Is it Spam or Is it Malware?
The Friend
Does anyone have a friend that regularly still sends you crap via email that usually includes a link or some pic's? We are all IT security professionals here and know the preacher's drill on this topic. Really, we do not like wasting our time on the junk that is sent to us. Delete, Delete, Delete.
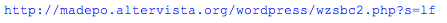
Now. We Need To Know
Did we just infect our system?
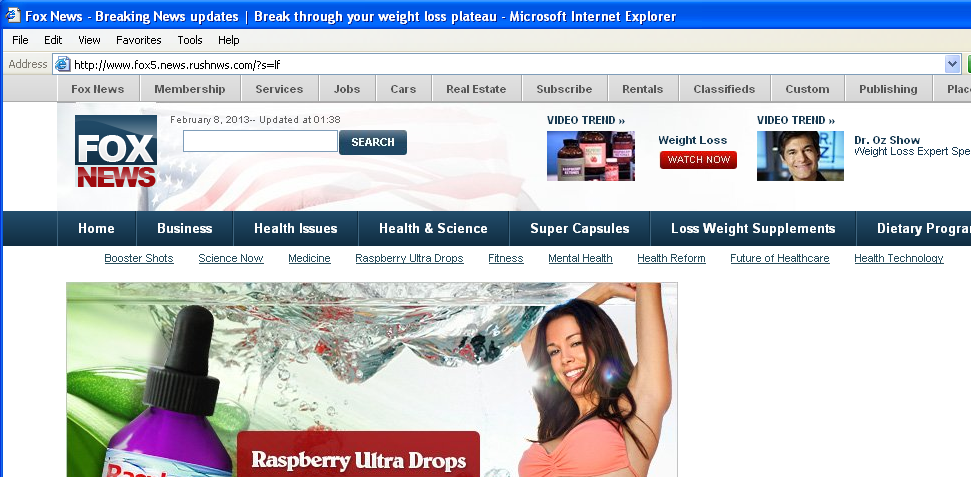
We need to know. It is time to act fast. Get to a shell and pull that page down with a text browser ala wget or curl. It is possible for this page to disappear quickly. This sample was sent in by a reader who acted fast. By the time I got around to verifying some things on this sample, the below pasted code was gone.
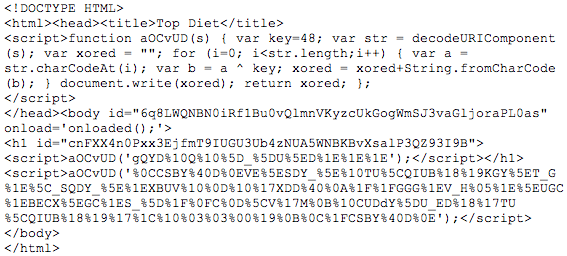
The Lazy Liston
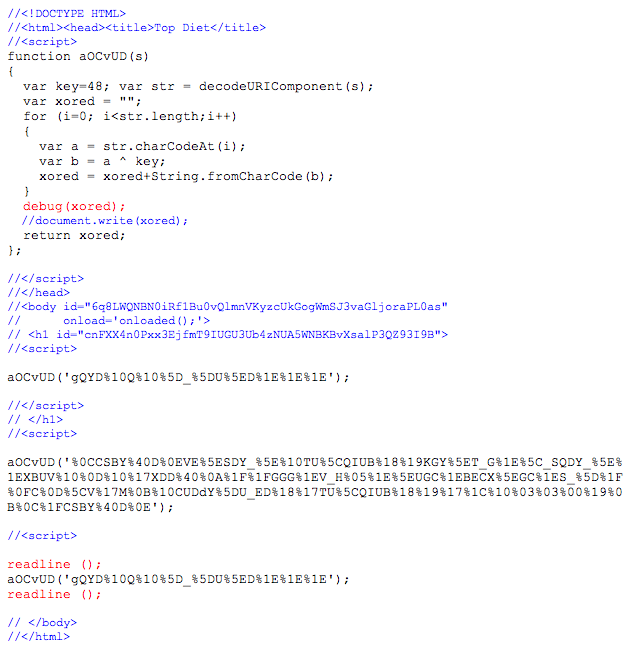
I used jsc to help me out with the prepared script above. jsc is a command line utility that allows you to run javascript interactively. I inserted a debug and a couple of readline statements to assist. The readline allows me to pause the script to view the output. Pressing enter continues it.
Below is a snapshot of the jsc run of script.js. I pasted and circled the obfuscated strings and the decoded pieces. Note the url listed matches the browser shot up above.
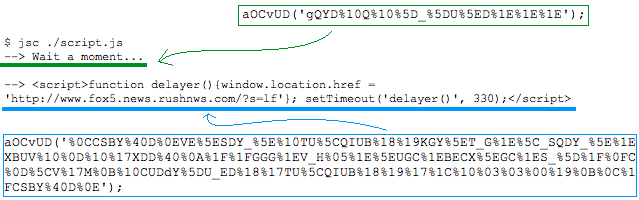
In summary, my diagnosis of the original email and sample with the clickable link, is it is only a spoofed email and intended to be spam. I humbly encourage all to offer any feedback to counter my assessment or offer any added value to it. Many thanks to Lode V. for sending it in!
-Kevin
--
ISC Handler on Duty


Comments
Never without "noscript".
Jens
Feb 8th 2013
1 decade ago
patermann
Feb 8th 2013
1 decade ago
Hope this helps!
patermann
Feb 8th 2013
1 decade ago
pogue
Feb 8th 2013
1 decade ago
I don't assume that's what happened here, but using wget/curl to get the source or trying to safely download a malware sample, is likely to fail.
If the attacker backdoored the site they may change the redirect, or upload different code, at any time after the link was emailed to people. So it's still a threat even if it was initially something inoccuous.
Steven Chamberlain
Feb 8th 2013
1 decade ago
Taking it further, if policy is to log all web activity, you could search those logs for previous hits on the infected blog; you could maybe scan unread mails in mailboxes for the URL and spam/trash them.
Steven Chamberlain
Feb 8th 2013
1 decade ago
Thanks for the Q/A patermann. I fixed the links.
Steven, excellent input. For what it is worth, I did open the page reviewed above to capture the browser shot in a secured VM. I ran regshot before and after the page load to confirm nothing malign was at play. Your note about about it changing at any time is definitely true and does not mean the link will always be benign.
Kevin Shortt
Feb 8th 2013
1 decade ago
I'll repeat this again: when analysis of obfuscated javascript yields a domain name, *PLEASE* report that domain name to MalwareDomains.com so that it can be filtered by others. In this case I'd have reported both madepo.altervista.org and rushnws.com
Thanks!
John Hardin
Feb 8th 2013
1 decade ago
pogue
Feb 9th 2013
1 decade ago
For malwaredomains.com you can email to the contact address on the "About us" page: http://www.malwaredomains.com/?page_id=2
I've been informed that if you know that it is hosting only spam rather than malware they (malwaredomains.com) would rather not be notified, they are only interested in malware host sites and (I assume) C&C hosts. I don't know whether malwaredomainlists.com has a similar policy, I haven't asked them.
It would be a good idea to submit to both. I don't know to what degree they overlap. I combine both lists for my proxy's filter, but some people may only use one or the other.
John Hardin
Feb 11th 2013
1 decade ago