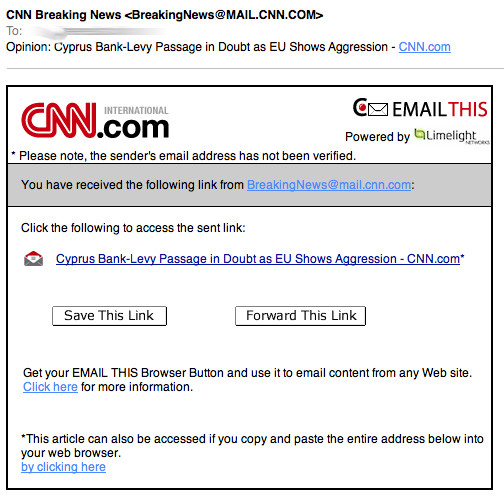
Scam of the day: More fake CNN e-mails
This one made it past my (delibertly porous) spam filter today. We don't cover these usually, as there are just too many of them (I just got another facebook related one while typing this). But well, from time to time its fun to take a closer look, and they make good slides for awareness talks.
The initial link sends the user to hxxp:// swiat-feromonow.pl / wiredetails.html which redirects the users to the usual obfuscated javascript at hxxp:// salespeoplerelaunch. org/ close/printed_throwing-interpreting-dedicated.php .
The later page not only uses javascript, but in addition for good measure will also try to run a java applet. Wepawet, as usual has no issues analyzing the file [1]. It discovers the usual browser plugin fingerprinting code, but no specific exploits.
ok. cool... yet more malware. But I didn't want to leave it at that, and went ahead to try and get that site shut down. First stop: whois salexpeoplerelaunch.org . The result is a legit looking contact in Michigan with a phone number, which has been disconnected :( ... so I am trying an e-mail to the listed e-mail address (just sent... no response yet, but will update this diary if I get one)
Moving on to the IP address. It is assigned to https://www.wholesaleinternet.net , a low cost dedicated server / colocation provider. Sending them an abuse request now via email, and again, will update this diary if I hear from them. Interestingly, the IP address is not "known" to serve any other domains based on a quick check of some passive DNS replication systems. I also sent an email to abuse @ szara.net which hosts the domain swiat-feromonow.pl.
Lets see how long the link will stay up.
[1] http://wepawet.iseclab.org/view.php?hash=dbeb07e4d46aa4cbd38617a925499c22&type=js
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
pogue
Mar 19th 2013
1 decade ago
Did you get a chance to examine the j1, j2, p1, p2, or f1 droppers? Unfortunately the page is down now so I wasn't able to pull them.
matt
Mar 19th 2013
1 decade ago
https://urlquery.net/report.php?id=1519825
https://wepawet.iseclab.org/view.php?hash=dea84e914a523c53b430e17e194702ae&t=1363727946&type=js
The j1 & j2 droppers are the same (possibly varies based on user-agent, I didn’t check this), md5: 88b055562334f7b45b747c9cb5dc9c75
https://www.virustotal.com/en/file/96952cada5a3a7c6aaec09edc50d68bd0ad56a35d6dbdb756bc5e206f394b1d1/analysis/
The p1 & p2 droppers vary per-request (i.e., a new PDF is generated per-request), according to Wepawet they’re using CVE-2009-0927 (Adobe getIcon)
https://www.virustotal.com/en/file/39905d71a73bf81d785fb07ff75f80b06562bcc094f0f6087f7acad2de67e7d1/analysis/
https://wepawet.iseclab.org/view.php?hash=ab7b055dbff84f03dfb6e221d0a05a94&type=js
The f1 dropper appears to be constant, md5: db2d3584fdbacdb7fd58fadc558144ae
https://www.virustotal.com/en/file/6d55150b066434d213074c200e2d1b8485cada62d1472e0013f10c7f136c58b7/analysis/
The final executable payload has very low detection on VirusTotal, currently 3/45, md5: 9e48716f33aa98dd7ecd387d9546b70c https://www.virustotal.com/en/file/ea572f741d5d229a271d333d81b8bc28f5c6240c9b44e70ae42ab943f1a73566/analysis/
I didn’t decompile the flash object or JARs but in the past I’ve seen the Java, Reader, and Flash droppers all dropping the same payload, based on the very low detection at the moment I’m guessing that’s the case here as well. The metadata on the file appears to be gibberish so it’s a pretty safe bet that the binary rotates regularly as well.
Sorry for the long post and all of the links, hopefully it’s of use to others.
matt
Mar 19th 2013
1 decade ago
pogue
Mar 20th 2013
1 decade ago