HTML phishing attachment with browser-in-the-browser technique
Although the browser-in-the-browser (BitB) technique has been with us for a while now[1], it is far from what one might call ubiquitous. Simply put, the technique is based on displaying a simulated browser pop-up window (usually a login prompt) within the confines of an HTML page opened in a browser. The simulated pop-up may look almost indistinguishable from a real browser window and since it may contain an arbitrary URL in the simulated address bar, the use of the BitB technique for phishing can be quite effective, as most people have been repeatedly taught that they should “check the URL, and if it is the right one, the page should be genuine” during security awareness courses.
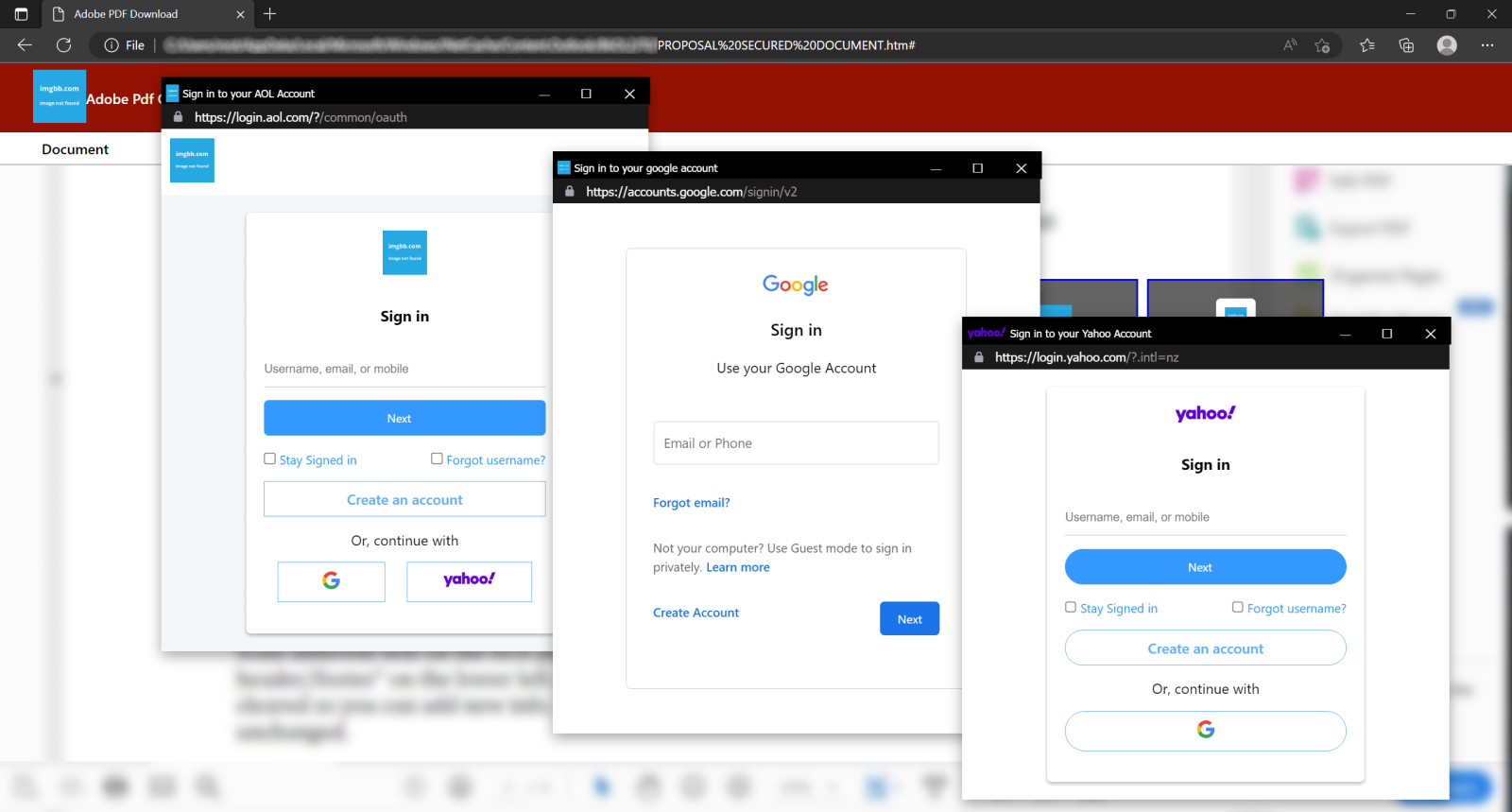
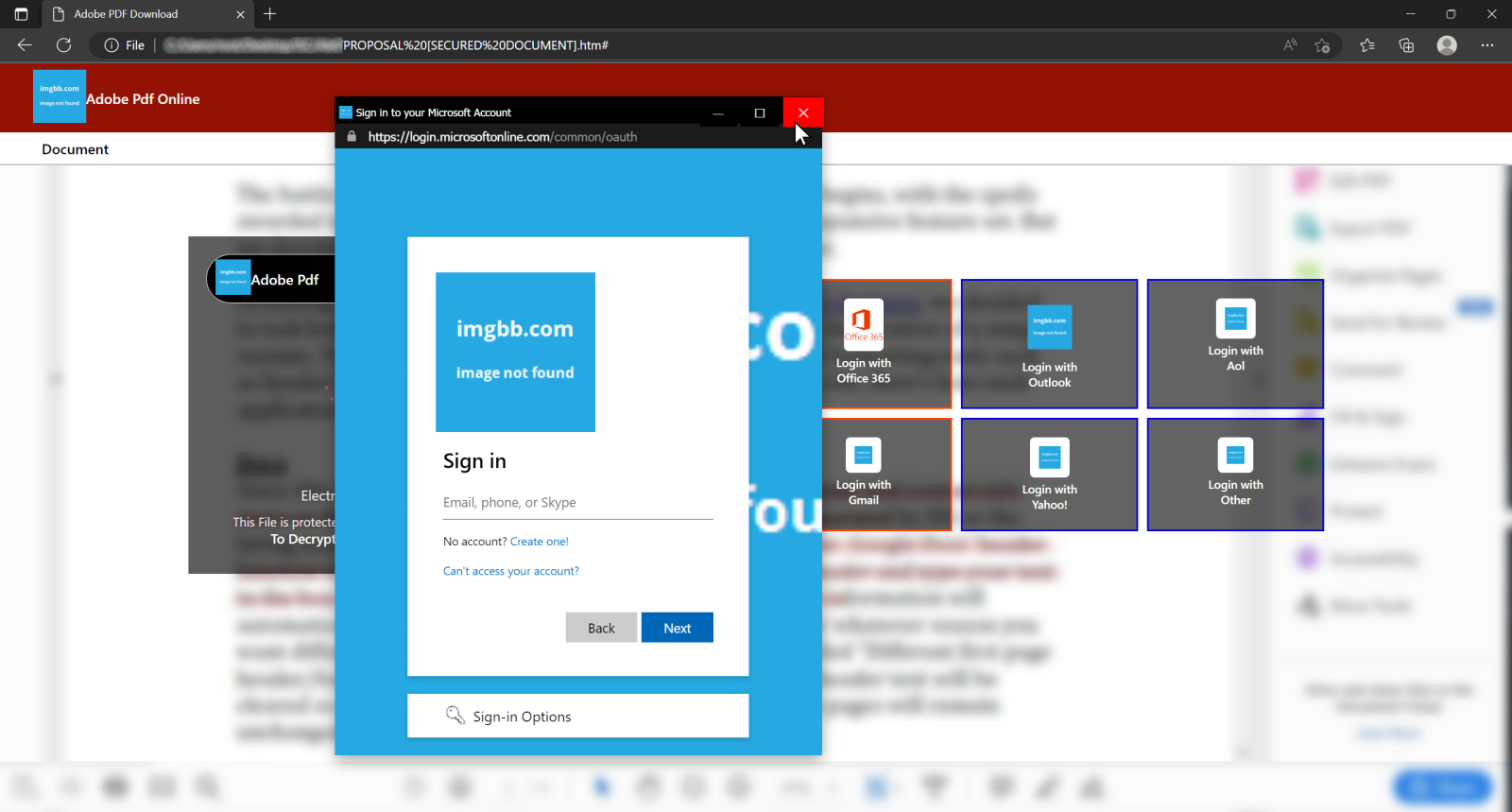
Checking the URL is undoubtedly still a good advice, however, when it comes to BitB, one should probably preface it by saying, that one first has to make sure that a browser window is actually a real browser window and that its address bar is actually a real address bar… Unlike in the example shown in the following image.
Even though the BitB technique has been repeatedly used by threat actors in the wild in targeted attacks[2,3], it hasn’t so far become the “default go to” for authors of phishing websites... Which is why I was a little surprised to find a generic phishing e-mail with an HTML attachment using this technique in my spam trap last week.
The e-mail itself had an empty body and – besides the fact that it originated from a SendGrid server, which seems to be used by the legitimate owner of the domain, and thus passed both SPF and DKIM checks – was completely uninteresting.
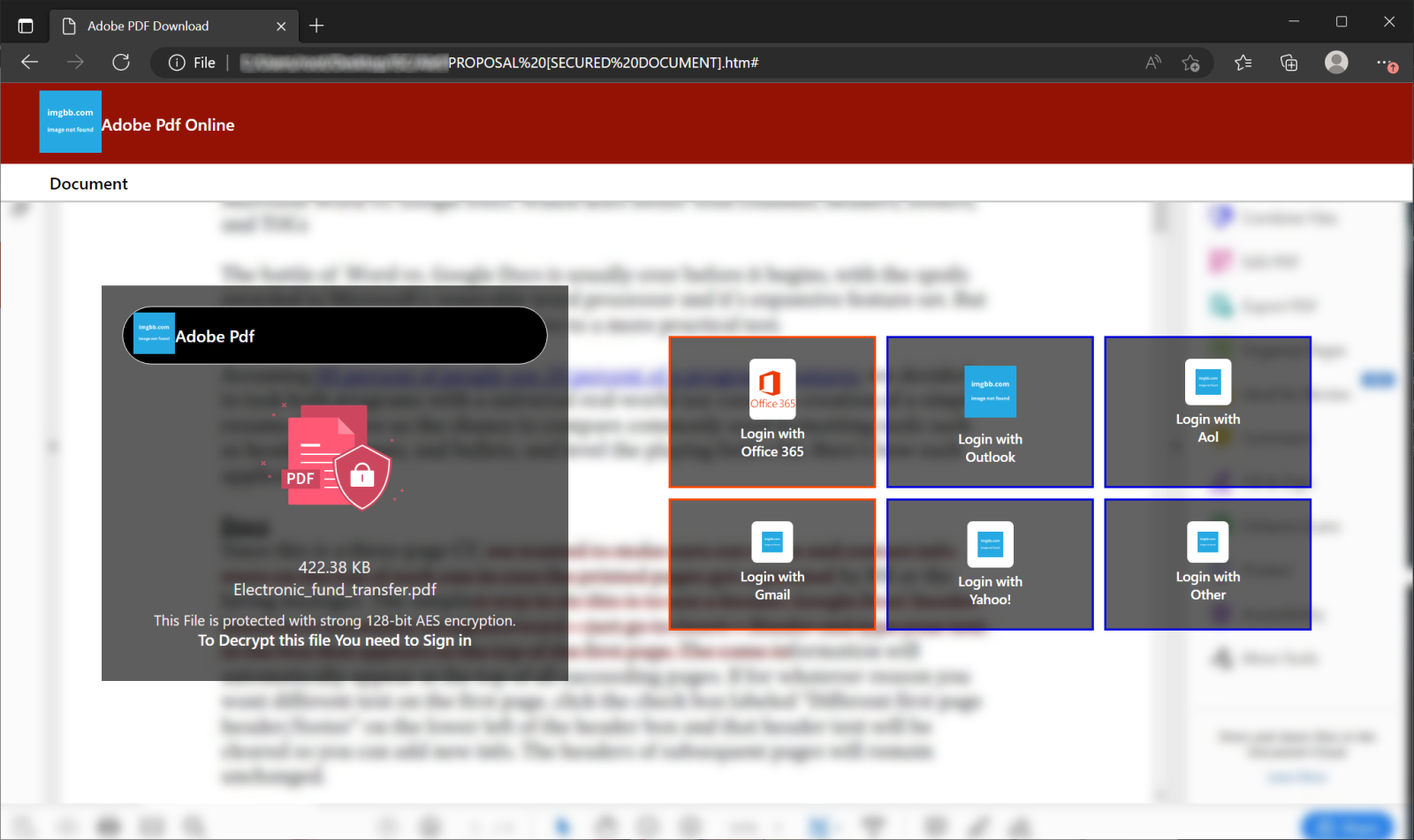
At a first glance, the attachment looked just as uninteresting and run-of-the-mill as the e-mail itself.
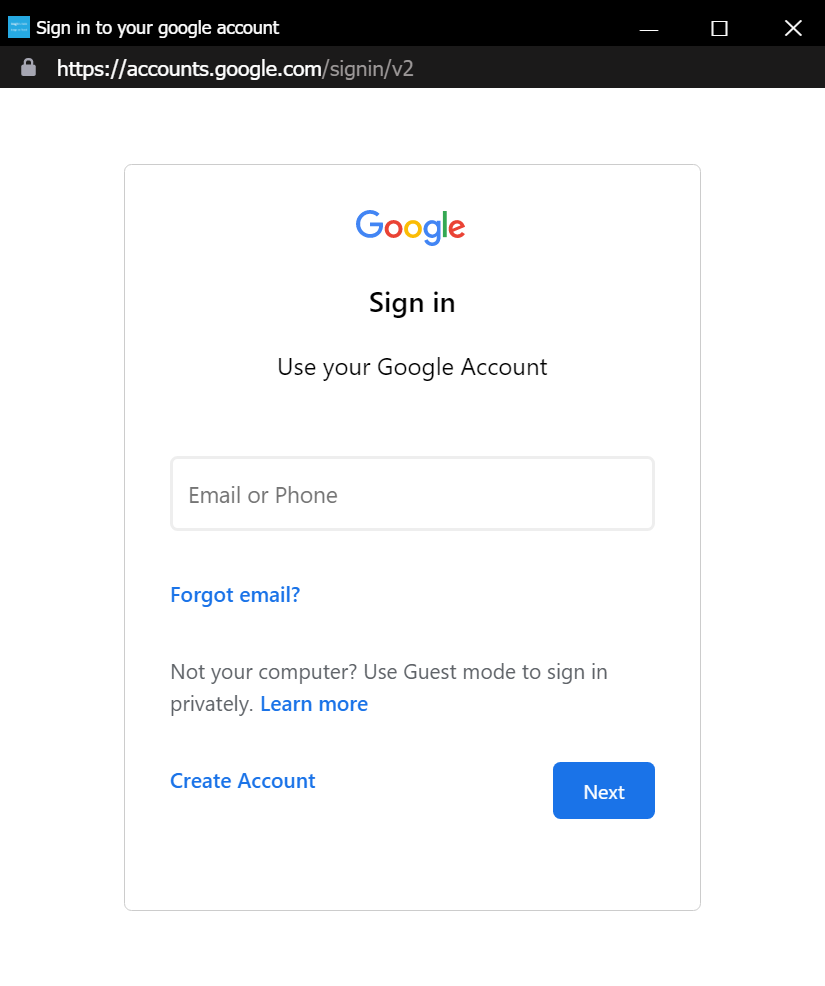
However, on a closer look, it proved to use the BitB technique to display fake pop-up login prompts if one of 5 of the 6 login options were selected. The displayed pop-ups looked somewhat convincing and behaved to a limited extent (it was possible to move them around on the screen, but not to resize/minimize/maximize them in any way) similarly to how real pop-ups would.
The code behind the HTML attachment turned out to be notable in two ways – first, it wasn’t obfuscated, which is quite unusual these days for HTML phishing attachments, and second, the sections of code used to display and control the pop-ups weren’t the same for all windows and, in a strange turn of events, didn’t contain the same functionality.
As a result, only the login pop-up for O365/Outlook (which, as you may see, tried to load images from external site that were no longer available at the time of writing) performed any animation when one hovered a mouse cursor over the minimize, maximize and close buttons on its top bar. All other simulated pop-up windows were completely unresponsive to such interaction.
As we already mentioned, the use of BitB in phishing is currently not yet as common as are some other techniques. And though this is quite fortunate, one can reasonably expect the situation to change, as there is no reason why threat actors wouldn’t use the technique more, given its potential effectiveness… Or, rather, as the example described above shows, the situation is slowly changing already.
Therefore, one recommendation that can be made to any security professionals out there, who are responsible for building security awareness within their organizations, would be to include a mention of the browser-in-the-browser technique in any educational/awareness materials their organizations might use for employee/end-user training, along with some pointers on how to spot the use of BitB. The most straightforward method for identifying BitB windows would probably be to try to move the pop-up outside of the parent browser window, but the lack of an icon for the pop-up window on a taskbar or possible issues with interactivity of the pop-up window might be good points to mention as well…
[1] https://mrd0x.com/browser-in-the-browser-phishing-attack/
[2] https://blog.google/threat-analysis-group/tracking-cyber-activity-eastern-europe/
[3] https://www.darkreading.com/attacks-breaches/steam-gaming-phish-showcases-browser-in-browser-threat
-----------
Jan Kopriva
@jk0pr
Nettles Consulting


Comments