SNMP service: still opened to the public and still queried by attackers
by Manuel Humberto Santander Pelaez (Version: 1)
Simple Network Management Protocol (SNMP) is a UDP service that runs on port 161/UDP. It is used for network management purposes and should be reachable only from known locations using secure channels.
I reviewed my honeypot today for interesting connections during december 2019. Saw an increase of snmp queries with the following distribution:
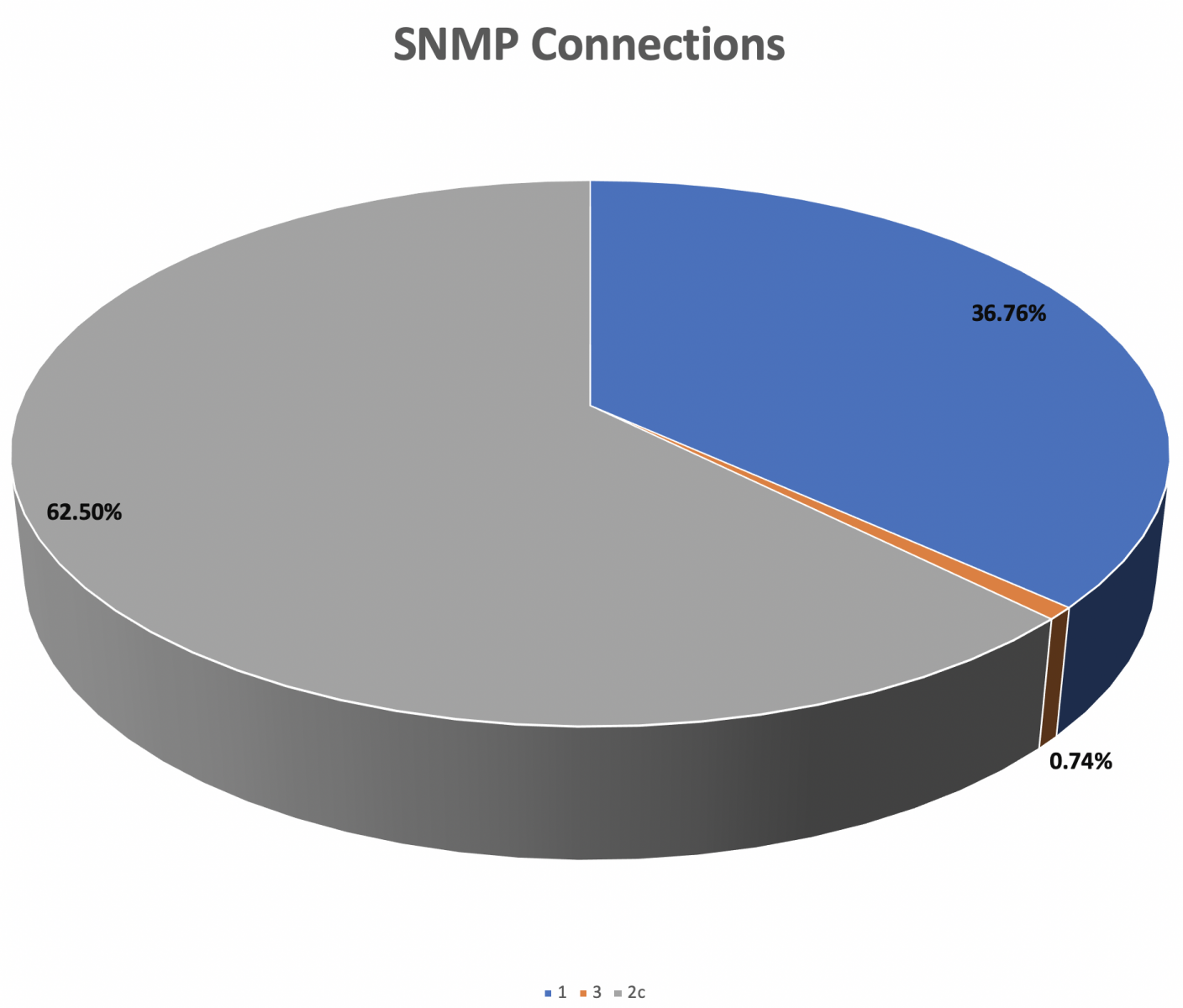
This is interesting as attackers are querying for the Community-Based Simple Network Management Protocol version 2 (SNMPv2c) instead of SNMPv2. It introduced GetBulkRequest command to gather large amount of data. SNMPv2c includes SNMPv2 without the SNMPv2 security model, using instead the simple community-based security scheme of SNMPv1.
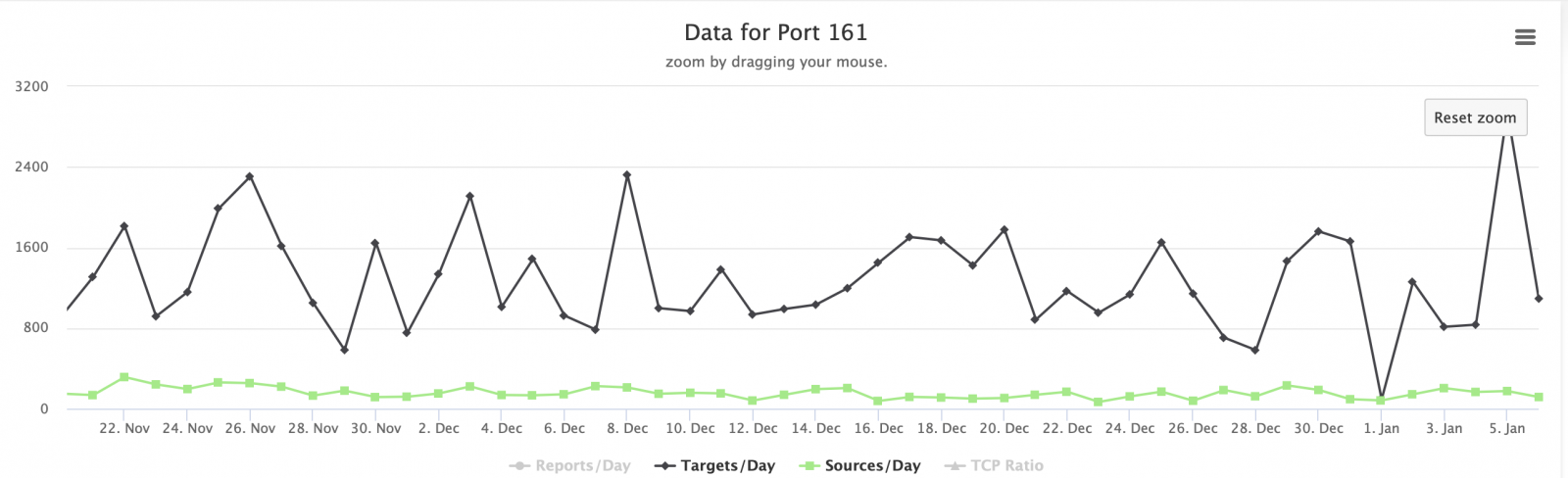
Our ISC data shows this port was also active during december with a small spike during the first week of 2020:
Shodan report shows many devices connected to the internet with open SNMP port:

And there are domains with an important number of devices with open SNMP port. Source is Shodan:
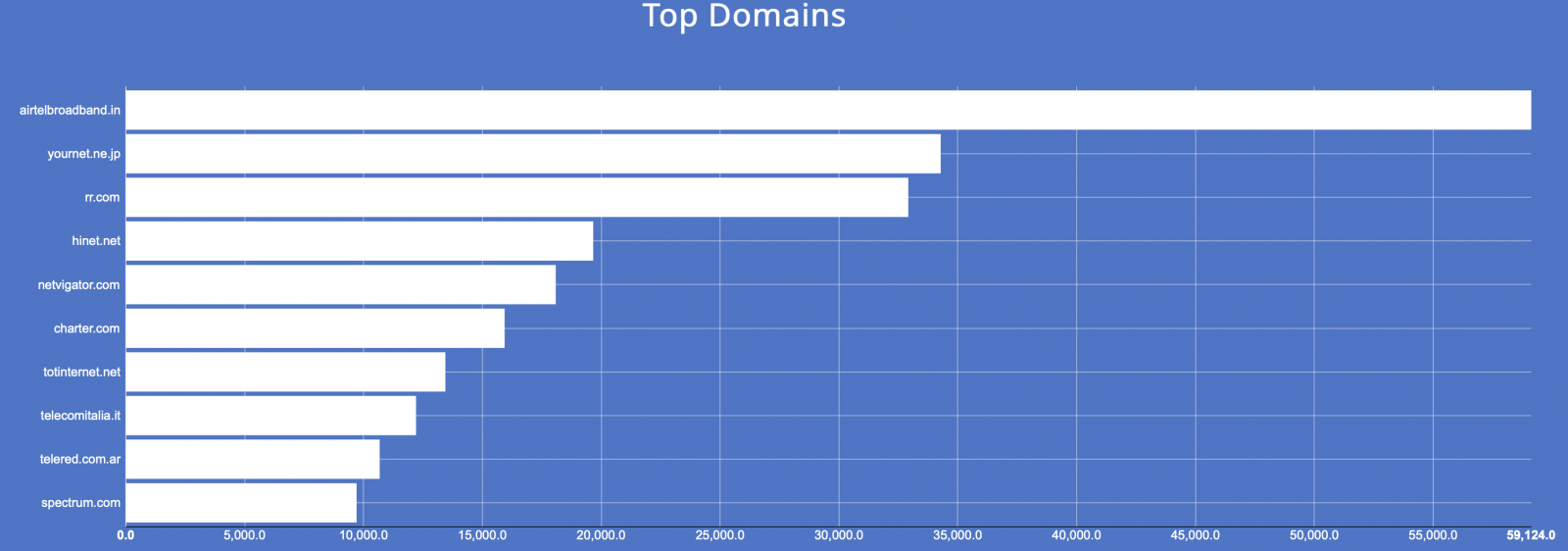
We can conclude the following:
- There are devices that still have SNMP open to the Internet and the attackers know it. They predominantly search for devices that respond under the SNMPv2c protocol.
- You should not place devices on the Internet with open SNMP services. This is a very cheap way for an attacker to gather intelligence about your network and traffic.
- Please always use secure protocols:
- SNMPv1 send passwords in clear text. SNMPv2 is prone to password hashing attacks.
- SNMPv1 and SNMPv2 are vulnerable to IP spoofing. None of them should be used.
- SNMPv3 is vulnerable to brute force and dictionary attacks. This is the current protocol version. To mitigate the vulnerabilities, you should use IPSec transport connections.
Do you have any other interesting findings to share with us? Please send them out using our contact form.
Manuel Humberto Santander Pelaez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org



Comments
Anonymous
Jan 6th 2020
5 years ago
SNMP v1 and v2 enabled RW (!!) by default.
TFTP (!!!) enabled by default.
Lots of other fun and games, but those two are probably the most memorable of the many preinstalled vulnerabilities.
Anonymous
Jan 7th 2020
5 years ago