A First Look at macOS 11 Big Sur Network Traffic (New! Now with more GREASE!)
In the next couple of months, Apple will likely release its next major update to macOS, "Big Sur" or also called macOS 11. I was able to install the most recent beta version of the operating system in a virtual machine to look at some of the network traffic. This should help you get ready for any oddities you may be seeing as users upgrade.
First of all: Network traffic pretty similar to the older versions of macOS. By default, it still uses "time.apple.com" for NTP. You will also still see a lot of connections to Apple's IP addresses in 17.0.0.0/8 for iCloud/Cloudkit connections.
TCP
Interestingly, macOS 11 uses a smaller window scale (5) instead of the slightly larger window scale (6) used by 10.15. I would have expected it to go the other way. However, the overall window size is about the same (128 KBytes). I guess the smaller window scale gives a bit more granularity. Just like MasOS 10.15, Big Sur does use ECN.
TLS
TLS now adds "GREASE" per RFC8701 (https://tools.ietf.org/html/rfc8701). GREASE is a bit an odd concept. TLS is extendable in that a client may use whatever cipher suites / TLS versions it feels like, and the server picks one that works while at the same time ignoring any options it doesn't understand. But some TLS implementations have been buggy and instead of ignoring unknown ciphers and TLS versions, they have refused to connect. So the idea of GREASE is to add random ciphers/TLS versions to weed out non-compliant implementations. I have often seen a "GREASE" cipher in current TLS implementation. But MacOS 11 also adds a "GREASE" TLS version
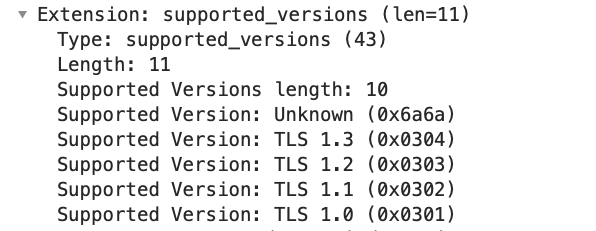
The version appears to vary randomly among the values allowed for GREASE (always two identical bytes. The second nibble of the byte is always "A").
Safari User-Agent
The User-Agent, as expected, uses "Mac OS X 11_0" as an operating system identifier.
Mozilla/5.0 (Macintosh; Intel Mac OS X 11_0) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/14.0 Safari/605.1.15
Compare to Mac OS 10.15.6:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.1.2 Safari/605.1.15
Security/Privacy Settings
The overall security settings appear to be identical to prior versions of macOS. A couple of new options were added to the privacy settings. It is now possible to restrict access to Bluetooth, Media & Apple Music as well as Homekit. I have not had a chance to look at some other security features in detail.
Installing BigSur in VMWare Fusion
I had an existing virtual machine running macOS, which I upgraded to BigSur using the public beta. The upgrade went without a problem. I had some glitches (for example, the virtual machine refuses to shut down. It will shut down but immediately reboot). This is expected for a beta version and VMWare Fusion does not officially support macOS 11. I did not attempt to install VMWare tools. In general, macOS is supported inside VMWare Fusion.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|


Comments