A Malicious Word Document Inside a PDF Document
Yesterday Steve Basford informed us of yet another type of malicious document (Sales Invoice 519658.pdf MD5 bfe397fb9b7907ab34ba83f0f086336d). It is a PDF document, containing an embedded file, with JavaScript to extract the embedded file to a temporary folder and then open it. The embedded file is a malicious Word document like we've seen many of them the last months.
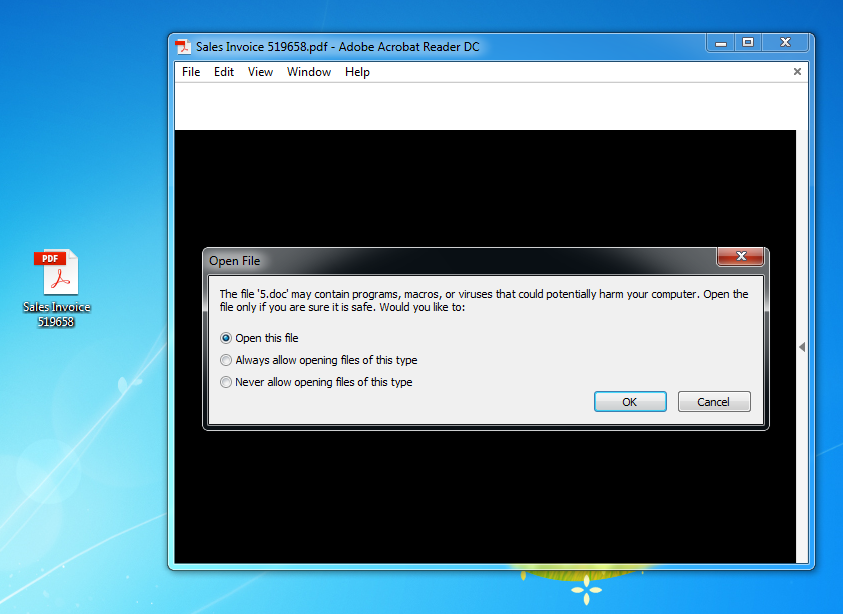
When you open this PDF file with Adobe Reader, you get a warning and the embedded file is only opened when you approve it.
You can analyze such PDFs without using Adobe Reader or Microsoft Word, but with my tools pdfid, pdf-parser and oledump.
If you want to know in detail how to do this, I have a video.
Keywords:
1 comment(s)
×
![modal content]()
Diary Archives


Comments
Have been disabling all active content for over ten years now, originally because only idiots ever use it and do so only for annoying content, primarily advertising. When maleware started arriving the coffin lid was nailed shut. Have not missed it even once in all that time.
For the .01% of users who embed Excel spreadsheets in Word documents, well they can generate a PDF to distribute when they're finished.
Instead of spending huge sums on IPS and being hacked regardless, organizations would be better served by disabling any and all forms of active content and permitting only whitelisted browser JavaScript, random sites be damned.
Microsoft, Adobe, et al have self-servingly chosen the wrong defaults and the typical home user will nevertheless be owned, especially the 10% that will click on any attachment and willfully click through a series of three for four warning screens much like IV drug users who share needles. Stupid is as stupid does.
Anonymous
Apr 25th 2015
1 decade ago