A Day of SMB: What does our SMB/RPC Honeypot see? CVE-2022-26809
After Microsoft patched and went public with CVE-2022-26809, the recent RPC vulnerability, we set up a complete Windows 10 system exposing port 445/TCP "to the world." The system is not patched for the RPC vulnerability. And to keep things more interesting, we are forwarding traffic from a subset of our honeypots to the system. This gives us a pretty nice cross-section and keeps the system pretty busy. Other than not applying the April patches, the system isn't particularly vulnerable and is left in the default configuration (firewall disabled, of course).
So what did we get? I set up a quick Kibana dashboard on my home "SIEM" to track the activity:
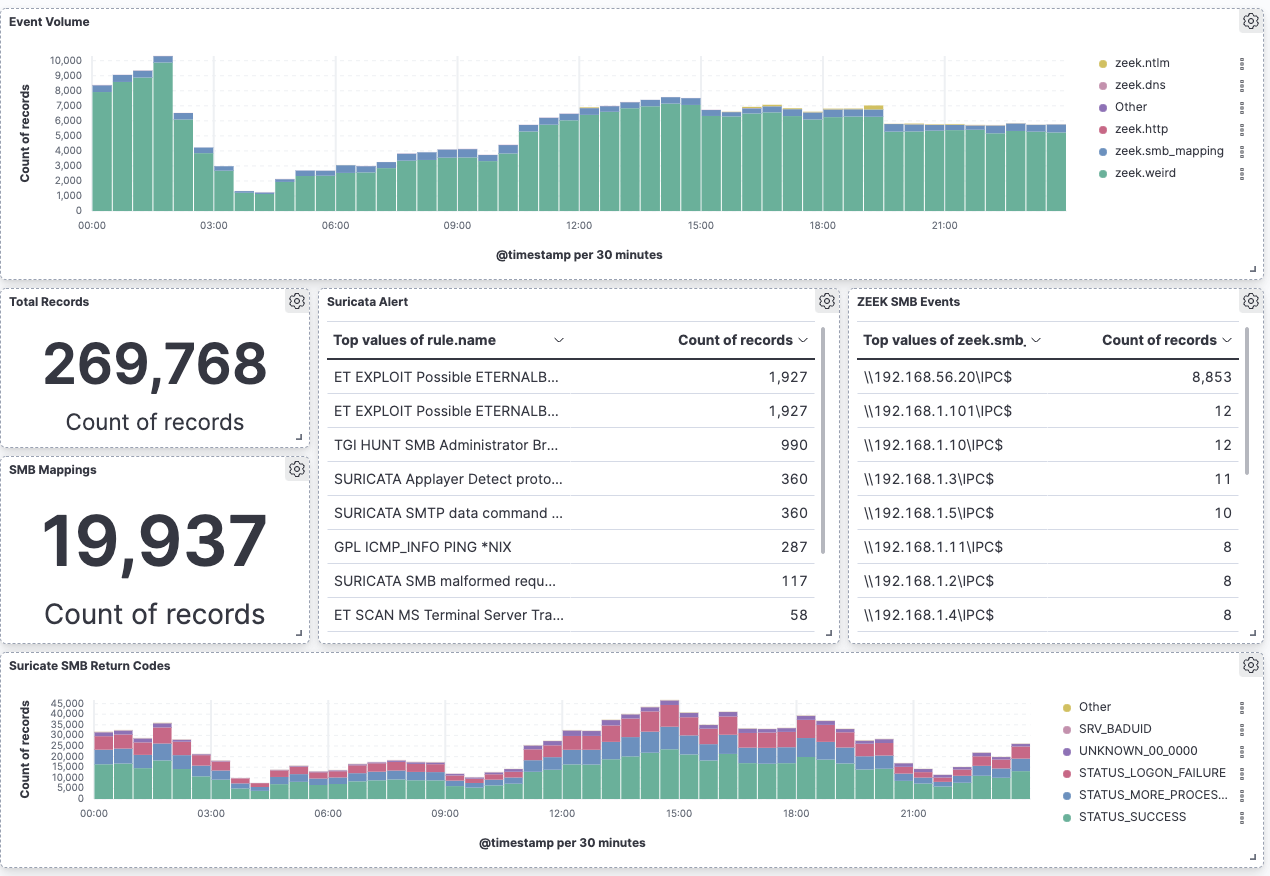
BLUF: We have not seen any attempts to exploit CVE-2022-26809. But instead, we saw a lot of old familiar exploits.
Due to redirecting many IP addresses to one little honeypot, we do get a good number of inbound connections to port 445. About 20k attempts to map shares per day or about a dozen a minute (well, more a baker's dozen). The share attempts are exclusively for IPC$, and they fail because we do not have a super-simple password.
But the #1 alert is still for "ETERNALBLUE" (MS17-010, CVE-2017-0144). I guess that vulnerability is still yielding some success, which is surprising given that I would expect vulnerable systems to be all taken over by now. Attackers may be hoping for new systems to be brought online.
We did get a non-neglectable number of attempts to look for an MS Terminal Server (58/day). RDP/VNC/Terminal server is still a favorite among attackers, and attackers are scanning various ports/means of access to find vulnerable systems. Hiding on an odd port will not help!
So how do we know that we got exploited? One thing I am watching on this honeypot is outbound connections (not displayed in the screenshot above as there isn't anything to show... yet).
Should you stop rushing out the April patch? Absolutely not. I hope you are already done applying the patch. But the April Windows patch had several additional gems, not just patches for RPC. Chatter about CVE-2022-26809 has died down, but as they say: Sometimes the quiet ones are the dangerous ones, and people able to exploit this vulnerability may not broadcast what they are doing on social media.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments