"Stolen Images Evidence" Campaign Continues Pushing BazarLoader Malware
Introduction
Another day, another wave of malware. Although there's plenty to find, I've been focusing on BazarLoader as it comes through various distribution channels. One such channel is the "Stolen Images Evidence" campaign, which Microsoft describes here. This campaign was pushing IcedID as we entered 2021, but it switched to BazarLoader as early as July 2021.
The "Stolen Images Evidence" campaign uses emails generated through contact forms on various websites. So these messages don't originate through normal spam methods. They appear through contact form submissions describing a copyright violation to the intended victim. These form-submitted messages include a Google firebase storage URL in the message text. This malicious link supposedly provides proof of stolen images that resulted in a copyright violation.
However, Google's service is being abused in this case, and the zip archive named Stolen Images Evidence.zip contains a JavaScript file designed to infect a vulnerable Windows host with BazarLoader.
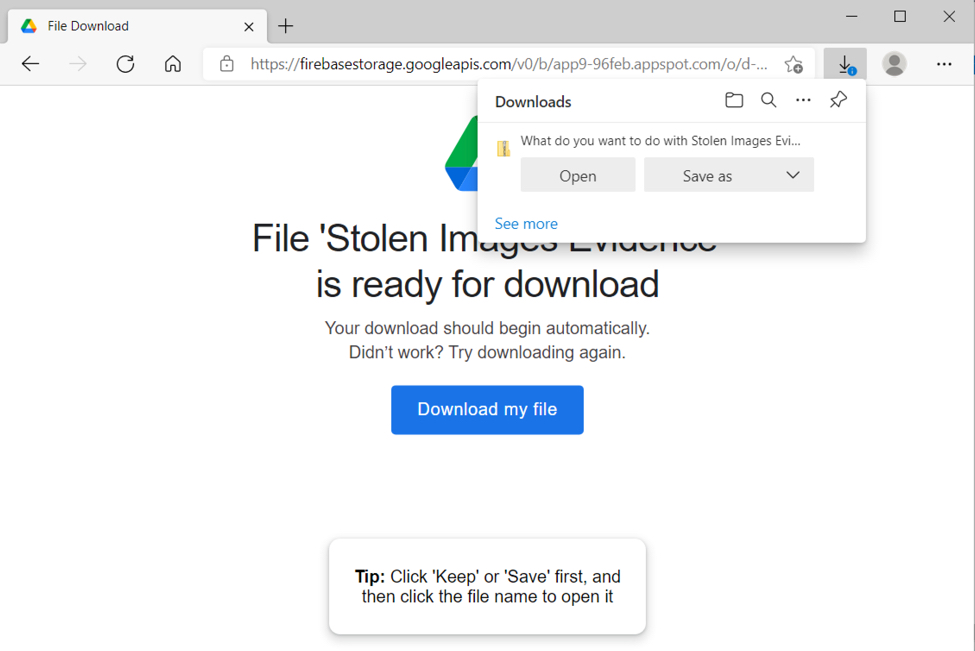
Shown above: Lnk from a copyright violation-themed form submission-generated email.
Downloaded zip archives
The downloaded zip archives are always named Stolen Images Evidence.zip. They contain a JavaScript file named Stolen Images Evidence.js.
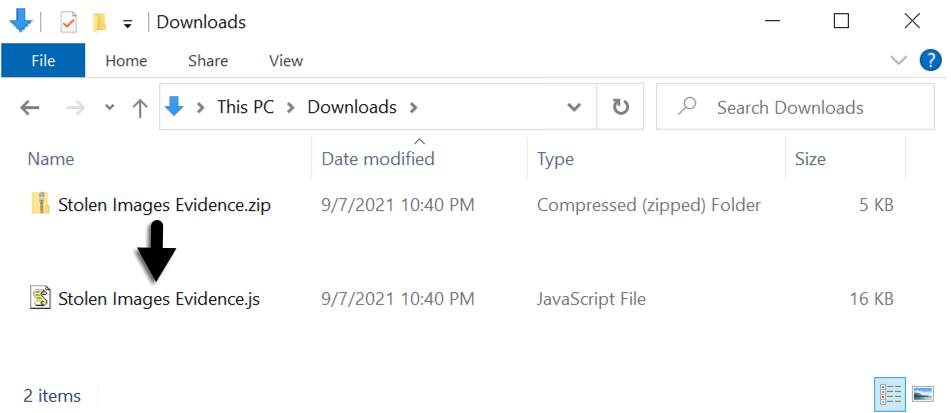
Shown above: Example of a downloaded zip archive and extracted .js file.
BazarLoader from the JS file
If a victim double-clicks the extracted JavaScript file on a vulnerable Windows host, it retrieves and runs a DLL for BazarLoader malware. The DLL is saved to the infected user's AppData\Local\Temp directory with a .dat file extension.
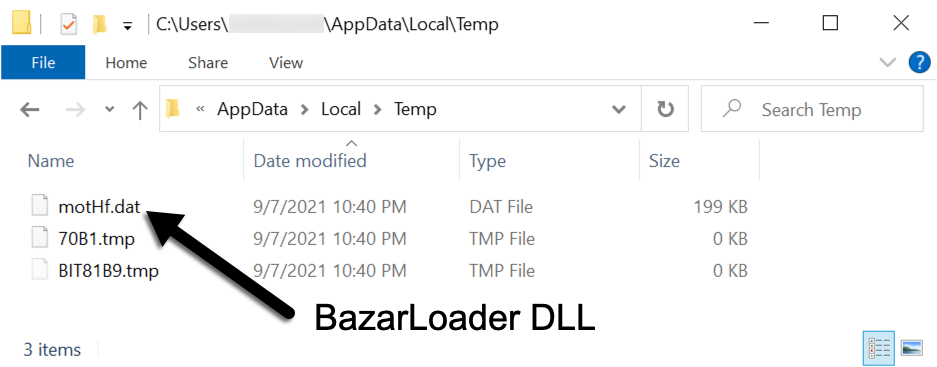
Shown above: BazarLoader DLL stored to an infected Windows host.
Infection traffic
Infection traffic is typical for what we normally see with BazarLoader.
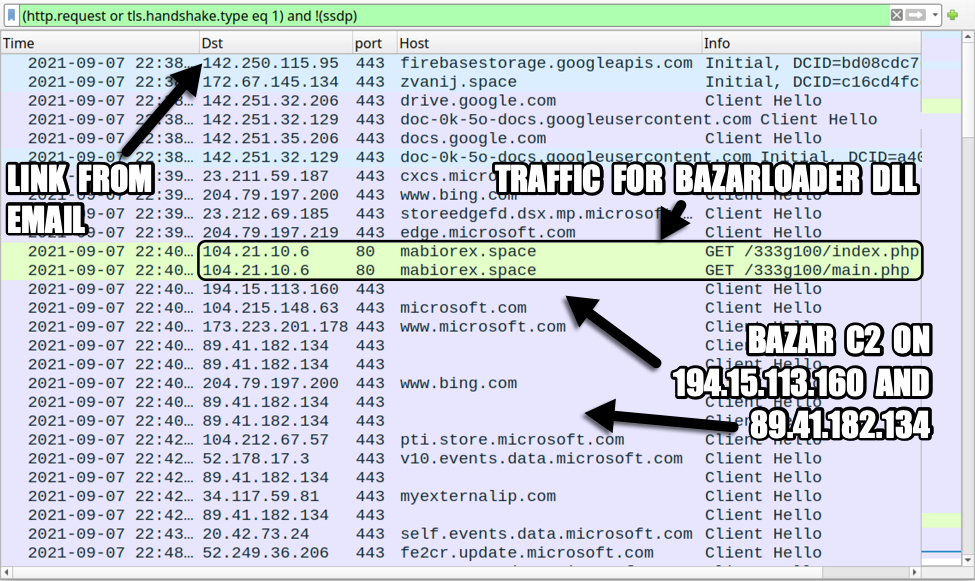
Shown above: Traffic from an infection filtered in Wireshark.
Indicators of Compromise (IOCs)
The following is malware retrieved from an infected Windows host.
SHA256 hash: c1cc9ec32368165e6625b2e2623ac0c3ca69bfa63a5b11e82a09bf18f6bd6410
- File size: 4,763 bytes
- File name: Stolen Images Evidence.zip
- File description: zip archive downloaded after clicking Google Firebase Storage link
SHA256 hash: 5a22e9bde5aaed03b323e5c933c473e9ba3831f4473790a3d4394baefe809d8a
- File size: 15,755 bytes
- File name: Stolen Images Evidence.js
- File description: JS file extracted from the above zip archive
SHA256 hash: dcf67fd6bfb62bea66f5e45d871d6c15b0c61d85c5fa9e9ded03e57f83dfc814
- File size: 203,281 bytes
- File location: hxxp://mabiorex[.]space/333g100/main.php
- File location: C:\Users\[username]\AppData\Local\Temp\motHf.dat
- File description: BazarLoader DLL retreived by the above JS file
- Run method: rundll32.exe [filename],StartW
Google Firebase URL used to deliver the malicious zip archive:
- hxxps://firebasestorage.googleapis[.]com/v0/b/app9-96feb.appspot.com/o/d-03rfdsbknu.html?alt=media&token=f7fc9a25-71b6-424d-aaf7-208fb11c27dd&f=025239220255728020
Malicious domain called when using the above Google Firebase URL:
- 172.67.145[.]134 port 443 - zvanij[.]space - HTTPS traffic
Traffic generated by the extracted JavaScript file to retrieve BazarLoader DLL:
- 104.21.10.6 port 80 - mabiorex[.]space - GET /333g100/index.php
- 104.21.10.6 port 80 - mabiorex[.]space - GET /333g100/main.php
Bazar C2 traffic:
- hxxps://194.15.113[.]160/workdir/tasks/run/handle
- hxxps://198.244.180[.]69/workdir/tasks/run/handle
- hxxps://89.41.182[.]134/workdir/tasks/run/handle
- hxxps://172.83.155[.]144/workdir/tasks/run/handle
Final words
The associated malware samples have been submitted to bazaar.abuse.ch, and they're available using links from the above SHA256 hashes.
This campaign uses "Stolen Images Evidence" and copyright violation as its primary theme. However, it also used a "DDoS attack proof" theme last month. Either way, this campaign has been fairly active in 2021, and we expect it to continue throughout the rest of this year. It will probably continue into 2022 as well.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
Microsoft Offers Workaround for 0-Day Office Vulnerability (CVE-2021-40444)
Microsoft today published an advisory with a workaround to mitigate an unpatched vulnerability in Microsoft Office. This vulnerability is currently used in targeted attacks.
CVE-2021-40444 is a code execution vulnerability in MSHTML. The exploit would arrive as an Office document that includes a malicious ActiveX control. As a workaround, Microsoft recommends disabling ActiveX in Internet Explorer and the advisory includes the necessary registry changes. At this point, it should be pretty low impact to disable ActiveX, but of course, there may be individual enterprise applications that still use ActiveX.
For more details, see Microsoft's advisory here:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-40444
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments