Tracking Malware Campaigns With Reused Material
A few days ago I wrote a diary called "Malicious Script Delivering More Maliciousness"[1]. In the malware infection chain, there was a JPEG picture that embedded the last payload delimited with "BaseStart-" and "-BaseEnd" tags.
Today, I discovered anoher campaign that relies exactly on the same technique. It started with an attachment called "TELERADIO_IB_OBYEKTLRIN_BURAXILIS_FORMASI.xIs" (SHA256:1bf3ec53ddd7399cdc1faf1f0796c5228adc438b6b7fa2513399cdc0cb865962). The file in itself is not interesting, it contains a good old Equation Editor exploit (CVE-2017-11882). The exploit triggers the download of an HTA payload that executes a PowerShell payload and finally a DLL:
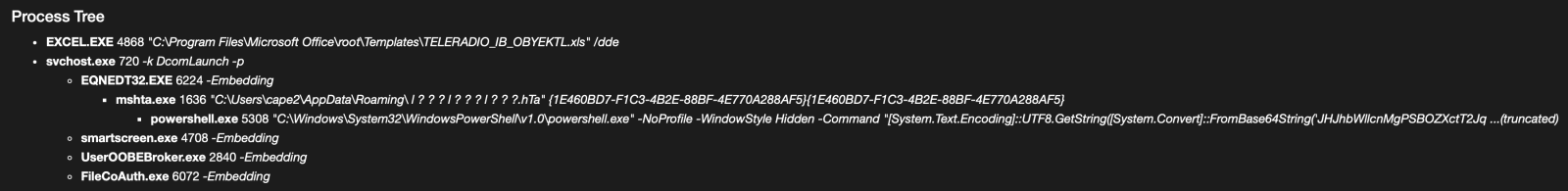
When I investigated the different payload, there was pretty simple to deobfuscated, the interesting code was polluted with Unicode characters. First the HTA file was downloaded from:
hxxp://192[.]3[.]101[.]19/31/sd878f23823878428348fd8g8g8384838f3453dfg.hta
The interesting code is here and you can easily spot the "powershell" string, no need to use AI for this :-)
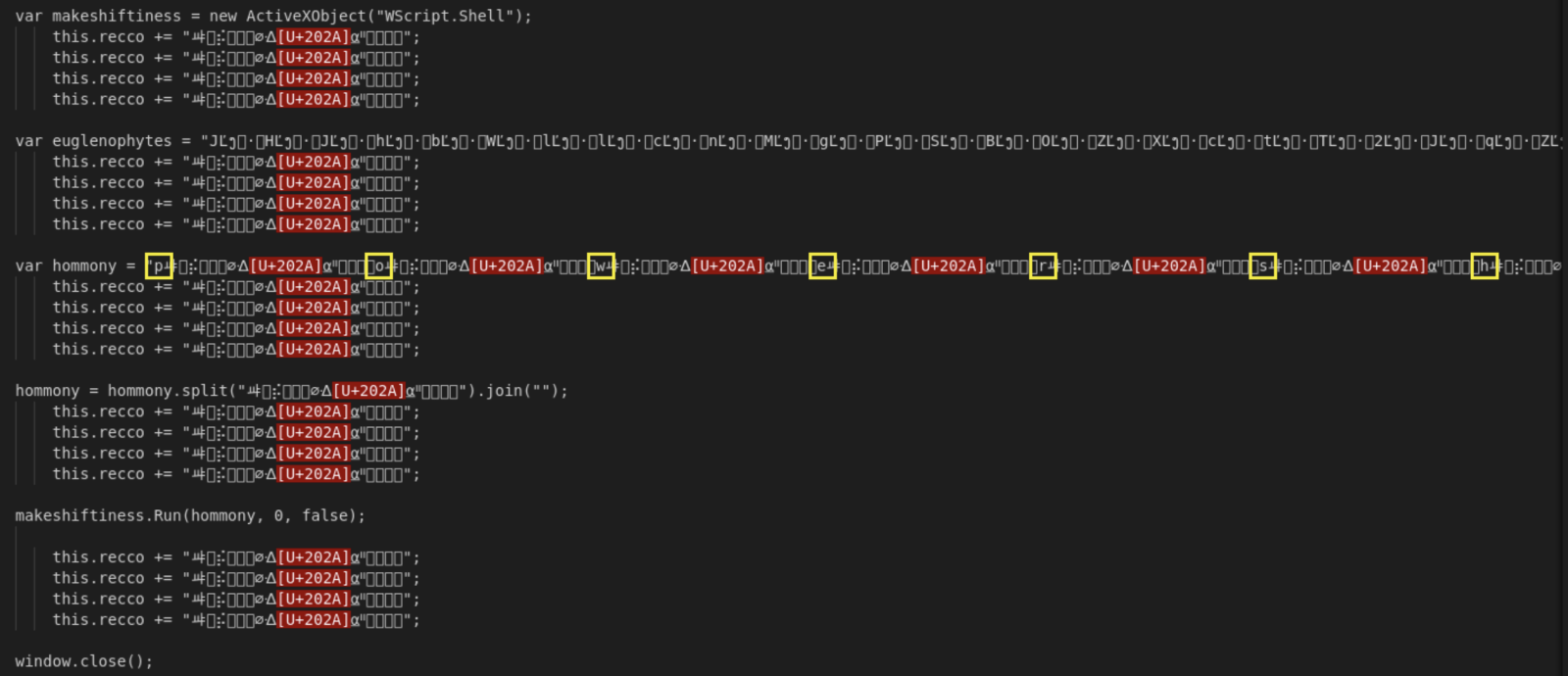
The Powershell payload will fetch another file:
hxxps://172[.]245[.]155[.]116/img/optimized_MSI.png
Do you make the link with my previous diary? It's the same picture:

The technique is also exactly the same, the next stage is Base64-encoded and delimited by the same tags:
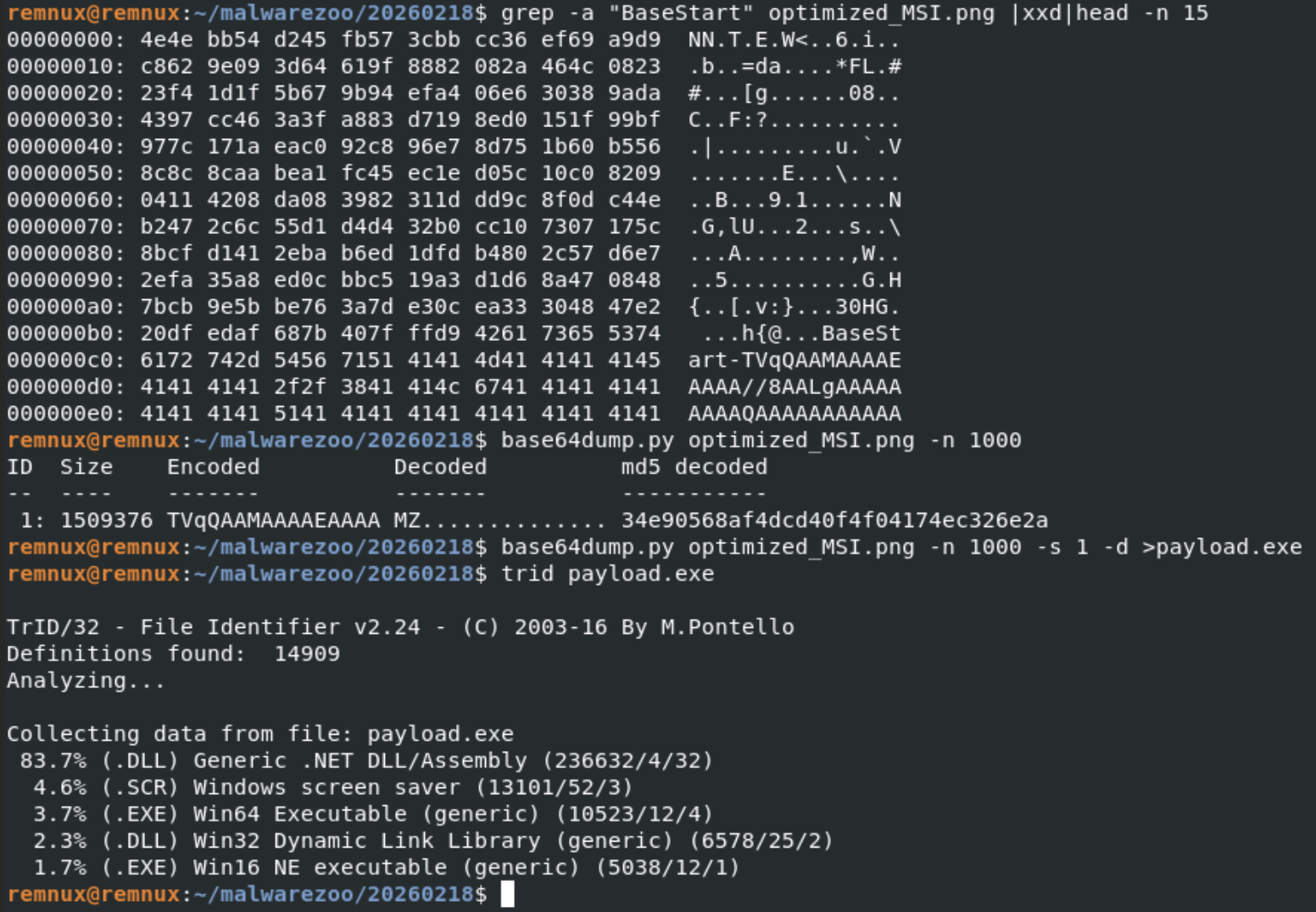
The extracted payload is a .Net binary (SHA256:adc2f550e7ff2b707a070ffaa50fc367af6a01c037f1f5b347c444cca3c9a650).
The fast that the same picture is re-used looks interesting! I did a quick search on VT and use the feature to search for similarities based on the icon/thumbnail and found a lot of identical pictures:
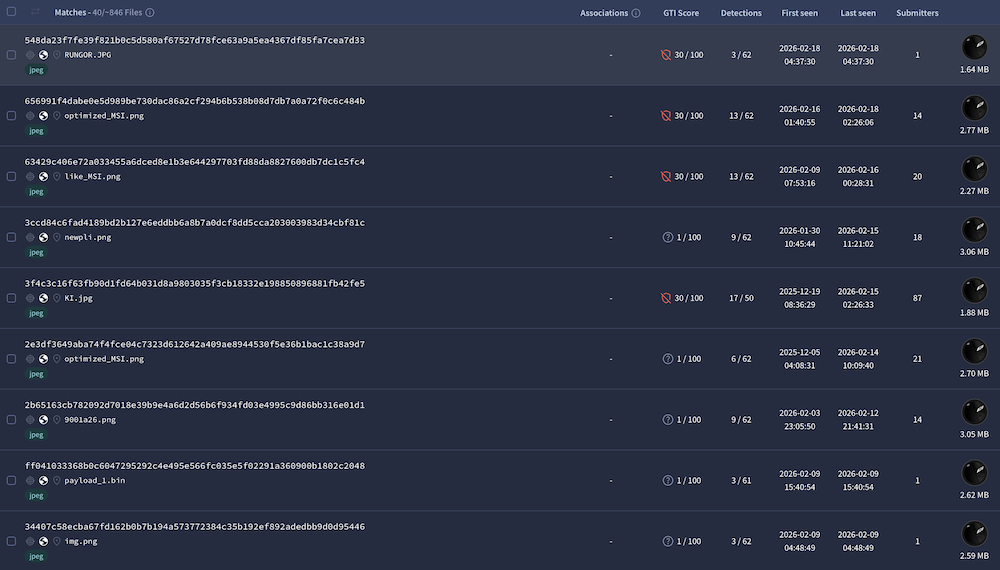
846 similar pictures have been reported but only 36 have a VT score above 5. I created a YARA rule to track them, just curious...
[1] https://isc.sans.edu/diary/Malicious+Script+Delivering+More+Maliciousness/32682
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments