Obscure Wininet.dll Feature?
The Internet Storm Center relies on a group of Handlers[1] who are volunteers and offer some free time to the community besides our daily job. Sometimes, we share information between us about an incident or a problem that we are facing and ask for help. Indeed, why not request some help from fellow Handlers with broad experience? Yesterday, Bojan was involved in an incident with a customer and came back to us with this question:
"Did you already see this long list of domain names listed in C:\Windows\SysWOW64\wininet.dll on Windows 10?"
$ strings -e l wininet.dll | egrep 'hr\.'hr.com.eujuicershr.globalhr.prvikvadrathr.ak-varazdinhr.stinhr.pizzeriaamadeushr.silvergoldbullhr.maskicehr.perzeidihr.udruga-pointhr.tokichr.advancehr.com.airbnbhr.svijet-medijahr.autoskolehr.kubhr.slinkhr.com.cevohr.mallhr.autoskolahr.blablacarhr.abpishr.audionhr.from.brunohenchr.orkestar-krizevci ...
Immediately, other handlers started to check in their own labs and reported the same finding. Bojan, based in Croatia searched for the ".hr" TLD. I searched for ".be":
$ strings -e l wininet.dll |grep "be\." be.slimmerbouwen be.fanjoe be.buderus-family be.loanstreet be.de-spil be.maximdeboiserie be.intux be.lafosseobservatoire be.rubendv be.rigartmichael be.eliott be.pgtb be.kgm-irm be.psncardplus be.carroarmato0 be.poollicht be.mths be.nord-sud be.centralpoint ...
Guy did the same test and reported that his copy of the DLL has 47881 Unicode strings! We tested several Windows 10 systems and all of them had the same kind of strings in wininet.dll, so Bojan's one was not compromised.
What is this DLL? wininet or "Win32 Internet Extensions" is used to allow programs to interact with the Internet. It provides well-known API calls like:
InternetOpenURL InternetReadFile HTTPOpenRequest
You can imagine that it's being used by a lot of processes and applications. Note that you can list which processes loaded a specific DLL with the following command:
C:\Users\REM>tasklist /m wininet.dll Image Name PID Modules ========================= ======== ============================================ taskhostw.exe 4576 wininet.dll explorer.exe 4964 WININET.dll ShellExperienceHost.exe 4004 WININET.dll SearchUI.exe 4368 WININET.dll RuntimeBroker.exe 5192 WININET.dll Fiddler.exe 7048 WININET.dll WinStore.App.exe 2036 WININET.dll RuntimeBroker.exe 64 WININET.dll
Let's come back to the list of suspicious domains. What did we find? There are domains from many different TLDs. Some belong to small companies, others belong to big players within different domains of activity, and no relation between them. What we found is that many of them appear to be preloaded HSTS domains. The Chrome browser does this and has a hardcoded list of domains sites as being HTTPS only[3]. Does Microsoft implement the same within wininet.dll?
Our next step was to start debugging the DLL to learn more about these domains. They are passed to a function called IsHostInBlocklist(), which is in turn called from two separate locations CServerInfo::DetermineStrongCryptoState(), and CServerInfo::DetermineFalseStartState().
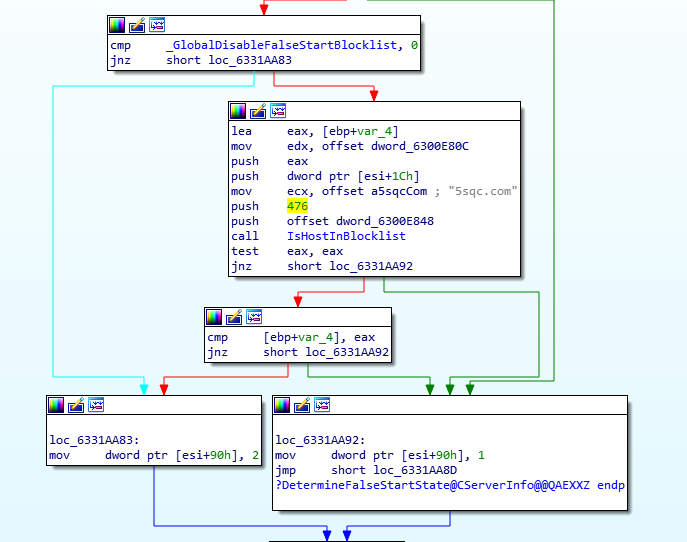
This function IsHostInBlockList() is used by interesting API calls but through a deep list of functions:
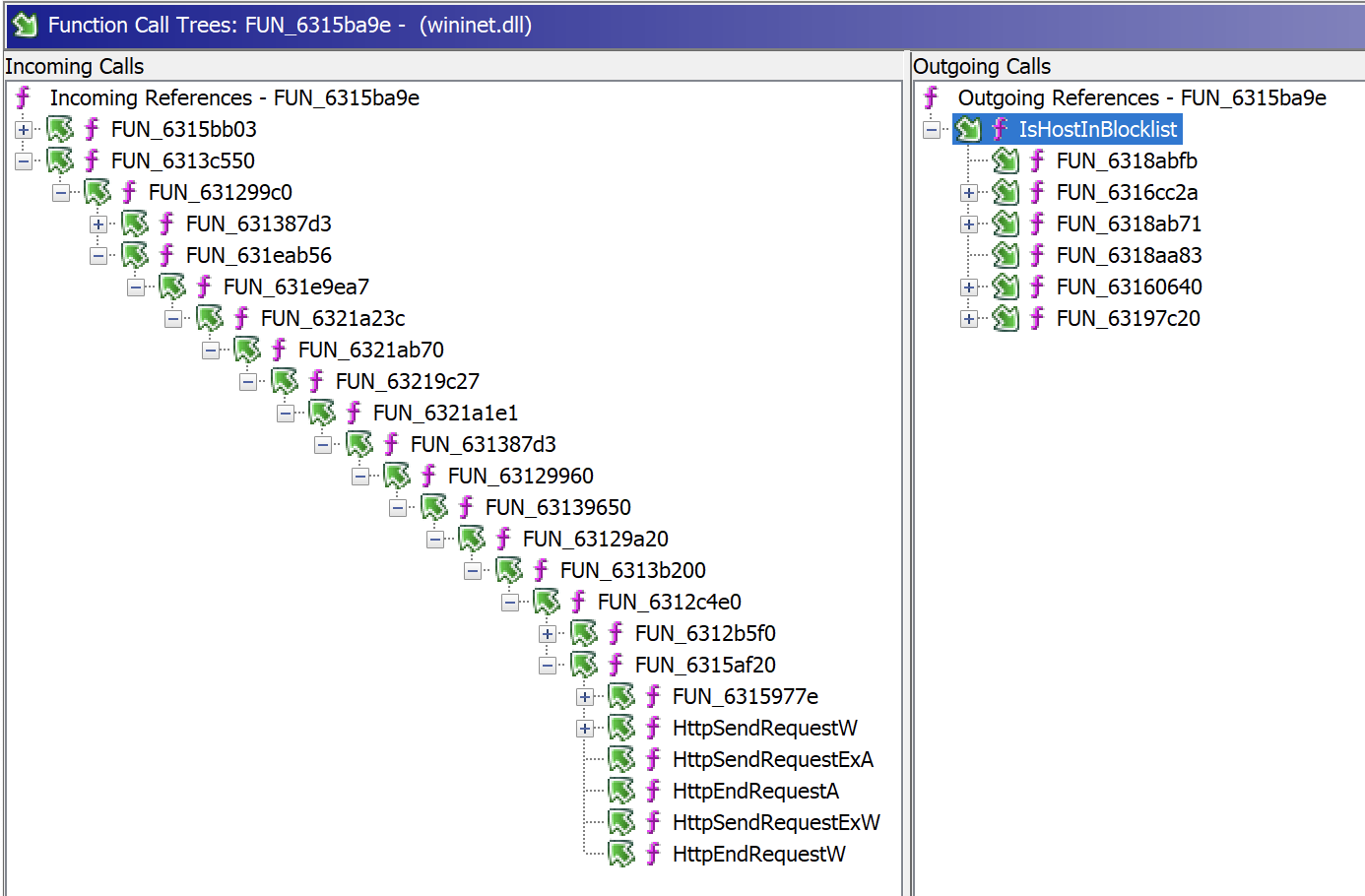
At this time, we are still investigating and trying to understand the purpose of those hardcoded domains and functions. They are listed in the DLL symbols[4] but no documentation was found. If you have more information, or if you are working for Microsoft, please share your findings with us!
[Update 1]
Benjamin Delpy[5] contacted us to give some information. The DLL has two lists of domains:
- A list of domains that ask for an SSL connection by default (tested through the function
DetermineStrongCryptoStart()) - A list of domains that are not compatible with TLS False Start[6] (tested with
DetermineFalseStartState())
According to Benjamin, the goal of IsHostInBlockList() changed with time but Microsoft kept the name.
[1] https://isc.sans.edu/handler_list.html
[2] https://docs.microsoft.com/en-us/cpp/mfc/win32-internet-extensions-wininet?view=msvc-170
[3] https://hstspreload.org/
[4] https://lise.pnfsoftware.com/winpdb/8B274E3115F9D58AB6E0DCF4CA336C86E4E1866AE7E801860B5F2876FAE48E24-wininet.html
[5] https://twitter.com/gentilkiwi
[6] https://tools.ietf.org/id/draft-bmoeller-tls-falsestart-00.html
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments