Port 1434: Sudden Slammer Decline?
We're interested to know what's happening out there. It has been observed through DShield data that Slammer traffic has had a sudden decline. I played with the data for a while. I could make it look like many things, such as slow and steady decline over time. However, the most compelling story is the one where the data drops on March 9 and 10.
Below is the DShield data and graph on port 1434 for March 2011. It's speculative at this point as to the cause of the sudden drop. Japan's earthquake or Patch Tuesday have been kicked around. I would be remiss if I did not mention Kevin Liston's series on Slammer Cleanup during October. We are loving the thought his great effort was a catalyst for the eradication of it.
So go back and take a look at your data for us and share what you're seeing. Send us your thoughts on this.
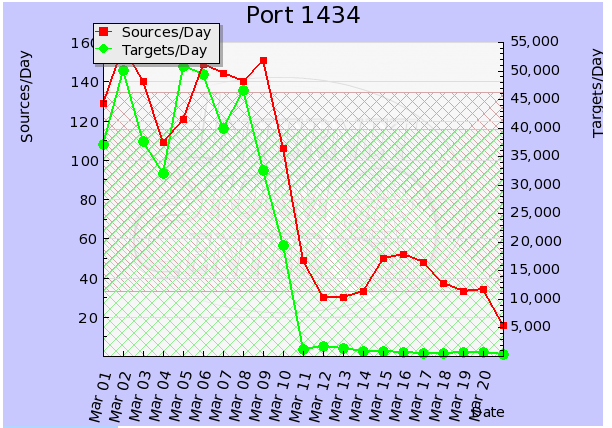
# portascii.html # Start Date: 2011-03-01 # End Date: 2011-03-21 # Port: 1434 # created: Mon, 21 Mar 2011 10:15:34 +0000 # Date in GMT. YYYY-MM-DD format. date records targets sources tcpratio 2011-03-01 42862 37215 129 0 2011-03-02 62157 50028 158 0 2011-03-03 46789 37745 140 0 2011-03-04 37634 32068 109 0 2011-03-05 62649 50868 121 0 2011-03-06 62221 49475 149 0 2011-03-07 44110 39895 144 0 2011-03-08 60921 46609 140 0 2011-03-09 38503 32512 151 0 2011-03-10 23459 19438 106 0 2011-03-11 1411 1282 49 1 2011-03-12 1740 1702 30 0 2011-03-13 1414 1384 30 1 2011-03-14 1151 944 33 0 2011-03-15 1256 883 50 2 2011-03-16 1021 667 52 4 2011-03-17 1542 599 48 2 2011-03-18 978 515 37 8 2011-03-19 794 639 33 3 2011-03-20 766 635 34 3 2011-03-21 533 435 16 1 # (c) SANS Inst. / DShield. some rights reserved. # Creative Commons ShareAlike License 2.5 # http://creativecommons.org/licenses/by-nc-sa/2.5/ |
--
Kevin Shortt
ISC Handler on Duty


Comments
Sebastien
Mar 21st 2011
1 decade ago
One thing I am playing around with is Dionea hxxp://dionaea-carnivore-it. This emulates a bunch of things that are considered worm food, one being ms-sql. That has dropped in hits as well..but I have to wonder if we got Dionea running around the world if we couldn't trick Slammer back to life?
@HackDefendr
Mar 21st 2011
1 decade ago
pwobbe
Mar 21st 2011
1 decade ago
I realize there are many legal and ethical problems with executing code on someone else's system, but depending what country you live in, your local law enforcement might not care about computer crimes. And besides, if someone is so negligent that they have allowed their computer to be infected with Slammer for 8 years, it's highly unlikely that they have a firewall or any type of logs that would let them even identify who was responsible for the "attack."
To test this theory, I suppose you could set up a host intentionally infected with Slammer, let it blast packets out onto the internet for a while, and run a packet capture to see if any "interesting" responses start coming your way on UDP 1434.
AlexB
Mar 22nd 2011
1 decade ago
We saw a drop already on Tue 03/08/2011 and since
03/10/2011 11:10 (UTC+1) slammer seems to be marginalized.
Maybe the big chinese wall did the trick?
URL with our view:
http://www-users.rwth-aachen.de/Jens.Hektor/end-of-slammer-flows-rwth.png
(note: the "unallocated" block is due to my laziness in updating the latest IPv4 assignments - but this classification was only rough anyway)
Time window: 2011-03-08 21:49:52 - 2011-03-10 11:14:54:
IP Addr Flows(%)
150.140.187.X 168047(66.5)
61.178.13.X 17272( 6.8)
200.203.126.X 17057( 6.7)
217.149.5.X 15232( 6.0)
178.150.208.X 4933( 2.0)
120.202.76.X 2983( 1.2)
98.100.142.X 2950( 1.2)
170.210.60.X 2929( 1.2)
61.58.25.X 2065( 0.8)
203.174.36.X 1692( 0.7)
Jens
Mar 22nd 2011
1 decade ago
@HackDefendr
Mar 31st 2011
1 decade ago