.docx With Embedded EXE
I received a malicious document sample, a .docx file: c977b861b887a09979d4e1ef03d5f975f297882c30be38aba59251f1b46c2aa8.
If you are familiar with maldocs, you know that .docx files do not contain VBA macros.
What is hiding in this maldoc, is just 2 embedded files:
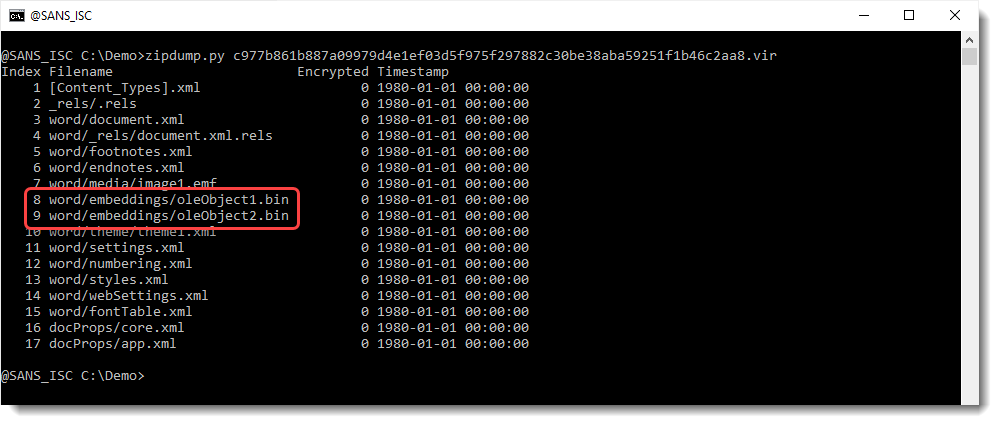
In the command above, I just use my zipdump.py tool to peek into the .docx file (OOXML files like .docx files are ZIP containers).
Embedded files are stored as OLE files inside OOXML files. Thus one can use my oledump.py tool to analyze them:
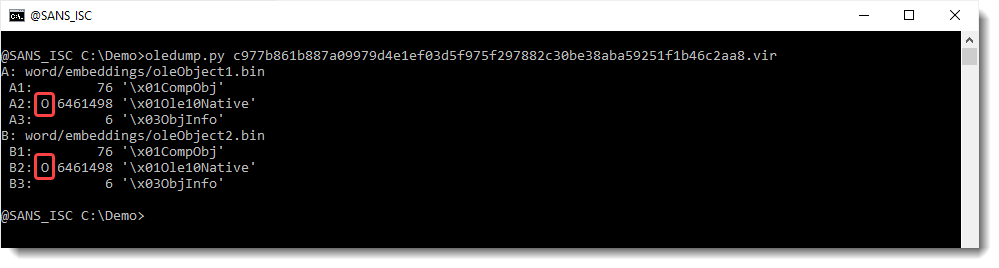
Remark the two O indicators: they tell us there is an embedded object inside that stream (streams A2 and B2).
More info about embedded objects can be obtained with option -i:
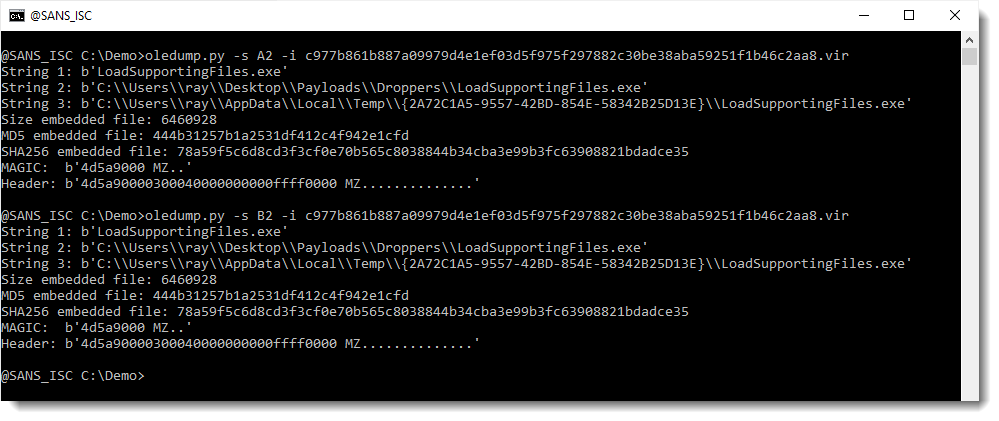
We have quite some information here. First of all, the hashes of both files are identical, thus the file was embedded twice.
The original name of the embedded file is LoadSupportingFiles.exe, and it comes from a user ray who keeps their payloads on their desktop.
The first 2 bytes (MZ) indicate that this is most likely a Windows executable.
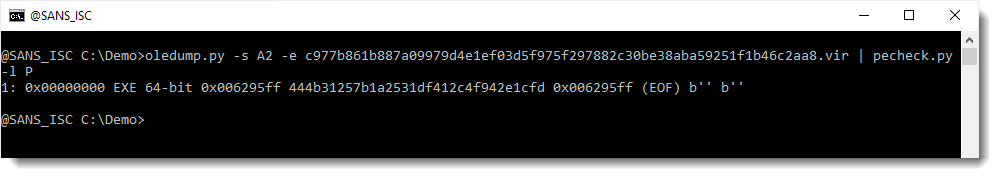
We can extract the file with option -e, and pass it to my tool pecheck.py for example, to verify that it is a PE file:
I also opened the file with Word inside a sandbox, to see how it looks:
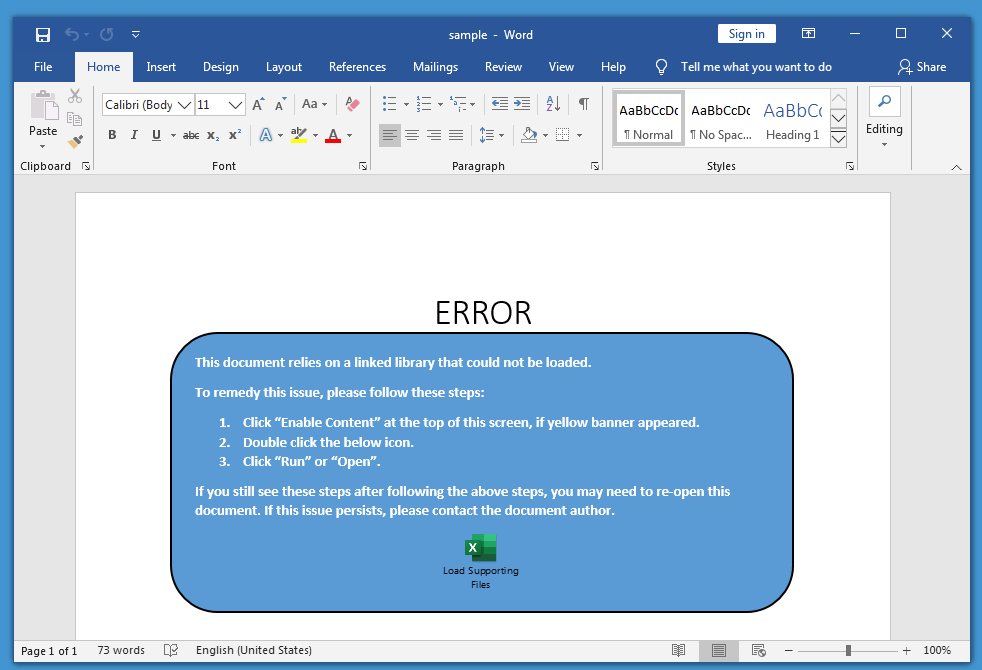
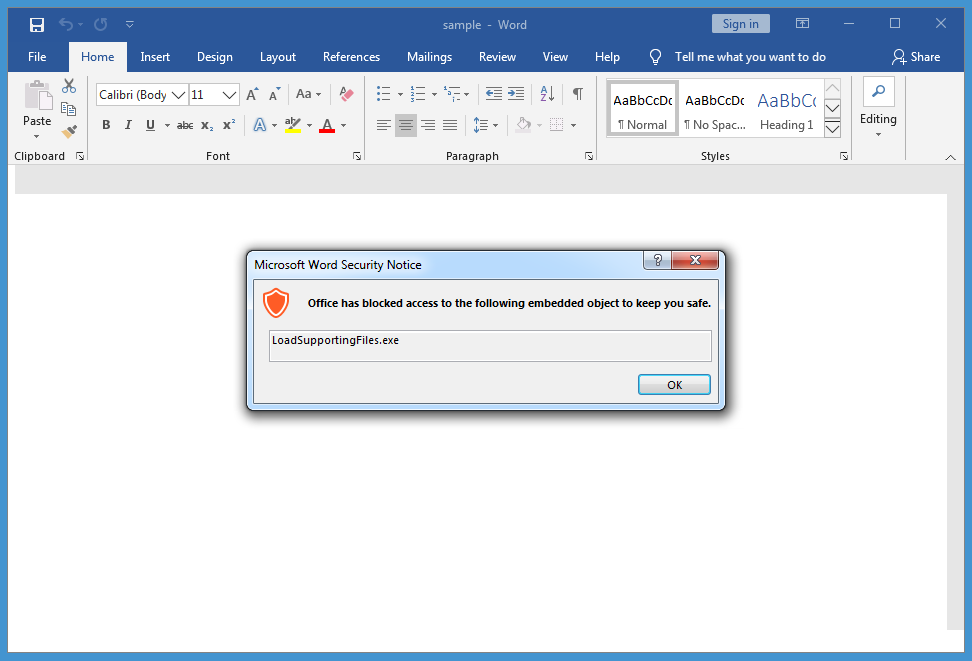
Interestingly, when I follow the instructions, I'm prevented from executing the program. This happens even on an outdated machine (Windows 7 without AV and running Office 2016 patched in October 2020):
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments