"Rocket Kitten": Is it still APT if you can buy it off the shelf?
Gadi Evron and Tillmann Werner presented an interesting case at 31C3 Conference in Hamburg yesterday, that shows how commercial software can be used to launch APT style attacks. In this case, several similar attacks where discovered against targets in Israel and Western Europe. In all cases, the attack started with a simple Excel spreadsheet which was sent as an attachment [1]. The email itself was brief and unremarkable, but used fake and plausible "From" headers.
Gadi was nice enough to share with us some screenshots of these attachments. They are all very plausible for the targeted recipients. Click on the thumbnail to see the full size image (these are images, not the original Excel files)
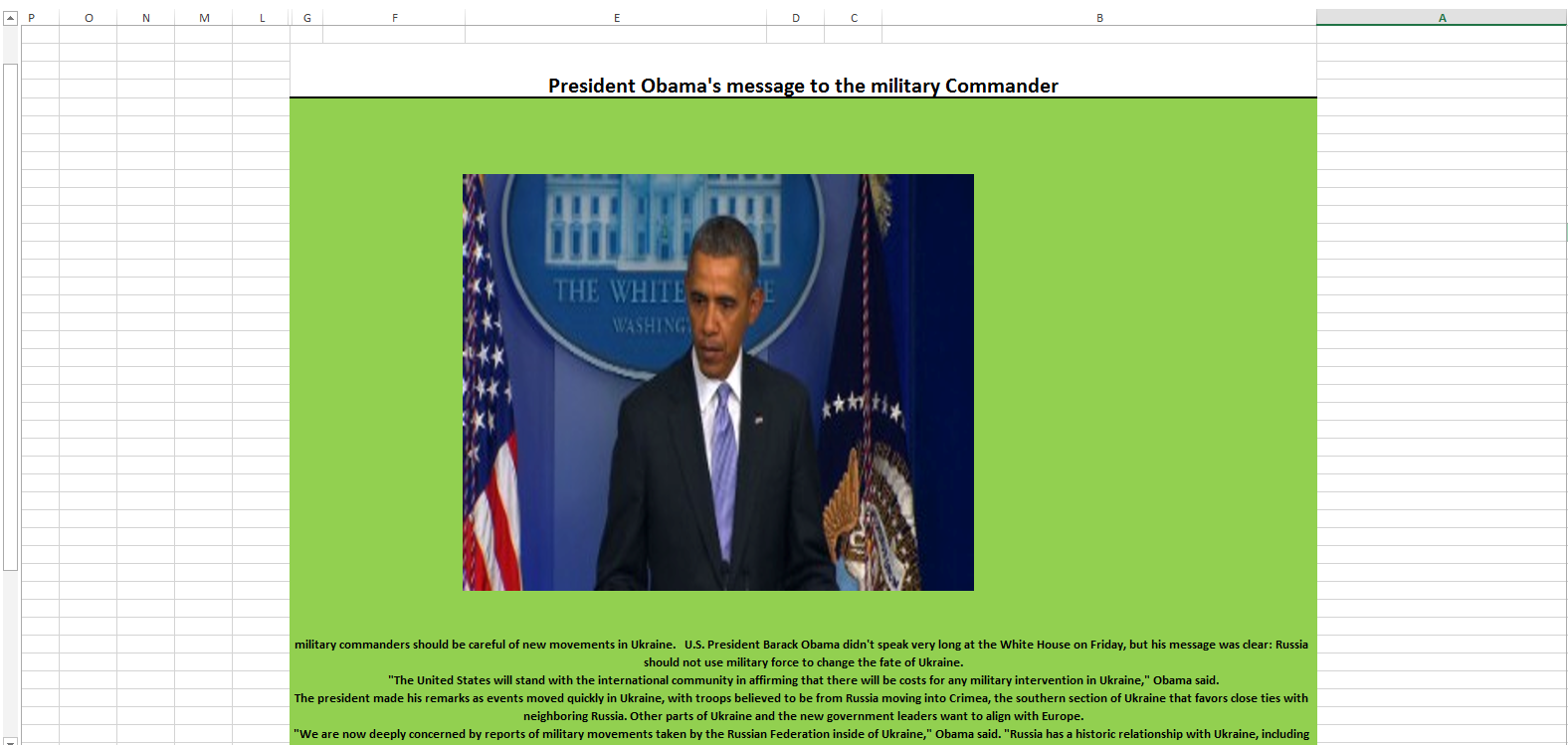 |
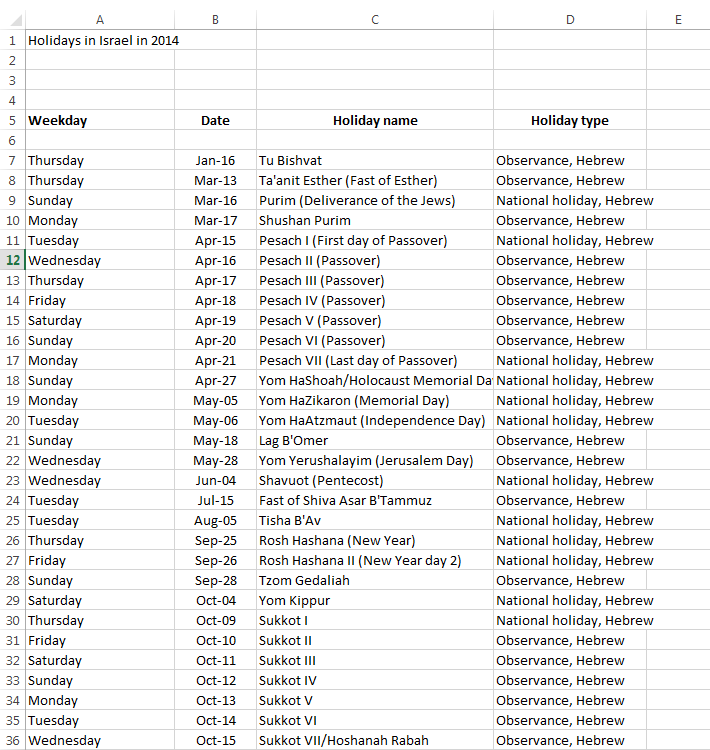 |
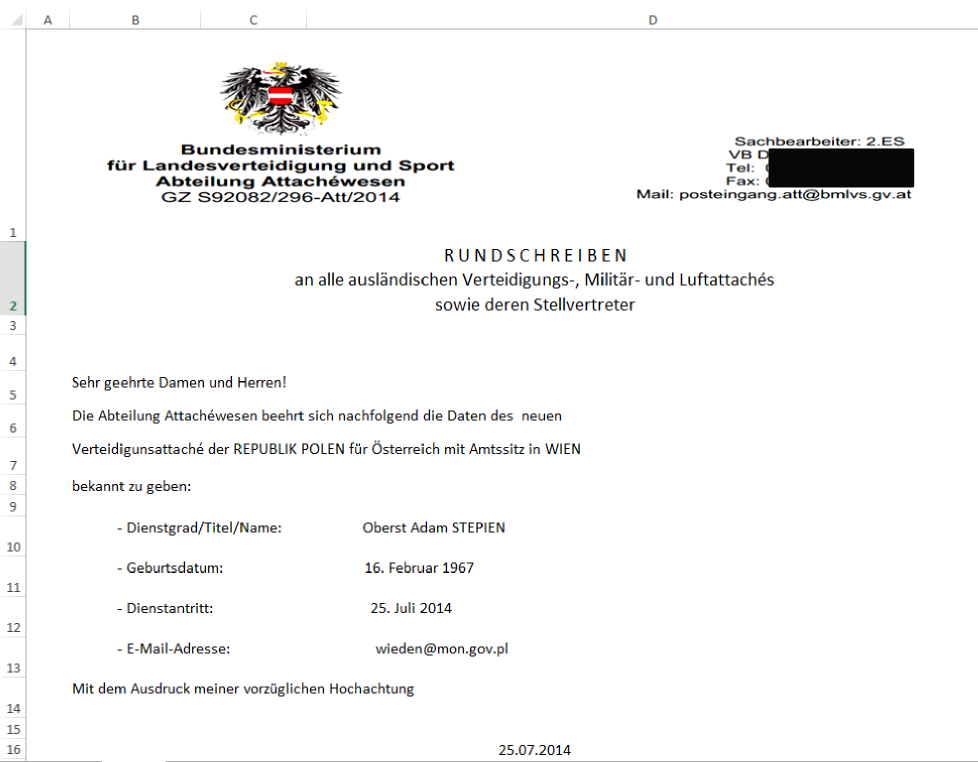 |
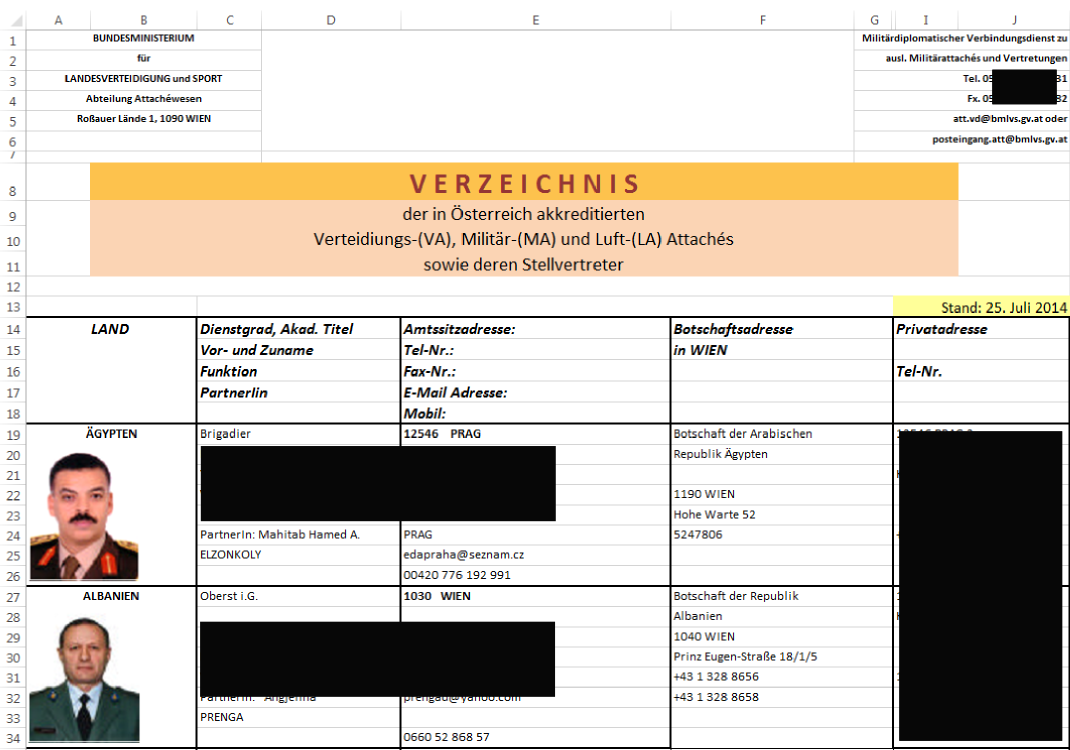 |
Each Excel file included a macro. While the use of Excel Macros and the simple e-mail message initially looked like an old and simple exploit, the backdoor caught the attention of Gadi and Tillmann who assisted with the reverse analysis. It turned out more sophisticated and stealthy then what was found in standard crimeware.
The Excel macro consisted of two files. One was an encoded PE binary, the second a simple VBA script to decode the PE binary, write it to disk and run it. This binary is where things got more interested. It implemented a very capable backdoor, essentially proxying system calls, allow for very flexible access to the system not limiting the attacker to a set of pre-defined commands.
In the end, it turned out that the entire attack was performed using Core Impact, a pricey, but highly sophisticated product allowing for "point and click" attacks of a level that are typically used for APT attacks [2]. In particular when attributing attacks like this to Nation States, or suggesting that the attacker has to be highly sophisticated and able to write custom exploits, one has to consider the possibility that the attacker just re-purposed commercial pentesting software like Core Impact, or even open source tools that offer similar features. The budget for such an attack typically is well below $100k to purchase the required software, a number that is well within reach of even minor nations or organized crime groups. In some cases, it may be possible to find pirated copies fo the required software. Another advantage of using commercial software is the ability to ask for support or professional services to help you with your APT attack.
Oddly, the backdoor was not recognized by anti-virus tools, even though Core Impact is a commonly used product. Core impact also fails to "tag" any of the software with a customer specific serial number, hindering attribution in cases like the one above. Such a serial number would not prevent an authorized pen test, but would help attribute unauthorized attacks.
For more details, I highly recommend that you watch Gadi and Tillmann [1].
[1] http://streaming.media.ccc.de/relive/6575/ (The talk starts around 15 min into the recording)
[2] http://www.coresecurity.com/core-security-client-side-exploits
Indicators of compromise:
IP Addresses
83.170.33.37
83.170.33.60
83.170.33.80
83.170.43.67
84.11.75.220
MD5 Hashes
01c9cebbc39e273ac1f5af8b629a7327 08273c8a873c5925ae1563543af3715c 08e424ac42e6efa361eccefdf3c13b21 0b0e2c4789b895e8ac44b6ada284aec1 177ef7faab3688572403730171ffb9c4 266cfe755a0a66776df9fd8cd2fee1f1 271a5f526a638a9ae712e6a5a64f3106 393bd2fd420eecf2d4ca9d61df75ff0c 395461588e273fab5734db56fa18051b 48573a150562c57742230583456b4c02 4bf2218eb068385ca1bfff8d609c0104 50d3f1708293f40a2c0c1f151c2c426f 5a009a0d0c5ecaac1407fb32ee1c8172 5af0cbc18c6f8ed4fd1a3f68961f5452 916be1b609ed3dc80e5039a1d8102e82 c222199c9a7eb0d162d5e96955739447 d0c3f4c9896d41a7c42737134ffb4c2e da976a502a3afc4ba63611d47c625738 ee41e7c97f417b07177ea420afe510a1 f68a0a3784a7edfc60ad9333ec209cbf f8547010eb4238f8fb76f4e8a756e36d f89a4d4ae5cca6d69a5256c96111e707
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Dec 28th 2014
1 decade ago
Anonymous
Dec 28th 2014
1 decade ago
https://pbs.twimg.com/media/B6MBzU5CYAACAhU.png
Anonymous
Dec 31st 2014
1 decade ago