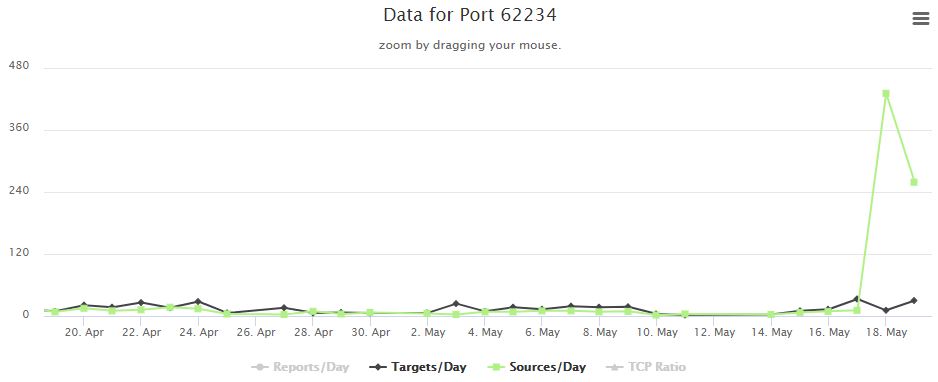
What is up on Port 62234?
Here at the ISC we provide access to a number of bits of data which can be used to dig into problems or even as an early warning system of unusual activity. Well today's data has revealed a confounding one. Port 62234, which traditionally has zero on near zero sources attempting to access it suddenly has hundreds of sources.
This port is not one I have seen as a target before, and none of my sources show any traffic on this port. A check of Shodan shows only 3 hits, and two of those appear to be BitTorrent related. I am at a loss. If any of you has further information, firewall logs, or better yet, packet captures of this activity it would be appreciated if you could send it over for analysis.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
Cisco Advisories for FTD, ASA, Firepower 1000
Cisco has released a number of advisories for Firepower and Adaptive Security Appliance (ASA).
Cisco Adaptive Security Appliance Software
CVE-2020-3259 - Web Services Information Disclosure Vulnerability – High
- An unauthenticated, remote, attacker can access memory and potentially confidential information.
CVE-2020-3298 - Malformed OSPF Packets Denial of Service Vulnerability – High
- An unauthenticated, remote, attacker could cause a device to reload resulting in DOS
CVE-2020-3196 – SSL/TLS Denial of Service Vulnerability - High
- Unauthenticated, remote attacker can exhaust memory resources leading to DOS
CVE-2020-3195 – OSPF Packet Processing Memory Leak Vulnerability – High
- Unauthenticated, remote attacker can exhaust memory resources resulting in DOS
Firepower Threat Defense
CVE-2020-3259 - Web Services Information Disclosure Vulnerability – High
- An unauthenticated, remote attacker can access memory and potentially confidential information.
CVE-2020-3298 - Malformed OSPF Packets Denial of Service Vulnerability – High
- An unauthenticated, remote, attacker could cause a device to reload resulting in DOS
CVE-2020-3255 – Packet Flood Denial of Service Vulnerability – High
- An unauthenticated, remote attacker can cause a DOS on the device.
CVE-2020-3189 – VPN System Logging Denial of Service Vulnerability - High
- Unauthenticated, remote attacker can cause memory leak resulting in device degradation or crash.
CVE-2020-3196 – SSL/TLS Denial of Service Vulnerability - High
- Unauthenticated, remote attacker can exhaust memory resources leading to DOS
CVE-2020-3195 – OSPF Packet Processing Memory Leak Vulnerability – High
- Unauthenticated, remote attacker can exhaust memory resources resulting in DOS
Firepower 1000
CVE-2020-3283 – SSL/TLS Denial of Service Vulnerability – High
- Unauthenticated, remote attacker can cause buffer underrun resulting in DOS.
Althought Cisco rated all of these vulnerabilities the same, high, most of them require a patient, determined attacker and will result in a DOS condition. The exception to this is CVE-2020-3259 which can result in a breach of sensitive information. Either way the solution is to upgrade to an unaffected version of the software.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments