James Webb JPEG With Malware
On Wednesday's stormcast, Johannes talked about a JPEG picture (coming from the Jales Webb telescope) that malware authors had laced with malware.
I always like to take a look at such images with my analysis tools, like jpegdump.py.
This is the picture laced with malware.
When I run jpegdump.py on this picture, I get an overview of all the segments:
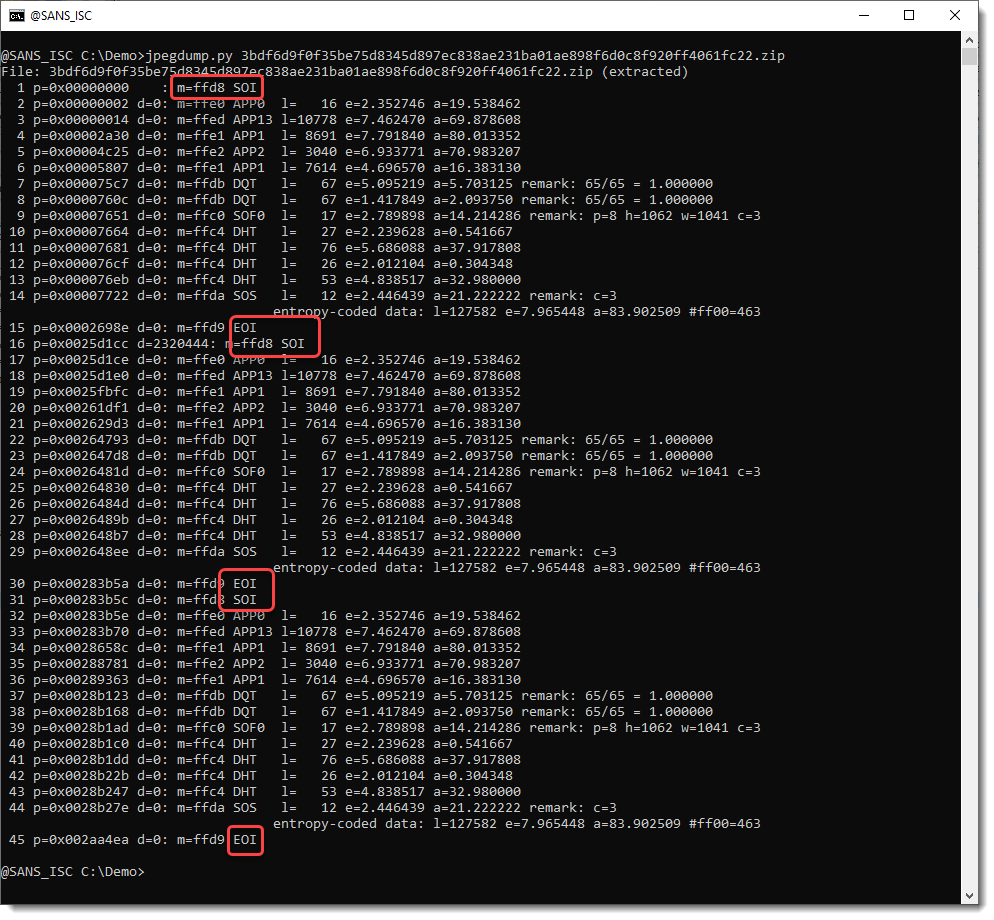
In a "normal" JPEG picture, you will find one Start Of Image (SOI) segment as the first segment in the file, and one End Of Image (EOI) segment as the last segment in the file.
Here we find 3 different SOIs and EOIs. Segments 1, 16 and 31 are SOI segments. anf Segments 15, 30 and 45 are EOI segments.
So there are 3 jpeg images in this file.
To check if these images are the same, I use option -E to display the hash of the data of each segment (I use MD5 for the demo here because it gives shorters strings than sha1 and sha256, and thus will not line wrap).
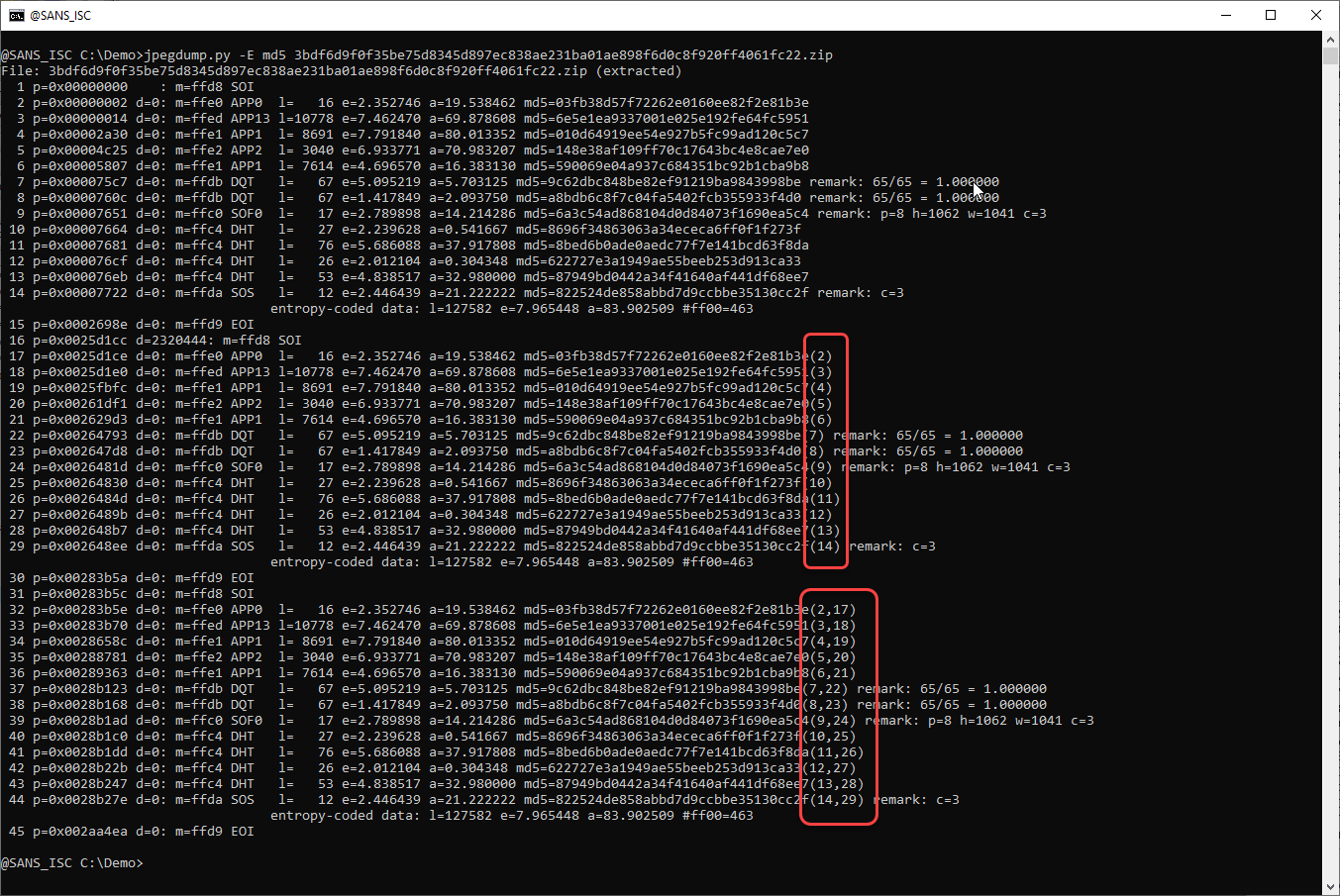
Notice that for the second and third JPEG image (between SOI and EOI), all the hash values are followed by parentheses and numbers.
Like for segment 17: md5=03fb38d57f72262e0160ee82f2e81b3e(2)
This means that the hash of the data of segment 17, is the same as the hash of the data of segment 2. Thus that the data is the same, if you don't fear md5 collisions (and if you do, just use sha256).
And that is the case for all segments of the second and third JPEG image. So what we have here, is a concatenation of 3 identical JPEG pictures.
Next, notice that the difference (d= value) of segment 16 is not 0.
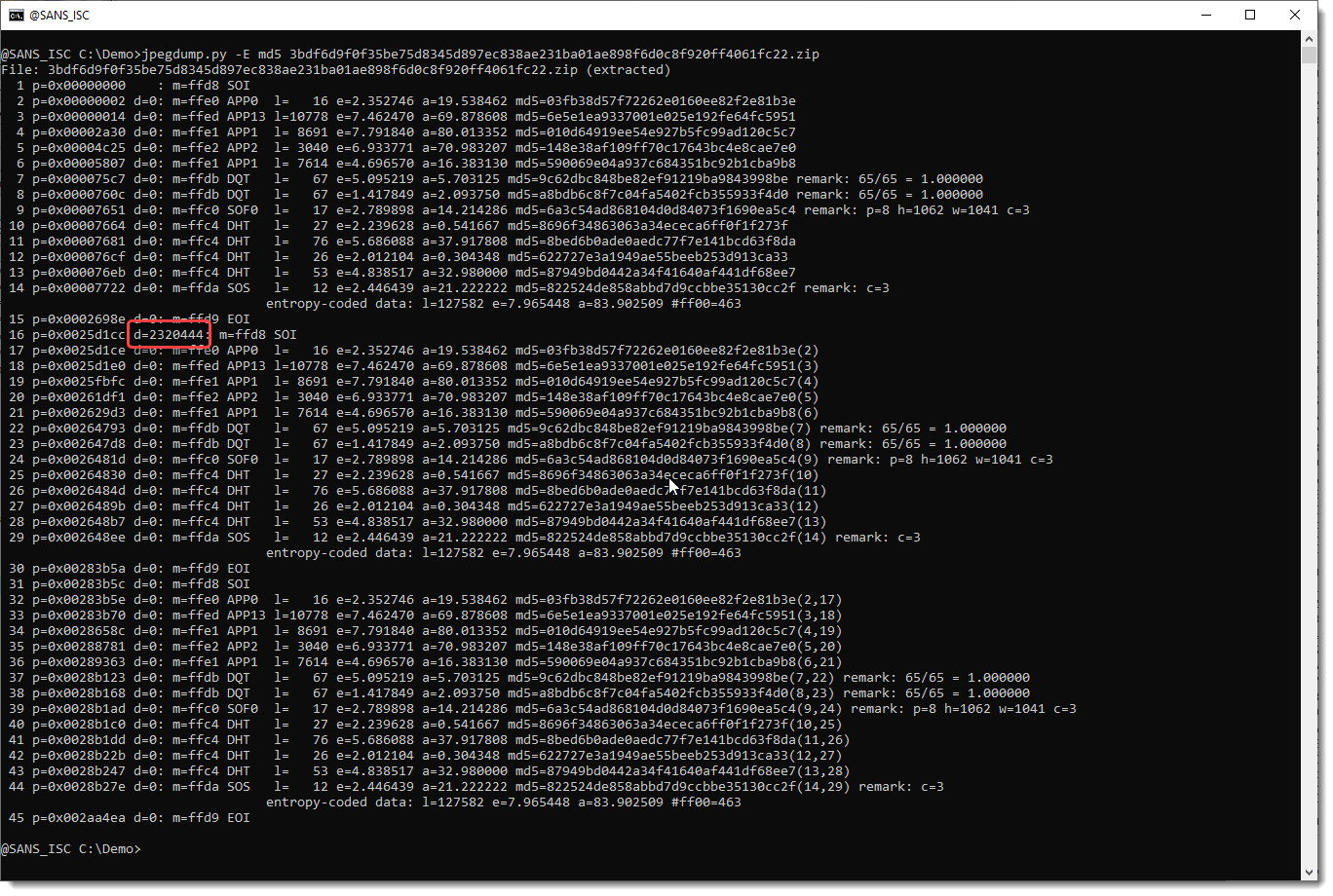
This means that there is some data between segment 15 and segment 16. d=2320444 means that there are 2320444 bytes of data between EOI (segment 15) and SOI (segment 16).
We can select this data as follows: -s 16d (select the data between segment 15 and 16)
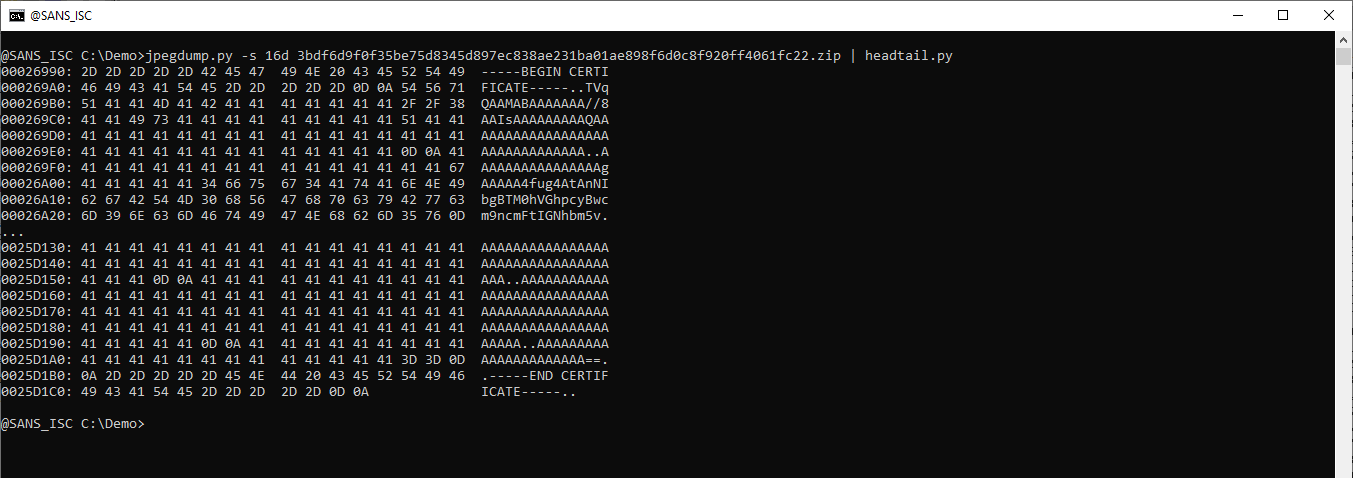
This looks like a certificate in ASCII. Let's dump it:
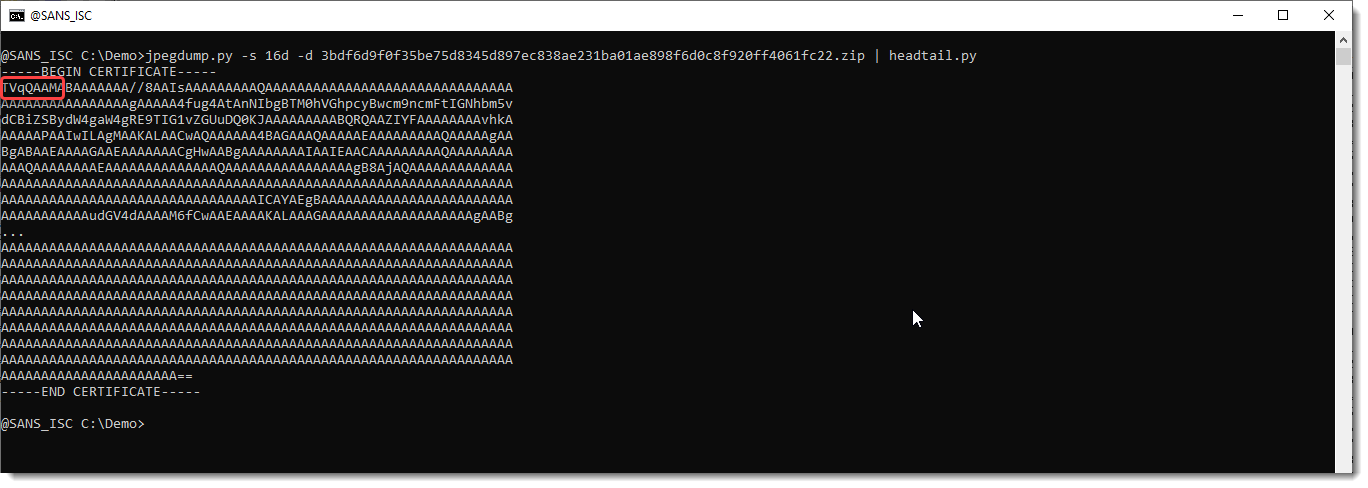
This is indeed a certificate. Notice that it starts with TV: that means that the data that was BASE64 encoded, starts with MZ. The magic header of a PE file.
A valid certificate should have letter M as first letter of the BASE64 data (and not T).
Let's decode this with base64dump.py (option -w ignores all whitespace):
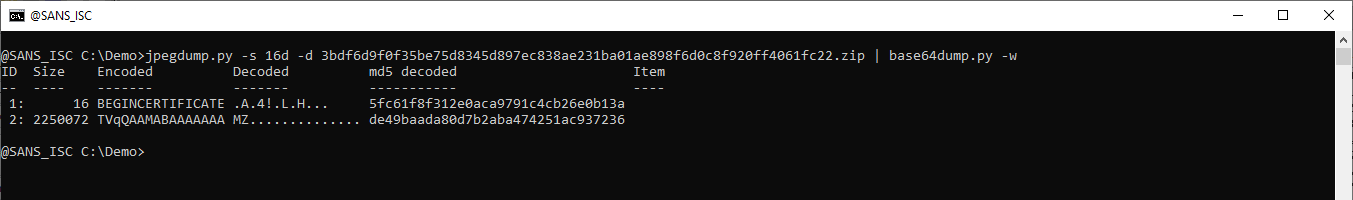
And this is indeed a PE file.
Thus, what the malware authors did was equivalen to: copy /b webb.jpeg + malware.crt + webb.jpeg + webb.peg malware.jpeg
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments