Struts "devmode": Still a problem ten years later?
Like many similar frameworks and languages, Struts 2 has a "developer mode" (devmode) offering additional features to aid debugging. Error messages will be more verbose, and the devmode includes an OGNL console. OGNL, the Object-Graph Navigation Language, can interact with Java, but in the end, executing OGNL results in arbitrary code execution. This OGNL console resembles a "web shell" built into devmode.
No matter the language, and the exact features it provides, enabling a "devmode", "debug mode" or similar feature in production is never a good idea. But it probably surprises no one that it still shows up in publicly exposed sites ever so often. Attackers know this as well, and are "playing" with it.
To take advantage of devmode, an attacker would request a URL like:
/[anything].action?debug=command&expression=[OGNL Expression]
I noticed today that one URL in this format is showing up in our "first seen" URLs:
/devmode.action?debug=command&expression= (#_memberAccess["allowStaticMethodAccess"]=true, #foo=new java.lang.Boolean("false") , #context["xwork.MethodAccessor.denyMethodExecution"]=#foo, @org.apache.commons.io.IOUtils
For readability, I URL decoded and added spaces. This URL is likely just a scan for vulnerable systems. I ran a quick database query to see if we have other similar URLs recently. Indeed we had 2,443 distinct URLs in our database. Most of them follow this pattern:
debug=command&expression=(43867*40719)
Again, a simple check is performed to see if a system is vulnerable. Scans for this issue are sporadic, but we have had some notable increases recently. An old issue like this often comes back as people start to forget about it, so take this as a reminder to double-check your systems.
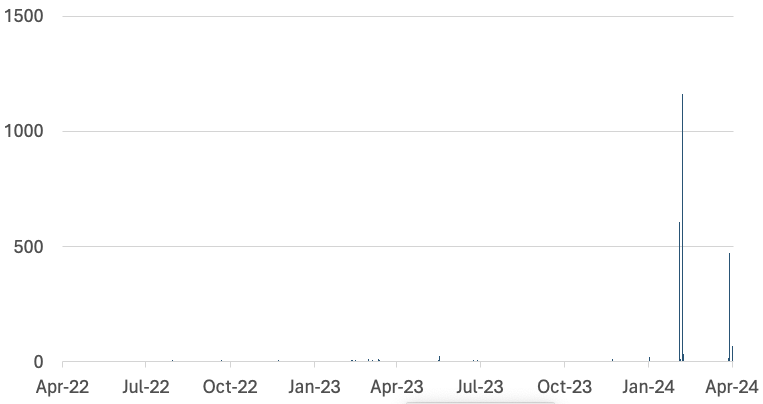
I am plotting the last two years below, and you see big spikes on February 24th, 27th, and April 19th this year.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments