Windows Autorun Part-1
When someone suspecting that a malware activity that may exist in a system or a compromised systemone of the most obvious places to check is the startup locations .In this diary I am going to discuss some of the startup locations in Windows Systems:
1-Startup Folders:
On Windows XP systems:
C:\Documents and Settings\All Users\Start Menu\Programs\Startup
C:\Documents and Settings\%UserName%\Start Menu\Programs\Startup
On Windows Vista/7/8
C:\Users\All Users\Microsoft\Windows\Start Menu\Programs\Startup
C:\Users\%UserName%\Appdata\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
When an executable file (application or batch file) is located in the All Users folder will run for any user when he/she logon, while when it's located in particular user’s folder it will run only for that user when he/she logon.
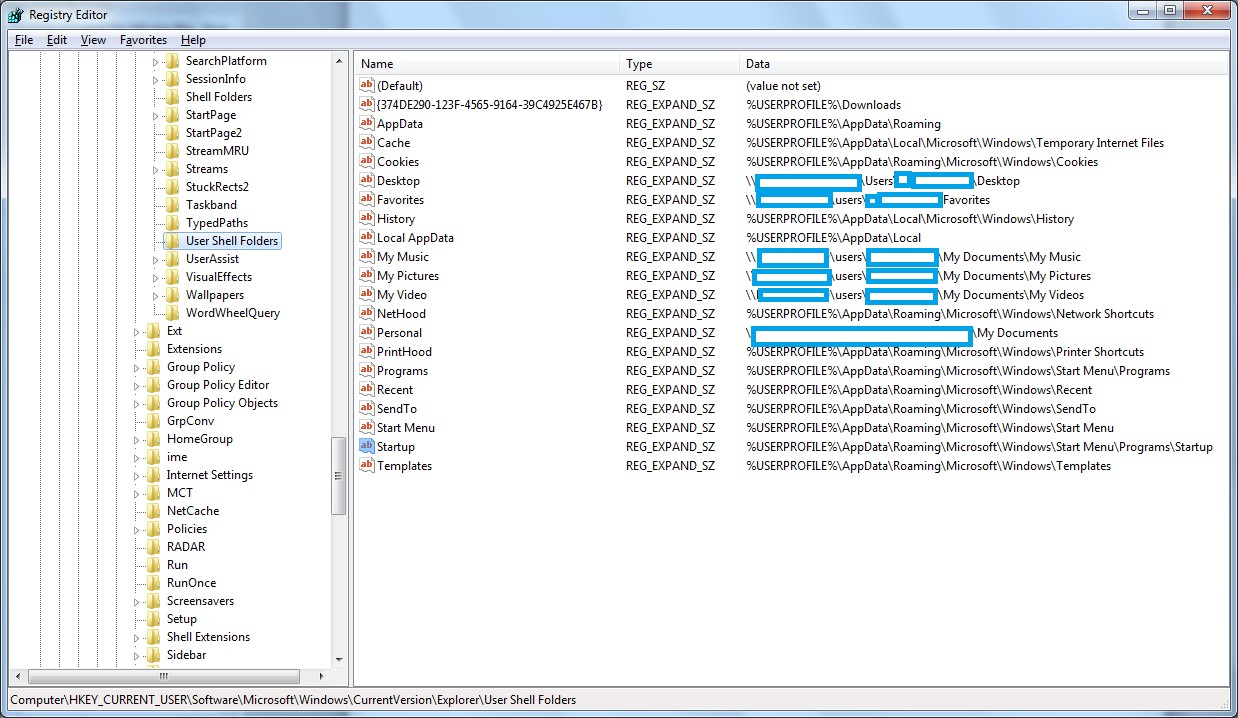
Please note that the above locations are the default and it can be changed, I will suggest first to check the following registry keys:
On Windows XP /Windows Vista/7/8 (See figure 2):
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders



Comments
Anonymous
Dec 27th 2013
1 decade ago
Anonymous
Dec 27th 2013
1 decade ago
Speaking of which, a while ago I read some stats on how common various persistence mechanisms were used by malware. Does anyone know where that was or know of similar stats?
Anonymous
Dec 27th 2013
1 decade ago