Word Maldoc With CustomXML and Renamed VBAProject.bin
Friend and colleague 0xThiebaut just gave me a heads up for this interesting sample: 2056b52f8c2f62e222107e6fb6ca82708cdae73a91671d40e61aef8698e3e139
This is what we get with oledump.py:
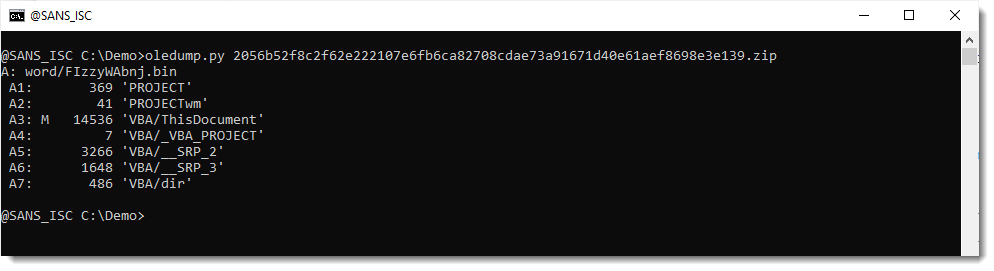
As there seems to be quite a lot of VBA code, I use plugin plugin_vba_dco to give me a summary:
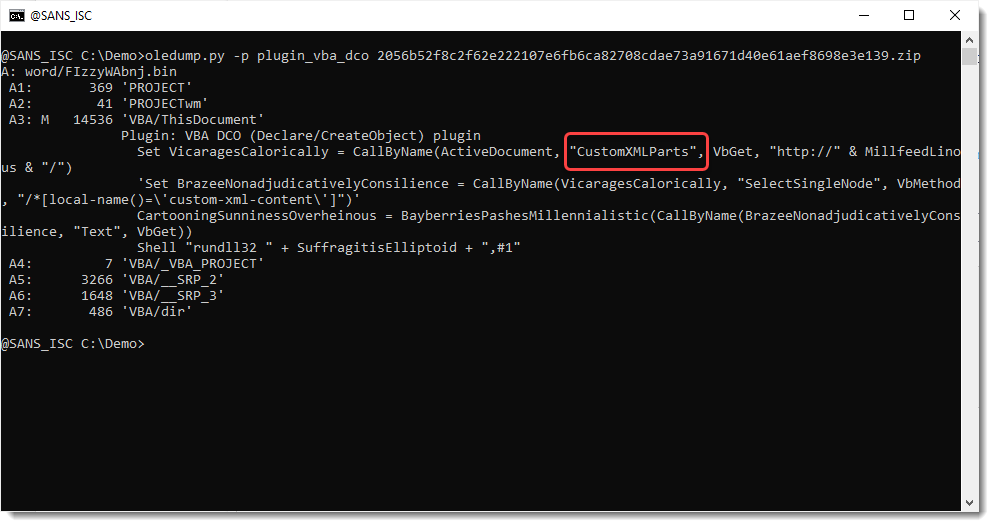
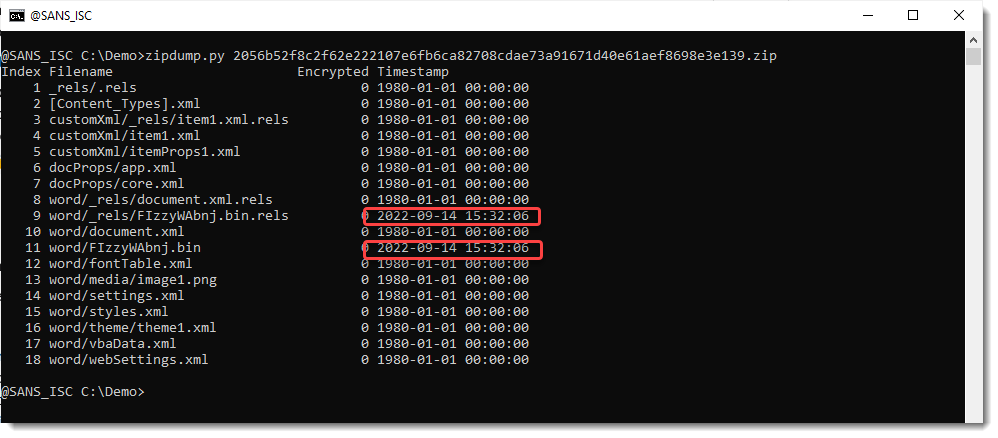
I notice the CustomXMLParts, and I take a look with zipdump.py (because this is an OOXML file):
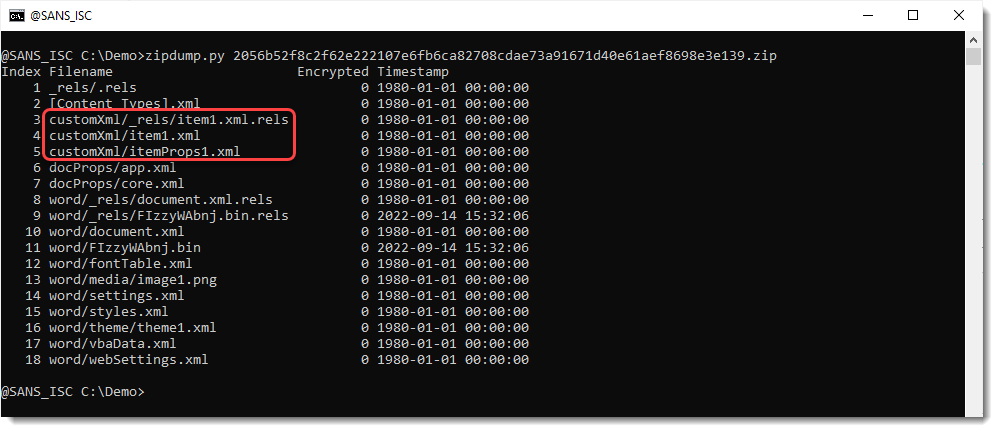
Taking a look at the content of customXml/item1.xml:
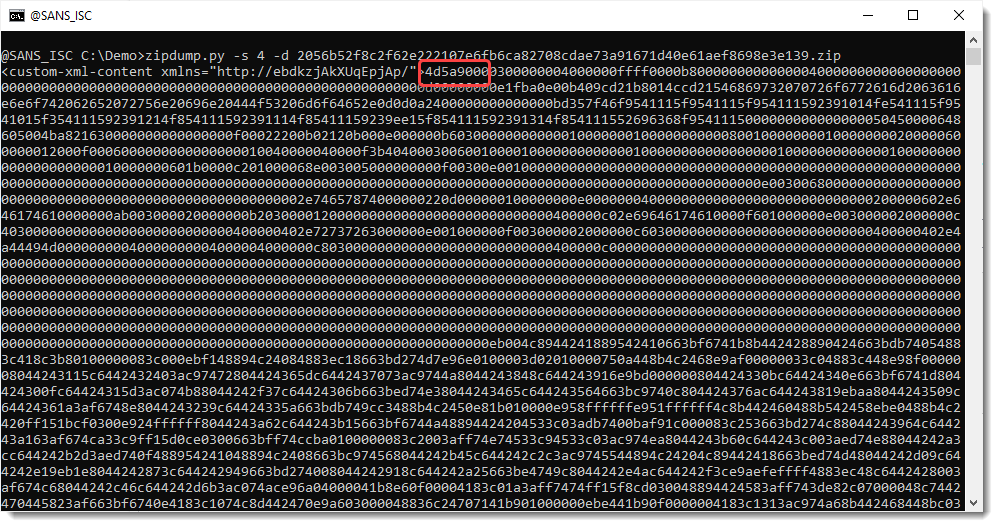
And I see a MZ header (4d5a), so this must be a PE file. Let's extract it with base64dump.py:
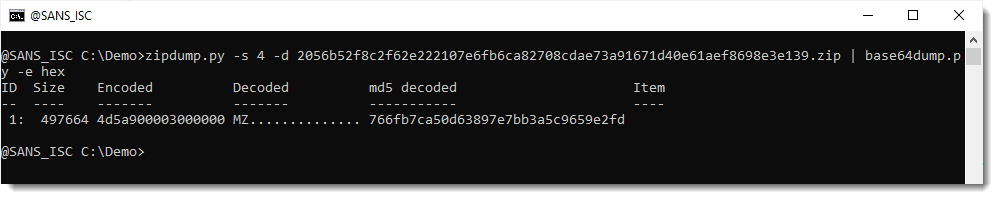
And this is the embedded payload: 766fb7ca50d63897e7bb3a5c9659e2fd (IcedID).
There's more interesting things to notice about this sample. One of them is that the VBA project file (ole file) is named FIzzyWAbnj.bin in stead of the usual VBAProject.bin.
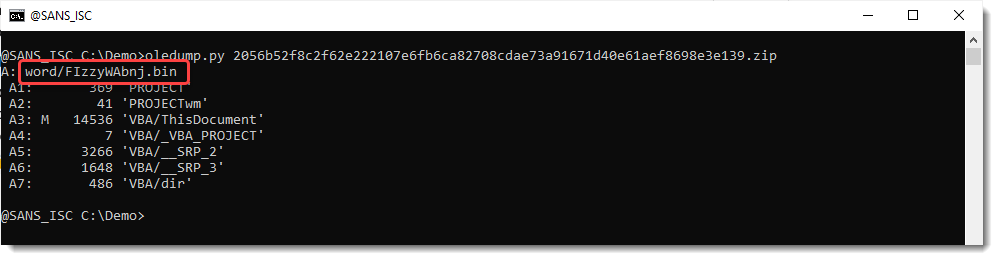
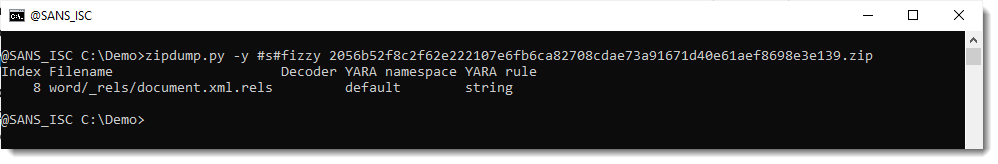
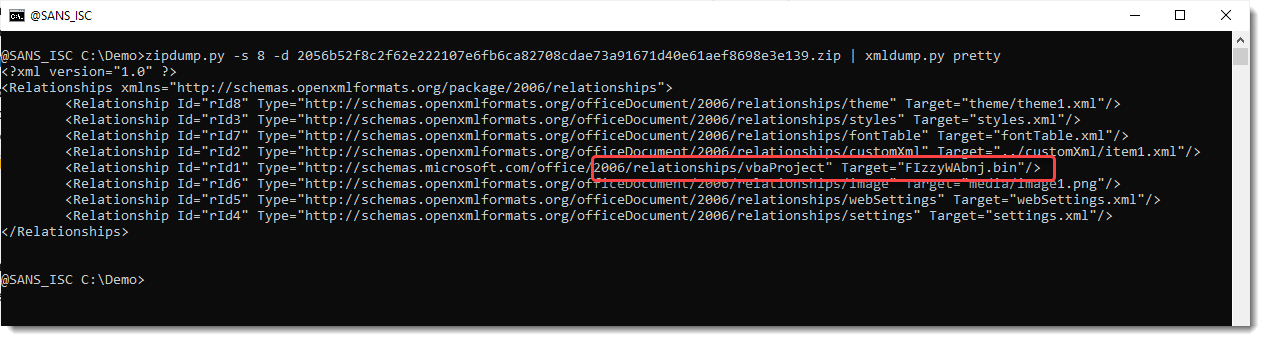
And some tampering:
There's maybe more to discover, but I'm on holiday :-)
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments