Pivoting and Hunting for Shenanigans from a Reported Phishing Domain
I was alerted to a web page masquerading as a local financial institution earlier in the day. The phishing web page was constructed well, looked extremely similar to the financial institution’s actual page and had input fields for victims to input their credentials. Fortunately, it was taken down quickly. However, I was unable to do further analysis on the perpetrator nor access the site to obtain data (for example, the phishing site allegedly restricted access only to mobile device browsers). Albeit a little disappointed, I analyzed the information that was sent to me and decided to pivot and hunt for a potential website that was involved in shenanigans.
Using the trusty Hurricane Electric’s BGP Toolkit [1], I investigated the IP address block of 104.219.248.0/24 (this was where the financial institution phishing site originated from). After examining the swath of domain names, I discovered a web site attempting to masquerade as the United Nations (UN) Peacekeeping site (Figure 1 shows the masqueraded site, while Figure 2 shows the real UN Peacekeeping site). At the first look, we can see that both websites had slightly different layouts, along with different favicons and page titles. There was also a tawk.to chat plugin observed on the masqueraded UN Peacekeeping site.
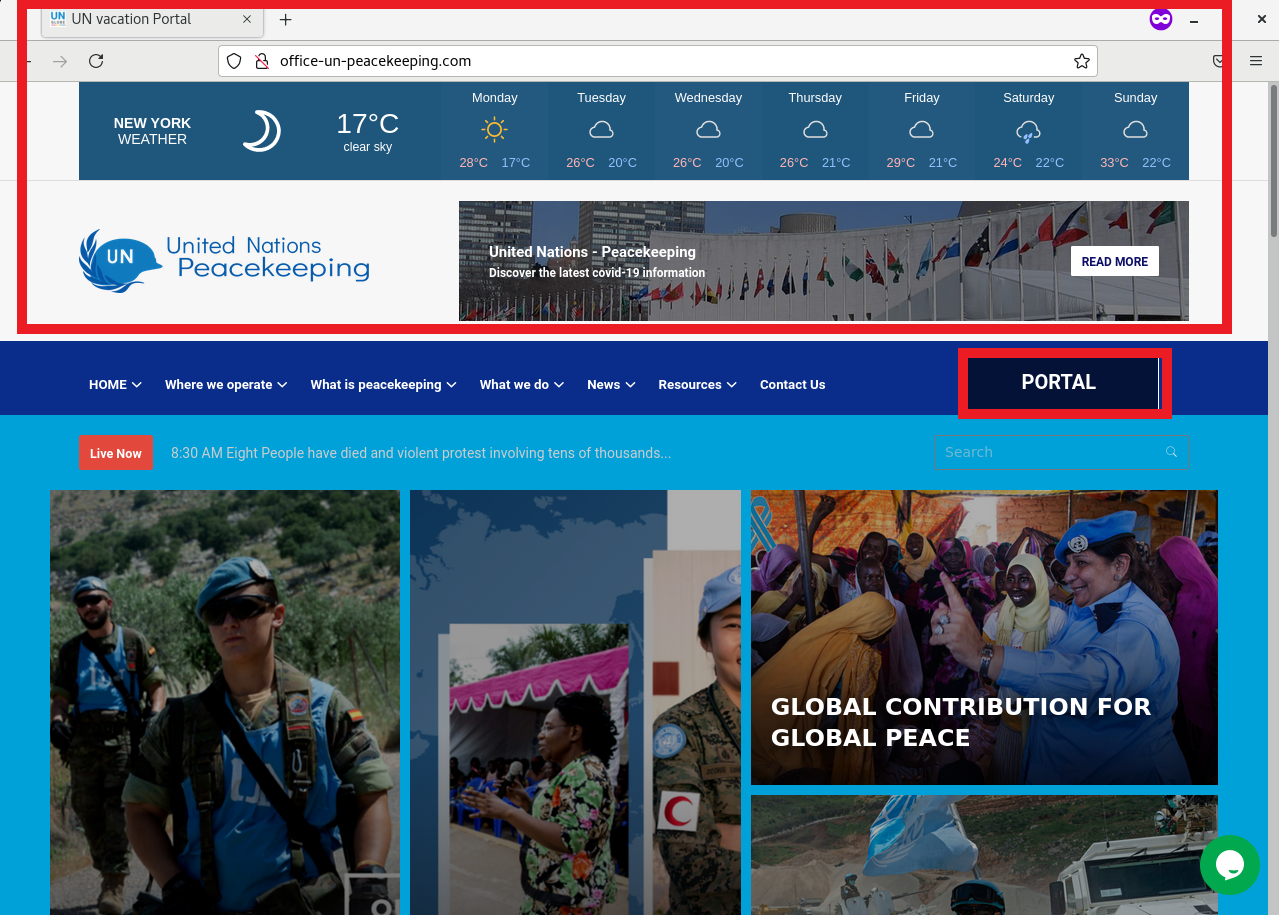
Figure 1: Masqueraded UN Peacekeeping Site
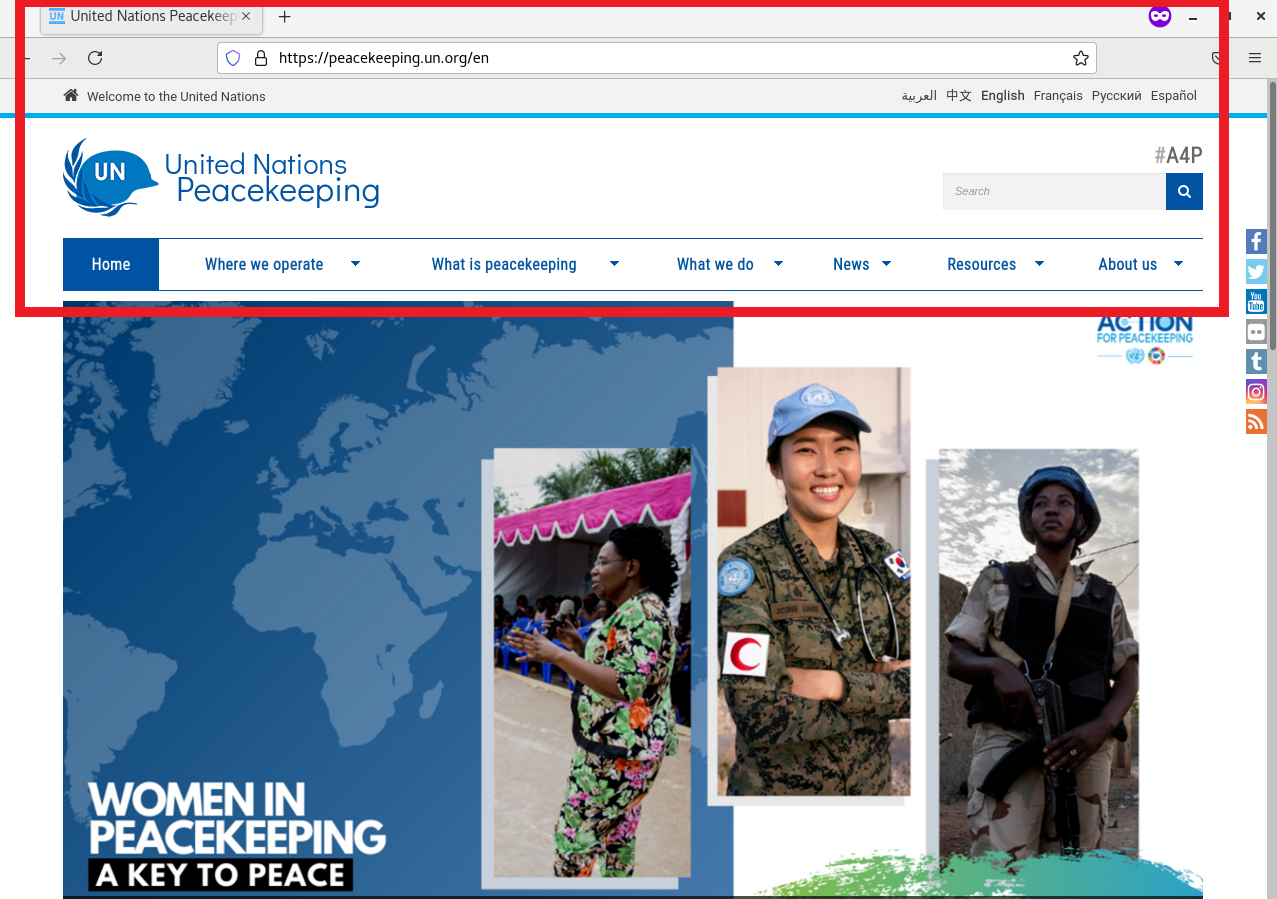
Figure 2: Official UN Peacekeeping Site
In contrast to the previous site that was analyzed in my previous diary [2], the graphics used by this site were self-hosted (the previous site used third-party image hosting sites). I also examined the HTML code, and observed that some portions of the code had comments written in Traditional Chinese characters (as compared to Simplified Chinese characters). This is highlighted in red boxes and shown in Figures 3 and 4.
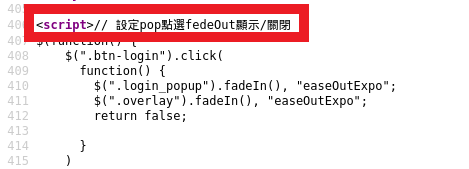
Figure 3: HTML Code with Traditional Chinese Characters Comment (Translation: Configure pop-up selection button, fadeOut show/hide)
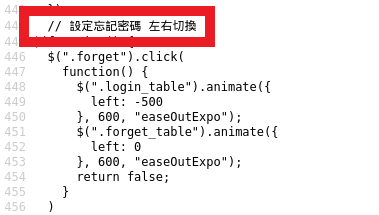
Figure 4: HTML Code with Traditional Chinese Characters Comment (Translation: Configure forget password, left right switch)
Several links in the website appear to redirect to the main index of the website, while others led to a HTTP 404 error message as the links were not configured properly. However, the videos section did redirect to the legitimate UN Web TV website, but there was a typo for “Featured Video” (as shown in Figure 5).
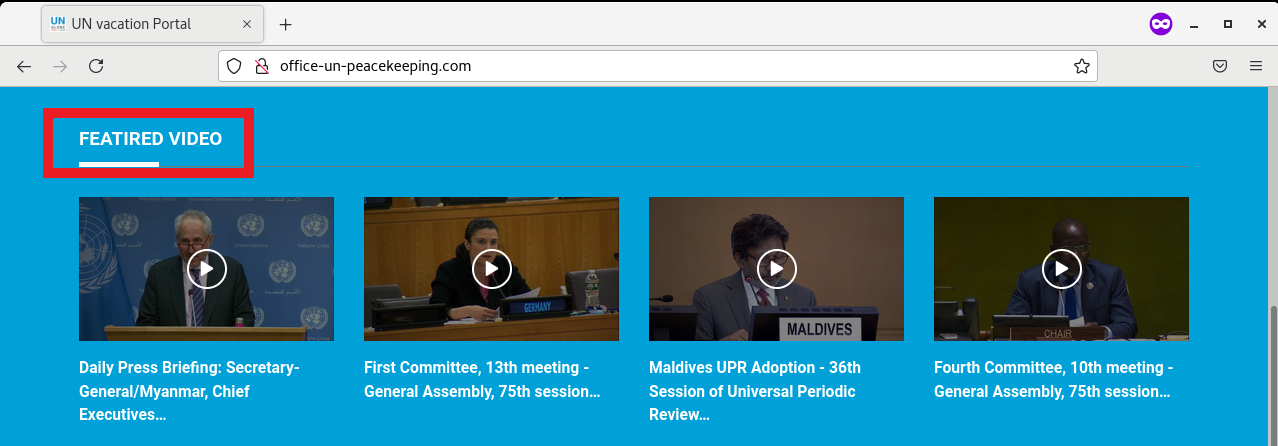
Figure 5: Typo on Masqueraded UN Peacekeeping Site
The masqueraded website also purportedly offered a mechanism to find military personnel. By clicking on the “Portal” button (highlighted in Figure 1), an input field and even a captcha image was displayed (as shown in Figure 6). This was not found on the actual UN Peacekeeping site.
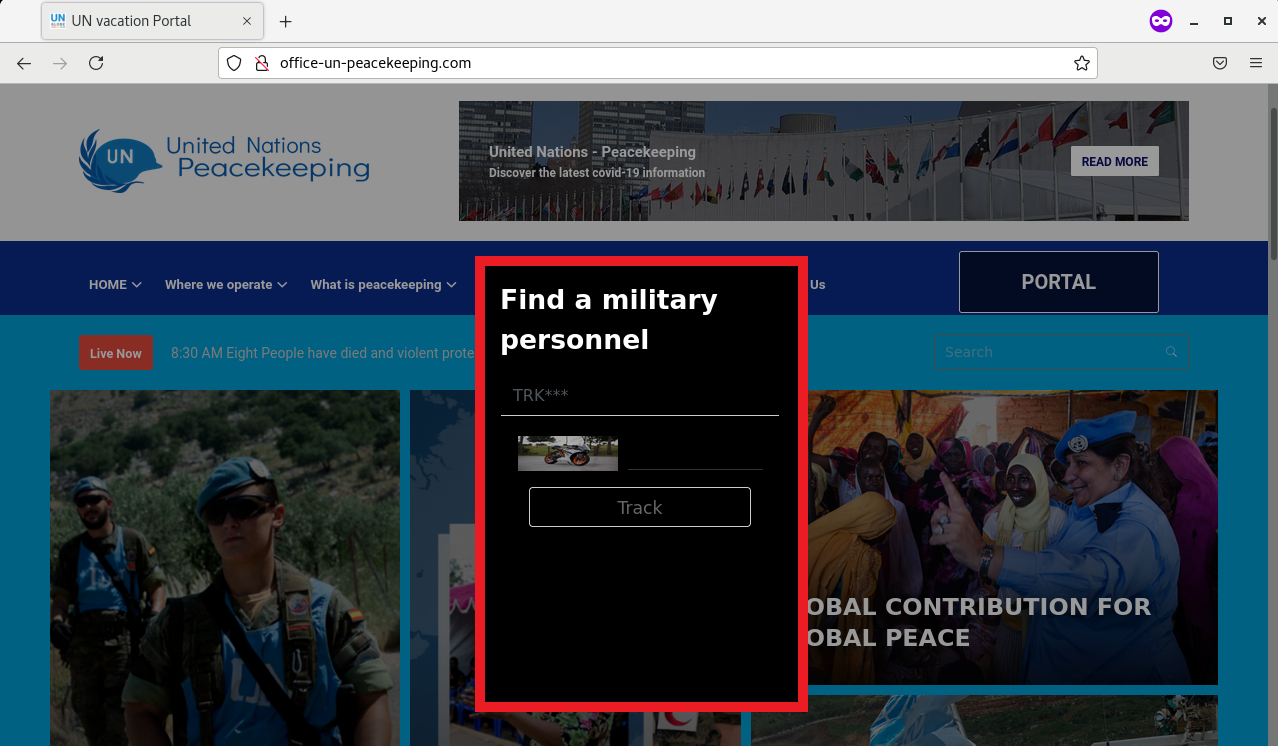
Figure 6: Military Personnel Search on Masqueraded Site
Input validation was not enforced on the masqueraded site. By clicking the “Track” button with no input showed an animation of train on tracks (with reference to Figure 7). Even if there were inputs, the page would still redirect to the page as shown in Figure 7.
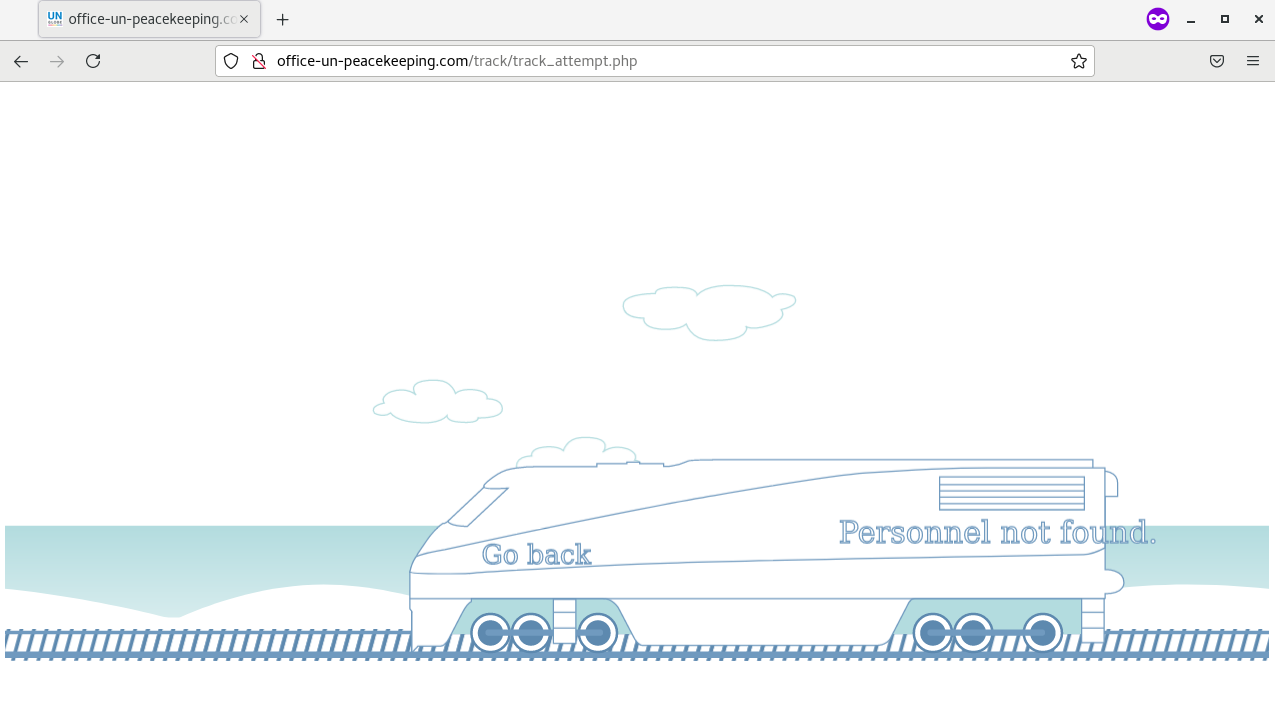
Figure 7: Response to Search on Masqueraded Site
Finally, with reference to Figure 8, it was observed that the site had embedded Google Analytics to track and monitor visitors. However, after digging deeper into the Google Analytics Tracking ID, it turned out that the Tracking ID was copied by many people online and it appeared in several online sites such as forums, Stack Overflow and Pastebin.
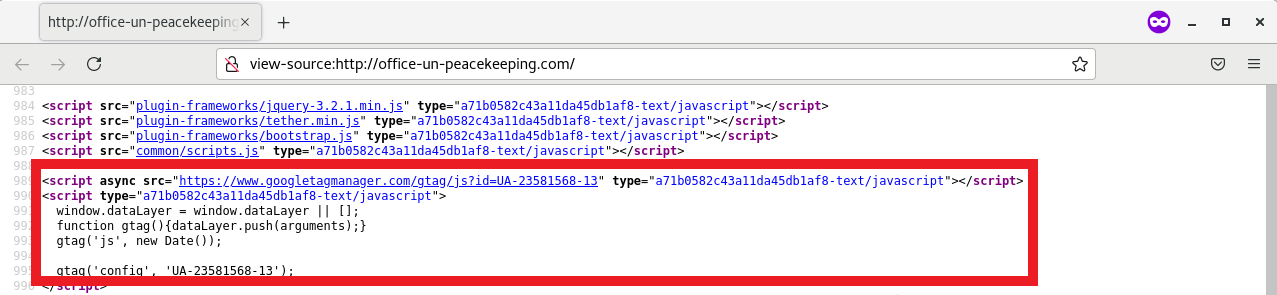
Figure 8: Google Analytics Code on Masqueraded Site
There were many interesting takeaways after examining this masqueraded site, especially from Open-Source Intelligence (OSINT) and operational security (OPSEC) perspectives. This site could gather visitor and geolocation data via Google Analytics. However, the appearance of the same Tracking ID in many different online sites (especially those requesting for guidance in coding) meant that more efforts to trace its actual owner and first appearance/usage would be required.
Native data collection (Find a military personnel) and communications (tawk.to plugin) functionality were also present. Since the website was titled as “UN vacation Portal”, a plausible hypothesis could be that the perpetrators were fishing for information on vacationing UN Peacekeepers. For example, they could invite unsuspecting victims to input details of their colleagues (or even their own data) to verify their vacation status. Having such knowledge could facilitate phishing, social engineering attempts or even potential armed conflict. Another interesting observation was that the perpetrators chose to display current weather information of New York at the top of the site, and had made sure that the site appeared current by also putting in a banner about COVID-19 information. As of now, attribution would be difficult since more data will be needed. Having said that, considering all the points raised and observations, this web site most certainly do not appear to be benign.
The indicators of compromise of the site are listed below.
Indicators of Compromise (IOCs):
hxxp://office-un-peacekeeping[.]com
104.219.248[.]9
References:
[1] https://bgp.he.net/
[2] https://isc.sans.edu/diary/27456
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter


Comments