalators, elevators, power circuits, heating, ventilating and air conditioning (HVAC) to the main control center. Since those devices are in the same location as computers and all other corporate devices, some companies place them in same network segments with all other user's devices. This could lead to a serious security problem, as it is wide known that many industrial protocols does not require the clients to authenticate for issuing commands or requesting data. If companies combine BACnet devices inside network segments with regular users, they will be able to attack the BACnet devices with no difficult. Only new version of those protocols are beginning to support authentication, confidentiality and integrity. It's important to follow the Purdue security model and separate building automation network devices from all other segments of the corporate network(check https://ics.sans.org/resources/ics-security-resource-poster):
BACnet is one of those industrial protocols. With the new version release of nmap, there is a new script that is able to check for devices supporting the BACnet protocol stack and gathers all possible information from it (vendor id, vendor name, instance number, firmware, application software, object name, model name, description and location).
Usage is pretty simple: since we need to target the BACnet port, a UDP scan must be launched to port 47808 of the target network segments where we are interested to locate BACnet devices (e.g. 10.90.1.0/24). The command to launch the script is nmap --script bacnet-info -sU -p 47808 10.90.1.0/24. If any BACnet device is located, you will see something analog to the following text:
47808/udp open bacnet
| bacnet-discover:
| Vendor ID: BACnet Stack at SourceForge (260)
| Vendor Name: BACnet Stack at SourceForge
| Instance Number: 260001
| Firmware: 0.8.2
| Application Software: 1.0
| Object Name: SimpleServer
| Model Name: GNU
| Description: server
|_ Location: USA
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments