Annotating Golang binaries with Cutter and Jupyter
In my previous post we've gone through some of the basics of analysing Golang binaries. This post will annotate source path and line information to the disassembly in Cutter. If you're not familiair with Cutter, it is the Qt bases frontend for Radare2.
Adding source path and line information for disassembled instructions makes it much easier to interpret and analyse the binaries. It will add a lot more context to the binary. If you want to play with the notebook, you' can download the notebook here. Later the notebook can be converted to a plain python script / plugin, making it easier to use within Radare2 or Cutter as a plugin.
Inside Cutter there is a tab to start Jupyter, which contains a link to open the Jupyter session. In the first cell we connect to the active Cutter session, assuming the Golang binary has been opened and analysed already.
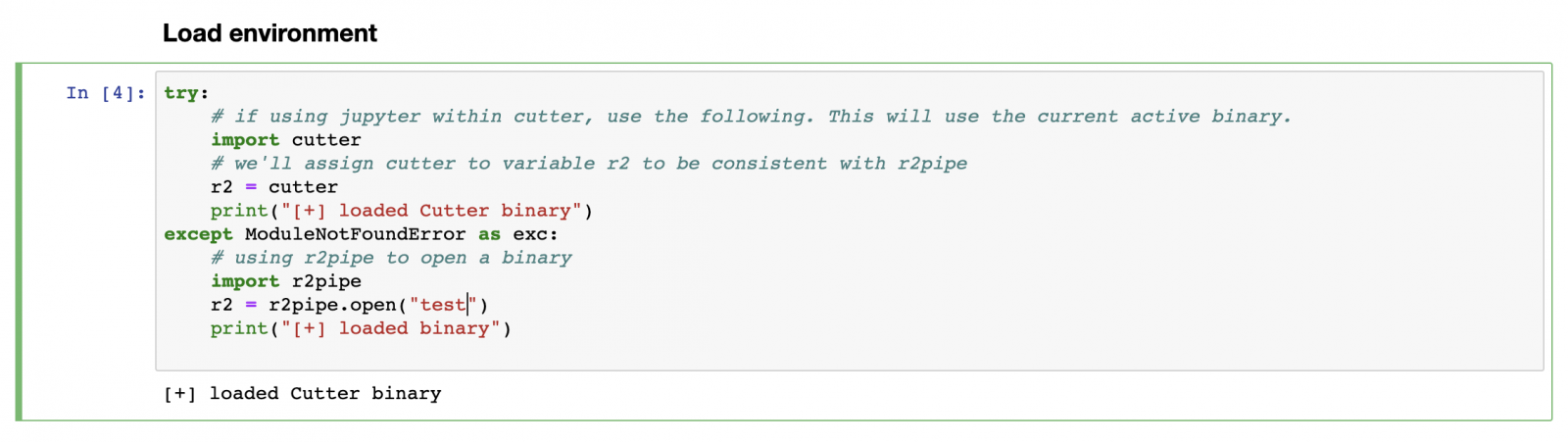
Communication with Cutter is being done using r2pipe, executing radare2 commands returing json. To retrieve information about sections in the binary, we execute command iSj. Suffixing commands with a j will return json output, making it easier to use within python. The returned section information will be be stored in a map, with size and vaddr information for later reference.
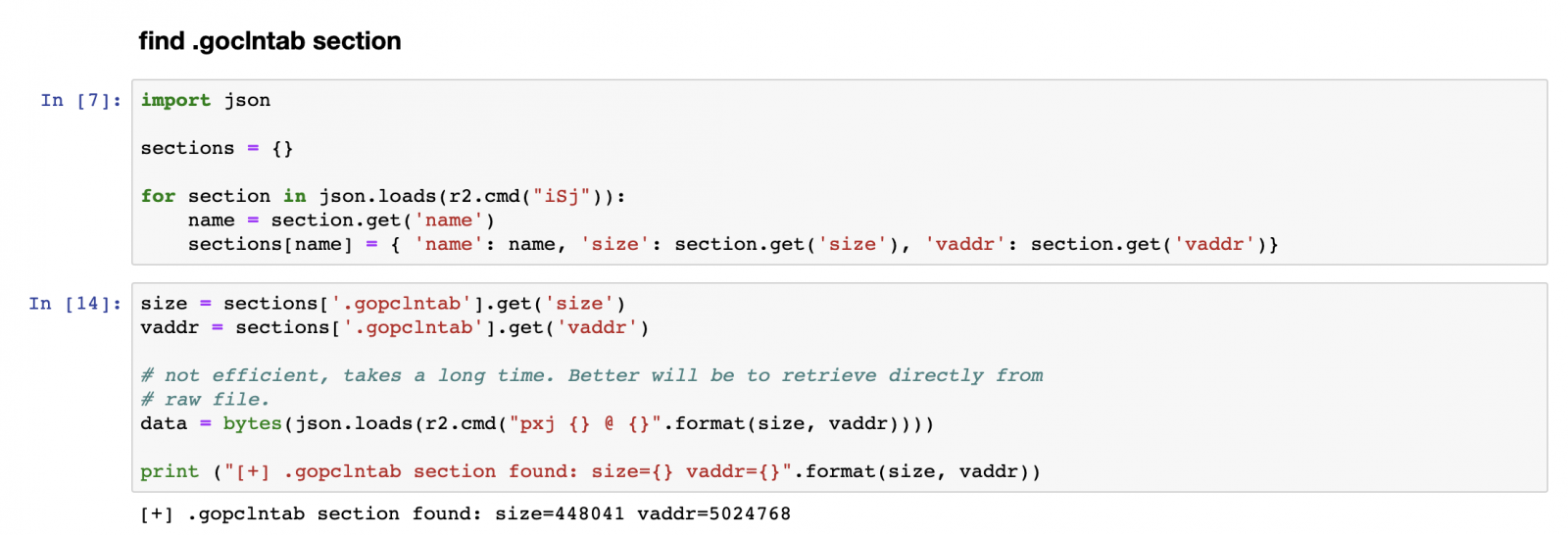
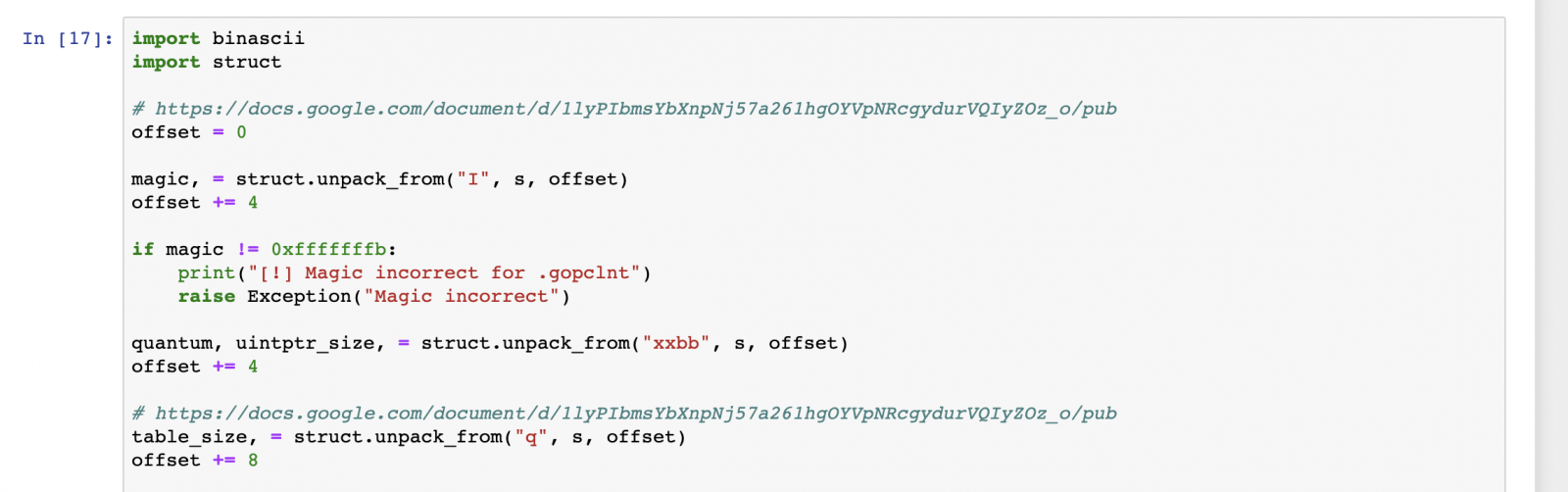
The interesting bits are located in the .gopclntab section, this section contains the source path and line information per address. The .gopclntab section documentation can be found here. Next we'll walk through the section, verifying the magic bits, extract the configuration and table size.
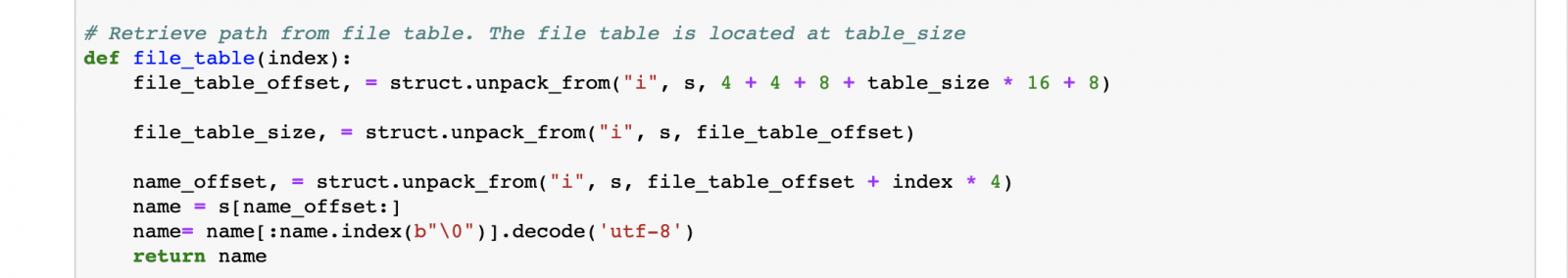
Defining a method file_table, which will be used to lookup indexes in the file_table and return the corresponding path.
Now we can walk through the actual table. The table consists of a pair of a program counter and a function offset. Each function is being described in detail at the function offset, containing information about arguments, function name, arguments, path and line information.
Using r2.cmd we can use the command CCu, which will add comments at the specified address. Executing the cell shows information about the program counters found and their corresponding source lines.
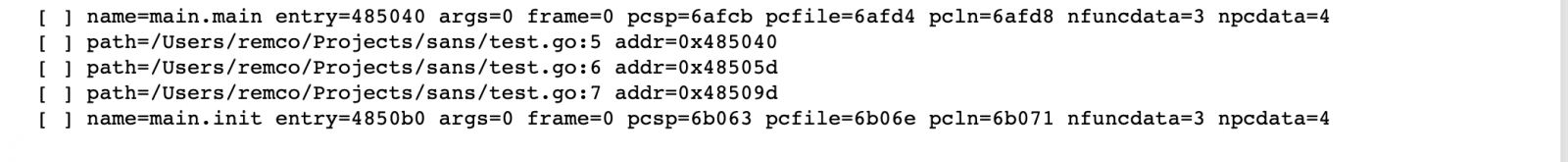
Switching back to Cutter again, you'll see that specific addresses now have comments with the source location for the address.
Please share your ideas, comments and/or insights, with me via social media, @remco_verhoef or email, remco.verhoef at dutchsec dot com. Have a great day!
Remco Verhoef (@remco_verhoef)
ISC Handler - Founder of DutchSec
PGP Key


Comments