Office Documents with Embedded Objects
A reader asked about another malicious file, thinking it is an intentionally corrupt ZIP file.
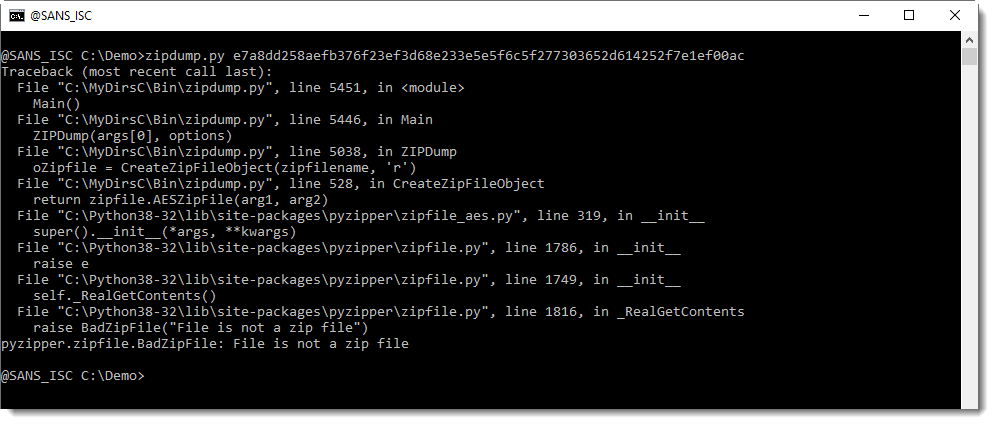
If you follow the steps I showed in diary entry "Office: About OLE and ZIP Files", you will see that it is not a corrupt ZIP file, but an OLE file containing 2 ZIP files.
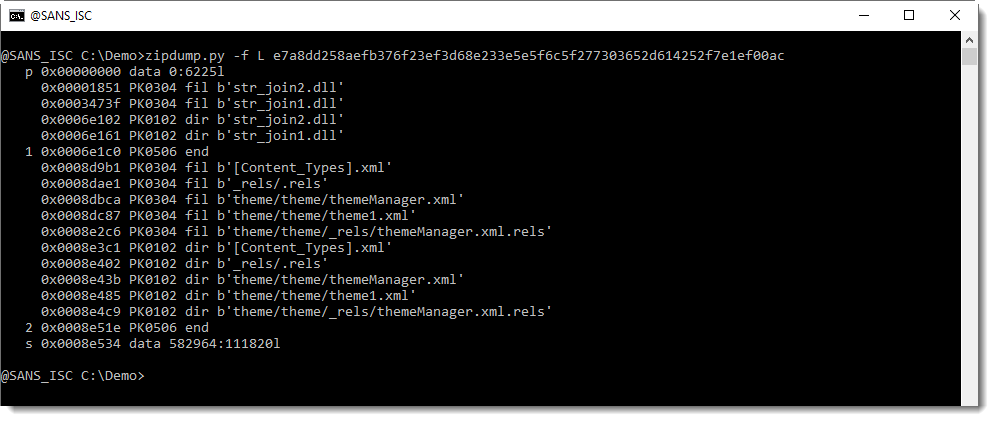
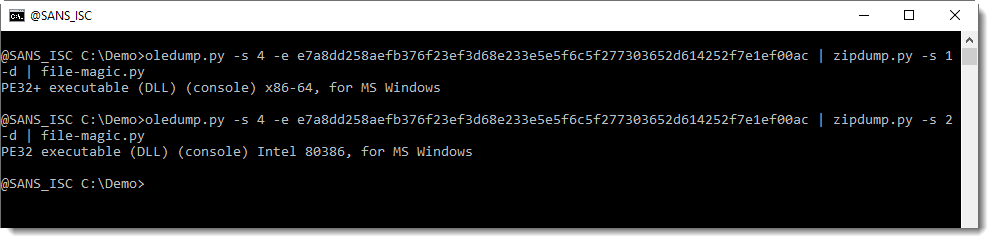
Once you have listed the PKZIP records with -f L, you will see 2 end-of-central-directory records (PK0506 end), indexed with 1 and 2. You can use this index to select and analyze the found ZIP file, like this:
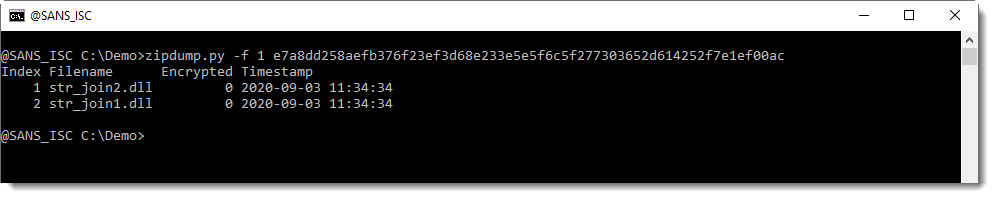
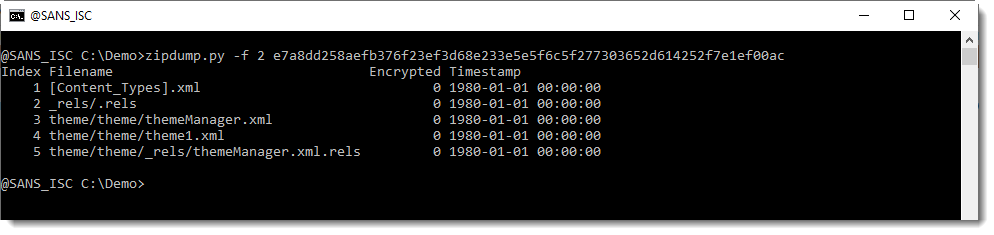
The first ZIP file appears to contain DLLs, and the second ZIP file contains theme data, as I explained in diary entry "Office: About OLE and ZIP Files".
This is indeed an OLE file:
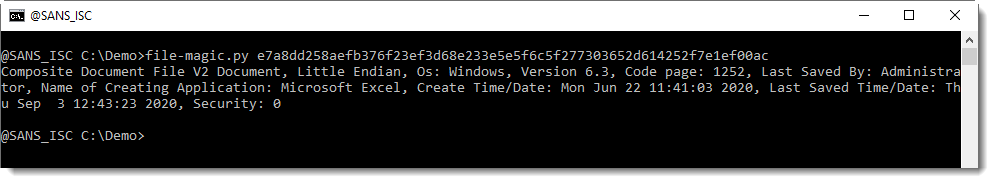
It is a spreadsheet (stream Workbook) with VBA code:
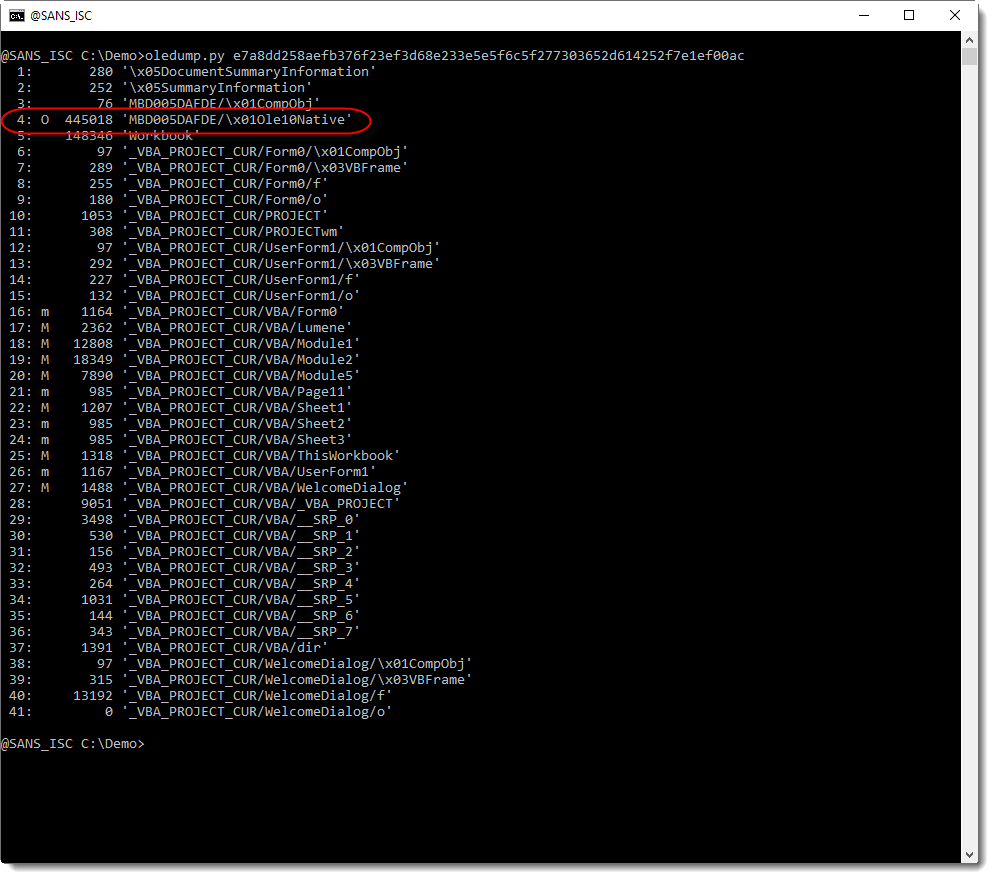
But it also contains an embedded object: remark indicator O for stream 4.
My tool oledump.py can handle embedded objects. Use option -I (info) to get more information:
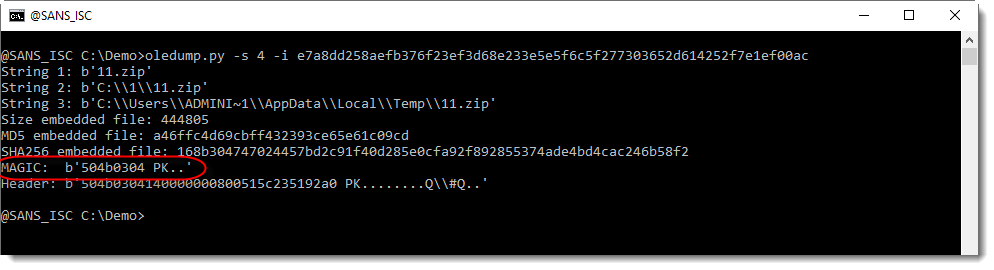
It is a ZIP file: not only by the file extension .zip, but also by the first 4 bytes of the file: 504B0304
With option -e (extract), you can extract the embedded file to stdout:
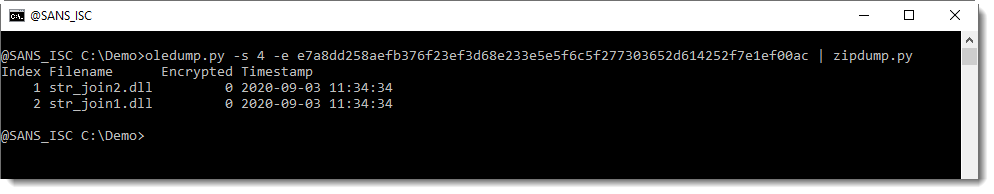
This is the first ZIP file we looked at with zipdump.py.
It contains a 64-bit and a 32-bit DLL:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments