Underscores and DNS: The Privacy Story
The use of underscores in DNS records can easily trigger DNS purists into a rage. Since the beginning of (DNS) time, only the letters a-z, numbers, and dashes are allowed in DNS labels (RFC 1035 section 2.3.1). After all, we want to remain compatible with ARPANET.
So but what about DNS records like "dkim._domainkey.1105info.com"? Clearly, there is an underscore. Is this valid? The simple justification is that these are TXT records, not host names. So the ARPANET backward compatibility doesn't apply, and underscores are okay.
But that isn't all. I noticed a while ago (maybe I already wrote about it a couple of years back but forgot about it... anyway, the question came up again earlier today....
Let's check out the query Arkime parsed so nicely for us:
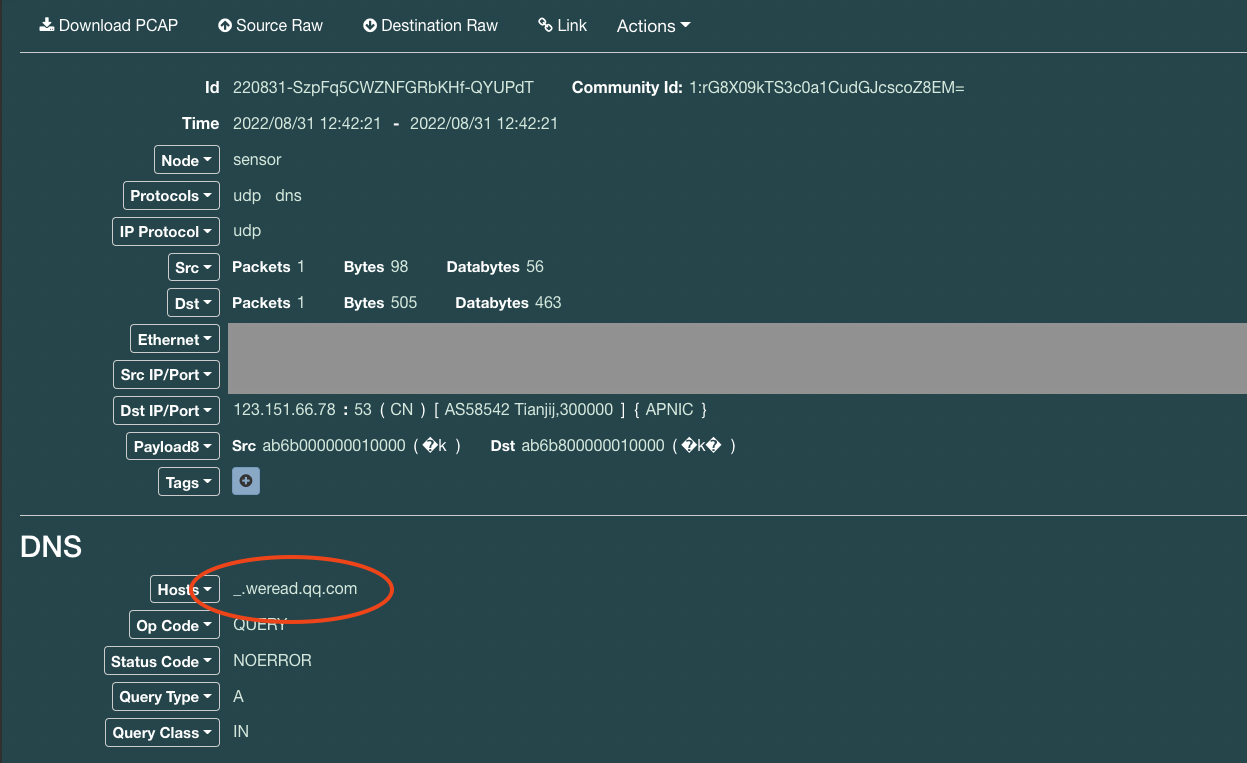
Here we request an "A" record for "_.weread.qq.com." So what's that about? The destination, 123.151.137.18, is a valid name server for qq.com:
% dig qq.com NS +short
ns2.qq.com.
ns3.qq.com.
ns4.qq.com.
ns1.qq.com.
% dig qq.com A ns2.qq.com +short
183.3.226.35
61.129.7.47
123.151.137.18
So we expect to hit that server as our recursive server (the query source) attempts to resolve example.weread.qq.com. According to textbook/classroom examples, Recursive name servers send the hostname they are attempting to resolve to root nameservers, TLD nameservers, and so on until they get the answer. But the makers of BIND saw a privacy issue here and also, in some ways, a performance issue. For example, you have users resolve 1.example.com, 2.example.com, and so on. These are considered distinct queries, and you are not taking advantage of caching. But if for both, you use _.example.com, caching may help you to find the NS records faster.
So BIND started sending _.example.com as part of its recursion process. Is this RFC compliant? Sure it is. There is a specific RFC, RFC 7816, describing this feature. This RFC is based on the principle that "the less data you send out, the fewer privacy problems you have." [RFC 6973]
This behavior is only seen for recursive name servers. Forwarding name servers will let the recursive server they connect worry about this. But if you see these hostnames in your logs: There is nothing to worry about, just a name server trying to keep you believing in privacy on the internet. Not sure which name servers other than BIND do use QNAME minimization.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments