Trickbot gtag red5 distributed as a DLL file
Introduction
Trickbot is an information stealer/banking malware that uses modules to perform different functions. With Windows 10, these modules are loaded into memory, and we only see initial Trickbot binary and a text-based configuration file stored on the infected Windows 10 host.
Access to Trickbot-infected hosts is granted to other criminals groups to distribute other malware like Ryuk ransomware. This sort of follow-up malware has previously been noted in conjunction with Powershell Empire traffic and/or Cobalt Strike activity on a Trickbot-infected host.
But today's diary focuses on one of the distribution methods for the initial Trickbot infection.
Last month on 2020-02-25, I ran across an example of Trickbot (gtag red4) distributed as a Windows DLL file. Normally, I see Trickbot distributed as an Windows EXE. 2020-02-25 was the first time I personally saw Trickbot distributed and made persistent as a DLL.
On Tuesday 2020-03-17, I ran across another example of Trickbot as a DLL. This time, it was gtag red5, and I've documented the occasion in today's ISC diary.
Of note, a Trickbot sample's "gtag" indicates its specific method of distribution. The "red" series gtag has been noted with Trickbot as a DLL file distributed using a JSE downloader. The image below shows a flow chart for my infection on Tuesday 2020-03-17.
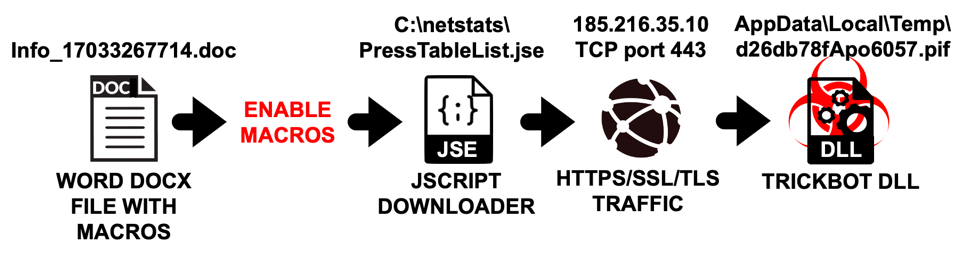
Shown above: Flow chart for this specific gtag red5 Trickbot infection chain.
Images from the infection
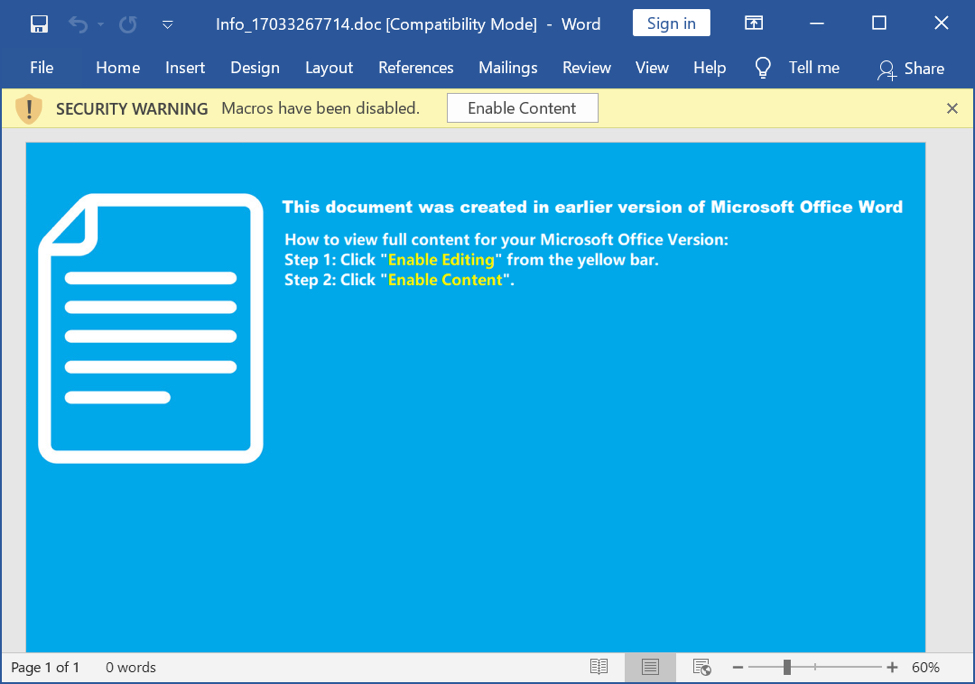
Shown above: Screenshot of the Word document that kicked off this Trickbot infection.
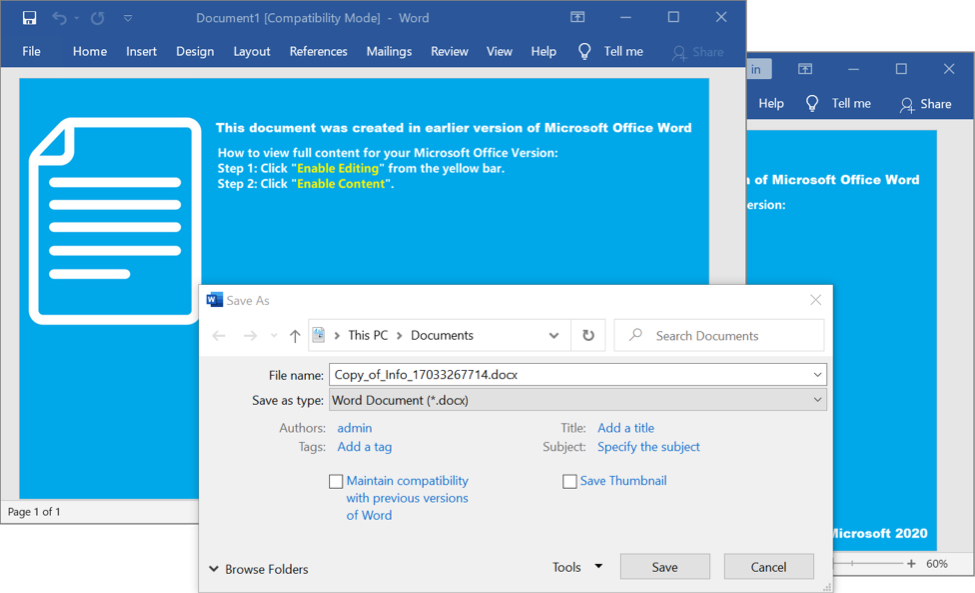
Shown above: Enabling macros caused the Word document to save a copy of itself.
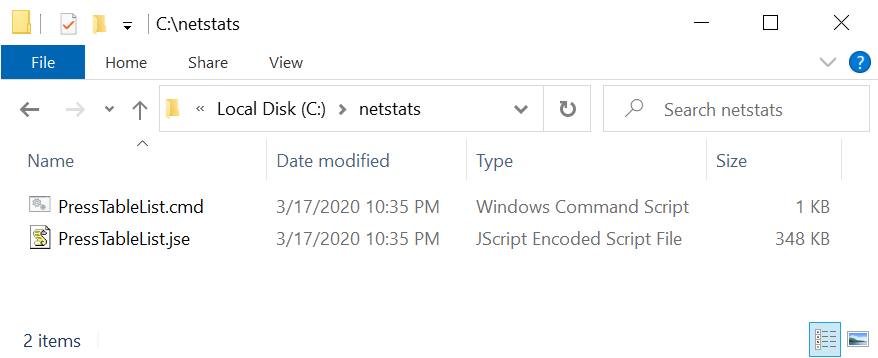
Shown above: Meanwhile, I found a JSE file that acted as a malware loader in a newly-created directory named C:\netstats\.
Shown above: The JSE-based loader PressTableList.jse appears to be highly-obfuscated.
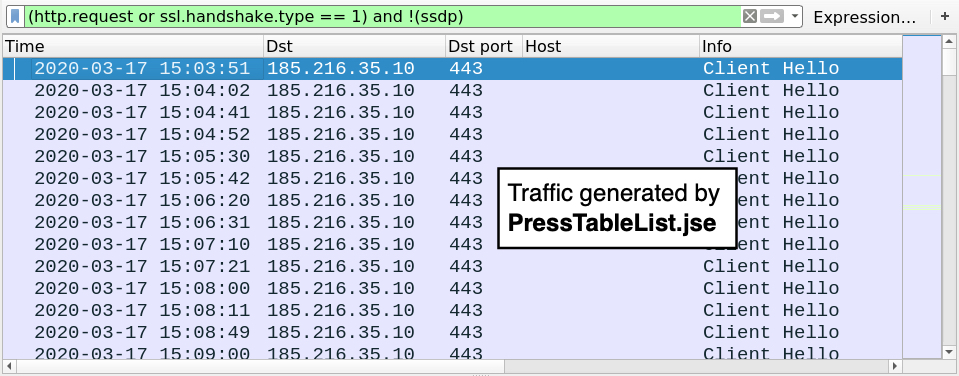
Shown above: HTTPS/SSL/TLS traffic generated by PressTableList.jse filtered in Wireshark.
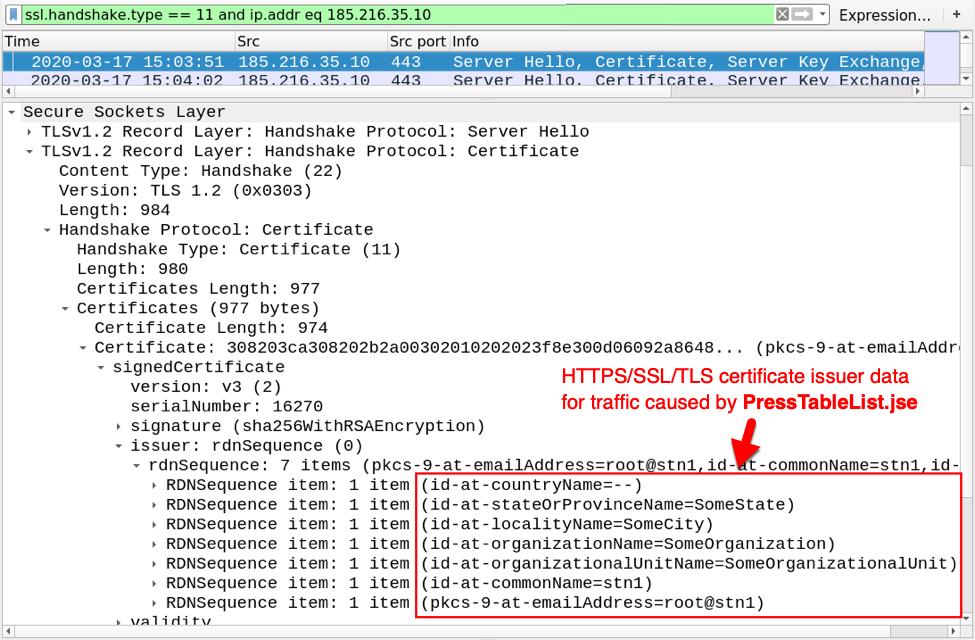
Shown above: Certificate issuer data from HTTPS/SSL/TLS traffic caused by PressTableList.jse.
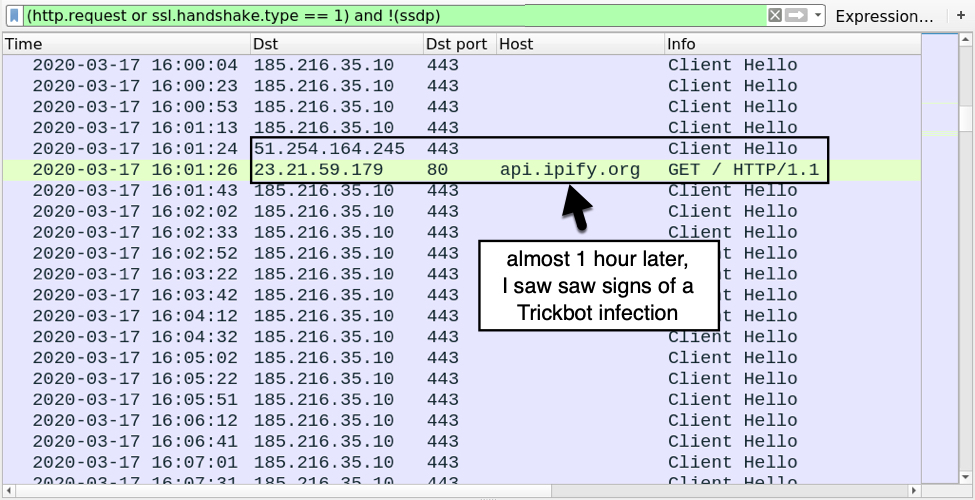
Shown above: About 1 hour after the initial infection, I saw signs of a Trickbot infection.
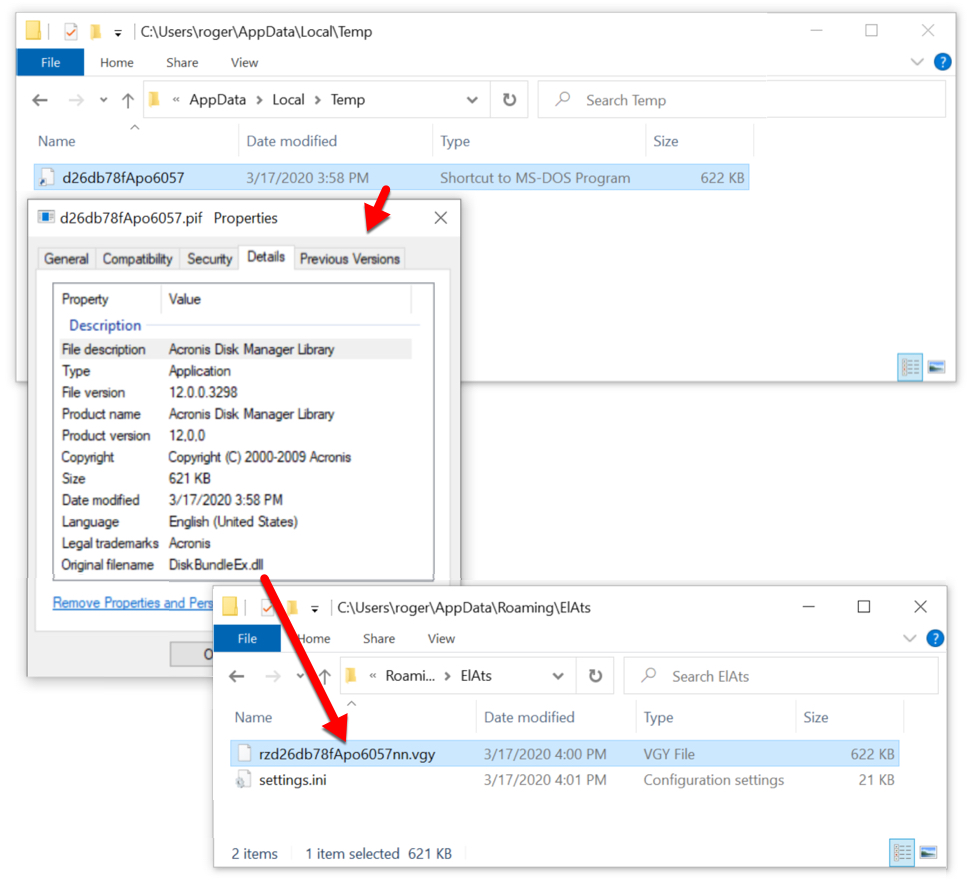
Shown above: Shortly before the Trickbot traffic, I found evidence of a Trickbot binary saved to the infected Windows host.
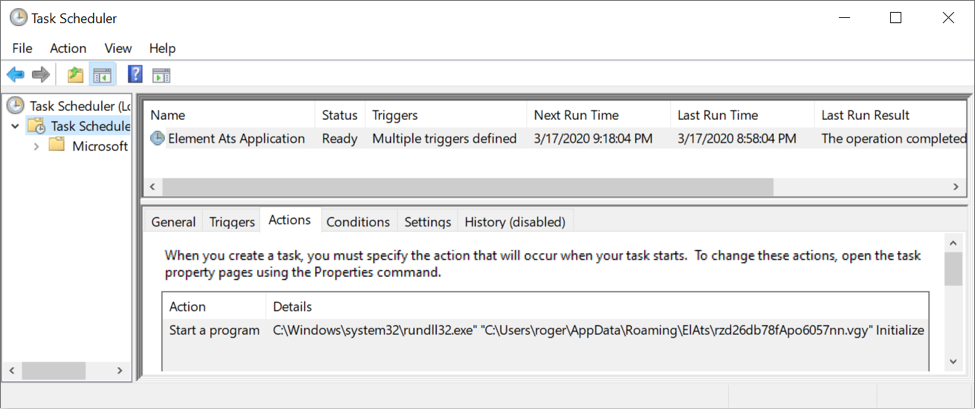
Shown above: The scheduled task to keep Trickbot persistent indicates this Trickbot binary is a DLL.
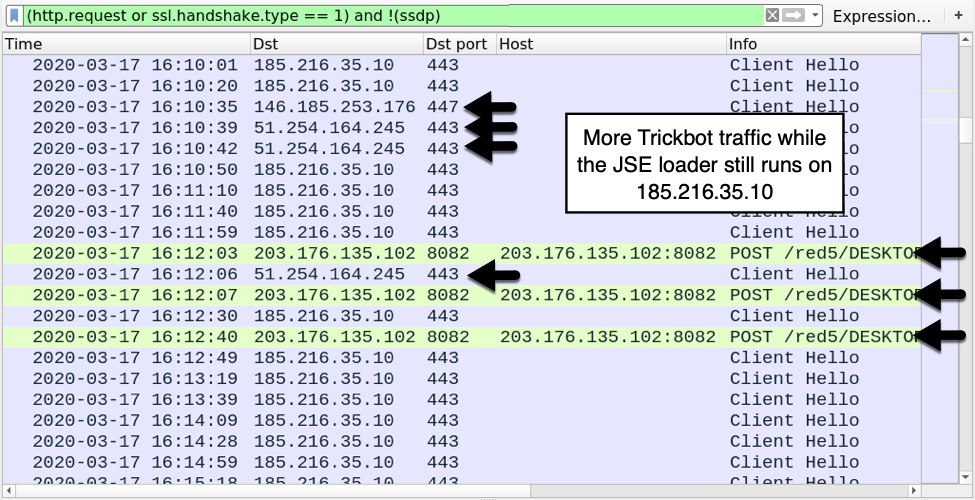
Shown above: More Trickbot traffic, including HTTP requests over TCP port 8082 that reveal this Trickbot is gtag red5.
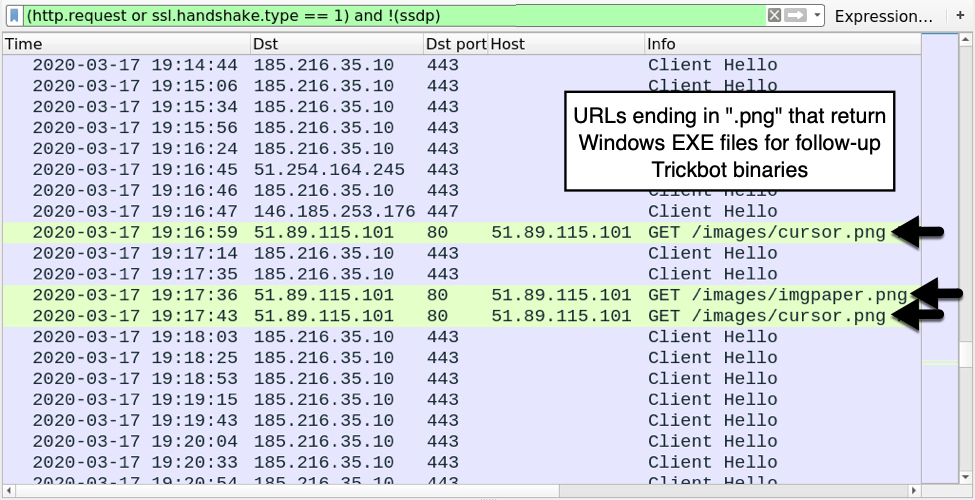
Shown above: HTTP requests ending in .png that returned follow-up Trickbot binaries (these were EXE files, not DLL or PNG).
Indicators of Compromise (IoCs)
Traffic from an infected Windows host:
JSE loader traffic:
- 185.216.35[.]10 port 443 - HTTPS/SSL/TLS traffic
Trickbot infection traffic:
- port 80 - api.ipify[.]org - GET / [ip address check by the infected host, not inherently malicious]
- 51.254.164[.]245 port 443 - HTTPS/SSL/TLS traffic
- 146.185.253[.]176 port 447 - HTTPS/SSL/TLS traffic
- 181.129.104[.]139 port 449 - HTTPS/SSL/TLS traffic
- 46.4.167[.]250 port 447 - attempted TCP connections but no response from the server
- 64.44.51[.]113 port 447 - attempted TCP connections but no response from the server
- 203.176.135[.]102 port 8082 - 203.176.135[.]102:8082 - POST /red5/[host name]_[windows version].[32-digit hex string in ASCII]/90
- 203.176.135[.]102 port 8082 - 203.176.135[.]102:8082 - POST /red5/[host name]_[windows version].[32-digit hex string in ASCII]/81/
- 51.89.115[.]101 port 80 - 51.89.115[.]101 - GET /images/cursor.png
- 51.89.115[.]101 port 80 - 51.89.115[.]101 - GET /images/imgpaper.png
Malware/artifacts from an infected Windows host
SHA256 hash: 08b885ccc3eda61a918bd1887b7669e54d03be79a3accae765c10cd0850ff10d
- File size: 270,883 bytes
- File name: Info_17033267714.doc
- File description: Word doc with macro for JSE downloader
SHA256 hash: c0fe570561cc3546ed7e03523baf5e482ec9ee98e6a8de161fdc885f6721f0a0
- File size: 49 bytes
- File location: C:\netstats\PressTableList.cmd
- File description: CMD script to run PressTableList.jse
- File content: cscript //nologo c:\netstats\PressTableList.jse
- Note: Not malicious by itself
SHA256 hash: 36ef77fe7b4a27813c8149674565f60aceb2fa9510e04732ef53367ce3dc567a
- File size: 356,006 bytes
- File location: C:\netstats\PressTableList.jse
- File description: JSE-style malware downloader
SHA256 hash: 445716d2fdd0cc8927c02bda53f44cba82f3a934d1a6cb9163760544b3e515e9
- File size: 636,416 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\d26db78fApo6057.pif
- File location: C:\Users\[username]\AppData\Roaming\ElAts\rzd26db78fApo6057nn.vgy
- File description: DLL file retrieved by JSE-style downloader, this is Trickbot gtag red5
SHA256 hash: 262cf3e4da865ff7b028d2f1be407d1d37008644ee89c3e16f4b873e6cde344c
- File size: 20,541 bytes
- File location: C:\Users\[username]\AppData\Roaming\ElAts\settings.ini
- File description: Configuration/settings file used by Trickbot, different file hash and content for each infection. This is not inherently malicious on its own.
SHA256 hash: efb75ce7030fc32190909048fcb3fab024cb8779b9559a417b8d397352ae6ea2
- File size: 696,371 bytes
- File location: hxxp://51.89.115[.]101/images/cursor.png
- File description: Follow-up Trickbot EXE (gtag: tot698) returned from URL ending in .png
SHA256 hash: 3850e5731f9f1430eafd477b5e0607aad48f80bb28e32d163b941414db7f1695
- File size: 696,371 bytes
- File location: hxxp://51.89.115[.]101/images/imgpaper.png
- File description: Follow-up Trickbot EXE (gtag: lib698) returned from URL ending in .png
Final words
A pcap of the infection traffic along with the associated malware can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments