Not All Malware Samples Are Complex
Everyday we hear about new pieces of malware which implement new techniques to hide themselves and defeat analysts. But they are still people who write simple code that just "do the job". The sample that I’m reviewing today had a very short lifetime because it was quickly detected by most antivirus. Its purpose is to steal information from the infected computers like credentials. When the sample was submitted for the first time to VT, it reached a score of 11/59 which is not bad. Today, its score is 44/59[1].
Amongst actions like copying itself to C:\Users\%USER%\Temp\Skype\chrome.exe. It checks the victim’s computer location via hxxp://ip-score.com/checkip/ and collects information about the victim. Then the malware creates a scheduled task to execute itself every minute:
C:\WINDOWS\system32\cmd.exe /c schtasks /create /tn "MOCLXG" /tr C:\DOCUME~1\Xavier\LOCALS~1\Temp\Skype\chrome.exe /sc minute /mo 1
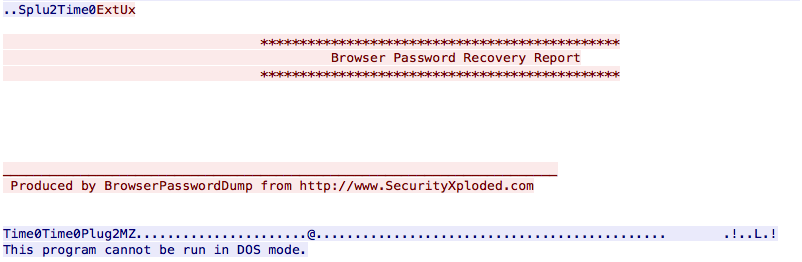
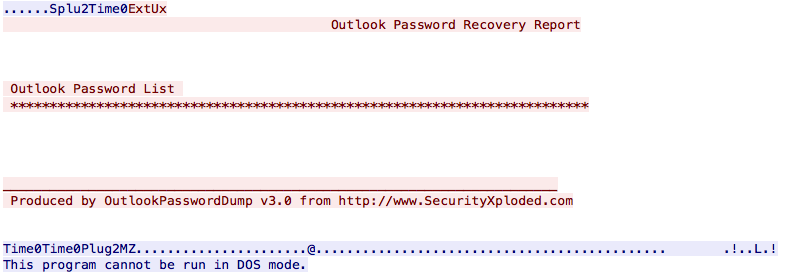
The way it steals information from the victim in interesting in this case. People are often lazy so why reinvent the wheel? There already exists tools to collect credentials from applications like browsers, email clients, …
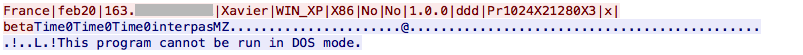
The PE file is dropped on the file system, executed and the output is saved in a temporary file:
C:\WINDOWS\system32\cmd.exe /c Pl2.exe -f "Pl2.txt"
It captures passwords from well-known applications. Once completed, results are sent to the C2:

| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments