Using Referers to Detect Phishing Attacks
“Referers” are useful information for webmasters and system administrators that would like to have a better overview of the visitors browsing their websites. The referer is an HTTP header that identifies the address of the web page from which the resource has been requested.
For my corporate website, I have a weekly report that shows me the referers from the past week, the number of hits, etc. This helps me to detect if interesting visitors hit me and where they are coming from. Besides all the search engine stuff, it helps to learn if I’m referenced here and there.
This week, I found an interesting referer that looked suspicious:
hxxps://firebasestorage[.]googleapis[.]com/v0/b/ptr2806ge.appspot.com/o/%5C%5Cptr2806g%2Findex2ptr.html?alt=media&token=1835e8a1-64d2-4fe6-9c37-16727092f0e8
If you visit this page, you will see this:
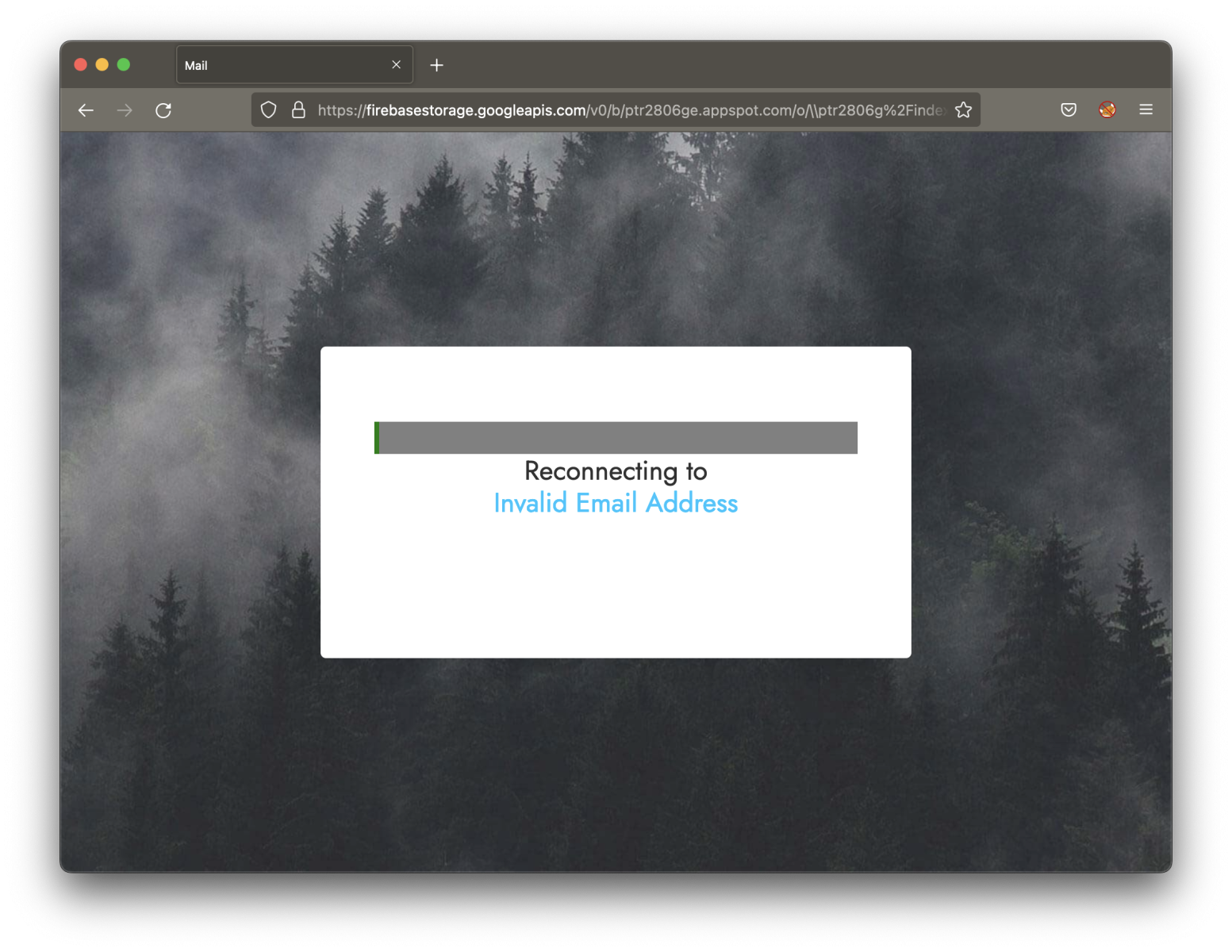
You can see that the targeted email address was not present. The original link was received in a classic phishing email:
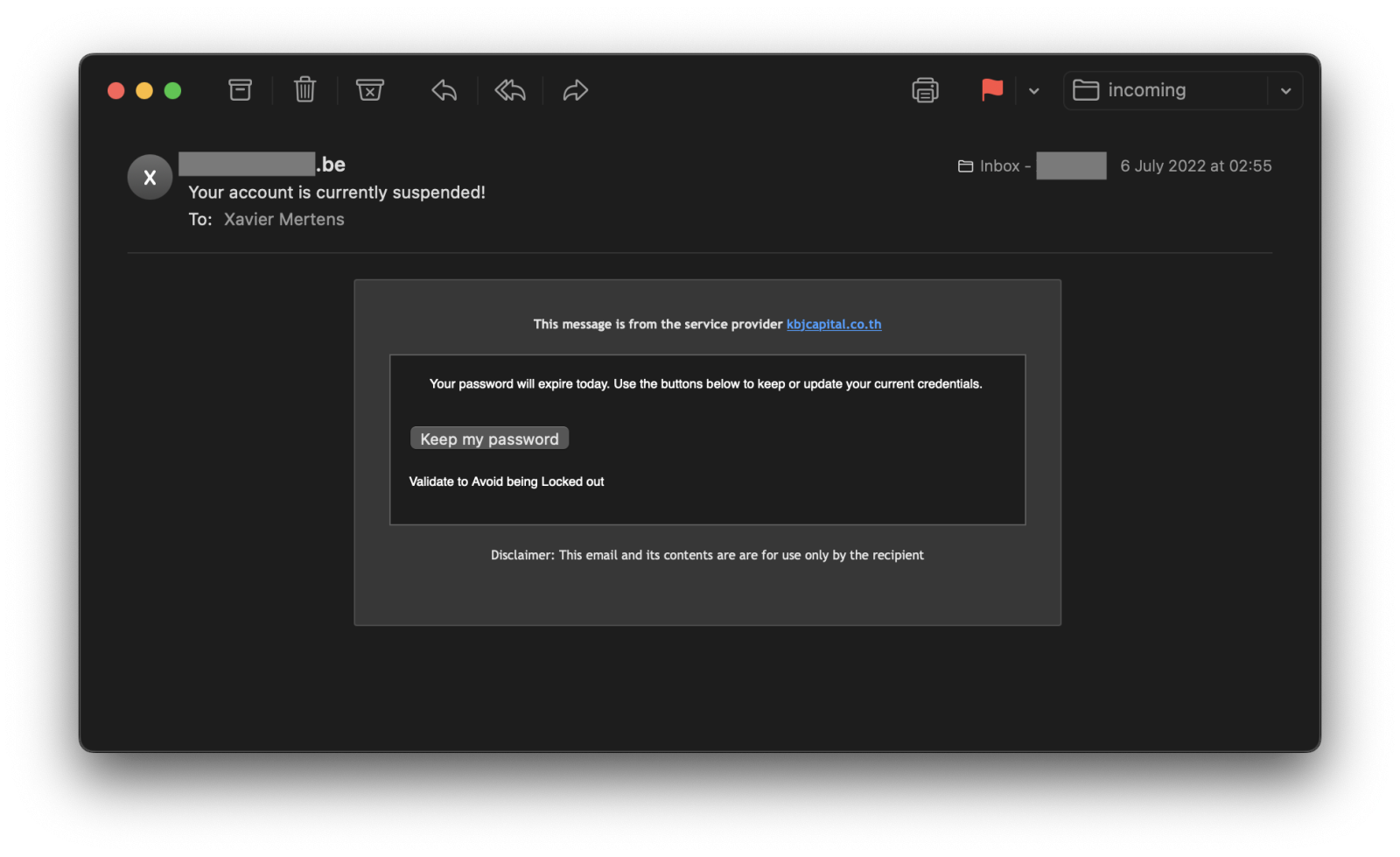
I received this email a few days before and, because we like spam and phishing, I had a quick look at it and clicked on the link in a sandbox.
Here is the complete URL with the victim's email address:
hxxps://firebasestorage[.]googleapis[.]com/v0/b/ptr2806ge.appspot.com/o/%5C%5Cptr2806g%2Findex2ptr.html?alt=media&token=1835e8a1-64d2-4fe6-9c37-16727092f0e8#xavier@<redacted>
When the link is visited by the victim, it will extract the domain name from the email address and make an HTTP requests to this domain. But why? I think that the purpose is to display the website in the background to make the user confident to enter his/her credentials. In my case, it did not work for the following reason:
The loading of “hxxps://<redacted>/” in a frame is denied by “X-Frame-Options“ directive set to “sameorigin“.
My website is not allowed to be loaded into an iframe, thanks to the X-Frame-Options[1] header.
To know exactly who was targeted by this phishing email, just check your corporate web server logs and search for the referer above. All requests found have been generated by people who clicked on the malicious link!
I tried to replace the original email address with another one but it did not work. Apparently, the token is linked to the email address. This is what you get when you change the address:
{
"error": {
"code": 400,
"message": "Invalid HTTP method/URL pair."
}
}
[1] https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments