Zarya Hacktivists: More than just Sharepoint.
Last week, I wrote about a system associated with pro-Russian hacktivist scanning for vulnerable Sharepoint servers [1]. Thanks to @DonPasci on X for pointing me to an article by Radware about the same group using Mirai [2][3]. This group has been active for a while, using various low-hanging fruit exploits to hunt for defacement targets.
The group calls itself "Zarya" (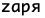 ). The Cyrillic alphabet does not contain the letter "z." After Russian troops used the "Z" symbol to mark their vehicles in their push on Kyiv early in 2022, the character became a popular symbol to express support for the war in Russia. It has often been used to replace the letter "
). The Cyrillic alphabet does not contain the letter "z." After Russian troops used the "Z" symbol to mark their vehicles in their push on Kyiv early in 2022, the character became a popular symbol to express support for the war in Russia. It has often been used to replace the letter "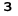 ," which is pronounced like the English "Z." Therefore, the name of the hacktivist group is likely supposed to be pronounced as "
," which is pronounced like the English "Z." Therefore, the name of the hacktivist group is likely supposed to be pronounced as " ," or "dawn" in English.
," or "dawn" in English.
But let's return to the IP address we identified last week: 212.113.106.100. This IP address has not been idle since then. We have observed several different exploits with our honeypots.
Many of them are just simple recognizance. Requests for "/" to retrieve index pages. These are likely just used to identify possible targets.
There are also some directory traversal attempts. I have no idea if they will work with reasonably up-to-date systems. In particular, requests like "/../../../../etc/passwd".
Some of the directory traversal attempts are going after more specific vulnerabilities: /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/config/nodogsplash . "nodogsplash" is a captive portal designed for OpenWRT based routers. I can't find a specific directory traversal vulnerability documented for this extension. If you have the nodogsplash installed, See if this works and let me know.
There are several additional exploit attempts like this, hunting for configuration files. For example /ajax-api/2.0/mlflow-artifacts/artifacts. Straight from the MLflow web page, "MLflow provides a unified platform to navigate the intricate maze of model development, deployment, and management." MLFlow has also been probed recently by 139.59.79.166, and that software may deserve some additional investigation.
And just simple access to admin APIs like, for example, this Coldfusion URL: ///CFIDE/adminapi/accessmanager.cfc . This URL was recently probed by 18.218.123.107.
None of the other IPs probing the same vulnerabilities ( 18.218.123.107 and 139.59.79.166) display the defacement page. However, the similarity of the exploit scans may suggest some coordination. However, the user agent strings suggest that different tools are used for the scans.
Currently, Shodan only shows two IP addresses with the defacement banner. 212.113.106.100 and 185.174.137.26. The second IP shows similar "random" attacks, searching for configuration files and other simple exploits.
Geolocation of the IPs is a bit tricky. Both IPs reverse resolve to aeza.network, a low-cost hosting provider. The mailing address listed on the provider's homepage is a small townhouse in Sheffield, across the street from Sheffield Soccer Stadium. Aeza maintains data centers in several European locations but has a significant presence in Russia. Aeza uses Whois to point to a file with additional geolocation details for its address space [4]. According to this file, 212.113.106.100 is in Vienna, Austria, and 185.174.137.26 is in Helsinki, Finland. Traceroute results are inconclusive. The last responding hop for both hosts is 89.187.184.98, which appears to be in England.

I notified the ISP last week. The ISP has not responded, and the sites are still actively scanning. However, it is not unusual for ISPs and hosting providers to ignore abuse reports.
Zarya isn't exactly the type of threat you should be afraid of, but it is sad how these groups can still be effective due to organizations exposing unpatched or badly configured systems to the internet. Most of the attacks sent by Zarya will not succeed even if they hit a vulnerable system. For some added protection, you may consider blocking some of the Aeza network's traffic after ensuring that this network hosts no critical resources you need. Aeza uses ASN 210644.
[1] https://isc.sans.edu/diary/Pro+Russian+Attackers+Scanning+for+Sharepoint+Servers+to+Exploit+CVE202329357/30436/
[2] https://twitter.com/DonPasci/status/1730256497693593880
[3] https://www.radware.com/security/threat-advisories-and-attack-reports/pro-russian-hacktivists-leverage-mirai-botnets/
[4] https://aeza.net/static/ipv4_f.csv
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments