Malspam with links to zip archives pushes Dridex malware
Introduction
In recent weeks, I continue to run across examples of malicious spam (malspam) pushing Dridex malware. While malspam pushing Dridex can use attachments (usually Excel spreadsheets with malicious macros), I tend to focus on malspam using links to zip archives for Dridex. Today's diary, provides a quick rundown of link-based Dridex activity on Tuesday, 2020-05-12.
Chain of events for these infections:
- Link from malspam
- Downloaded zip archive
- Extracted and execute VBS file
- Initial Dridex DLL dropped under C:\ProgramData\ directory
- HTTPS/SSL/TLS traffic caused by Dridex
- Three different Dridex DLLs loaded through copies of legitimate system files made persistent through a Windows registry entry, a scheduled task, and a shortcut in the Windows startup menu
The malspam
See the following images for 4 examples of the 14 samples I collected on Tuesday 2020-05-12.
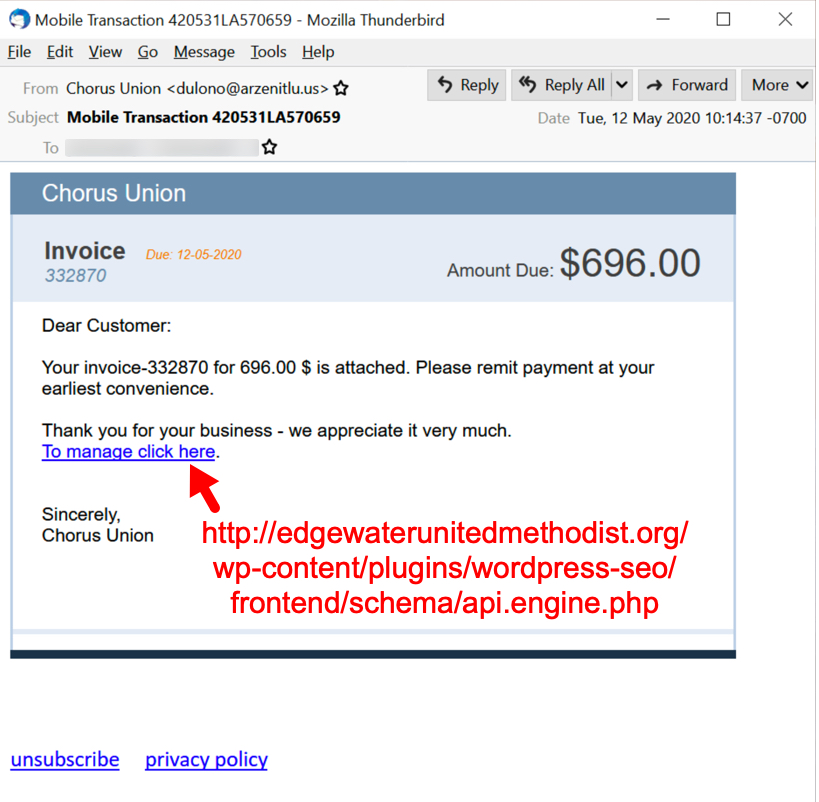
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 1 of 4.
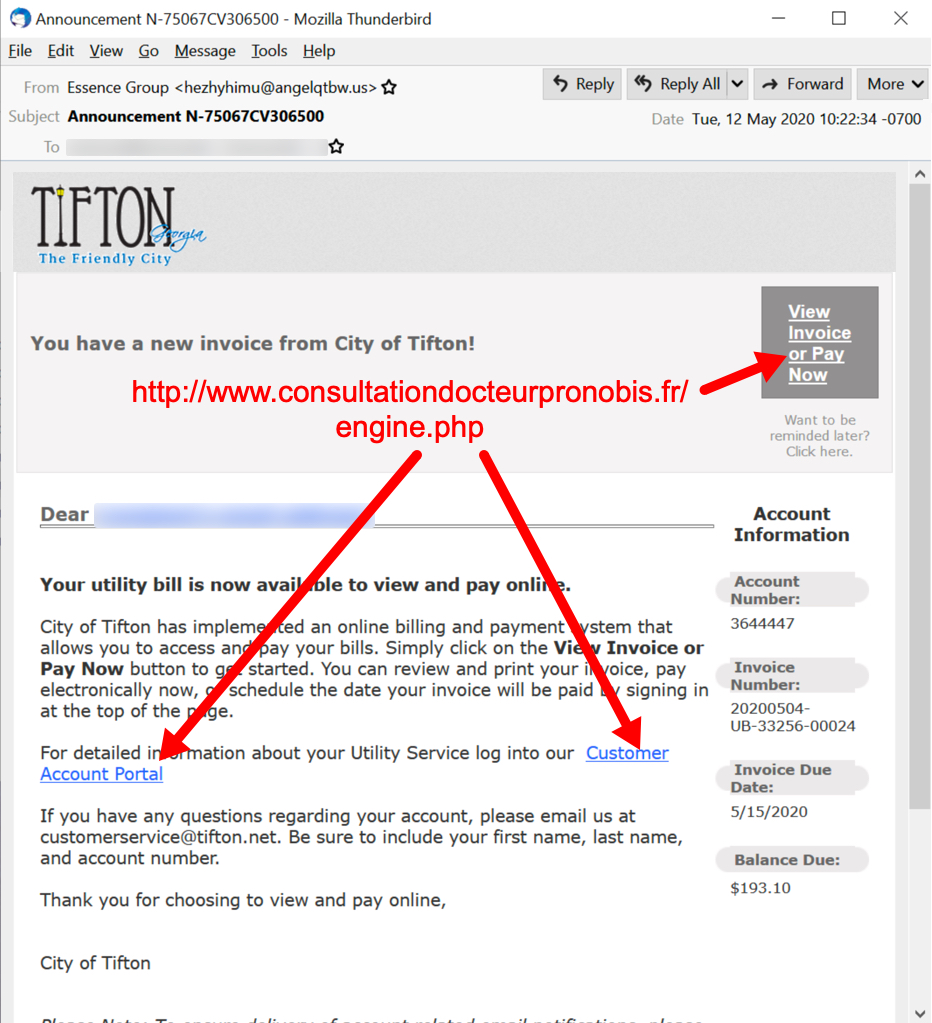
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 2 of 4.
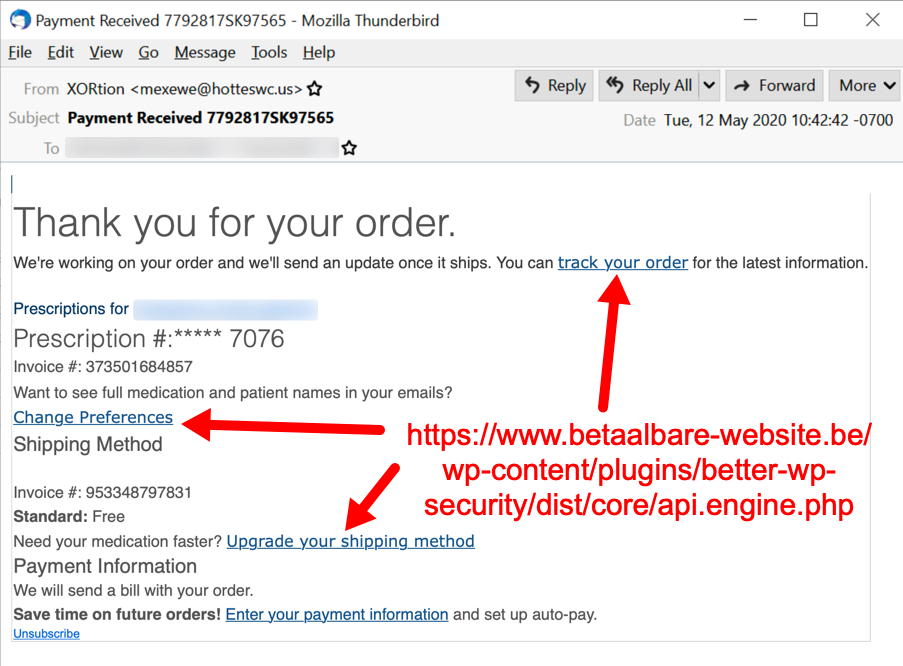
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 3 of 4.
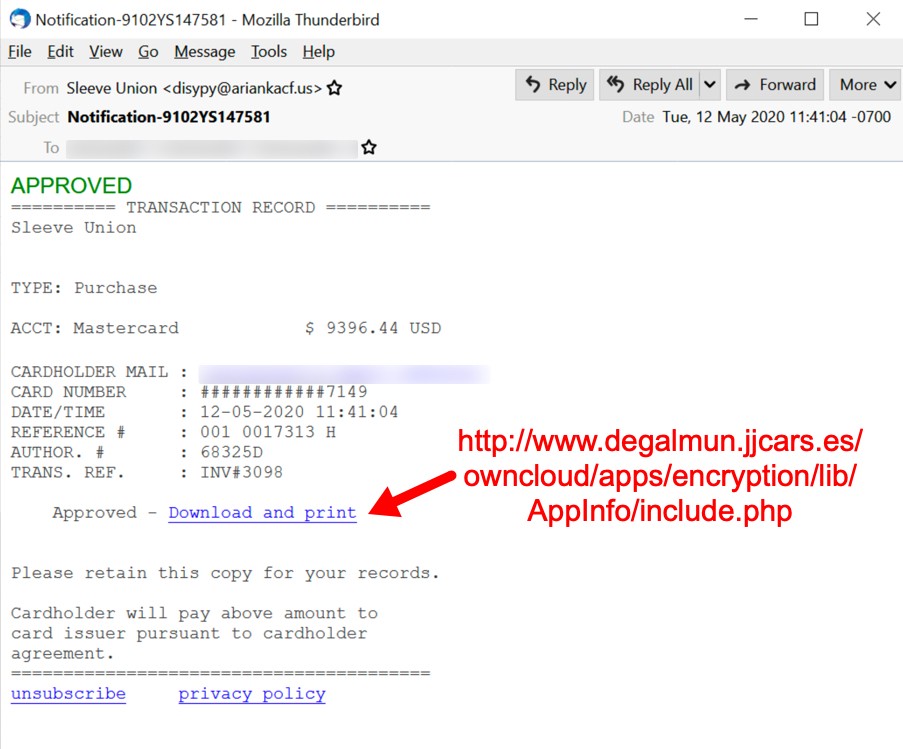
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 4 of 4.
Downloading the zip archive
When successfully downloading a zip archive from one of the email links, you get a redirect to another URL that returns the zip. These URLs are aware of the IP address you're coming from, so if you're a researcher coming from a VPN or other address the server doesn't like, it will redirect you to a decoy website. If you try the same email link more than once (and you're from the same IP address), each successive attempt will give you the decoy website. These decoy websites are different for each new wave of Dridex malspam that uses links for zip archives.
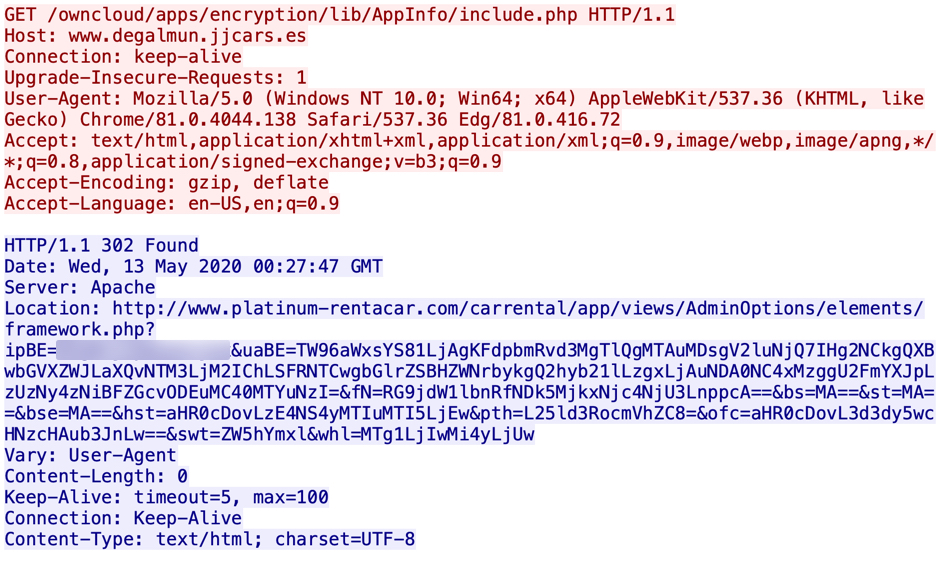
Shown above: Link from an email provides a successful redirect that will return a malicious zip archive.
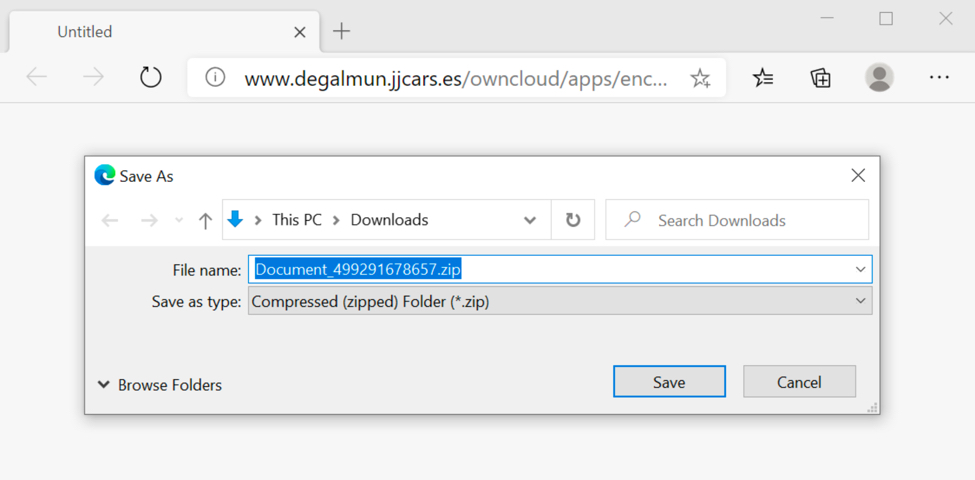
Shown above: Saving the malicious zip archive.
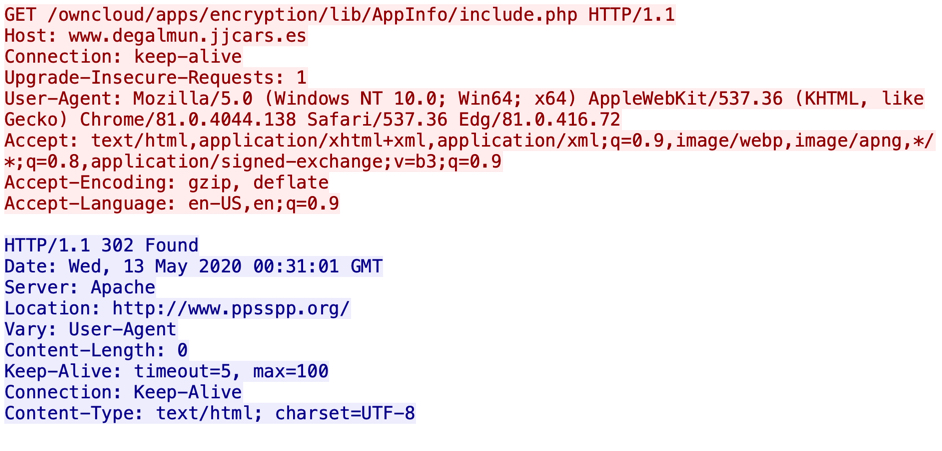
Shown above: Link from an email redirects to a decoy website.
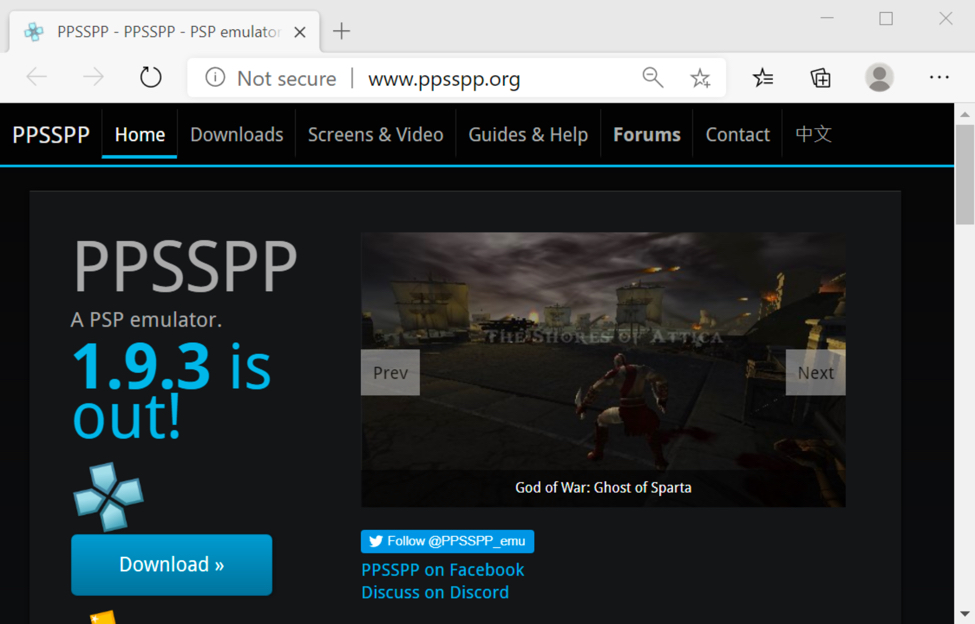
Shown above: Decoy website when the server doesn't like the IP you're coming from. The decoy site from the 2020-05-12 wave was www.ppsspp.com.
The zip archive contains a VBS file, which will use Windows script host to run and install Dridex on a vulnerable Windows host.
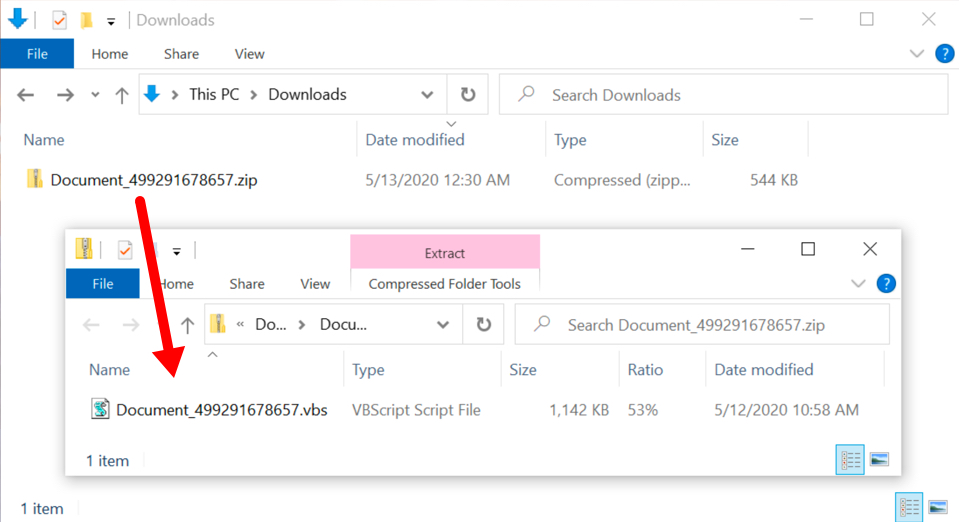
Shown above: The downloaded zip archive contains a VBS file.
Shown above: Start of the contents on the extracted VBS file.
Infection traffic
Infection traffic was typical for what I normally see with Dridex infections.
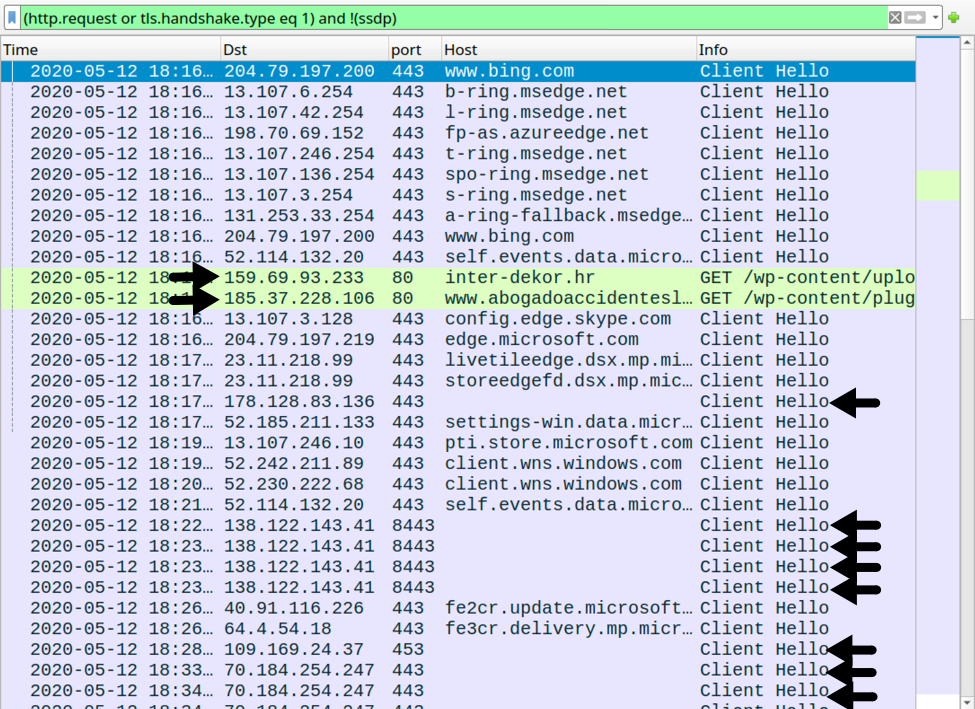
Shown above: Traffic from an infected Windows 10 host filtered in Wireshark. Dridex traffic is noted with the arrows.
Indicators of Compromise (IoCs)
Data from 14 email examples of malspam with links to zip archives pushing Dridex:
- Date: Tue, 12 May 2020 10:14:37 -0700
- Date: Tue, 12 May 2020 10:22:34 -0700
- Date: Tue, 12 May 2020 10:42:42 -0700
- Date: Tue, 12 May 2020 10:52:58 -0700
- Date: Tue, 12 May 2020 11:17:48 -0700
- Date: Tue, 12 May 2020 11:21:09 -0700
- Date: Tue, 12 May 2020 11:41:04 -0700
- Date: Tue, 12 May 2020 11:51:54 -0700
- Date: Tue, 12 May 2020 11:57:37 -0700
- Date: Tue, 12 May 2020 12:12:12 -0700
- Date: Tue, 12 May 2020 12:24:10 -0700
- Date: Tue, 12 May 2020 12:32:41 -0700
- Date: Tue, 12 May 2020 12:49:01 -0700
- Date: Tue, 12 May 2020 12:56:48 -0700
7 different sending mail servers:
- Received: from angelqtbw.us ([147.135.60.145])
- Received: from ariankacf.us ([147.135.60.150])
- Received: from arzenitlu.us ([51.81.254.89])
- Received: from falhiblaqv.us ([147.135.99.6])
- Received: from hotteswc.us ([147.135.60.146])
- Received: from ppugsasiw.us ([147.135.99.18])
- Received: from pufuletzpb.us ([147.135.99.8])
14 different spoofed senders:
- From: Abg Deem <[email protected]>
- From: Abg Icarus <[email protected]>
- From: Abg Navy <[email protected]>
- From: Amity Save <[email protected]>
- From: Arid Save <[email protected]>
- From: Chorus Union <[email protected]>
- From: Continuum Union <[email protected]>
- From: Cool Union <[email protected]>
- From: Essence Group <[email protected]>
- From: Goal Save <[email protected]>
- From: Laced Save <[email protected]>
- From: Seeds Group <[email protected]>
- From: Sleeve Union <[email protected]>
- From: XORtion <[email protected]>
14 different subject lines:
- Subject: Announcement N-75067CV306500
- Subject: Customer your Booking N-1341KM290237
- Subject: Invoice 9497989GM301562
- Subject: Invoice-376198HW271105
- Subject: Mobile Transaction 420531LA570659
- Subject: Notification-9102YS147581
- Subject: Payment Received 245906CW349815
- Subject: Payment Received 7792817SK97565
- Subject: Prevention_216443WF226975
- Subject: Prevention_739687SL4713
- Subject: Recipient your Inquiry N-0650581WC836637
- Subject: Report-03551HJ5068
- Subject: Your Bell e-Bill is ready 70605KU2719
- Subject: Your Transaction was Approved 8877WA048712
13 different links from the emails:
- hxxp://brisbaneair[.]com/class.cache.php
- hxxp://carbonne-immobilier[.]com/images/2016/icons/list/api.core.php
- hxxp://edgewaterunitedmethodist[.]org/wp-content/plugins/wordpress-seo/frontend/schema/api.engine.php
- hxxp://inter-dekor[.]hr/wp-content/uploads/wysija/bookmarks/medium/framework.php
- hxxp://iris[.]gov[.]mn/app/framework.php
- hxxp://masterstvo[.]org/modules/mod_rokgallery/templates/showcase_responsive/dark/cache.php
- hxxp://www[.]consultationdocteurpronobis[.]fr/engine.php
- hxxp://www[.]degalmun.jjcars[.]es/owncloud/apps/encryption/lib/AppInfo/include.php
- hxxps://azparksfoundation[.]org/wp-content/themes/twentynineteen/sass/blocks/styles.php
- hxxps://equineantipoaching[.]com/wp-includes/sodium_compat/namespaced/Core/ChaCha20/lib.php
- hxxps://rudhyog[.]in/surat/include/login/api.core.php
- hxxps://www[.]betaalbare-website[.]be/wp-content/plugins/better-wp-security/dist/core/api.engine.php
- hxxps://www[.]boosh[.]io/class.lib.php
Traffic from an infected Windows host
- 159.69.93[.]233 port 80 - inter-dekor[.]hr - GET /wp-content/uploads/wysija/bookmarks/medium/framework.php
- 185.37.228[.]106 port 80 - www[.]abogadoaccidenteslaboralesen-madrid[.]com - GET /wp-content/plugins/drpsassembly/css/inc.php?[string of variables and base64-encoded data]
- 178.128.83[.]136 port 443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
- 138.122.143[.]41 port 8443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
- 109.169.24[.]37 port 453 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
- 70.184.254[.]247 port 443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
Examples of malware from an infected Windows host:
SHA256 hash: ff8e2e72b1282b72f1a97abb30553d2b8d53366f429083f041c553d2a90878f6
- File size: 571,519 bytes
- File name: Report_224726231283.zip
- File description: File downloaded from link in malspam pushing Dridex
SHA256 hash: a61b462f61f526c4f9d070ba792ecd4a8b842f815ed944b7f38169698bed047e
- File size: 1,260,284 bytes
- File name: Report~224726231283.vbs
- File description: VBS file extracted from downloaded zip archive (designed to infect vulnerable host with Dridex)
SHA256 hash: 223e3e76df847b4e443574e616e56b348213bd0361a7f6789d21754de571cce7
- File size: 714,240 bytes
- File location: C:\ProgramData\qEWTLCuYyH.dll
- File description: Initial Dridex DLL dropped by above VBS file
- Run method: regsvr32.exe -s C:\ProgramData\qEWTLCuYyH.dll
SHA256 hash: 9a9e0ab271f8a27f689a350db3cecc84320dd3c708085c75d14adbafdd9da2a1
- File size: 700,416 bytes
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\CloudStore\DyGykefYBHT\DUser.dll
- File description: Dridex DLL persistent on an infected Windows host (1 of 3)
- File note: DLL loaded by bdeunlock.exe in the same directory, persistent through registry update
SHA256 hash: 9197396ed203f804226fb94548b4b899a46feaa7f7ff963fbccff232b5a79277
- File size: 696,320 bytes
- File location: C:\Users\[username]\AppData\Roaming\Thunderbird\Profiles\mng7115w.default-release\crashes\Niby8ztx\VERSION.dll
- File description: Dridex DLL persistent on an infected Windows host (2 of 3)
- File note: DLL loaded by iexpress.exe in the same directory, persistent through Startup menu shortcut
SHA256 hash: 28b9c07de53e41e7b430147df0afeab278094f3585de9d78442c298b0f5209e3
- File size: 978,944 bytes
- File location: C:\Users\[username]\AppData\Roaming\Adobe\Acrobat\DC\JSCache\Y3skYJ7F3B\DUI70.dll
- File description: Dridex DLL persistent on an infected Windows host (3 of 3)
- File note: DLL loaded by bdeunlock.exe in the same directory, persistent through a scheduled task
Final words
When a Dridex-infected Windows host is rebooted, the locations, names, and file hashes of the persistent Dridex DLL files are changed.
Dridex remains a feature of our threat landscape, and it will likely continue to be. Windows 10 hosts that are fully patched and up-to-date have a very low risk of getting infected from Dridex, so it pays to follow best security practices.
Email examples, malware samples, and a pcap from an infected Windows host used in today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments